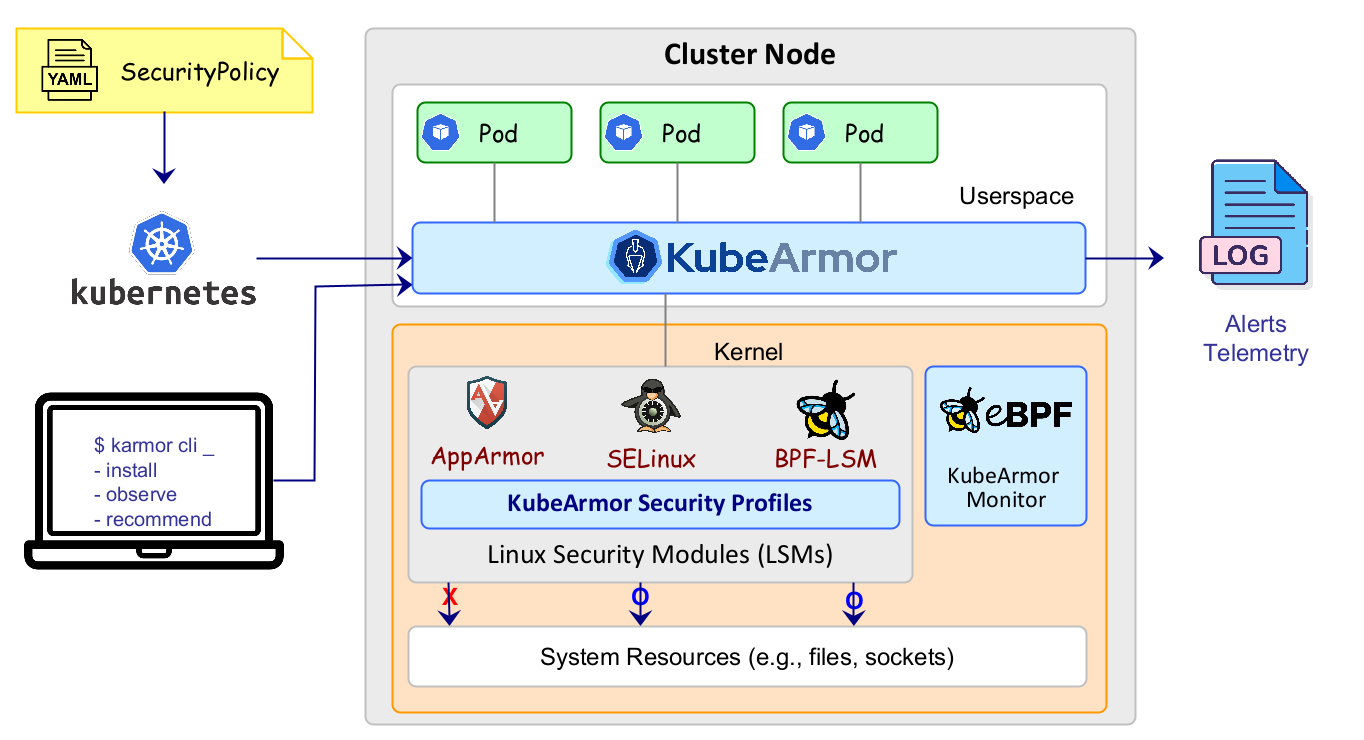
KubeArmor is a cloud-native runtime security enforcement system that restricts the behavior (such as process execution, file access, and networking operations) of pods, containers, and nodes (VMs) at the system level.
KubeArmor leverages Linux security modules (LSMs) such as AppArmor, SELinux, or BPF-LSM to enforce the user-specified policies. KubeArmor generates rich alerts/telemetry events with container/pod/namespace identities by leveraging eBPF.
| 💪 Harden Infrastructure 🔹 Protect critical paths such as cert bundles ⛓️ 🔹 MITRE, STIGs, CIS based rules 🗜️ 🔹 Restrict access to raw DB table 🛅 |
💍 Least Permissive Access 🔹 Process Whitelisting 🚥 🔹 Network Whitelisting 🚥 🔹 Control access to sensitive assets 🎛️ |
| ❄️ Network Segmentation 🔹 Communication Graph between services/pods 🕸️ 🔹 Generate k8s network policies 🪄 🔹 Keep policies in sync with app updates 📥 |
🔭 Application Behavior 🔹 Process execs, File System accesses 🧬 🔹 Service binds, Ingress, Egress connections 🧭 🔹 Sensitive system call profiling 🔬 |
- 👉 Getting Started
- 🎯 Use Cases
- ✔️ KubeArmor Support Matrix
- 🏅 How is KubeArmor different?
- 📜 Security Policy for Pods/Containers [Spec] [Examples]
- 📜 Security Policy for Hosts/Nodes [Spec] [Examples]
- 🗣️ Zoom Link
- 📄 Minutes: Document
- 📆 Calendar invite: Google Calendar, ICS file
- KubeArmor uses Tracee's system call utility functions.
KubeArmor is Sandbox Project of the Cloud Native Computing Foundation.