@vgs/vgs-satellite
VGS Offline integration/debugging application.
- python =>3.8.0 (python --version)
- npm =>6.14.0 (npm --version)
VGS Satellite is an application that can ease your integration with Very Good Security to achieve Zero Data security
VGS Satellite provides:
- Demo VGS Vault capabilities
- Redact/reveal functinality
- JSON payload request/response transformer
- Route configuration generator according to specific request
- Route configuration editor
- Logging
- Man-in-the-middle proxy functionality (request incertept/replay/edit/etc)
This application gives you an ability to run requests with your service and transform them into suitable VGS route configuration without any need to sign up.
Note: VGS Satellite is in beta right now and is being run in electron development mode. Going forward VGS Satellite would be a bundled up executable.
-
Clone sources
git clone git@github.com:verygoodsecurity/vgs-satellite.git && cd vgs-satellite
-
Install dependencies
npm ci
-
Run application...
npm run start:app
Note: This would run application in electron locally. If you need to run in browser use
npm start
- Pull the image
docker pull verygood/satellite
- Start a container
Note: You can use any directory you like to mount
docker run --rm -v $HOME/.vgs-satellite/:/data -p 8089:8089 -p 9098:9098 -p 9099:9099 -p 1234:1234 verygood/satellite/datavolume - just make sure the directory exists before you start a container
When started VGS Satellite runs 2 proxies:
- reverse proxy (default port: 9098)
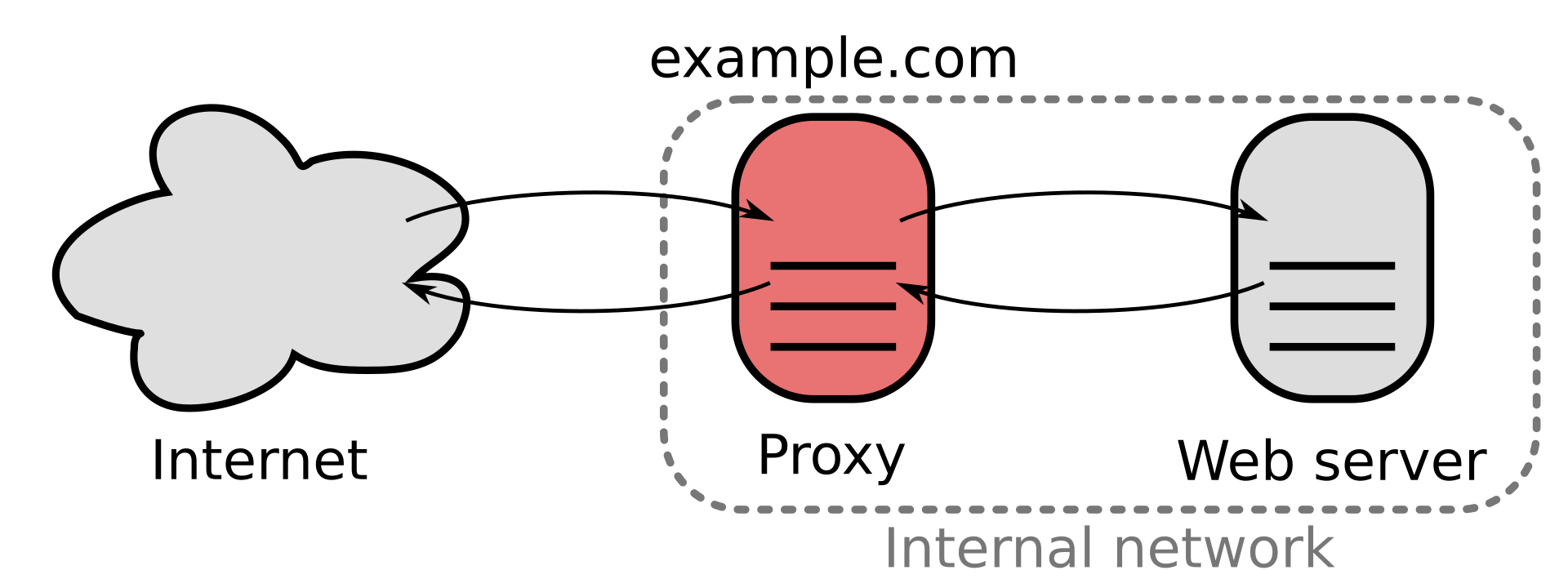
Note: Reverse proxy is started with dummy upstream, and can be used only when at least 1 inbound route is created
Satellite support following parameters:
web_server_port- ports that is used by backend webservice (default: 8089)reverse_proxy_port- reverse proxy port (default: 9098)forward_proxy_port- forward proxy port (default: 9099)
You can override default values using configuration file. Default location for config file is ~/.vgs-satellite/config.yml
You can find config file example at config.yml-example
You can also override them using command line arguments:
--web-server-port- ports that is used by backend webservice--reverse-proxy-port- reverse proxy port--forward-proxy-port- forward proxy port--config-path- path for config file.
