Features • Installation • Usage • Example • Join Discord
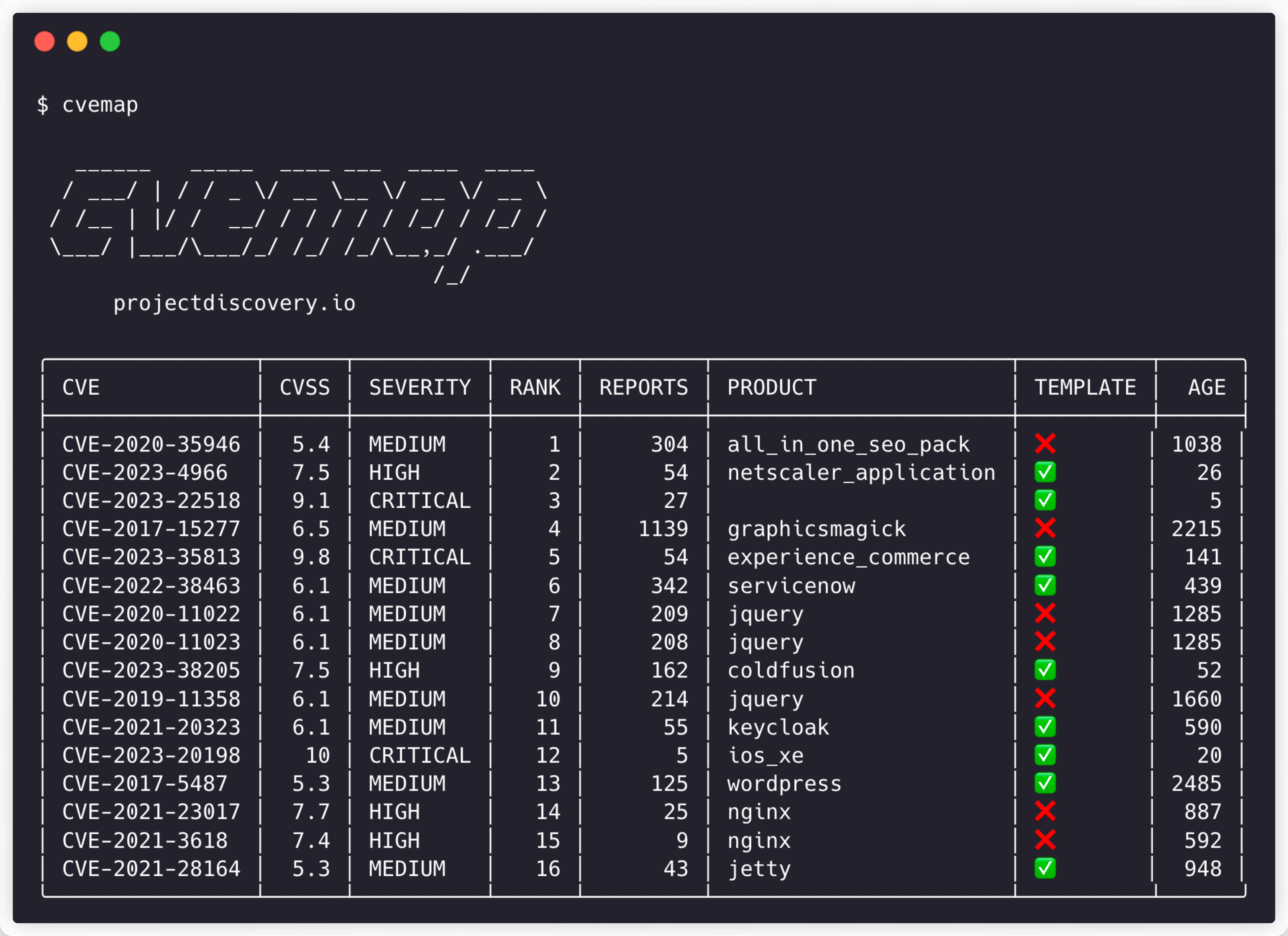
Navigate the Common Vulnerabilities and Exposures (CVE) jungle with ease using CVEMAP, a command-line interface (CLI) tool designed to provide a structured and easily navigable interface to various vulnerability databases.
