CVE-2023-2859: Stored HTML injection in folderName affecting Admin in TeamPass < 3.0.9 - M Nadeem Qazi
Hi,
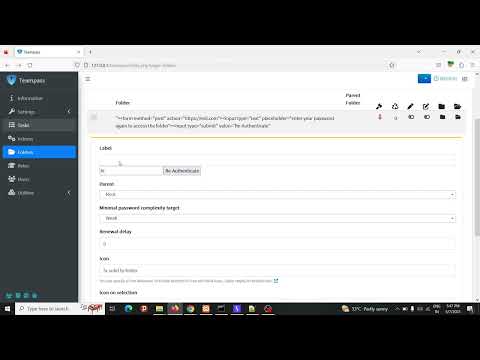
I have found a major vulnerability in the nilsteampassnet/teampass application that involves stored HTML injection in the FolderName field. By inserting malicious HTML code into the FolderName field, an attacker is able to change the names of folders.
- Vulnerability Type: Stored HTML Injection
- CVE: CVE-2023-2859
- Software Version: TeamPass < 3.0.9
- Author: M Nadeem Qazi
The injected payload can be executed when an administrator interacts with a compromised folder, opening the door to a variety of potential attacks. The HTML code that was injected could have malicious scripts, iframes, or other components that were created to attack the administrator's system and jeopardize its security.
If this vulnerability is exploited, serious consequences might result:
-
Data Theft: When the administrator interacts with the affected folder, malicious code might be injected to collect private data. This includes login information, personal information, and other sensitive data. Data that has been stolen can be exploited for financial fraud, identity theft, and other malicious activities.
-
Attacks that Redirect: The inserted code may redirect the administrator to a website that the attacker is in control of. This gives the attacker the ability to influence the admin's web surfing, possibly subjecting them to more assaults or phishing efforts.
This vulnerability has been fixed in version 3.0.9 of TeamPass.
If you're interested in learning more about my findings, check out the report link on huntr.dev.
You can also follow me for updates on my research and other security-related topics:
- Instagram: @mnqazi
- Twitter: @mnqazi
- Facebook: @mnqazi
- LinkedIn: M_Nadeem_Qazi
Stay safe out there!