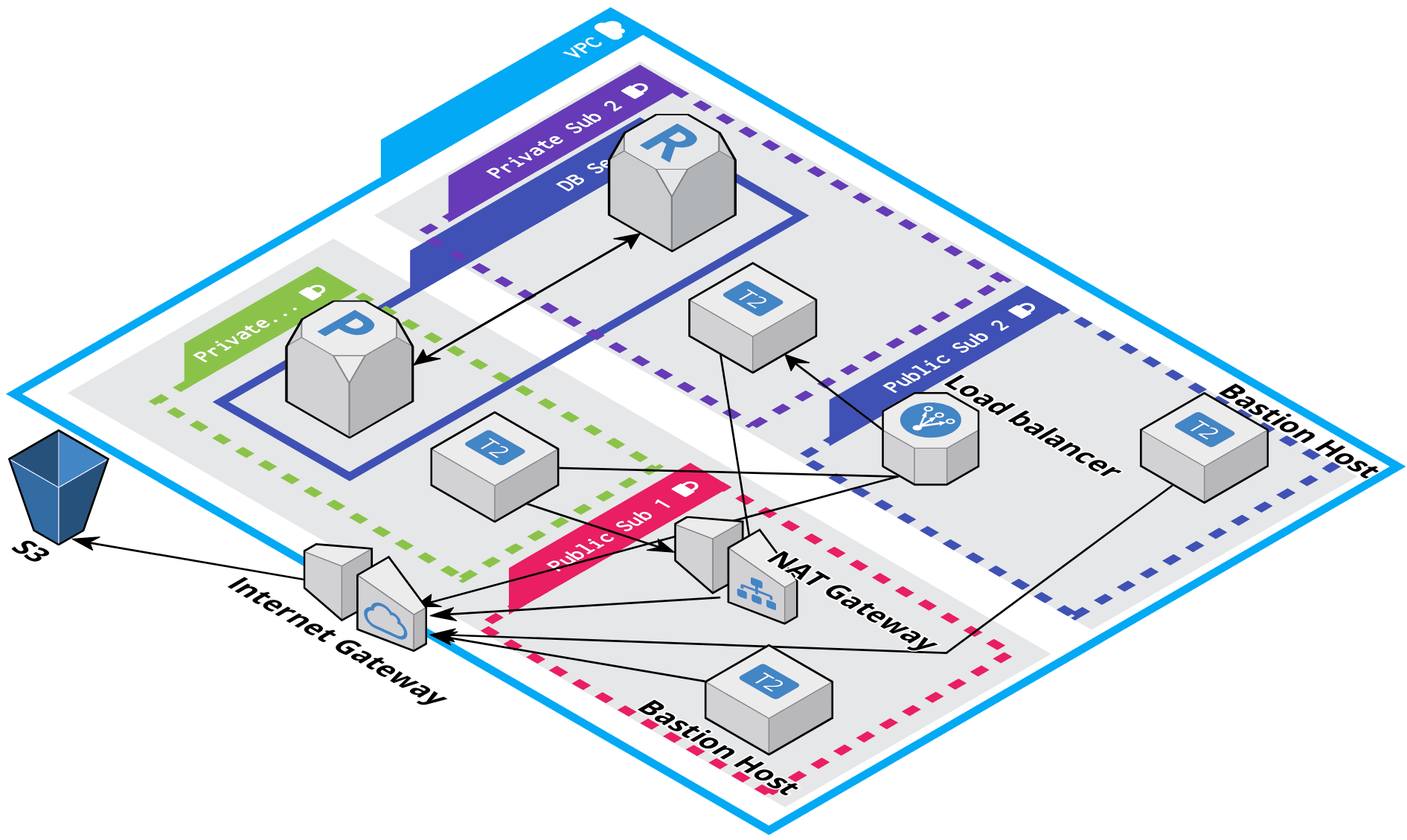
A terraform project to create AWS infrastructure to a web application with its container registry
The following diagram shows the key components of the configuration for this module:
- Setup
aws clior have~/.aws/credentialsfile so that terraform can call API using your AWS account. - Install terraform
- Install ansible
- VirtualBox
- Vagrant
-
The first step is to generate the SSH keys, that will be used to login to service boxes.
This will generate 2 files Public key and private key, use public key path in tfvars in next step.
# create the keys. ssh-keygen -m PEM -f "~/.ssh/awskey" # Add ssh keys to keychain ssh-add <PrivateKeypath> -
Now, Create a tfvar file to overwrite default variable values, edit
ap-south.tfvars.exampleand add your valuesin it.Add DB user and password. Also add public key path that you added above.
-
Now you can run terraform command to deploy all the changes. Yo
terraform plan -var-file=ap-south.tfvars OR terraform apply -var-file=ap-south.tfvars
After setup you can connect to bastion using this command.
ssh -i ~/.ssh/awskey -A ubuntu@<Bastion-public-ip>
-
Firstly, Install aws dynamic inventory plugin for ansible, it will be used to fetch hosts from AWS.
ansible-galaxy collection install amazon.aws # above collection requires boto3 and botocore -
Now if you have run terraform apply command it will create 3 things in ansible directory.
- File
ansible/s3_keys.yaml. It has secret for S3 users both Read-only and R/W. Copy themin vault.yaml. - File
ansible/terraform_vars.yaml. It contains all the variables/outputs from terraform. - Directory
ansible/certwhich contains SSL certificates for LB.
- File
-
Now you have to create a vault which will have values as given in
ansible/vault.yaml.example. Copy it and edit your secrets.# name vault.yaml is hardcoded right now so use that name only. ansible-vault encrypt vault.yaml -
Run playbook,
make deployThe above command will deploy docker
registry, a django app and initialize DB with default user.
make init_server # to initlize server with python packages and docker
make deploy_registry # only deploy registry
make deploy_app # only deploy django app
make init_db # initialize DB with default user.
Now you can login into application on LB dns address, goto
<lb-dns-address>/api-auth/login/
From makefile you can startup the vagrant machines
make jenkins
This will start 2 machines 1 master jenkins server 1 slave. You can access your jenkins on localhost:8080
Because jenkins uses ansible to deploy your app the files mentioned above are also important here.
For,ansible/terraform_vars.yamlandansible/vault.yaml, You need to copy these files to your local/vagrantdirectory which will be auto mounted to machines.
For,ansible/cert/*you have to copy it to/etc/docker/certs.d/<load balancer dns>/
Now, you need to setup node to connect a slave(hostname: jenkins-slave) to master.
After that you can setup a pipeline project, vagrant/jenkins/Jenkinsfile can be used for the script.
You also have to add few credentials, for pipeline to work.
- Credential named
AnsibleVault(type: Secret text) contaning vault password. aws-idAWS key and secret(type: AWS credentials) to list the host machines to deploy (used by ansible).aws-ssh-key(type: "SSH username with Key") which stores the private key we created/used in terraform to initilize service machines.
Plugins:
These plugins are required in order to run the above pipeline.
Ansible plugin, Docker Pipeline, SSH Agent Plugin
-
Application Load Balancer
-
Two bastion machines (one per AZ).
-
Attach 8 GB extra EBS volume.
-
RDS
-
S3 buckets with users.
-
Docker registry service, integrated with ansible.
-
Django application.
-
Containerize the application using docker.
-
make file to run tests, create docker images and push to docker registry.
-
Ansible's dynamic inventory to provision the application.
-
CI using Jenkins.
-
CD Pipeline