This opa implementation need opa server to be set up. See https://github.com/mhseptiadi/opa
Please refer to https://minikube.sigs.k8s.io/docs/start/
For linux & mac:
eval $(minikube docker-env)For windows using powershell:
& minikube -p minikube docker-env --shell powershell | Invoke-Expressiondocker build -f Dockerfile -t opa-py:latest .Run these one by one to create ssl certificate
openssl genrsa -des3 -out server.key 2048openssl req -new -key server.key -out server.csrcp server.key server.key.orgopenssl rsa -in server.key.org -out server.keyopenssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crtWe only need server.crt and server.key to configmap
kubectl create configmap server-crt --from-file ./server.crtkubectl create configmap server-key --from-file ./server.keykubectl apply -f deploy.yamlminikube service opa-py --url --httpsThe return of minikube url will be something like {host}:{port}, for example https://127.0.0.1:55738
. Then we can use this for our testing.
There are 3 users for this testing:
[
{
"email": "user@user.com",
"name": "user",
"password": "admin",
"roles": [
"user"
]
},
{
"email": "admin@admin.com",
"name": "admin",
"password": "admin",
"roles": [
"admin"
]
},
{
"email": "other@other.com",
"name": "other",
"password": "other",
"roles": [
]
}
]There are 3 api endpoints for this testing:
- Login API
- Get Users (admin and user role)
- Create Users (only admin role)
Login admin (admin@admin.com) that has crud privilege on users endpoint
curl --location 'https://127.0.0.1:55738/api/login' \
--header 'Content-Type: application/json' \
--data-raw '{
"email": "admin@admin.com",
"password": "admin"
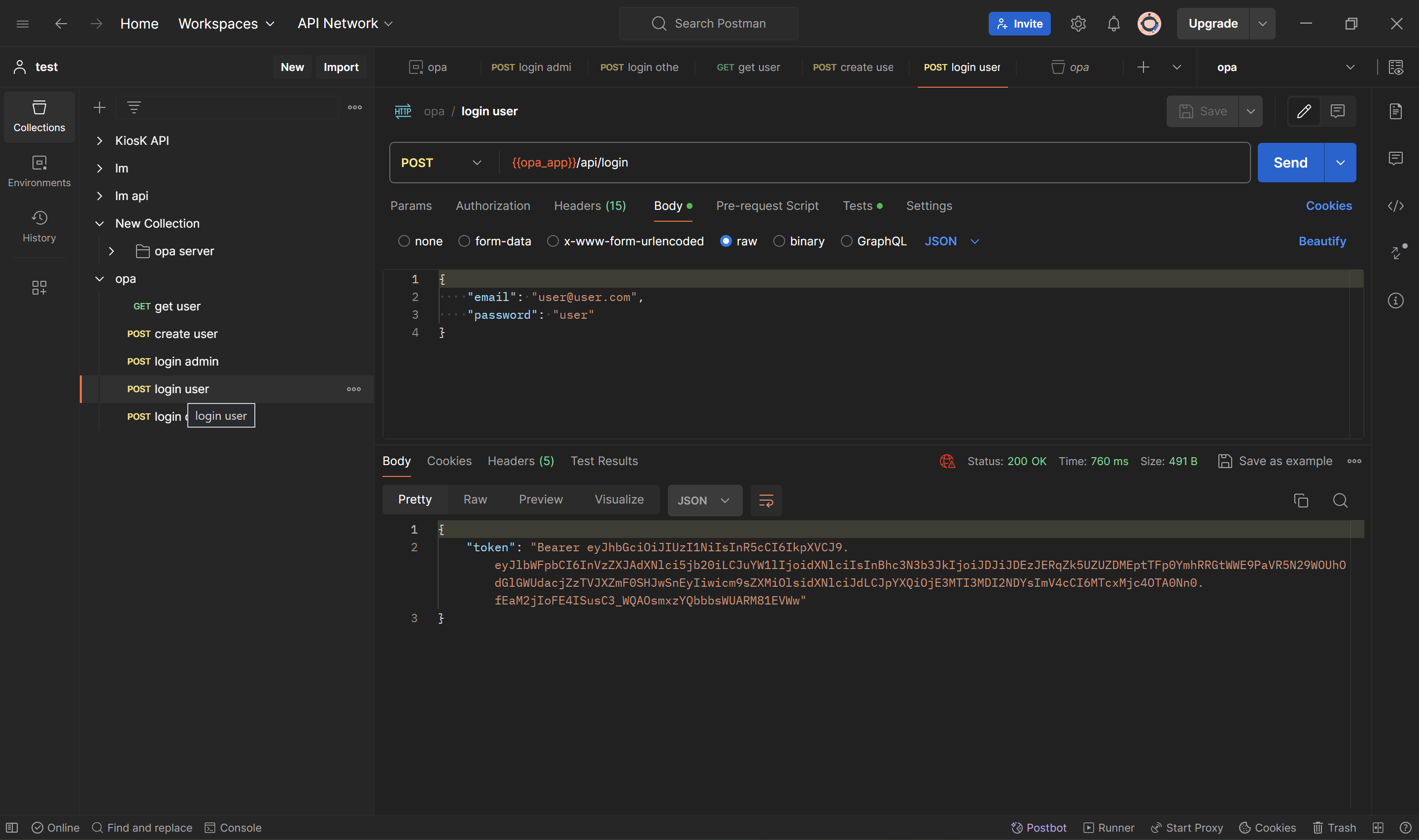
}'Login user (user@user.com) that has only read users endpoint
curl --location 'https://127.0.0.1:55738/api/login' \
--header 'Content-Type: application/json' \
--data-raw '{
"email": "user@user.com",
"password": "user"
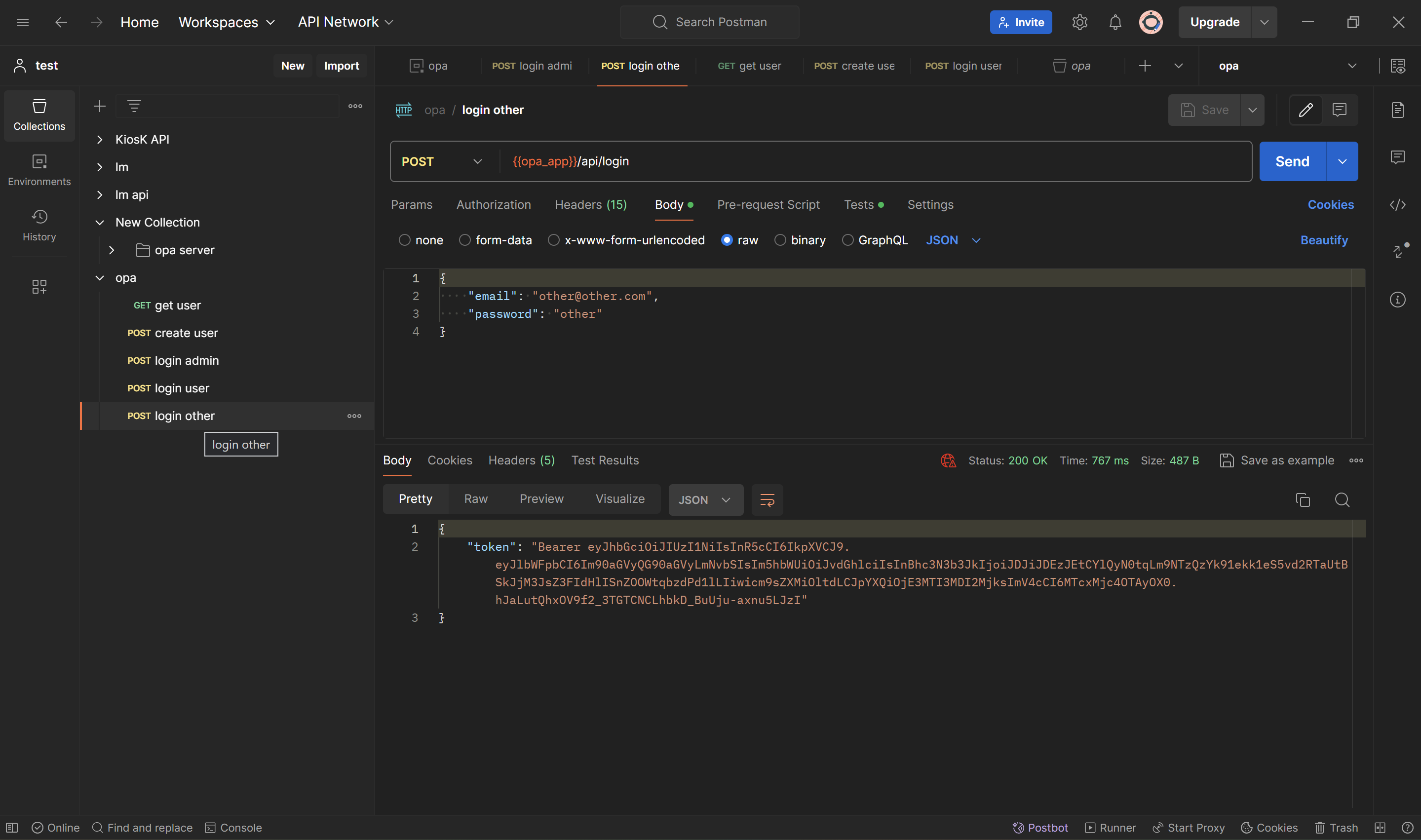