Overriding priority from highest priority to lowest is:
Command argument -> Configuration file -> Default value
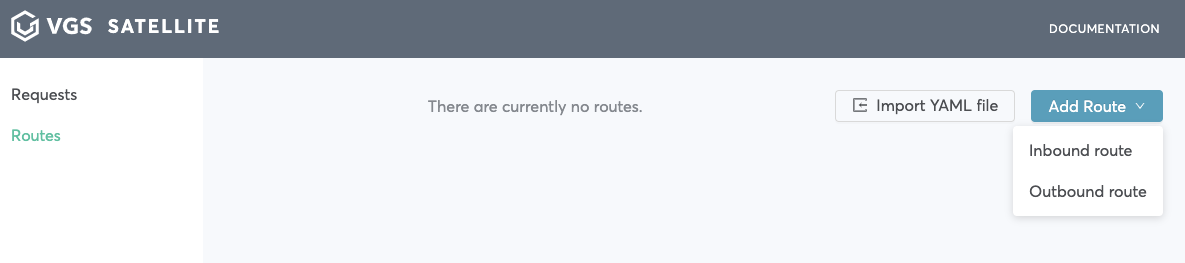
Lets use inbound route for redact scenario
-
Navigate to routes page and click
Add route->Inbound route -
Add upstream, for example
interactive-form.herokuapp.comand clickSave -
Visit
localhost:9098and make request you want to secure or make request directly tolocalhost:9098
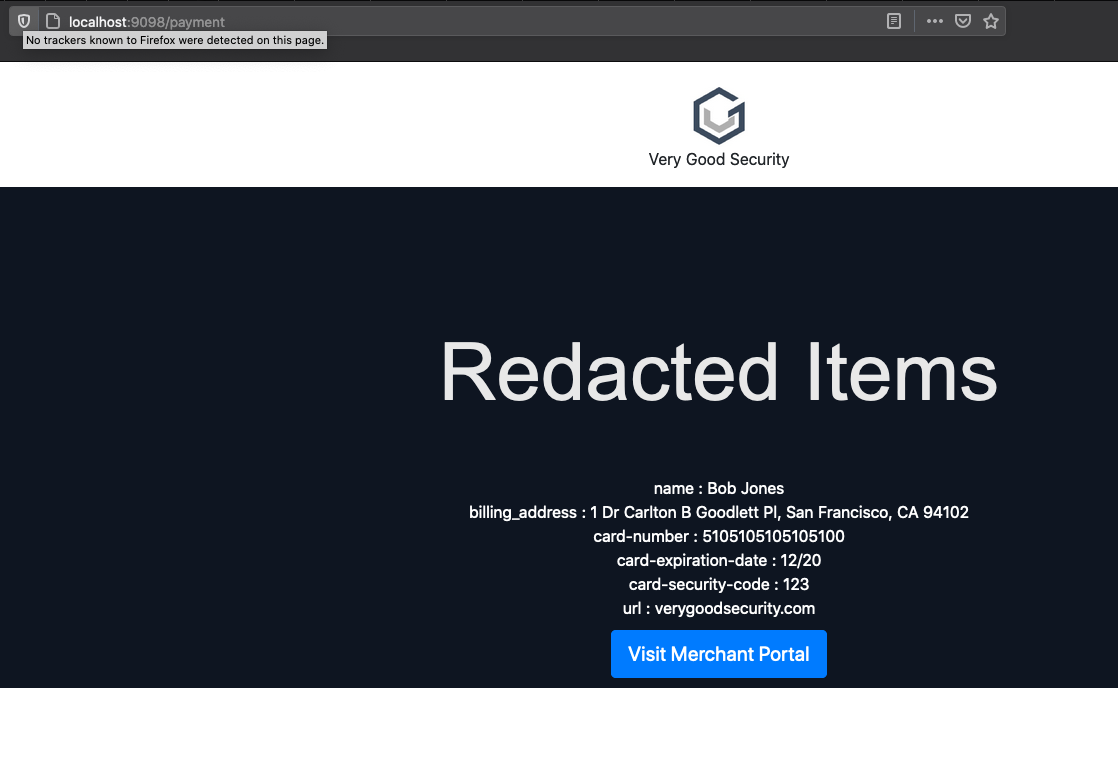
