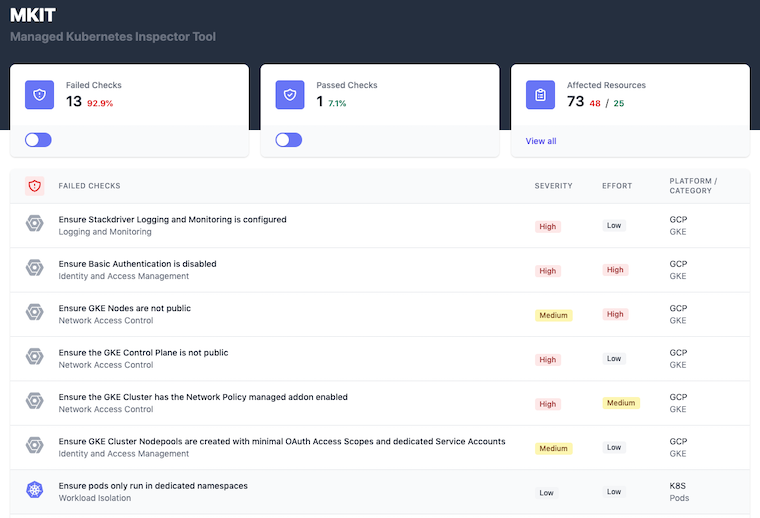
MKIT is a "Managed Kubernetes Inspection Tool" that leverages FOSS tools to query and validate several common security-related configuration settings of managed Kubernetes cluster objects and the workloads/resources running inside the cluster. It runs entirely from a local docker container and queries your cloud provider's APIs and the Kubernetes API to determine if certain misconfigurations are found. The same docker container then launches a web UI to view and navigate the results on localhost:8000.
MKIT provides security-minded Kubernetes cluster administrators with a quick way to assess several common misconfigurations in their Kubernetes environment.
- Azure Kubernetes Service - "AKS"
- Amazon Elastic Kubernetes Service - "EKS"
- Google Kubernetes Engine - "GKE"
You can run the in-cluster Kubernetes checks by themselves. See the steps for targeting k8s instead of aks, eks, or gke.
MKIT makes use of Chef Inspec-formatted profiles, and they are located at the locations below:
- https://github.com/darkbitio/inspec-profile-aks
- https://github.com/darkbitio/inspec-profile-eks
- https://github.com/darkbitio/inspec-profile-gke
- https://github.com/darkbitio/inspec-profile-k8s
When running make with various parameters, the MKIT tool is leveraging your cloud credentials to query the provider's APIs for the specific cluster and validating its configuration. It then connects to the cluster directly via the Kubernetes API server to validate several configuration items inside the cluster. Finally, it combines those results into a format viewable by the mkit-ui launched inside the mkit container listening on localhost:8000 for viewing.
All results are stored inside the container for the life of that MKIT run, and they are not uploaded or shared in any way.
- Clone this repository to your Linux/OSX/WSL2 system.
- See the section on building the image manually, if desired.
- Ensure you have the permissions to
get/list/describeyour cluster via the native APIs and you havecluster-adminor theviewClusterRolebound to your current account. - Run the tool for your use case:
- AKS:
- Export your Azure credentials as local environment variables (
AZURE_CLIENT_ID,AZURE_TENANT_ID,AZURE_CLIENT_SECRET,AZURE_SUBSCRIPTION_ID) make run-aks resourcegroup=myResourceGroup clustername=my-aks-cluster-name
- Export your Azure credentials as local environment variables (
- EKS:
make run-eks awsregion=us-east-1 clustername=my-eks-cluster-name
- GKE:
- Run
gcloud auth application-default login make run-gke project_id=my-project-id location=us-central1 clustername=my-gke-cluster-name
- Run
- K8s (Any Kubernetes Cluster):
- Ensure the current context is set in your
KUBECONFIG(~/.kube/config) file - Run
kubectl get nodesto confirm access and the proper cluster is being targeted. make run-k8s
- Ensure the current context is set in your
- AKS:
- Visit localhost:8000 to view the results of the scan.
Note: the K8s profile checks are automatically run by the AKS, EKS, and GKE invocations. You would only need to run the K8s checks separately if you don't have access to or want to review the cluster and node configurations.
$ export AZURE_CLIENT_ID="<client id>"
$ export AZURE_TENANT_ID="<tenant id>"
$ export AZURE_CLIENT_SECRET="<client secret>"
$ export AZURE_SUBSCRIPTION_ID="<subscription id>"
$ make run-aks resourcegroup=myResourceGroup clustername=aks1
Running in darkbitio/mkit:latest: /home/node/audit/aks.sh
Generating results...[2020-03-26T22:33:45+00:00] WARN: Overwriting resource azurerm_resource. To reference a specific version of azurerm_resource use the resource() method
[2020-03-26T22:33:45+00:00] WARN: Overwriting resource azurerm_aks_cluster. To reference a specific version of azurerm_aks_cluster use the resource() method
done.
Merged "aks1" as current context in /home/node/.kube/config
Generating results...done.
Visit http://localhost:8000 to view the results
yarn run v1.22.0
$ node app.js
MKIT Running - browse to http://localhost:8000
$ make run-eks awsregion=us-east-1 clustername=eks1
Generating results...done.
Added new context arn:aws:eks:us-east-1:1234567890:cluster/eks1 to /home/node/.kube/config
Generating results...done.
Visit http://localhost:8000 to view the results
yarn run v1.22.0
$ node app.js
MKIT Running - browse to http://localhost:8000
$ make run-gke project_id=my-gke-project location=us-central1 clustername=my-gke-cluster
Running in darkbitio/mkit:latest: /home/node/audit/gke.sh
Generating results...done.
Fetching cluster endpoint and auth data.
kubeconfig entry generated for my-gke-cluster.
Generating results...done.
Visit http://localhost:8000 to view the results
yarn run v1.22.0
$ node app.js
MKIT Running - browse to http://localhost:8000
$ make run-k8s
Running in darkbitio/mkit:latest: /home/node/audit/k8s.sh
Generating results...done.
Visit http://localhost:8000 to view the results
yarn run v1.22.0
$ node app.js
MKIT Running - browse to http://localhost:8000
- Clone this repo
- Modify the
Makefileto name the image as desired - Run
make buildto build the container from scratch
- Fork the desired profile repository
- Modify the release tag and release URL to point to your new repository/release
- Follow the steps in the previous section to build a custom container using your new profile