_
| | __ _ ____ _ _ _ __ ___ ___ ___ _ __
| |/ _ |_ /| | | | __/ _ \/ __|/ _ \| _ \
| | (_| / / | | | | | | __/ (__ (_) | | |
|_|\__ _|___/ \__ |_| \___|\___|\___/|_| |_v2
|___/
Lazyrecon is a subdomain discovery tool that finds and resolves valid subdomains then performs SSRF/LFI/SQLi fuzzing, brute-force and port scanning. It has a simple modular architecture and is optimized for speed while working with github and wayback machine.
- Super fast asynchronous execution
- CI/CD ready
- HTML/pdf reports
- Discord integration
- Background listen server
- Domain name, list of domains, IP, CIDR input - notations support
- Teardown and program exit housekeeping
This script is intended to automate your reconnaissance process in an organized fashion by performing the following:
- Creates a dated folder with recon notes for a target
- Grabs subdomains using
subfinder,assetfinder,gau,waybackurls,github-subdomains - Additionally finds new subdomains through alterations and permutations using
dnsgen - Searches subnets and new assets using math
Mode - Filters out live subdomains from a list of hosts using
puredns - Checks 1-200,8000-10000 for http(s) probes using
httpx - Gets visual part using
headless chromium - Performs
masscanon live servers - Scanns for known paths and CVEs using
nuclei - Shots for SSRF/LFI/SQLi based on fetched DOM's and Wayback machine's data
- Checks for 401/403 bypass using bypass-403
- Performs
ffufsupercharged byinterlaceusing custom WordList based on the top10000.txt - Generates report and send it to Discord
The point is to get a list of live IPs (in form of socket addresses), attack available network protocols, check for common CVEs, perform very simple directory bruteforce then use provided reports for manual research.
