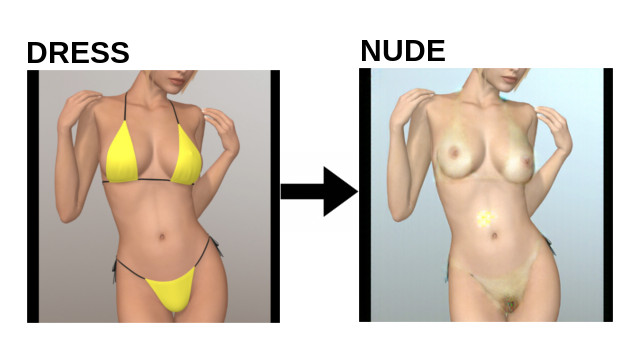
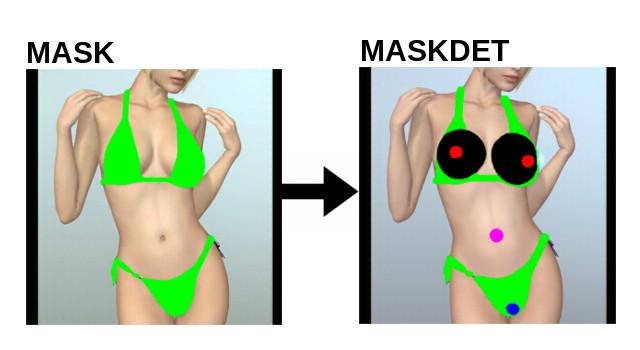
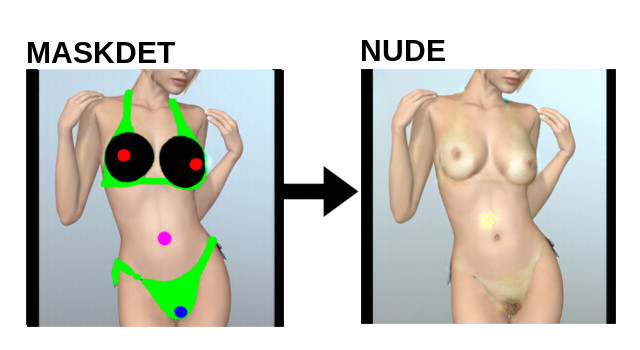
The original DeepNude Software and all its safety measures have been violated and exposed by hackers. Two days after the launch, the reverse engineering of the app was already on github. It no longer makes sense to hide the source code. DeepNude uses an interesting method to solve a typical AI problem, so it could be useful for researchers and developers working in other fields such as fashion, cinema and visual effects.
This repo contains the core algorithm, not the user interface.
DeepNude uses a slightly modified version of the pix2pixHD GAN architecture. If you are interested in the details of the network you can study this amazing project provided by NVIDIA.
A GAN network can be trained using both paired and unpaired dataset. Paired datasets get better results and are the only choice if you want to get photorealistic results, but there are cases in which these datasets do not exist and they are impossible to create. DeepNude is a case like this. A database in which a person appears both naked and dressed, in the same position, is extremely difficult to achieve, if not impossible.
We overcome the problem using a divide-et-impera approach. Instead of relying on a single network, we divided the problem into 3 simpler sub-problems:
-
- Generation of a mask that selects clothes
-
- Generation of a abstract representation of anatomical attributes
-
- Generation of the fake nude photo
This approach makes the construction of the sub-datasets accessible and feasible. Web scrapers can download thousands of images from the web, dressed and nude, and through photoshop you can apply the appropriate masks and details to build the dataset that solve a particular sub problem. Working on stylized and abstract graphic fields the construction of these datasets becomes a mere problem of hours working on photoshop to mask photos and apply geometric elements. Although it is possible to use some automations, the creation of these datasets still require great and repetitive manual effort.
To optimize the result, simple computer vision transformations are performed before each GAN phase, using OpenCV. The nature and meaning of these transformations are not very important, and have been discovered after numerous trial and error attempts.
Considering these additional transformations, and including the final insertion of watermarks, the phases of the algorithm are the following:
- dress -> correct [OPENCV]
- correct -> mask [GAN]
- mask -> maskref [OPENCV]
- maskref -> maskdet [GAN]
- maskdet -> maskfin [OPENCV]
- maskfin -> nude [GAN]
- nude -> watermark [OPENCV]
Before launch the script install these packages in your Python3 environment:
- numpy
- Pillow
- setuptools
- six
- torch
- torchvision
- wheel
To run the script you need the pythorch models: the large files (700MB) that are on the net (cm.lib, mm.lib, mn.lib). Put these file in a dir named: checkpoints. You can download them here: cm.lib mm.lib mn.lib
cd checkpoints
wget -O cm.lib https://github.com/open-deepnude/deepnude-model-3/raw/master/checkpoints/cm.lib
wget -O mm.lib https://github.com/open-deepnude/deepnude-model-2/raw/master/checkpoints/mm.lib
wget -O mn.lib https://github.com/open-deepnude/deepnude-model-1/raw/master/checkpoints/mn.lib
Due to GitHub bandwidth quota they might not be available. In that case, download DeepNude from Mega, then apply these patches to the .libs:
+0x000: 80 02 8A 0A 6C FC 9C 46 F9
+0x0C8: 75 74 69 6C 73 0A 5F 72 65
+0x3E8: 00 00 48 00 4E 74 71 40 51
python3 main.py
The script will transform input.png to output.png.
If you followed our story you will know that we have decided not to continue selling DeepNude because we could no longer guarantee enough safety. The original DeepNude app was intended to be fun and safe: we knew our customers, images were associated with them and watermarks covered the photos. But after 12 hours of launch, due to viral articles and clickbaits, the software had been hacked and modified. With multiple illecit DeepNude version in the web, anonymous and unknown users, virus and malware, the assumption of security dissolved soon. There are no valid security systems, when hackers from all over the world attack you.
We could have made a lot of money, but we preferred to limit the misuse as much as possible. If you have enjoyed our work or you would like our research not to stop there, make us a donation. We really appreciate it.
Bitcoin Address 1ExaDm9JVvCbFJ2ijRcgrfmHwRErEN6gA6
Ethereum Address 0x2133e5157c200C15624315c97F589A694d3589A8
This software is licensed under:
GNU General Public License v3.0
https://choosealicense.com/licenses/gpl-3.0/#
See license.txt for more details.