BP-AODV
Blackhole Protected AODV for Network Design and Audit Course 2019
Group 3:
- 05111540000043 - Hafara Firdausi
- 05111540000031 - Aulia T. Nururrahmah
- 05111540007001 - Nabe Gedalia Razafindrobelina
This simple documentation created by Mocatfrio 😽
Requirements
- Debian based-Linux OS (Ubuntu, Linux Mint, etc)
- Basic CLI skill
1. NS2 Installation on Linux Mint
2. Implementation
2.1 Adding Blackhole Attack Mechanism
- Before modifying the original AODV code, create a backup by typing
cp -R ~/ns-allinone-2.35/ns-2.35/aodv ~/ns-allinone-2.35/ns-2.35/aodv-ori
- Open aodv code using VSCode tool by typing
code ~/ns-allinone-2.35/ns-2.35/aodv - Modify aodv.h file by adding following code under the history management:
/* * History management */ double PerHopTime(aodv_rt_entry *rt); // Modification for blackhole attack nsaddr_t malicious; ...
- Modify aodv.cc file
- Add
malicious=999;in the constructor AODV::AODV(nsaddr_t).... LIST_INIT(&nbhead); LIST_INIT(&bihead); // modification - blackhole attack code malicious = 999; ...
- Add following code in the command function:
int AODV::command(int argc, const char*const* argv) { if(argc == 2) { Tcl& tcl = Tcl::instance(); if(strncasecmp(argv[1], "id", 2) == 0) { tcl.resultf("%d", index); return TCL_OK; } // Modification - blackhole attack code if(strncasecmp(argv[1], "blackhole", 9) == 0) { malicious = 1000; return TCL_OK; } ...
- Add following code in the recvRequest function to generate fake replies by blackhole attacker.
... // Just to be safe, I use the max. Somebody may have // incremented the dst seqno. seqno = max(seqno, rq->rq_dst_seqno)+1; if (seqno%2) seqno++; sendReply(rq->rq_src, // IP Destination 1, // Hop Count index, // Dest IP Address seqno, // Dest Sequence Num MY_ROUTE_TIMEOUT, // Lifetime rq->rq_timestamp); // timestamp Packet::free(p); } // Modification - generate fake replies by blackhole attacker else if(malicious==1000) { seqno = max(seqno, rq->rq_dst_seqno)+1; if (seqno%2) seqno++; sendReply(rq->rq_src, // IP Destination 1, // Hop Count rq->rq_dst, seqno, MY_ROUTE_TIMEOUT, rq->rq_timestamp); // timestamp //rt->pc_insert(rt0->rt_nexthop); Packet::free(p); } ...
- Add following code in the rt_resolve function to disable send error message because Blackhole attacker doesn't have route to destination.
... #ifdef DEBUG fprintf(stderr, "%s: sending RERR...\n", __FUNCTION__); #endif // modification - blackhole disable send (error) if(malicious==1000); else sendError(rerr, false); ...
- Add
