This Terraform folder is dedicated to create and configure the Vault server. For this purpose, we will create a Vault cluster in the HashiCorp Cloud Platform (HCP) and use the Terraform Cloud to configure it.
This folder will only manage the configuration of the Vault and not the GitLab-CI OR the AWS project. Refer to the project
project-gitlab-terraform-vaultfor that.
This repository is design to:
- Create and configure a HCP Vault and AWS IAM resources like roles. Those actions are located in the vault.tf & aws.tf files.
- Create a GitLab repository (used to deploy the app) and set a Terraform Cloud Workspace to this repository
- Configure the permissions to the GitLab-CI repository to have access to secrets stored in Vault like:
- Retrieve a AWS secret: to deploy the AWS infrastructure of the application.
- Retrieve a Terraform Cloud token: to execute a
localexecution of a Terraform Cloud Workspace. This token has generate based on a Terraform Team who has access to the Terraform Cloud Workspace. - Store a Database Dynamic secrets: when the infrastructure has been deploy, GitLab-CI will store the database secret to Vault as a dynamic secret.
- The GitLab-CI is allowed to authenticate to the Vault based on the
GitLab repository IDand allow the branchmain. Also, the repository GitLab is feed with some environment variables used by the GitLab-CI (e.g. Vault backend names, Vault role name to used, Vault address, etc )
You will find below an overview of this workflow:
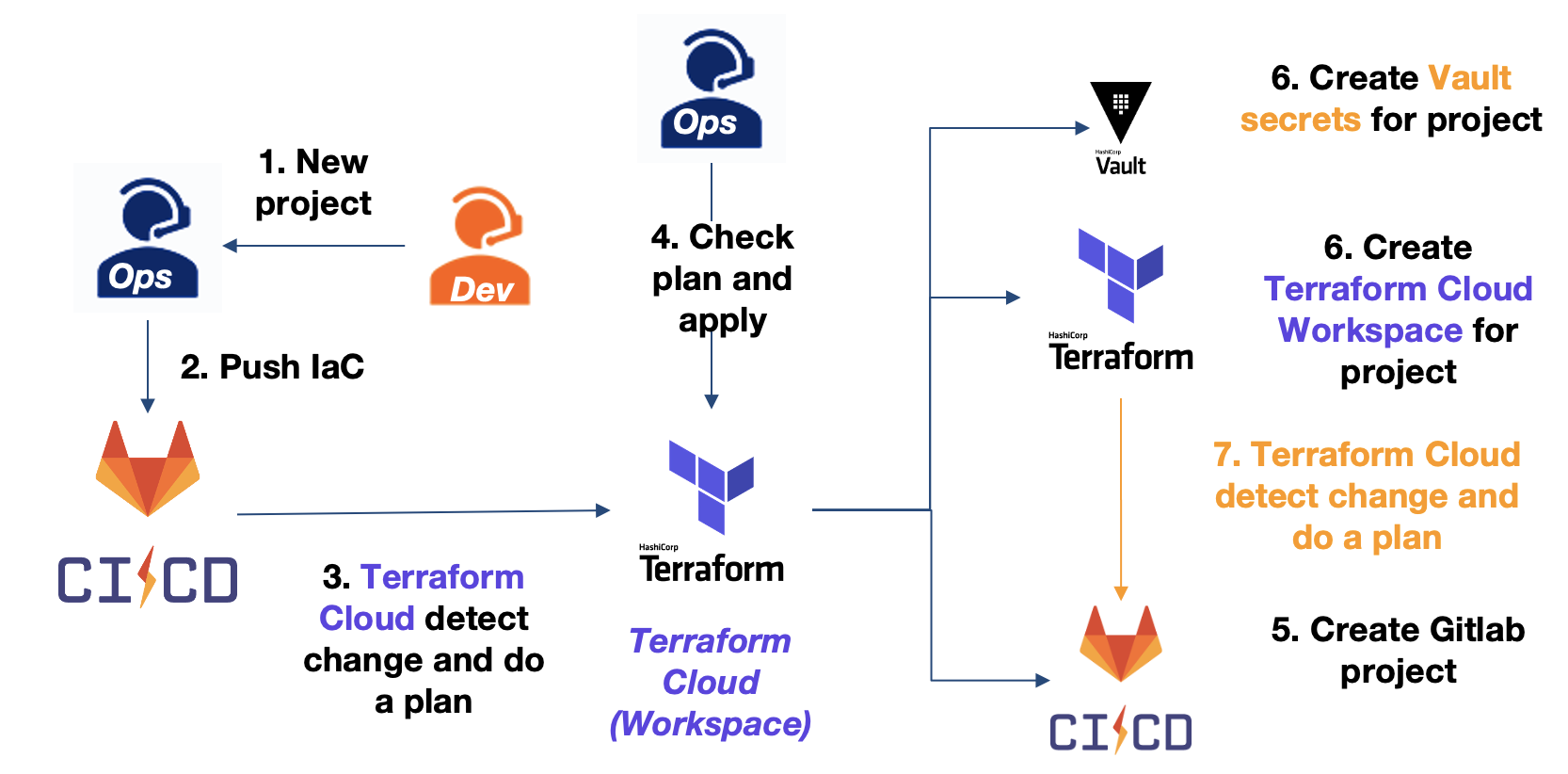
You need to create:
- A GitLab repository and push this repository
- In Terraform Cloud, create a VCS Providers where your GitLab repository is hosted.