}'Login other (other@other.com) that does not have any privilege
curl --location 'https://127.0.0.1:55738/api/login' \
--header 'Content-Type: application/json' \
--data-raw '{
"email": "other@other.com",
"password": "other"
}'From the login api above you will get authorization bearer. Copy the bearer and use it on get users api.
curl --location 'https://127.0.0.1:55738/api/users' \
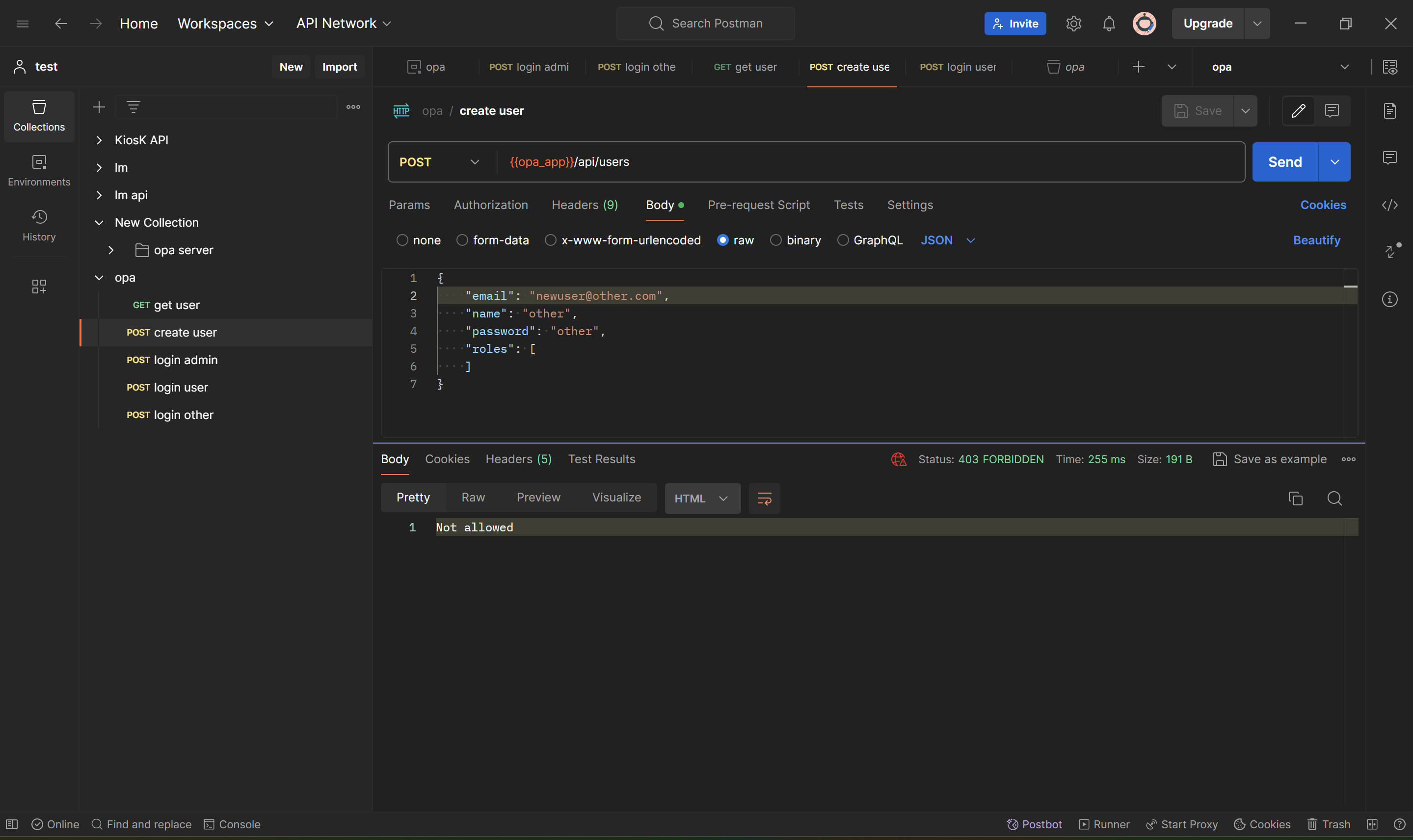
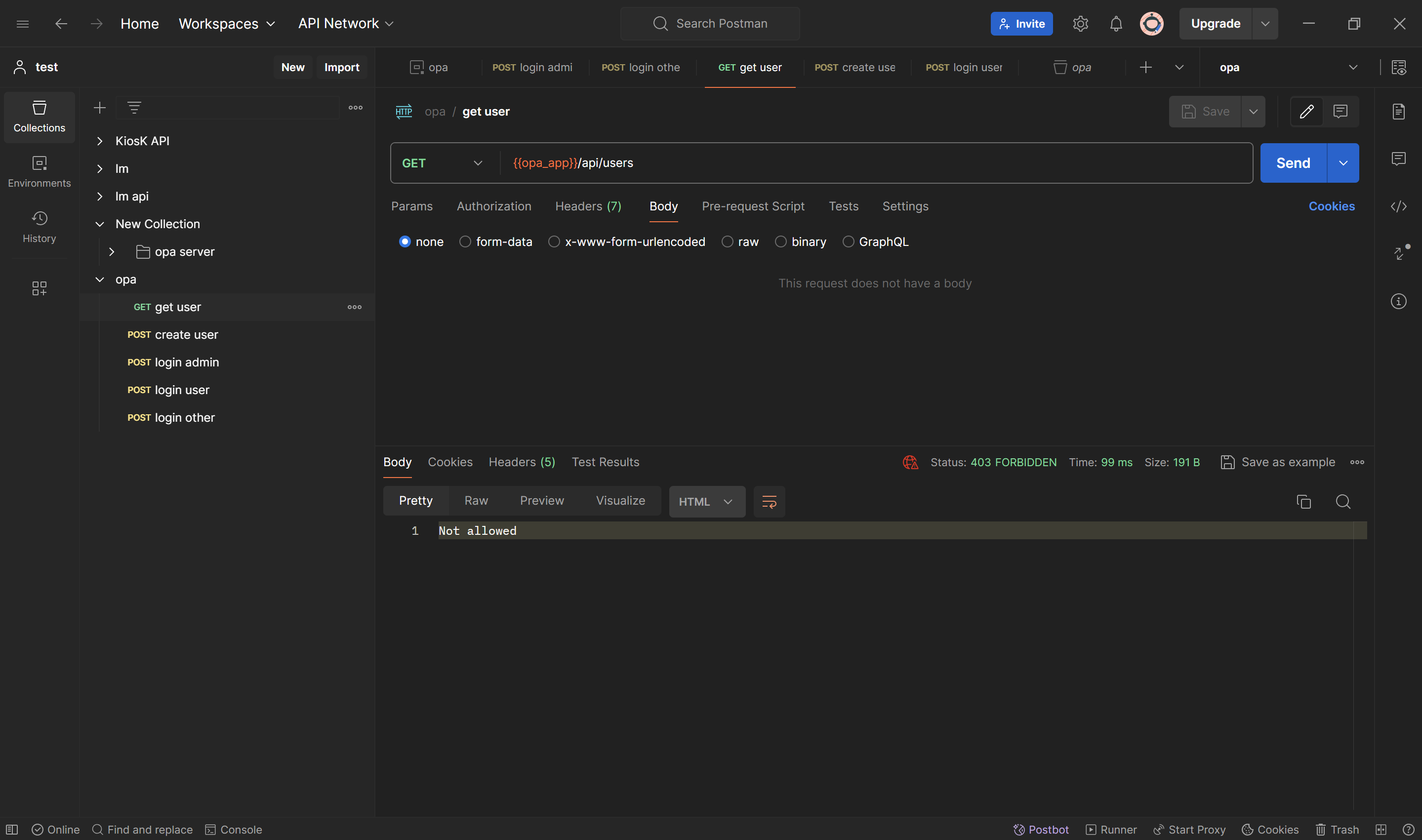
--header 'Authorization: {{bearer}}'Both admin and user can access this endpoint because they have role admin and user. The last user other cannot access this endpoint because he doesn't have access.