Note: If you are using interactive-form.herokuapp.com as an upstream, click Fill, then Place Order
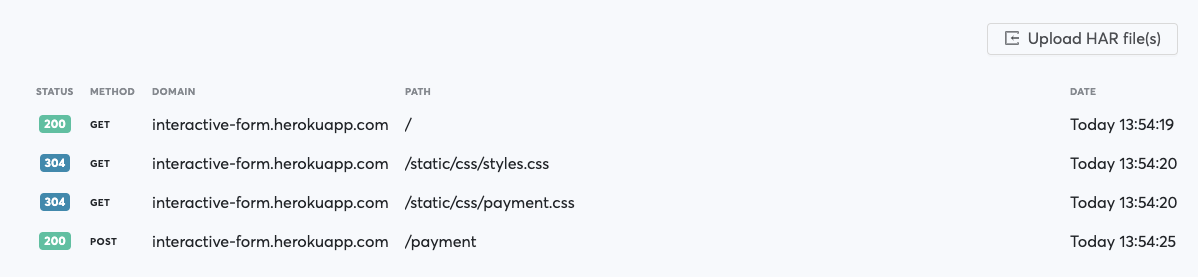
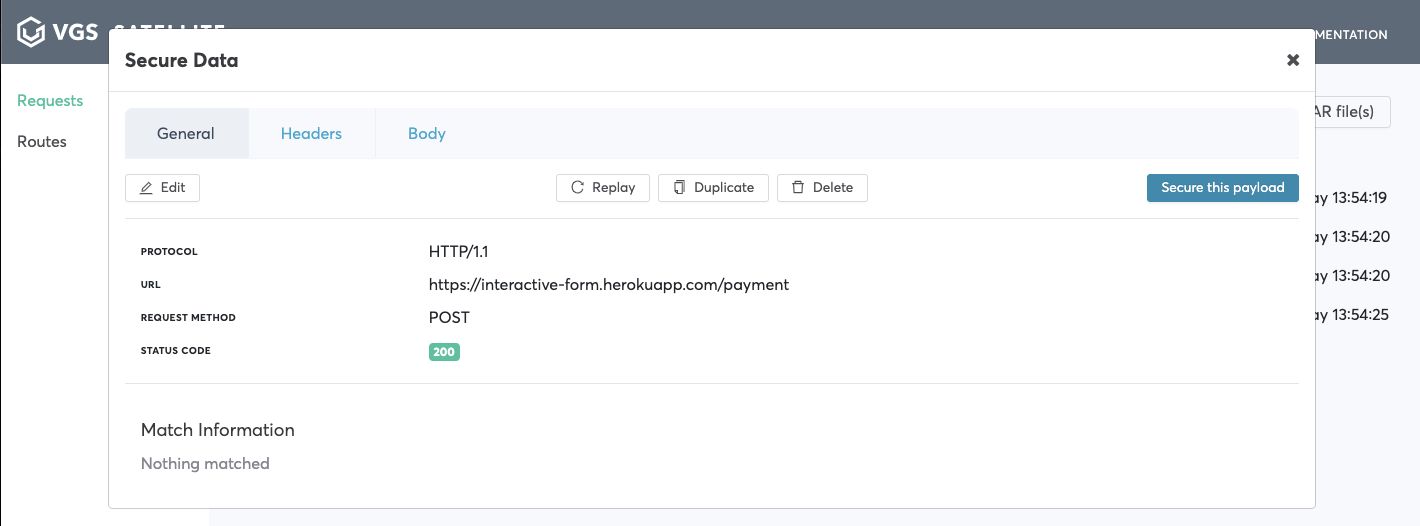
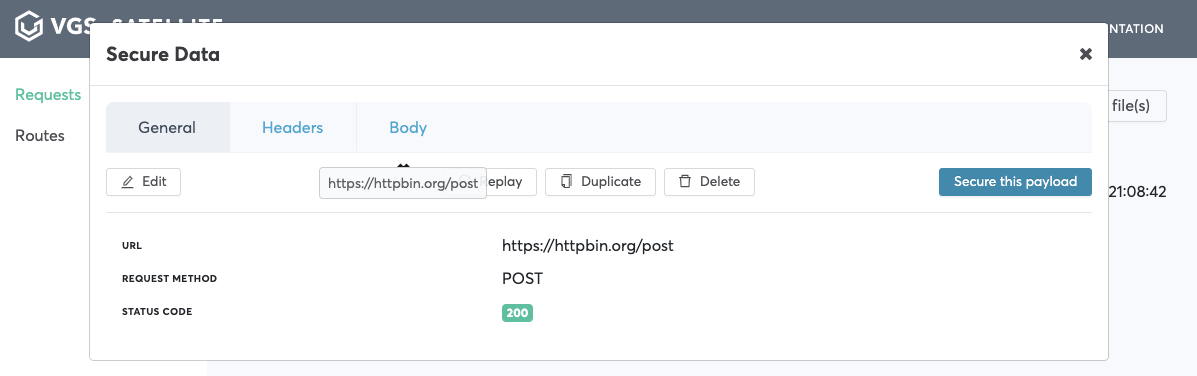
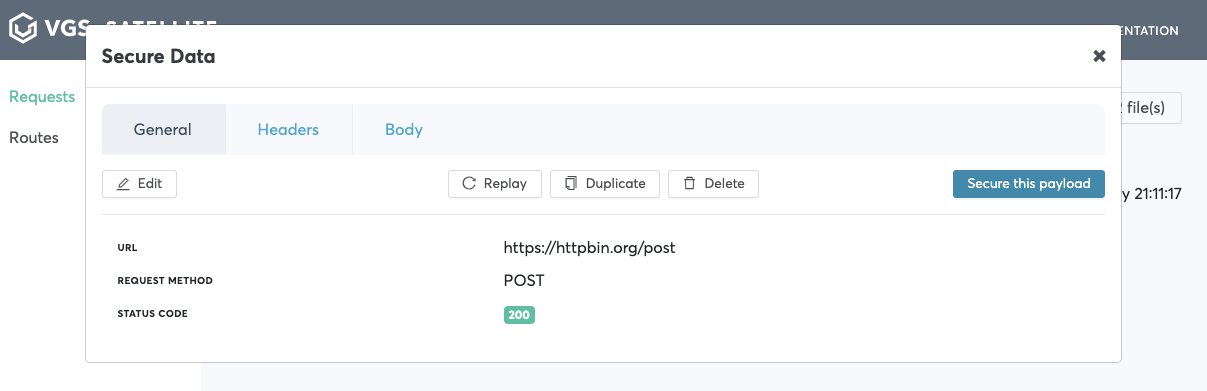