- Create a Terraform Cloud Workspace with a
Execution ModetoRemoteand connected to your previous Gitlab Repository. - Update the file
backend.tfin theremotesection with your organization name and the workspace name create before. - Configure the variables bellow.
Some token needed as a env of the project:
GITLAB_TOKEN: You need to create a GitLab Personal Access Token (PAT) and feed with this value as a Terrform variable & sensitive value.TFE_TOKEN: Create a User API Token and feed with this value as a Terrform variable & sensitive value.vcs_id: In theVCS Providerssettings, get the Oauth Token Id and set it as a Terrform variable.AWS_ACCESS_KEY_ID&AWS_SECRET_ACCESS_KEY: Create an IAM user with a IAM full permission. Then, create an Access & Secret key and feed with this value as a env variable & sensitive value.HCP_CLIENT_ID&HCP_CLIENT_SECRET: Create a Service Principal with the Contributor role in HashiCorp Cloud Platform and create a key for your Service Principal. Feed with this value as a env variable & sensitive value.tfc_org_name: The name of the Terraform Cloud Organization. Feed with this value as a Terrform variable.
You should provide some required value for your Terraform. Keep it mind, the .gitignore
will not push your terraform.tfvars file if you use it to setup your variables.
Refer to the section Input below to check which variables to setup.
It will create:
- An HCP Vault
- Gitlab Repository
- AWS IAM resources
- Terraform Cloud Workspace
- A Terraform Cloud Team token allowed to
writein the Terraform Cloud Workspace created - Configure the JWT auth backend for GitLab-CI pipeline and AWS auth backend for the application
- Configure the AWS and Terraform Cloud secret backend for GitLab-CI pipeline
- Configure the Database secret backend for the application
| Name | Version |
|---|---|
| aws | ~>5.70.0 |
| gitlab | ~>17.4.0 |
| hcp | ~>0.96.0 |
| tfe | ~>0.59.0 |
| vault | ~>4.4.0 |
| Name | Version |
|---|---|
| aws | ~>5.70.0 |
| gitlab | ~>17.4.0 |
| hcp | ~>0.96.0 |
| tfe | ~>0.59.0 |
| vault | ~>4.4.0 |
No modules.
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| aws_secret_default_ttl | The default lease ttl for AWS secret engine (default: 10min) | number |
600 |
no |
| aws_secret_max_ttl | The max lease ttl for AWS secret engine (default: 15min) | number |
900 |
no |
| gitlab_domain | The domain name of your gitlab (e.g: gitlab.com) | string |
"https://gitlab.com" |
no |
| gitlab_project_branch | The pipeline project branch to authorize to auth with Vault | string |
"main" |
no |
| hcp_vault_cidr | The CIDR used in the HCP for the HashiCorp Virtual Network (HVN) | string |
"192.168.0.0/16" |
no |
| hcp_vault_tier_level | The HCP Vault tier level to use | string |
"dev" |
no |
| is_hcp_vault_public | If this value is true, Vault endpoint will be public. | bool |
true |
no |
| jwt_auth_tune_default_ttl | The tune default lease ttl for JWT auth backend (default: 10min) | string |
"10m" |
no |
| jwt_auth_tune_max_ttl | The tune max lease ttl for JWT auth backend (default: 15min) | string |
"15m" |
no |
| jwt_token_max_ttl | The token max ttl for JWT auth backend (default: 15min) | number |
900 |
no |
| project_name | Project name (ex: web) | string |
"web" |
no |
| region | AWS regions | string |
"eu-west-1" |
no |
| tfc_org_name | The name of the Terraform Cloud Organization where workspace are | any |
n/a | yes |
| vcs_id | value | any |
n/a | yes |
| Name | Description |
|---|---|
| pipeline_auth_path | The path of the Vault JWT auth backend for pipeline |
| pipeline_auth_role | The role name of the Vault JWT auth backend for pipeline |
| pipeline_path_secret | The path of the AWS secret engine for pipeline |
| pipeline_role_secret | The role name of the AWS secret engine for pipeline |
| project_gitlab_path | The Gitlab path project |
| project_path_secret | The path of the Database secret engine for project |
| project_policy_name | The policy project name who give acces for project secrets |
| project_terraform_secret_path | Terraform Cloud secret path |
| project_terraform_workspace | The Terraform workspace name in Terraform Cloud |