- CVE Dataset Search & Query
- CVE to EPSS Mapping
- CVE to KEV Mapping
- CVE to CPE Mapping
- CVE to GitHub POCs Mapping
- CVE to Nuclei Template Mapping
- CVE to HackerOne report Mapping
- Customizable Filters on CVE data
- STDIN Input / JSONL Output
cvemap requires Go 1.21 to install successfully. To install, just run the below command or download pre-compiled binary from release page.
go install github.com/projectdiscovery/cvemap/cmd/cvemap@latestcvemap -hThis will display help for the tool. Here are all the switches it supports.
Usage:
cvemap [flags]
Flags:
CONFIG:
-auth configure projectdiscovery cloud (pdcp) api key
OPTIONS:
-id string[] cve to list for given id
-v, -vendor string[] cve to list for given vendor
-p, -product string[] cve to list for given product
-eproduct string[] cves to exclude based on products
-s, -severity string[] cve to list for given severity
-cs, -cvss-score string[] cve to list for given cvss score
-c, -cpe string cve to list for given cpe
-es, -epss-score string cve to list for given epss score
-ep, -epss-percentile string[] cve to list for given epss percentile
-age string cve to list published by given age in days
-a, -assignee string[] cve to list for given publisher assignee
-vs, -vstatus value cve to list for given vulnerability status in cli output. supported: unknown, new, confirmed, unconfirmed, modified, rejected
UPDATE:
-up, -update update cvemap to latest version
-duc, -disable-update-check disable automatic cvemap update check
FILTER:
-q, -search string search in cve data
-k, -kev display cves marked as exploitable vulnerabilities by cisa (default true)
-t, -template display cves that has public nuclei templates (default true)
-poc display cves that has public published poc (default true)
-h1, -hackerone display cves reported on hackerone (default true)
OUTPUT:
-f, -field value fields to display in cli output. supported: age, kev, template, poc, cwe, epss, assignee, product, vendor, vstatus
-fe, -exclude value fields to exclude from cli output. supported: age, kev, template, poc, cwe, epss, assignee, product, vendor, vstatus
-lsi, -list-id list only the cve ids in the output
-l, -limit int limit the number of results to display (default 50)
-offset int offset the results to display
-j, -json return output in json format
-epk, -enable-page-keys enable page keys to navigate results
DEBUG:
-version Version
-silent Silent
-verbose VerboseCVEMap CLI is built on top of the CVEMap API that requires API Token from ProjectDiscovery Cloud Platform that can be configured using environment variable named PDCP_API_KEY or using interactive -auth option as shown below.
export PDCP_API_KEY=*************cvemap -auth
______ _____ ____ ___ ____ ____
/ ___/ | / / _ \/ __ \__ \/ __ \/ __ \
/ /__ | |/ / __/ / / / / / /_/ / /_/ /
\___/ |___/\___/_/ /_/ /_/\__,_/ .___/
/_/
projectdiscovery.io
[INF] Get your free api key by signing up at https://cloud.projectdiscovery.io
[*] Enter PDCP API Key (exit to abort): *************
[INF] Successfully logged in as (@user)For details about running cvemap, see https://docs.projectdiscovery.io/tools/cvemap/running.
- CVE dataset gets updated in every 6 hours.
- National Vulnerability Database (NVD): Comprehensive CVE vulnerability data.
- Known Exploited Vulnerabilities Catalog (KEV): Exploited vulnerabilities catalog.
- Exploit Prediction Scoring System (EPSS): Exploit prediction scores.
- HackerOne: CVE discoveries disclosure.
- Nuclei Templates: Vulnerability validation templates.
- Live-Hack-CVE / PoC-in-GitHub GitHub Repository: Vulnerability PoCs references.
cvemap is made with ❤️ by the projectdiscovery team and distributed under MIT License.