BIOS Pass Bypass
Table of Contents
2 - What does BIOS Pass Bypass do?
3.1 - How do I acquire my BIOS Hash?
3.1.1 - Images of BIOS Hashes on different systems
3.2 - Obtaining a password without a hash
1 - What is a BIOS Hash?
In some BIOSes, by default or after entering a wrong password for 3 times, a hash will be displayed, accompanying a message telling the user that the system has been locked. BIOS Pass Bypass can give you a working password using the displayed hash.
2 - What does BIOS Pass Bypass do?
BIOS restricts access to a computer using a password in some places, namely:
- As soon as you turn on your computer.
- When accessing the BIOS setup.
In these cases BIOS Pass Bypass can help you bypass these passwords on some systems (and not all).
3 - What will I need?
For old BIOSes with a master password, the only thing you need is the name of the manufacturer of the BIOS. In other cases, you have to obtain the BIOS hash.
3.1 - How do I acquire my BIOS Hash?
You can obtain a BIOS hash, using one of these methods:
- Visible in the password prompt screen.
- Visible after entering 3 wrong passwords.
- For some manufacturers (like Fujitsu) you have to enter a specific sequence of wrong passwords. For example: 3hqgo3 jqw534 0qww294e
3.1.1 - Images of BIOS Hashes on different systems
Here you can see some instances of BIOS hashes, denoted by a red rectangle:
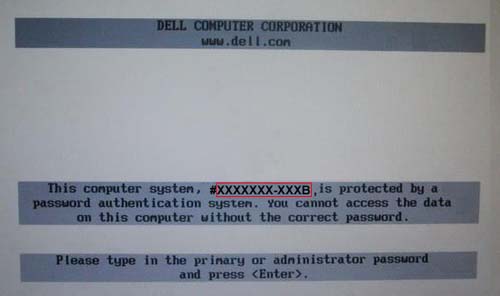
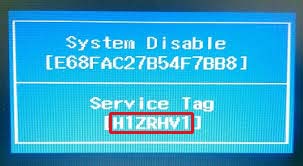
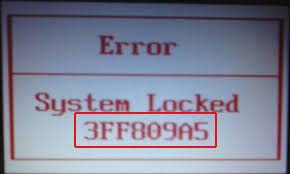
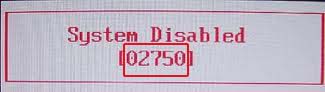
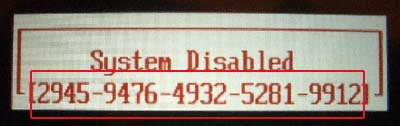
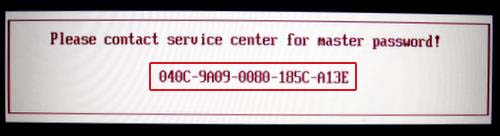
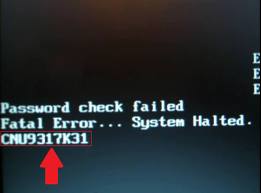
3.2 - Obtaining a password without a hash
For old BIOSes that don't provide a hash, you can go to the "Password for hash-less BIOSes" section and after choosing a make and model, see the master passwords for that specific BIOS.
Notice: If there were more than 1 password, try all of them, until you find the correct one.
Notice: In some cases, the algorithm used for obtaining a password from a hash is case sensitive. For example the passwords obtained for the following two hashes are different. 8WG0865-959B, 8wg0865-959b