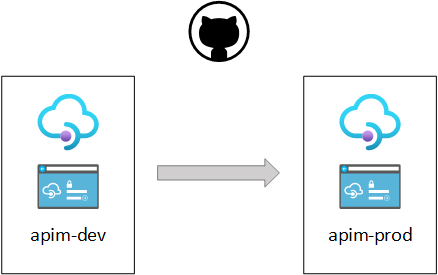
Using several Azure API Management (APIM) services is useful to have distinct isolated environments, for instance one for development stage and another for the production stage. Moving assets between these environments can be done using various tools and automated with GitHub Actions.
This repository provides sample workflows to automate those common integration tasks.
copy-apim-service.yml is a workflow that copy APIM assets from one service to another, including APIs, Products, Named Values, Backends, Policies and more.
Everything is moved except the Developer portal and some settings : What is not backed up
It uses the az cli apim backup and apim restore operations.
copy-apim-dev-portal.yml is a workflow that copy developer portal content and customization from one source APIM service to another destination APIM service. It uses the migrate.js v3 provided on the APIM developer portal repository.
More information about the whole process can be found on the Microsoft documentation : Automate developer portal deployments.
To run these workflows, it requires:
- A source APIM service
- A destination APIM service
- An Azure Storage Account and a nested Blob Container
- A Service Principal
- Some GitHub Secrets and inputs
To allow GitHub Actions to log onto your Azure subscription and execute the steps, you need to create a Service Principal with read/write permissions on the source and destination APIM services. The below command line creates a Service Principal with Contributor role on a resource group (assuming both source and destination services are inside).
Replace <YOUR_SUBSCRIPTION_ID> and <YOUR_RESOURCE_GROUP_NAME> with appropriated values.
az ad sp create-for-rbac --name "git-actions-apim" --sdk-auth --role contributor \
--scopes /subscriptions/<YOUR_SUBSCRIPTION_ID>/resourceGroups/<YOUR_RESOURCE_GROUP_NAME>Take note of the JSON output. It will be used further in the AZURE_CREDENTIALS secret.
{
"clientId": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxx",
"clientSecret": "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"subscriptionId": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxx",
"tenantId": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxx",
"activeDirectoryEndpointUrl": "https://login.microsoftonline.com",
"resourceManagerEndpointUrl": "https://management.azure.com/",
"activeDirectoryGraphResourceId": "https://graph.windows.net/",
"sqlManagementEndpointUrl": "https://management.core.windows.net:8443/",
"galleryEndpointUrl": "https://gallery.azure.com/",
"managementEndpointUrl": "https://management.core.windows.net/"
}Secrets are encrypted environment variables. Using secrets is a best practice to pass sensitive informations such as keys or ids to your workflows in a secure manner.
The following secrets are needed:
| Secret name | Value |
|---|---|
| AZURE_CREDENTIALS | Credentials of the Service Principal |
| SUBSCRIPTION_ID | ID of the Azure subscription where your APIM services are. Find your Azure subscription |
| STORAGE_NAME | Name of your Azure Storage Account. |
| STORAGE_KEY | Access key of your Storage Account. View account access keys |
For more information on how to create Secrets check this doc : Create secrets for GitHub workflows
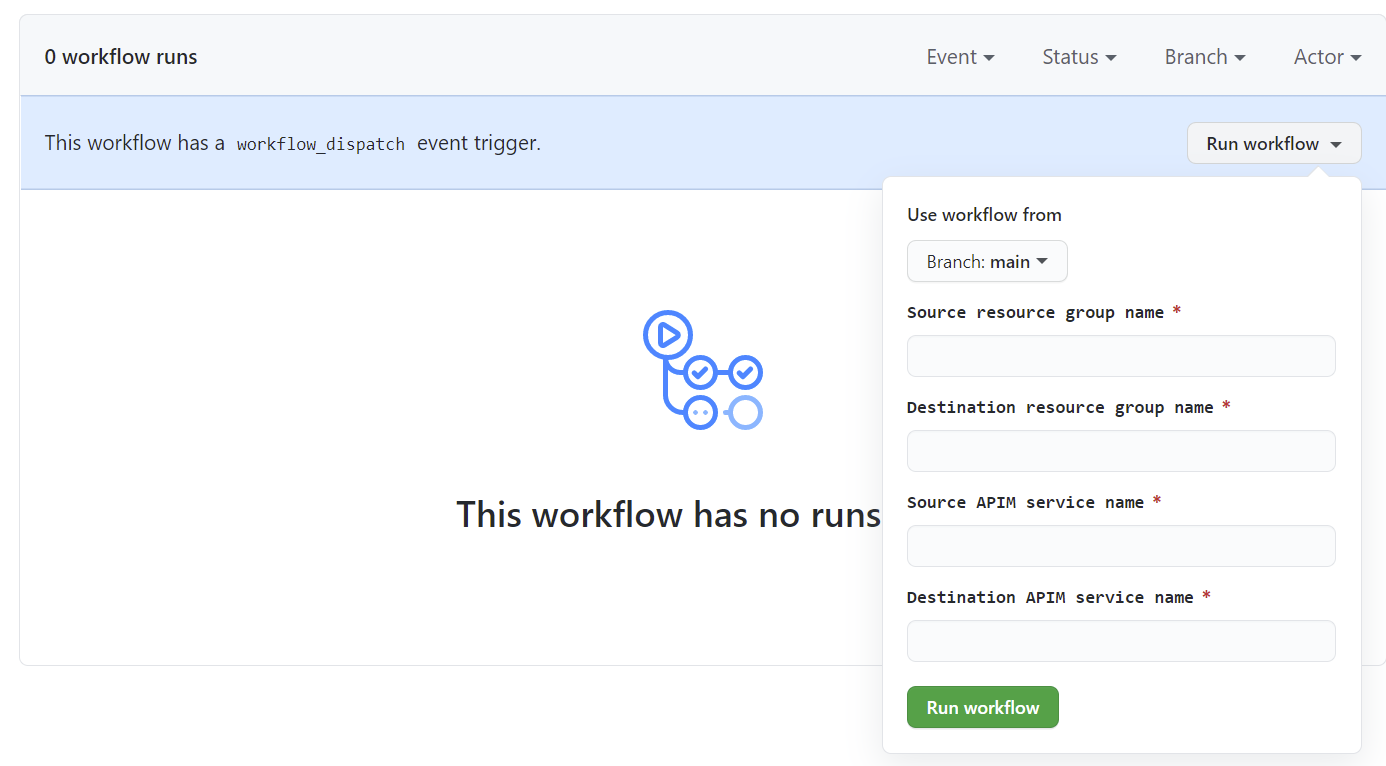
These workflows implement the workflow_dispatch event trigger which allow to run them manually from the Actions tab. Input source and destination resource groups/service names and run the workflow.