These icons are published under the extremely permissive Creative Commons Zero v1.0 Universal license.
We provide all icon SVGs in both black and blue - download icons.zip from the latest release.
We are now part of The Noun Project - the most comprehensive icon collection in the world!
We are also now available on Iconfinder!
We also provide a draw.io library.
Here's how to use it to build awesome diagrams:
- Download draw.io.xml from the latest release.
- Navigate to https://draw.io and create a new diagram.
- Click
File -> Open Library from -> Device
- Select the draw.io.xml you downloaded in Step 1.
 |  |  |  |  |
| Academy | Accept Risk | Accessibility | Add | Adhere to Policy |
 |  |  |  |  |
| Alerts New Risks | Alibaba Cloud | Amazon AWS | API Documentation | API Keys |
 |  |  |  |  |
| Approved Base Images | Aqua | Aqua Enforcer | Aqua Plugin | Aqua Score |
 |  |  |  |  |
| Artifacts | Assurance | Assurance Violation | Audit | Audit Only |
 |  |  |  |  |
| Binary File | Bitcoin Mining | Block List Allow List | Blocked Event | Brute Force Attack |
 |  |  |  |  |
| C2Control | Calendar | Cattle | ChainBench | Change Password |
 |  |  |  |  |
| Changelog | Changelog 2 | Check Mark | Chip | CICD |
 |  |  |  |  |
| CIS Compliance | Clean | Clock | Cloud Accounts | Cloud architect |
 |  |  |  |  |
| Cloud Misconfiguration | Cluster | CNAPP | CNDR | Code Repositories |
 |  |  |  |  |
| Collect | Collection Exfiltration | Commit | Communication | Compliance |
 |  |  |  |  |
| Compliance Program | Computer | Container | Container registry | Continuous Deployment |
 |  |  |  |  |
| Continuous Integration | Count Arrows | CPU | CVE | Cyber Intel |
 |  |  |  |  |
| Dashboard | Data repository | Database | Debian | Detection Events |
 |  |  |  |  |
| Developer | DevOps | DevSecOps | DISA Compliance | Disconnected |
 |  |  |  |  |
| Docker | Domain | Down | Download | DTA |
 |  |  |  |  |
| DTA Icon | DTA Risk | eBPF | Edit | eLearning on demand |
 |  |  |  |  |
| Enforcers | Enforcers Notification | Environment | Events | Evidence |
 |  |  |  |  |
| Export | Export PDF | Failed | Favorites | Federal Security |
 |  |  |  |  |
| File | Filter | Firewall | Folder | Forbidden Labels |
 |  |  |  |  |
| Full Screen | Function | Garbage | Gateway | Gateway New |
 |  |  |  |  |
| GitHub | Goal | Groups | Hacker | Hamburger |
 |  |  |  |  |
