Command-line interface to generate 2FA from Aegis' json file
Linux
Download:
- x86_64 Intel or AMD 64-Bit CPU
curl -L "https://github.com/navilg/aegis-cli/releases/latest/download/aegis-cli-linux-x86_64" \ -o "aegis-cli" && \ chmod +x "aegis-cli"
- arm64 Arm-based 64-Bit CPU (i.e. in Raspberry Pi)
curl -L "https://github.com/navilg/aegis-cli/releases/latest/download/aegis-cli-linux-arm64" \ -o "aegis-cli" && \ chmod +x "aegis-cli"
To determine your OS version, run
getconf LONG_BIToruname -mat the command line.
Move:
sudo mv aegis-cli /usr/bin/aegis-climacOS
Download:
- x86_64 Intel 64-bit
curl -L "https://github.com/navilg/aegis-cli/releases/latest/download/aegis-cli-macos-x86_64" \ -o "aegis-cli" && \ chmod +x "aegis-cli"
- arm64 Apple silicon 64-bit
curl -L "https://github.com/navilg/aegis-cli/releases/latest/download/aegis-cli-macos-arm64" \ -o "aegis-cli" && \ chmod +x "aegis-cli"
To determine your OS version, run
uname -mat the command line.
Move:
mv aegis-cli ~/Applications/aegis-cliTip:
- Add
~/Applications/to your$PATHecho 'export PATH="$HOME/Applications/:$PATH"' >> ~/.zshrc
- Or, add
~/Applications/aegis-clias alias foraegis-cliecho 'alias aegis-cli="$HOME/Applications/aegis-cli"' >> ~/.zshrc
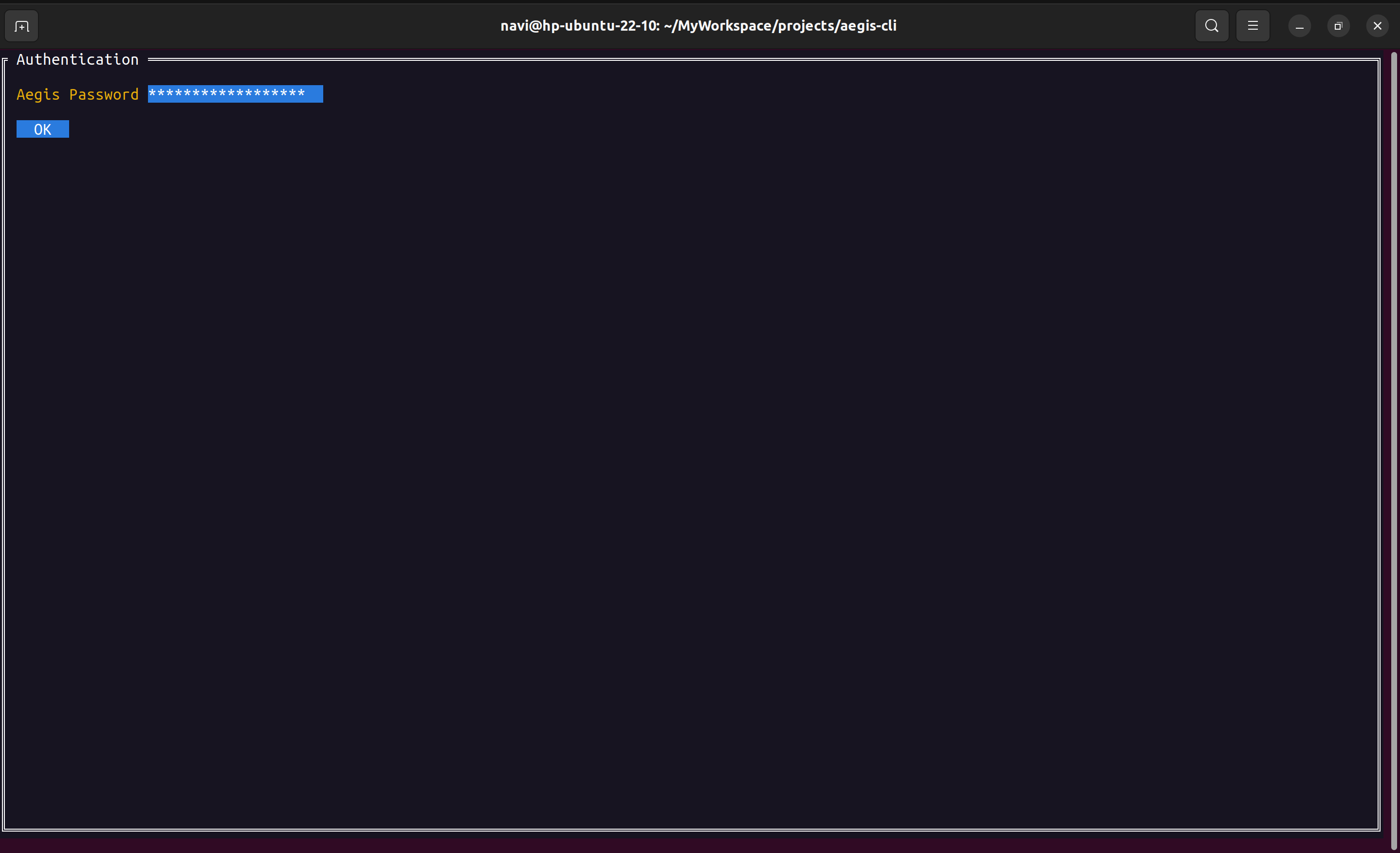
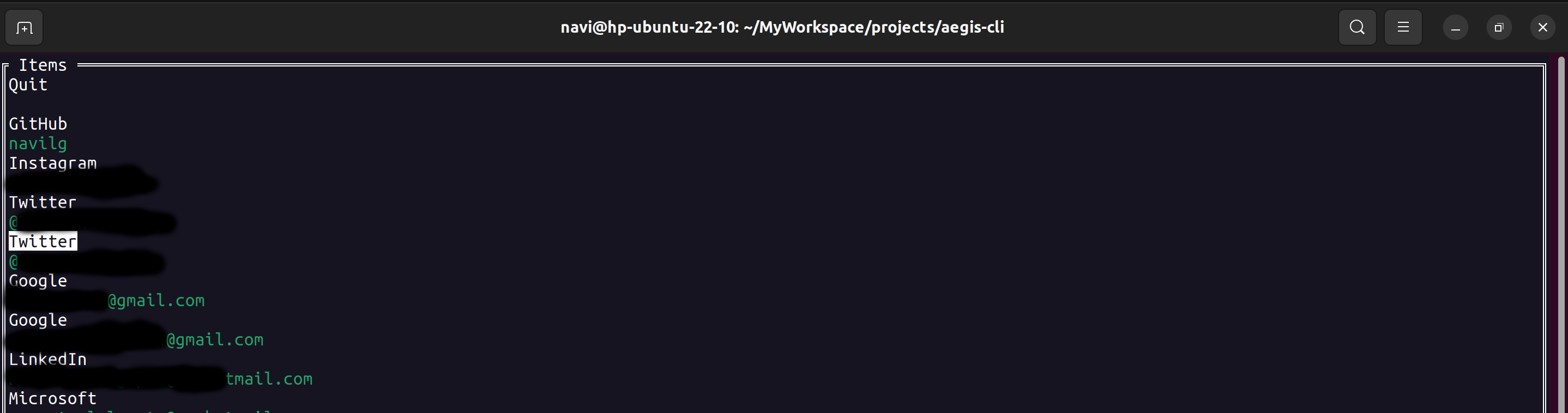
Export vault (encrypted) from your mobile app and put the vault file on your system under $HOME/.config/aegis-cli with filename aegis.json.