- Find your request in requests list and click it
Note: For our example we take /payment request
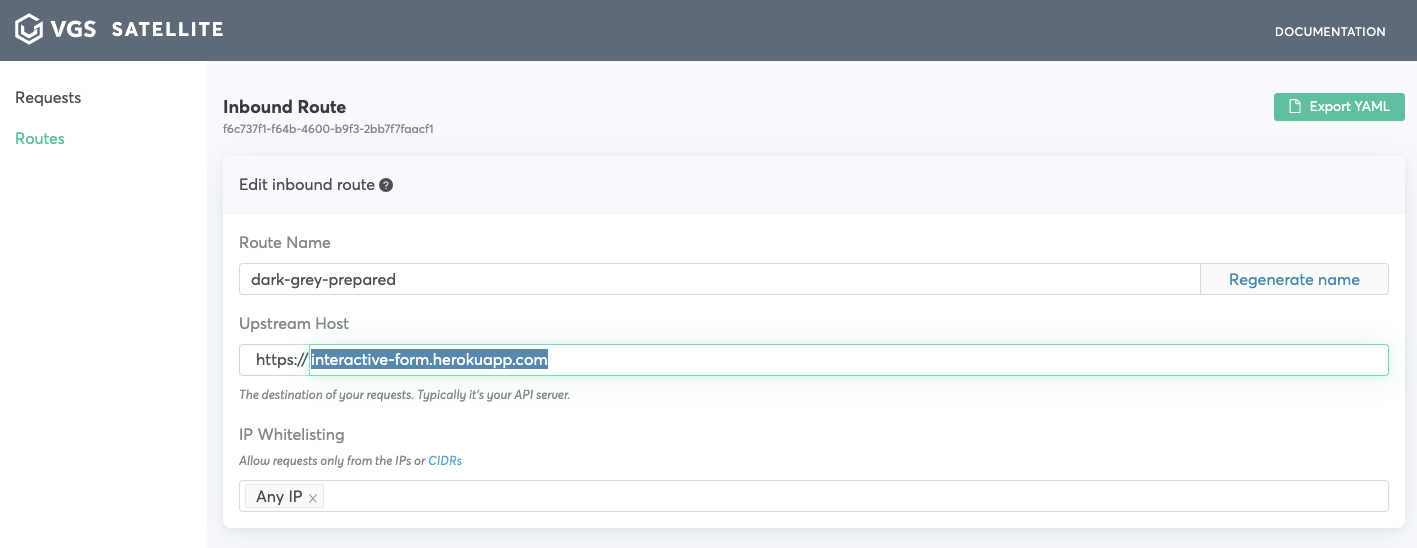
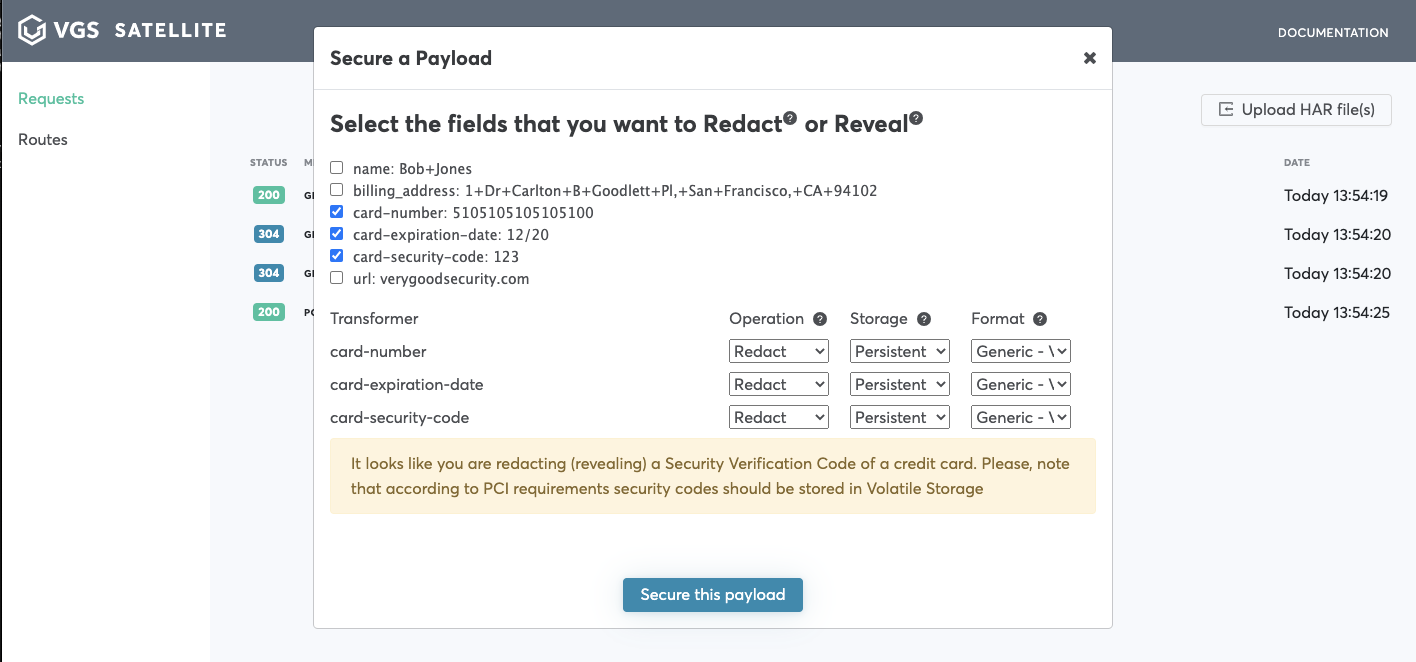
- Pick field that needs to be secured click
Secure this payload->View route configuration->Save inbound route