Linux&Mactested
python >= 3.7
pip3 >= 19.0
go >= 1.14You can use stateful/stateless build agent (worker). There is no additional time is required for provisioning. It may look tricky cause masscan/nmap/naabu root user required.
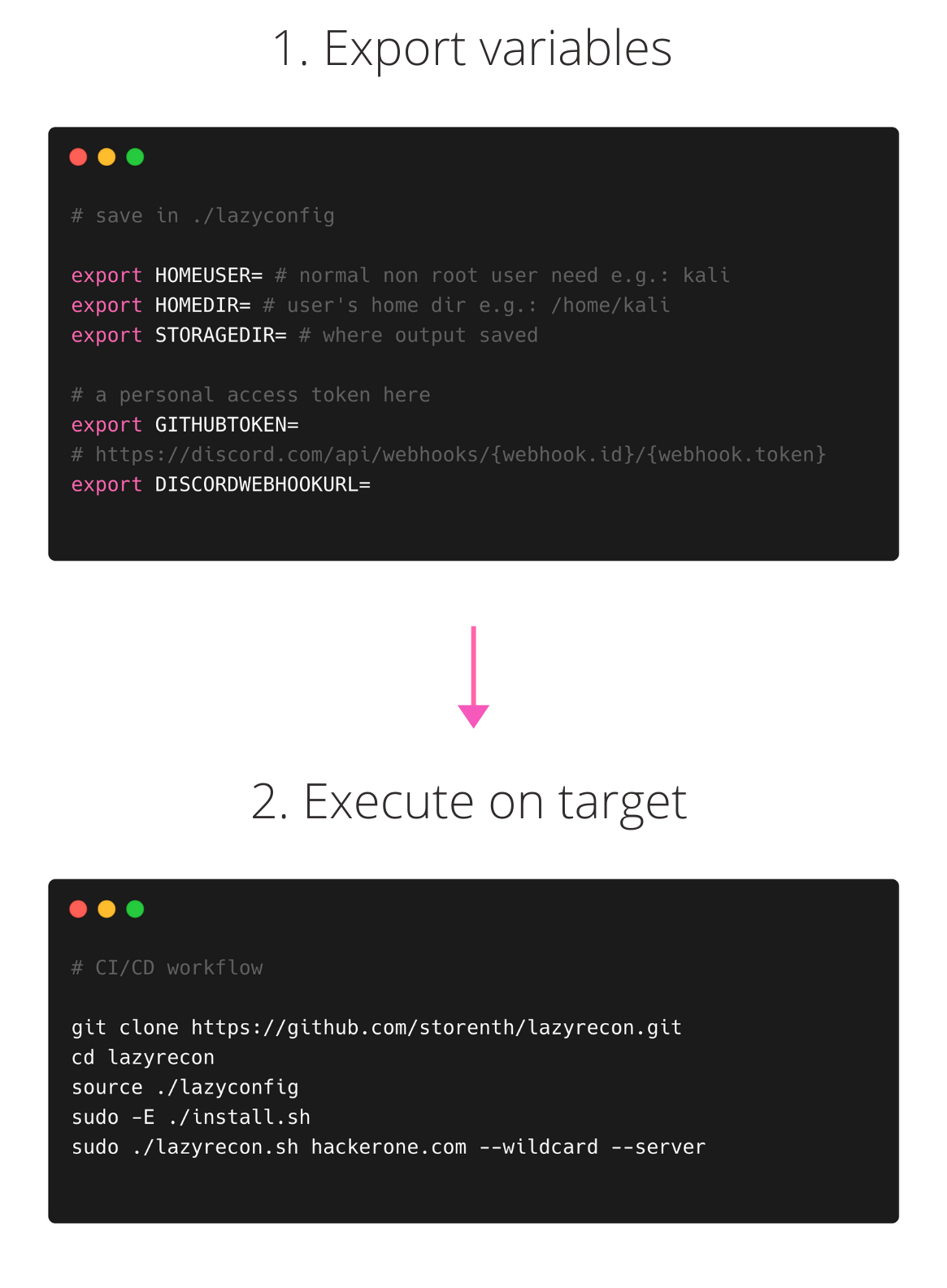
- Fill in these required environment variables inside:
./lazyconfig:
export HOMEUSER= # your normal, non root user: e.g.: kali
export HOMEDIR= # user's home dir e.g.: /home/kali
export STORAGEDIR= # where output saved, e.g.: ${HOMEDIR}/lazytargets
export GITHUBTOKEN=XXXXXXXXXXXXXXXXXX # a personal access token here
export DISCORDWEBHOOKURL= # https://discord.com/api/webhooks/{webhook.id}/{webhook.token}
export GOPATH=$HOMEDIR/go
export PATH=$PATH:/usr/local/go/bin:$GOPATH/bin:$GOROOT/bin:$HOME/.local/bin:$HOME/go/bin:$HOMEDIR/go/bin
export GO111MODULE=on- Enable new environment
source ./lazyconfig - Call
sudo -E ./install.sh - Execute
sudo -E ./lazyrecon.sh "hackerone.com"
Customize .github/workflows/test-recon-action.yaml using DISCORDWEBHOOKURL and GITHUBTOKEN secrets, enable --discord to receive a report:
- name: Install & Recon
env:
GO111MODULE: on
DISCORDWEBHOOKURL: ${{ secrets.DISCORDWEBHOOKURL }}
GITHUBTOKEN: ${{ secrets.GITHUBTOKEN }}
run: |
export HOMEDIR=$HOME
export HOMEUSER=$RUNNER_USER
export STORAGEDIR="${HOMEDIR}"/lazytargets
sudo -E ./install.sh
sudo -E ./lazyrecon.sh "hackerone.com" --quiet --discordConfig your environment variables and dependencies using INSTALL.MD
If you faced with some issues, feel free to join Discord, open PR or file the bug.