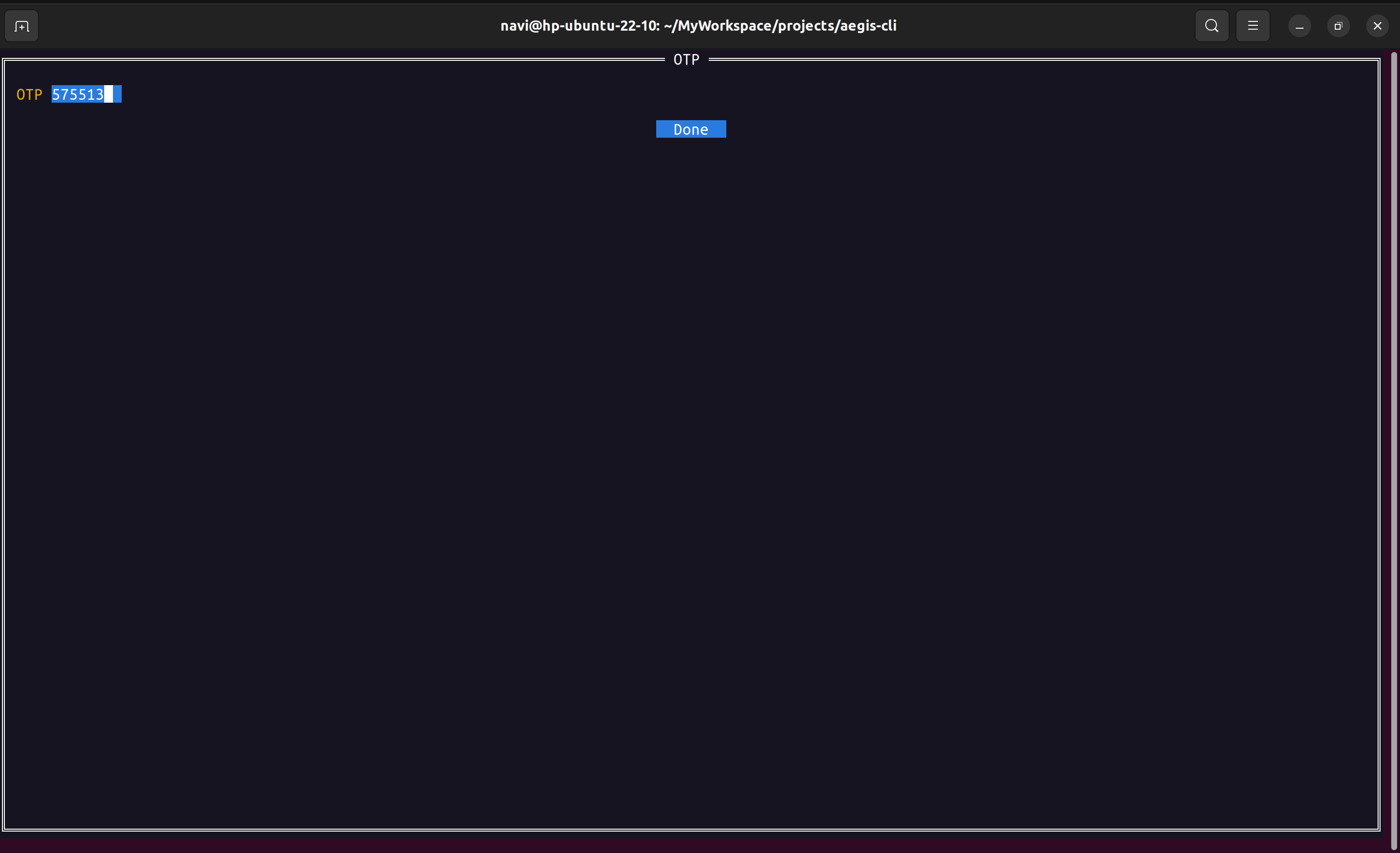
Execute aegis cli:
aegis-cliAES 256 in GCM mode is used as AEAD cipher.
Scrypt is used as the KDF with N=2^15, r=8 and p=1
Vault is encrypted using 256-bit master key. This master key is encrypted with credential in stored in slot. This process is called key wrapping.
Vault format:
{
"version": 1,
"header": {},
"db": {}
}db contains vault content. If its encrypted, Its value is base64 encoded (with padding) ciphertext of vault content. If its not encrypted, Its in json format.
Header contains slots and params.
{
"slots": [],
"params": {
"nonce": "0123456789abcdef01234567",
"tag": "0123456789abcdef0123456789abcdef"
}
}params contains nonce and tag that was produced during encryption encoded as hexadecimal string.
Slot is of three type. Type 1 is raw, Type 2 is password and Type 3 is biometric.