-
Visit routes page and delete route created on step #2
-
Choose your request in requests list and click
ReplayNavigate to request one more time and click
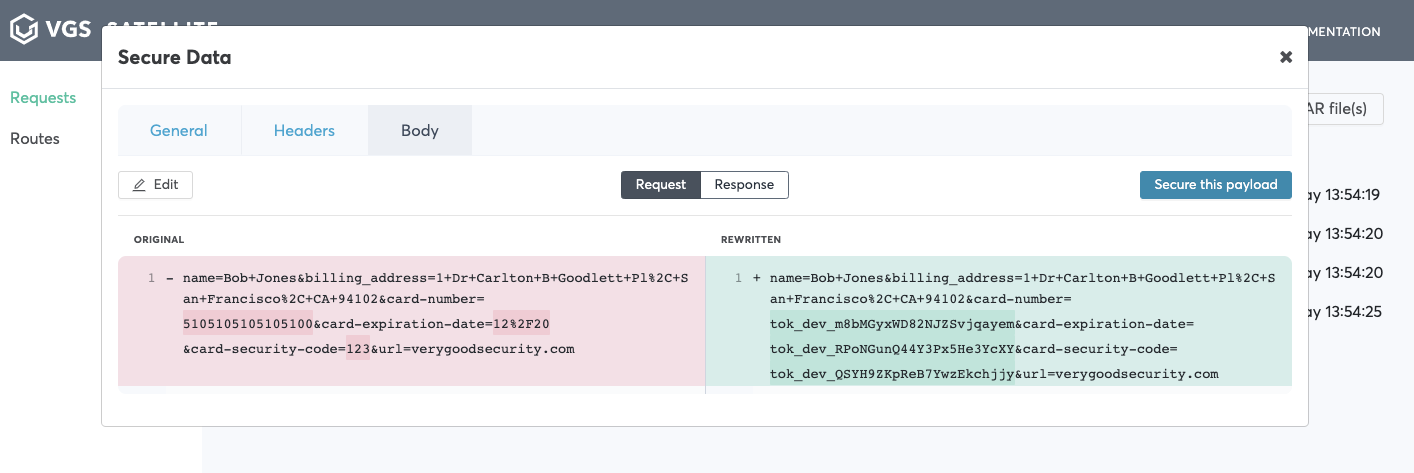
Body.
Your payload has been secured!
