Trivy (pronunciation) is a comprehensive and versatile security scanner. Trivy has scanners that look for security issues, and targets where it can find those issues.
Targets (what Trivy can scan):
- Container Image
- Filesystem
- Git Repository (remote)
- Virtual Machine Image
- Kubernetes
- AWS
Scanners (what Trivy can find there):
- OS packages and software dependencies in use (SBOM)
- Known vulnerabilities (CVEs)
- IaC issues and misconfigurations
- Sensitive information and secrets
- Software licenses
To learn more, go to the Trivy homepage for feature highlights, or to the Documentation site for detailed information.
Trivy is available in most common distribution channels. The full list of installation options is available in the Installation page. Here are a few popular examples:
brew install trivydocker run aquasec/trivy- Download binary from https://github.com/aquasecurity/trivy/releases/latest/
- See Installation for more
Trivy is integrated with many popular platforms and applications. The complete list of integrations is available in the Ecosystem page. Here are a few popular examples:
- GitHub Actions
- Kubernetes operator
- VS Code plugin
- See Ecosystem for more
trivy <target> [--scanners <scanner1,scanner2>] <subject>Examples:
trivy image python:3.4-alpineResult
trivy-image.mov
trivy fs --scanners vuln,secret,config myproject/Result
trivy-fs.mov
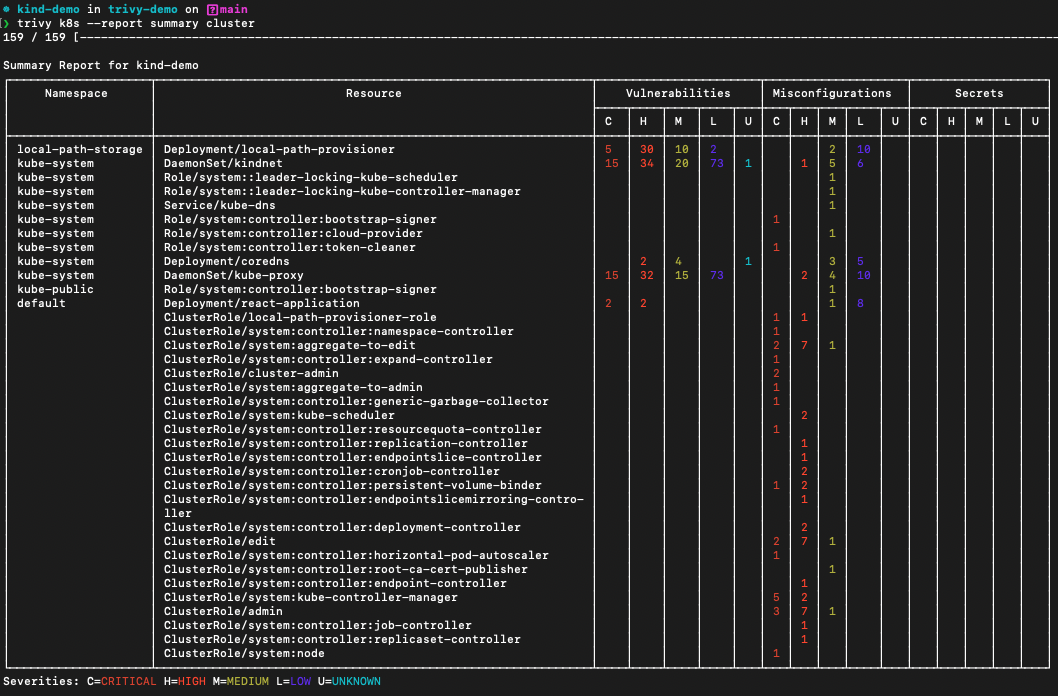
trivy k8s --report summary clustertri is pronounced like trigger, vy is pronounced like envy.
Trivy is an Aqua Security open source project.
Learn about our open source work and portfolio here.
Contact us about any matter by opening a GitHub Discussion here