The same like before, copy the bearer from login and use it in this api.
curl --location 'https://127.0.0.1:55738/api/users' \
--header 'Authorization: {{bearer}}' \
--header 'Content-Type: application/json' \
--data-raw '{
"email": "user2@user2.com",
"name": "user2",
"password": "user2",
"roles": [
"user2"
]
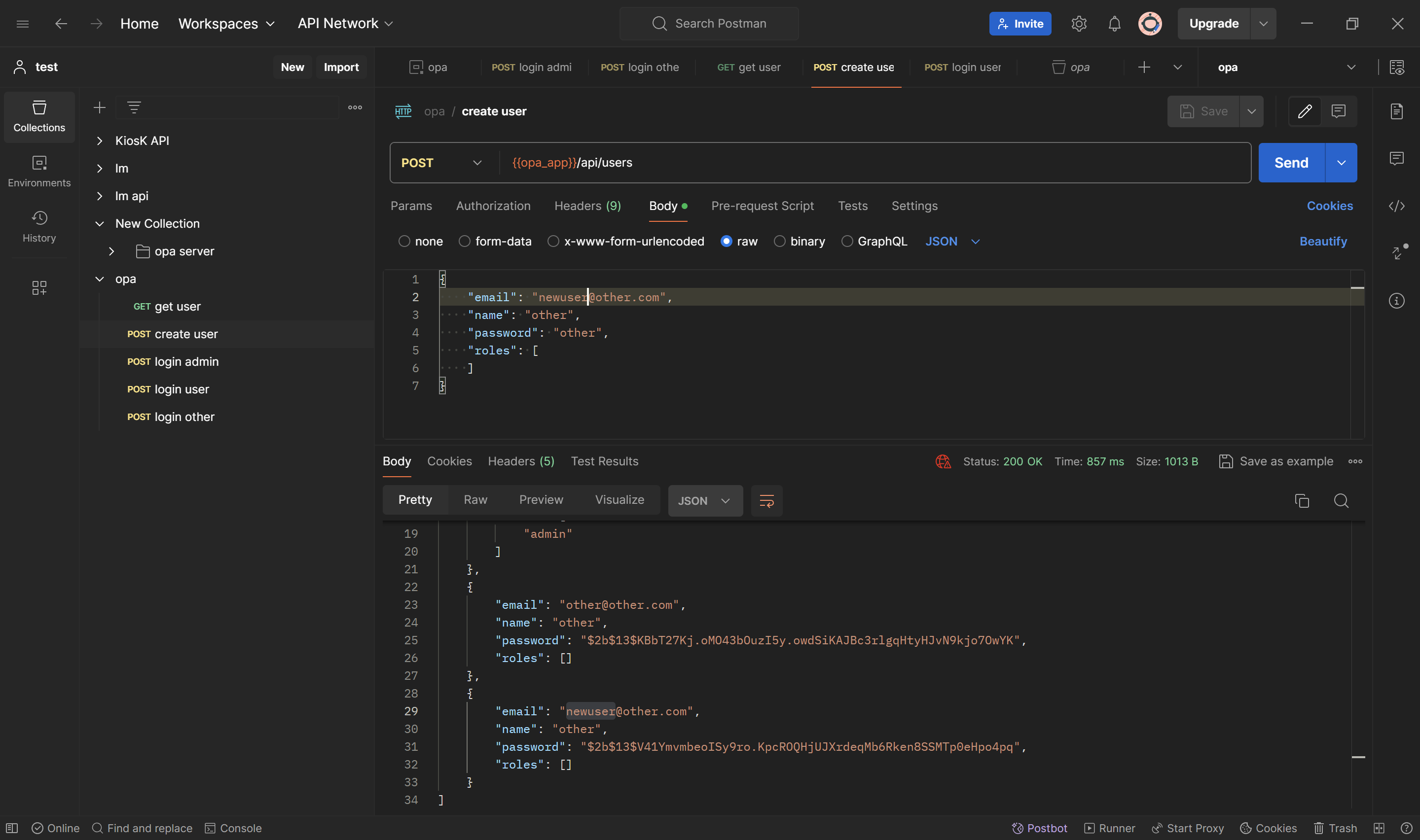
}'In this create user api, only admin can have access.