Lets use outbound route to reveal previously redacted payload scenario
This scenario will help you generate an outbound route using your request, made to a forward proxy
-
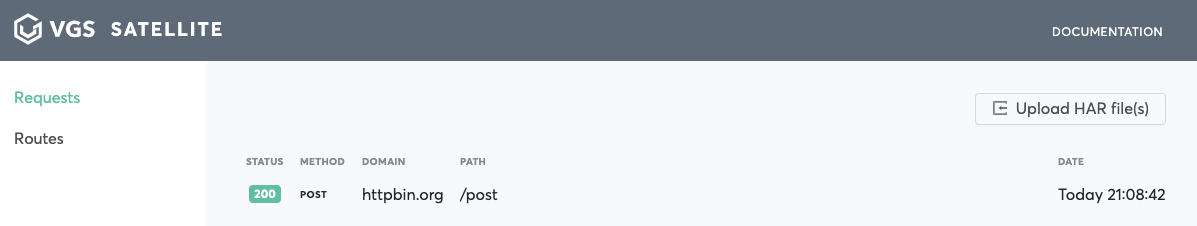
Run some request with alias, proxying it through forward proxy. For example:
curl http://httpbin.org/post -k -x localhost:9099 -H "Content-type: application/json" -d '{"foo": "tok_sat_m8bMGyxWD82NJZSvjqayem"}'
-
Wait for your requests to appear
-
Choose your request from the list
-
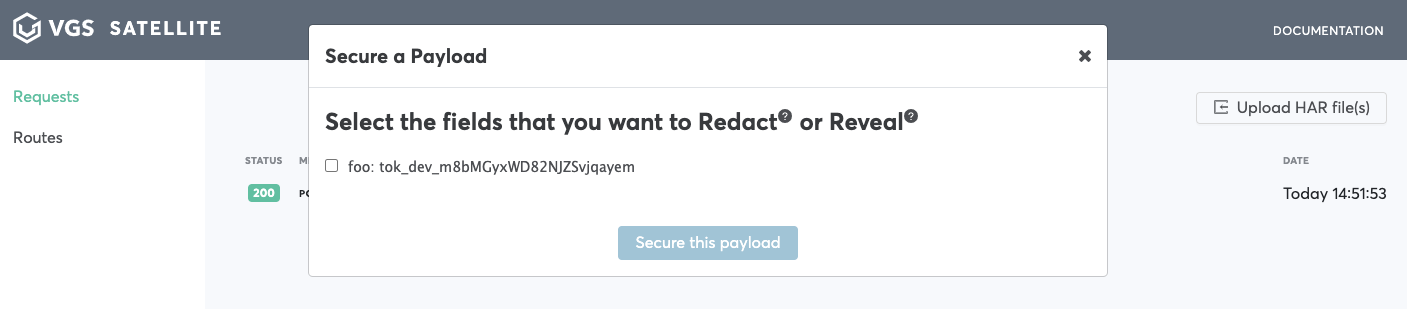
Click secure you payload
-
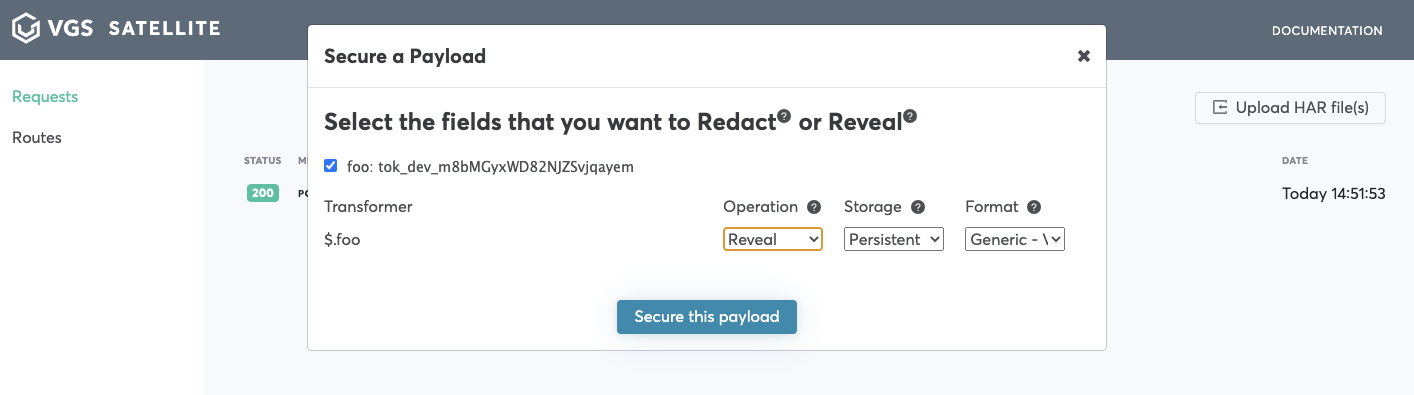
Check field you would like to reveal, choose
RevealinOperationdropdown.For additional setting please reference the nomenclature