You can check if the dependencies are installed correctly on your machine by running the following tests:
./test/test_nuclei_templates.sh "./test/nuclei_templates_list.txt"
./test/test_install.sh "./test/dependencies_list.txt"Execute with sudo because of masscan:
▶ sudo -E ./lazyrecon.sh tesla.com --wildcard| Parameter | Description | Example |
|---|---|---|
| --wildcard | Subdomains reconnaissance '*.tesla.com' (default) | ./lazyrecon.sh tesla.com --wildcard |
| --single | One target instance 'tesla.com' | ./lazyrecon.sh tesla.com --single |
| --ip | Single IP of the target machine | ./lazyrecon.sh 192.168.0.1 --single --ip |
| --list | List of subdomains to process for | ./lazyrecon.sh "./testa.txt" --list |
| --cidr | Perform network recon, CIDR notation | ./lazyrecon.sh "192.168.0.0/16" --cidr |
| --mad | Wayback machine's stuff | ./lazyrecon.sh tesla.com --mad |
| --fuzz | SSRF/LFI/SQLi fuzzing | ./lazyrecon.sh tesla.com --mad --fuzz |
| --alt | Additionally permutate subdomains (*.tesla.com only) | ./lazyrecon.sh tesla.com --wildcard --alt |
| --brute | Basic directory bruteforce (time sensitive) | ./lazyrecon.sh tesla.com --single --brute |
| --discord | Send notifications to discord | ./lazyrecon.sh tesla.com --discord |
| --quiet | Enable quiet mode | ./lazyrecon.sh tesla.com --quiet |
- Use dnsperftest to know your best resolvers
- Run
./lazyrecon.sh - Check output reports of chromium, nuclei, masscan,
403-bypass-output.txt_listen_server.log,lfi-matched-url.txt - Pick the right target for you based on screenshot and ports opened.
- Use Firefox and Burp to proxy all requests while exploratory testing
- Try to find file upload vulnerabilities
- Perform Google, Trello, Atlassian, Github, Bitbucket dorking
- Check JS sources for credentials, API endpoints
- Investigate
XHRrequests, fuzz parameters and variables - Check exploit-db.com for target-specific CVE based on
nmap/masscanoutput - GET/POST Bruteforce for directories: fuzbo0oM-top10000 --> raft --> target specific
- Continue bruteforcing using custom Headers (X-Custom-IP-Authorization: 127.0.0.1; X-Original-URL:)
- Try bypass 401/403 errors using notable methods (
%23,/%2e/,admin.php%2500.mdetc) - Look for XSS xsscrapy.py or XSSTRON
This project was inspired by original v1.0 Ben Sadeghipour and aimed to implement some of the best practices like Mechanizing the Methodology, TBHM, Subdomain Takeovers, Request Smuggling, SSRF, LFI and Bruteforce based on Custom wordlist.
- IDOR: https://www.aon.com/cyber-solutions/aon_cyber_labs/finding-more-idors-tips-and-tricks/?utm_source=newsletter&utm_medium=email&utm_campaign=bug_bytes_110_scope_based_recon_finding_more_idors_how_to_hack_sharepoint&utm_term=2021-02-17
- SSRF: https://notifybugme.medium.com/finding-ssrf-by-full-automation-7d2680091d68 and https://rez0.blog/hacking/2019/11/29/rce-via-imagetragick.html
- Enumeration guide: https://sidxparab.gitbook.io/subdomain-enumeration-guide/active-enumeration/dns-bruteforcing
aquatonereplaced by headless chromium async script based on performanceSublist3rreplaced withsubfinderbased on Twitter discussionnmapreplaced withmasscanbased on its features and Twitter duscussion, usehelpers/nmap_nse_ifile.shby hands usingmasscan_output.gnmapas inputsmugglerforked from its original aimed to get lightweight solution included this PRgrepmeg's output for Location in order to exclude 301/302 status codeshttpx -fc 301,302approach)httpx -ipused withoutdnsprobebased on @pdiscoveryio Twitter answeraltdnsused based on Scrutiny on the bug bountymassdnsfully replaced withshufflednsbecause of issueshufflednsreplaced withpurednsbased on performance- bounty-targets-data
- local listen server approach replaced with interactsh
- LFI payload now handled and fully featured by LFI-Payload-List caused outdated LFI-Payload-List
- WIP: you can track activity in Projects To Do board
Acknowledgement: This code was created for personal use with hosts you able to hack/explore by any of the known bug bounty program. Use it at your own risk.