For testing purpose, you can import opa.postman_collection.json postman. You need to add environment as login will save bearer to environment.
- First login as admin
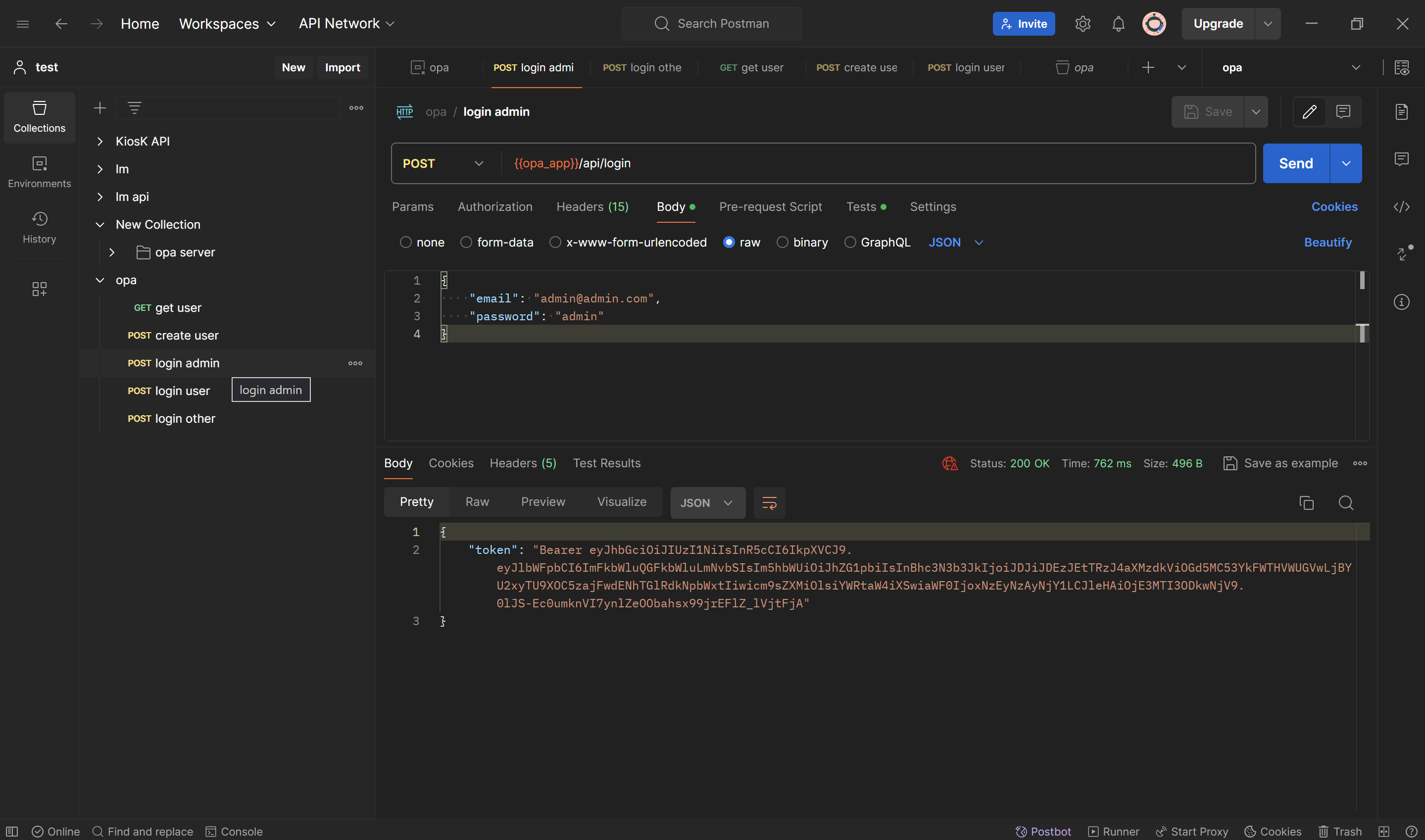
- Then try get users endpoint, you will have access on it
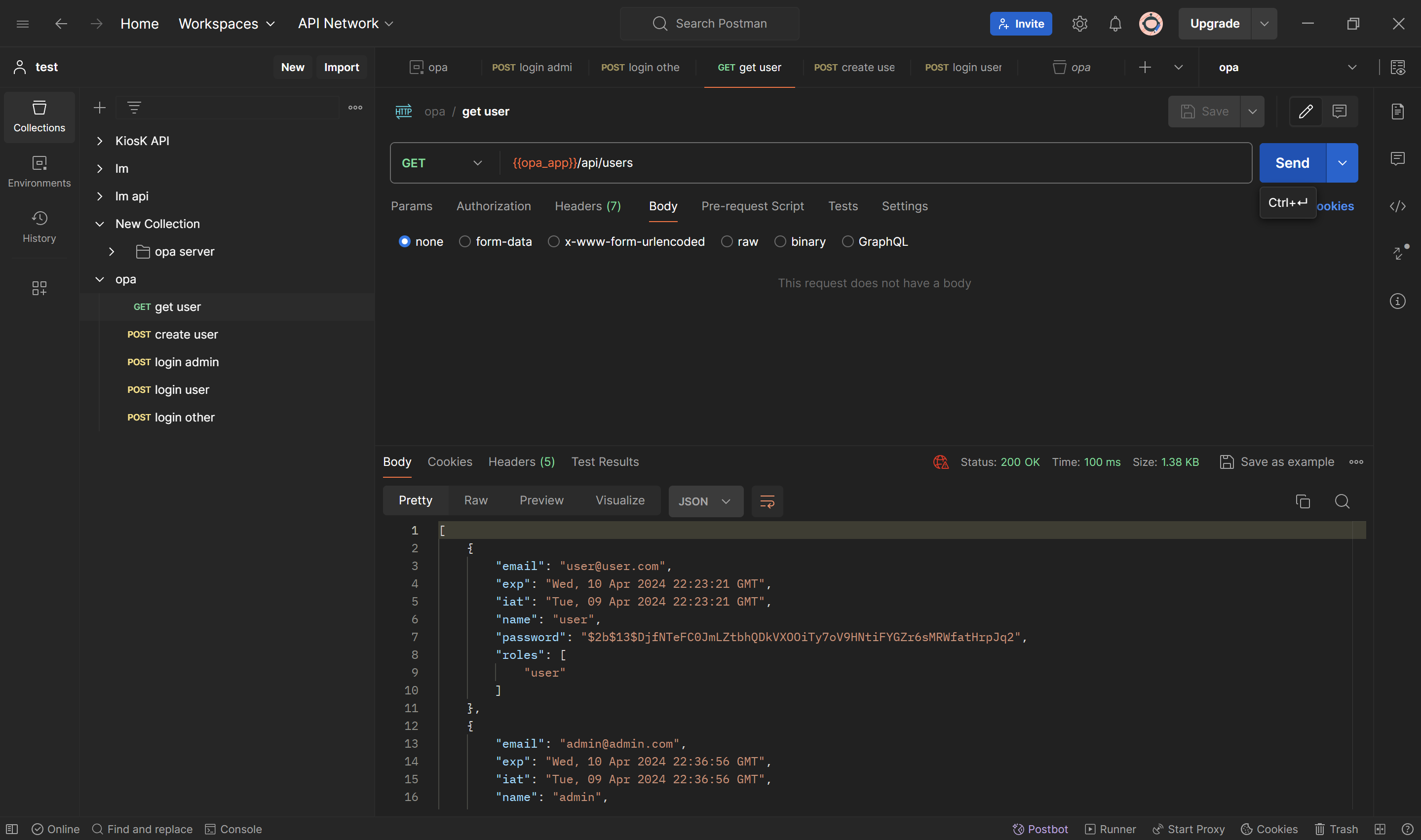
- Then try create users endpoint, you still have access