-
Click
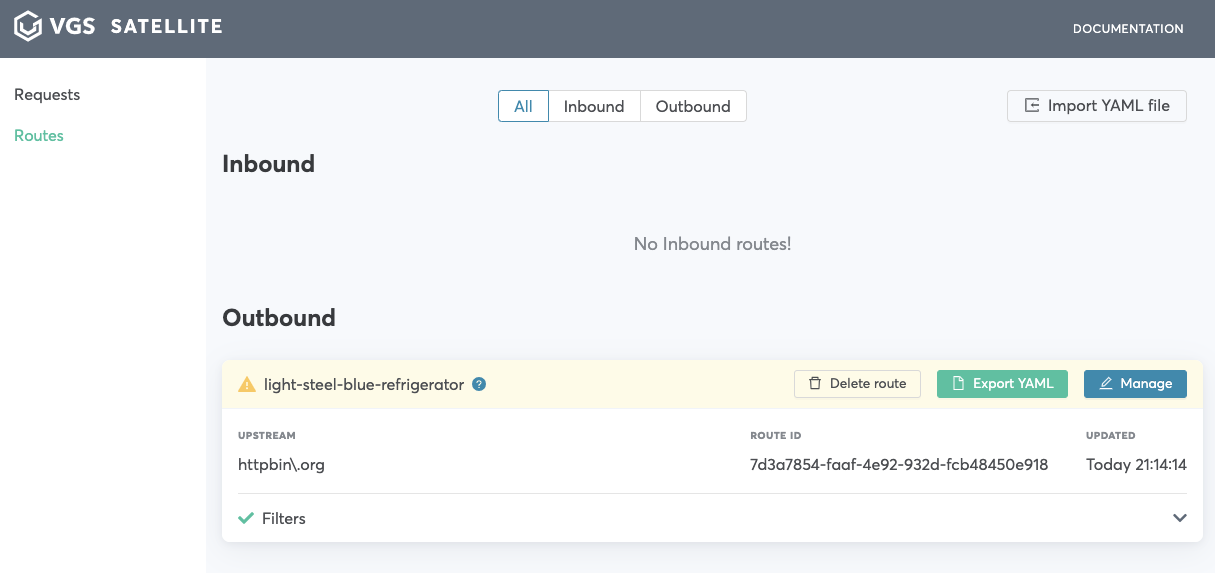
Secure this payload->View route configuration->Save outbound routeYour route is now available on
Routespage. You can edit/delete it or import another one from YAML. -
Re-send request from #3 or navigate to your request on
Requestsand clickReplay -
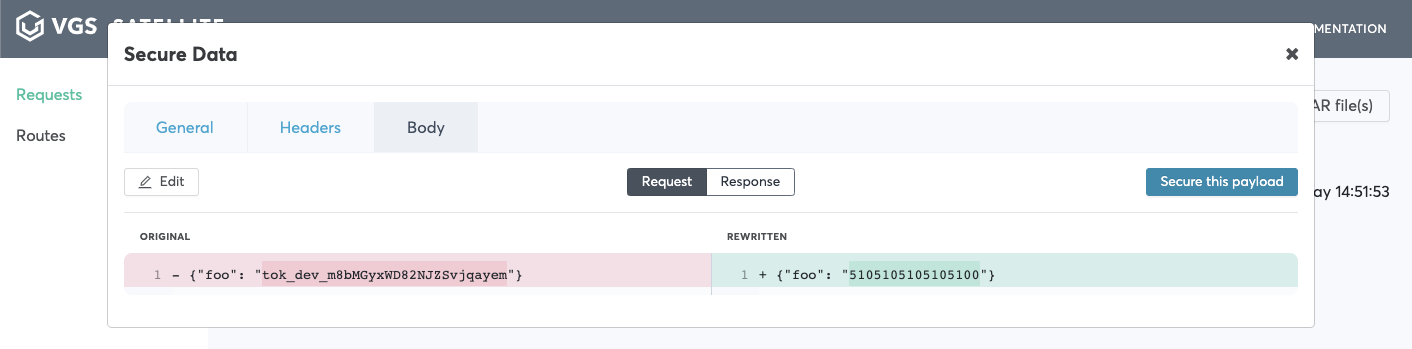
Click on the replayed request and click
Bodytab. You will see that your payload was redacted.
VGS Satellite's core depends on mitmproxy. mitmproxy or man-in-the-middle proxy is an interactive intercepting proxy with ton of build-in functionalities and protocol support. VGS Satellite is provided as a Open Source product under Apache License v2.0