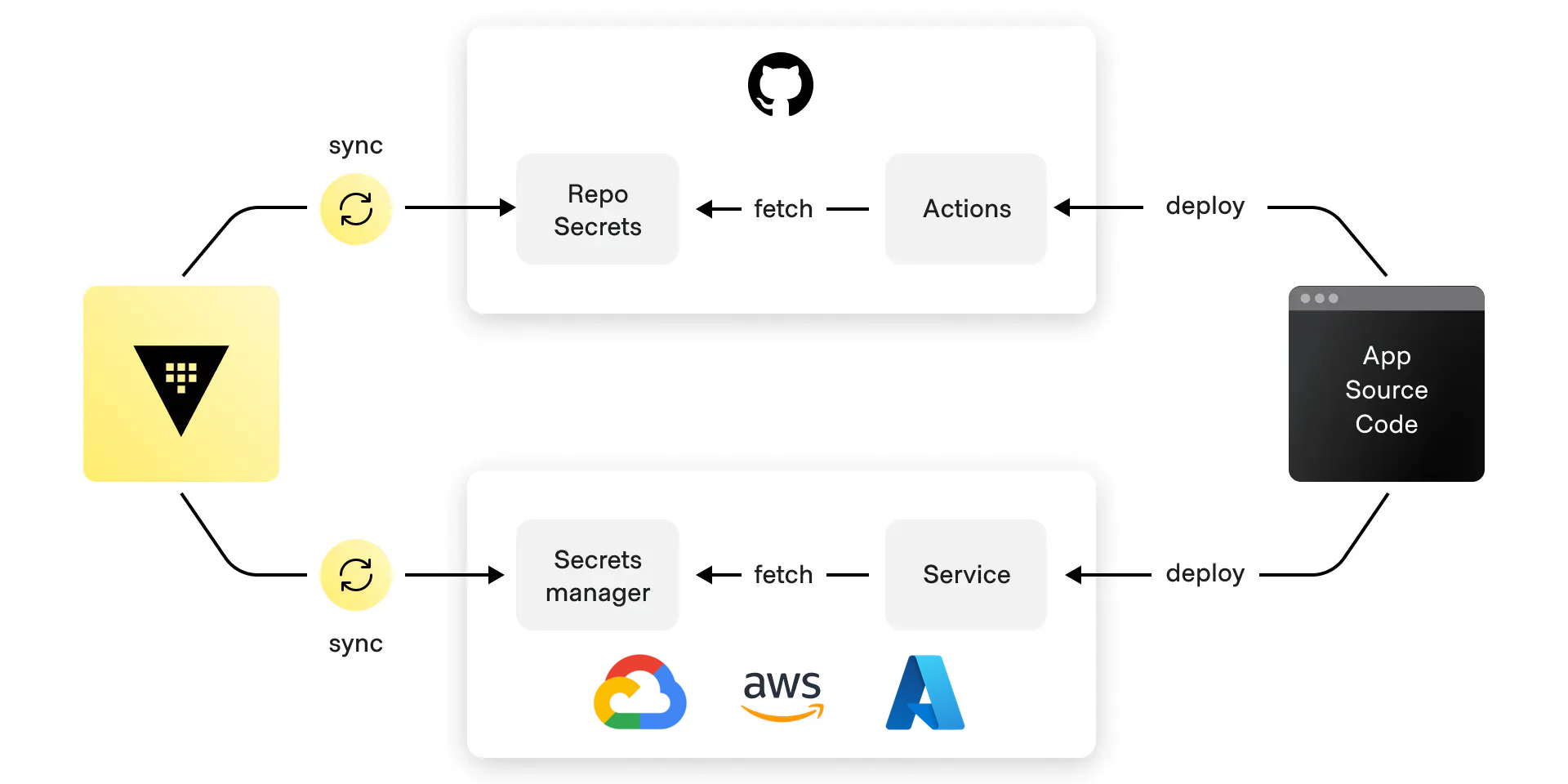
Secrets Sync allows you to automatically sync secrets from Vault Enterprise to a variety of third party platforms including AWS, Azure, GCP, GitHub, and Vercel.
cd vault-secrets-sync-demo/tf
# add `vault_license` to .auto.tfvars
terraform apply
export VAULT_ADDR=$(terraform output -raw vault_addr)
cd ..vault operator init -key-shares=1 -key-threshold=1 -format=json > init.json
vault operator unseal $(cat init.json | jq -r .unseal_keys_hex[0])
export VAULT_TOKEN=$(cat init.json| jq -r .root_token)vault write -f sys/activation-flags/secrets-sync/activate
vault secrets enable -version=2 kvvault kv put kv/path/to/secret \
username="foo" \
password=$RANDOM \
uuid=$(uuidgen)Perform this step from your local machine.
./scripts/aws-to-vault.sh# default template
vault write sys/sync/destinations/aws-sm/demo-use2 \
role_arn="arn:aws:iam::$AWS_ACCOUNT_ID:role/demo-secrets-sync" \
region="us-east-2"
# custom template (be cautious of overwrites)
# https://developer.hashicorp.com/vault/docs/sync#name-template
vault write sys/sync/destinations/aws-sm/demo-use2-templated \
role_arn="arn:aws:iam::$AWS_ACCOUNT_ID:role/demo-secrets-sync" \
region="us-east-2" \
secret_name_template="vault/{{ if .NamespacePath }}{{ .NamespacePath }}/{{ else }}{{ end }}{{ .MountPath }}/{{ .SecretPath }}"vault write sys/sync/destinations/aws-sm/demo-use2/associations/set \
mount="kv" \
secret_name="path/to/secret"Perform this step from your local machine.
./scripts/vault-to-aws.shView the replicated secrets in AWS Secrets Manager
Perform the modifications below in Vault; then view the changes replicated in AWS Secrets Manager
vault kv patch kv/path/to/secret foo="bar" hello="world"View the secrets and secrets sync settings within the Vault UI.
./scripts/cleanup.sh
cd tf/
terraform destroy