- The full code of blackhole-AODV can be found here. Move it to your
~/ns-allinone-2.35/ns-2.35directory.
2.2 Compiling
- After modifying AODV code, don't forget to recompile NS-2
cd ~/ns-allinone-2.35/ns-2.35 sudo make clean sudo make sudo make install
- Here's some bash scripts that will easier your life. Create these files in the
~/ns-allinone-2.35/ns-2.35directory.-
Switcher is used to switch from the AODV-ori code to AODV-blackhole, and vice versa.
#!/bin/bash if [ $1 -eq 1 ] ; then # switch from aodv ori to aodv bp mv ~/ns-allinone-2.35/ns-2.35/aodv ~/ns-allinone-2.35/ns-2.35/aodv-ori mv ~/ns-allinone-2.35/ns-2.35/aodv-bp ~/ns-allinone-2.35/ns-2.35/aodv exit 1 else # switch from aodv-bp to aodv ori mv ~/ns-allinone-2.35/ns-2.35/aodv ~/ns-allinone-2.35/ns-2.35/aodv-bp mv ~/ns-allinone-2.35/ns-2.35/aodv-ori ~/ns-allinone-2.35/ns-2.35/aodv exit 1 fi
bash switch.sh 1 bash switch.sh 2
-
Compiler is used to recompile NS-2
#!/bin/bash make clean make make install# dont forget to use SUDO sudo bash make.sh
-
2.3 Simple Simulation
- Scenario
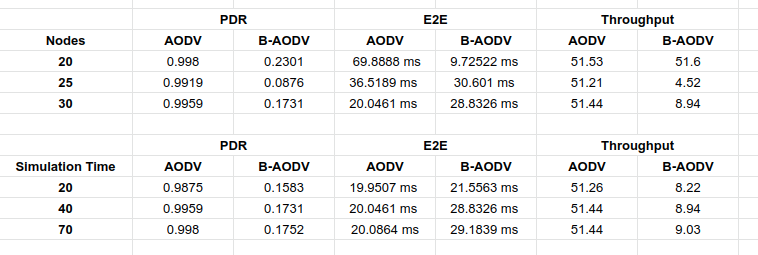
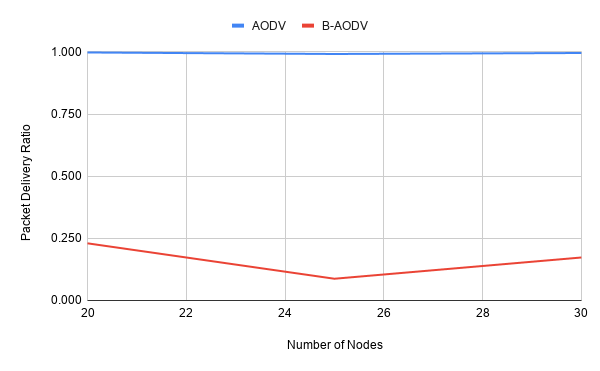
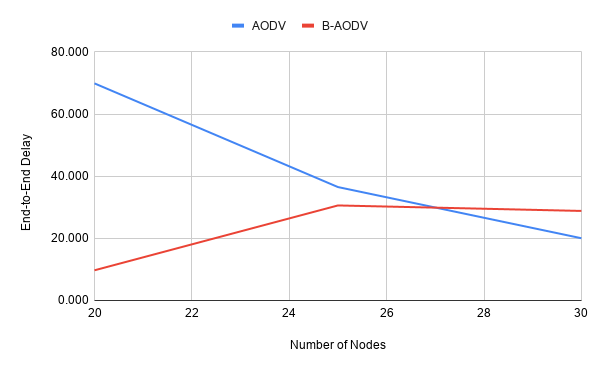
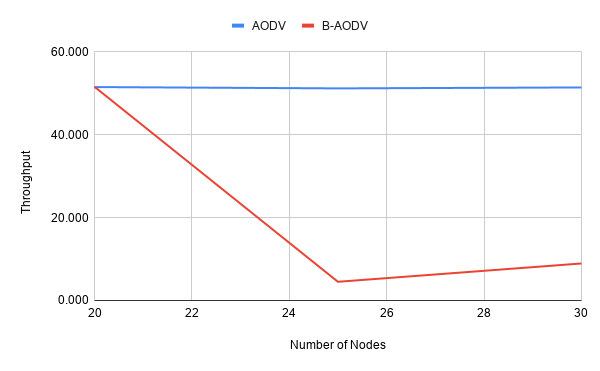
- Number of nodes : 20, 25, 30 nodes (30)
- Number of blackhole nodes : 3 nodes
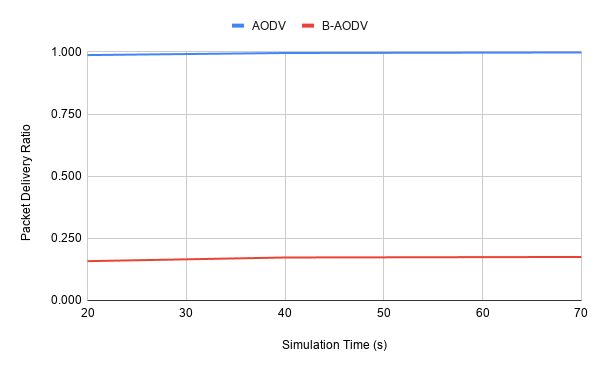
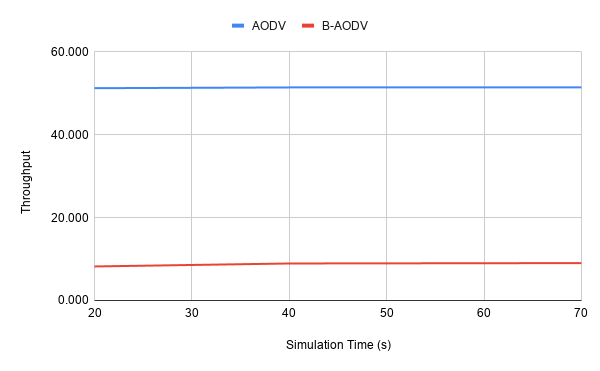
- Simulation time : 20, 40, 70 second (40)
- Routing protocol : AODV and Blackhole-AODV
- Area : 1186 x 600
- Make TCL scripts to conduct the simulation : Here's the scripts
- Run the scripts as usual, for example:
It will generate an output file.
ns blackhole20.tcl
- Analyze the output file using AWK scripts to get the PDR (Packet Delivery Ratio), End-to-end Delay, and Througput : Here's the scripts
cd awk-scripts/ awk -f eval.awk ../result/25node/ori/scenario.tr # get PDR and E2E Delay awk -f tput.awk ../result/25node/ori/scenario.tr # get throughput
2.4 Experiment Results
-
Packet Delivery Ratio (PDR)
-
End-to-End Delay (E2E)
-
Throughput
For the future work, we will implement BP-AODV (Blackhole Protected) and S-AODV (Secure).
3. Detailed Simulation and Evaluation
References
- A. M. El-Semary and H. Diab, "BP-AODV: Blackhole Protected AODV Routing Protocol for MANETs Based on Chaotic Map," in IEEE Access, vol. 7, pp. 95197-95211, 2019.
- Blackhole attack code tutorial : http://www.jgyan.com/ns2/blackhole%20attack%20simulation%20in%20ns2.php
- https://github.com/achiv/MANETs-under-Black-hole-attack