| Heartbeat | Honeypot | Hybrid | IaaS | IaC |
 |  |  |  |  |
| IAM | IDE | Ignore | Image Profile Detached | Image Unregistered |
 |  |  |  |  |
| Images | Import | Inbound Connection | Info | Infrastructure |
 |  |  |  |  |
| Infrastructure as Code | Initial Execution | Insights | Insights 2 | Instructor lead training |
 |  |  |  |  |
| Integration | Inventory | IP | Jenkins | KSPM |
 |  |  |  |  |
| Kube Hunter | KubeEnforcer | Kubernetes | Lambda Amazon | Left |
 |  |  |  |  |
| Linux | Lock | Log | Logout | Malware Detection |
 |  |  |  |  |
| Malware Tracking | Mega Menu | Memory | MicroEnforcer | Microsoft Azure |
 |  |  |  |  |
| Misconfiguration | Mitigation | More Vertical | NanoEnforcer | Nautilus |
 |  |  |  |  |
| Network Connection | Network Connection WWW | No Orch | Nodes | Notification Panel |
 |  |  |  |  |
| Notifications | Off | OK | On | Open Source |
 |  |  |  |  |
| OpenShift | OS Package Manager | OSS License | Outbound Connection | Pending |
 |  |  |  |  |
| PHP | Plans and Prices | Plans Pricing | Play | Pod Enforcer |
 |  |  |  |  |
| Pods | Policies | Policy Violation | PostgreSQL | Privacy |
 |  |  |  |  |
| Privileged | Process | Prometheus | Propagation | Protect Containerized Apps |
 |  |  |  |  |
| Proxy | Quality Assurance | Question Round | Refresh | Registries |
 |  |  |  |  |
| Remediation | Reports | Reset | Resource | Reverse |
 |  |  |  |  |
| Right | SaaS | SAST | SBOM | Scanning |
 |  |  |  |  |
| Schedule | SCM Accounts | Search | Secrets | Security |
 |  |  |  |  |
| Security Camera | Security specialist | Sensitive Data | Services | Settings |
 |  |  |  |  |
| Settings Gear | Show More | SIEM | SOC | Speed |
 |  |  |  |  |
| Stamp | Storage | Storage 2 | Superuser | SupplyChain |
 |  |  |  |  |
| Support Website | Suppress | Table | TAS | Tenant Manager |
 |  |  |  |  |
| Third Party | Tools | Tree | Troubleshooting | Ubuntu |
 |  |  |  |  |
| Unknown Image | Up | Upload | Usage | Video Camera |
 |  |  |  |  |
| Virtual classroom | VM Enforcer | Volume | vShield | Vulnerability Score |
 |  |  |  |  |
| Warning | Warning Round | Weaponization | WordPress | Workloads |
 |  |  | | |
| Workloads Misconfiguration | ZoomIn | ZoomOut | | |
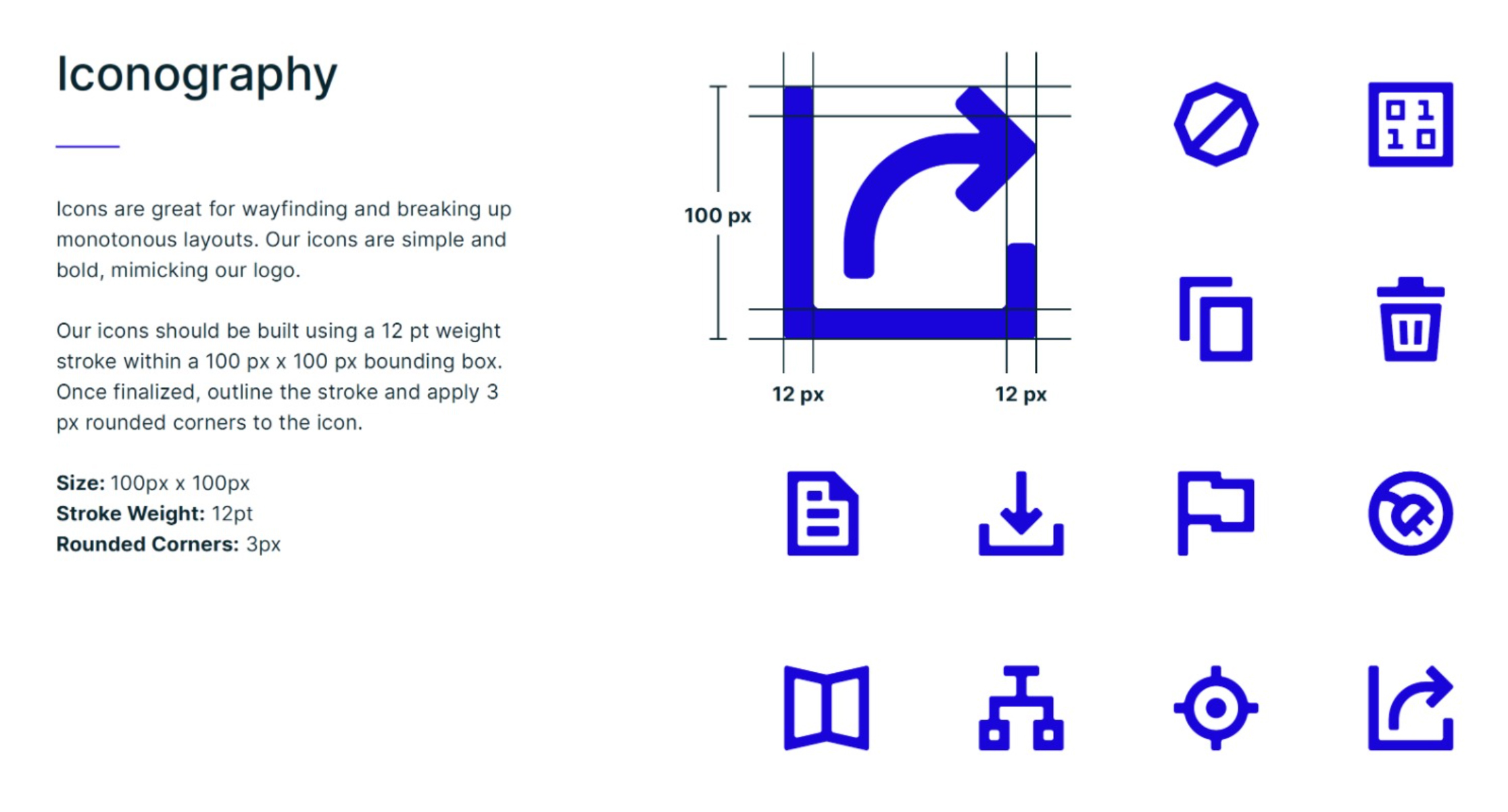
The icon grid establishes clear rules for the consistent, but flexible, positioning of graphic elements.
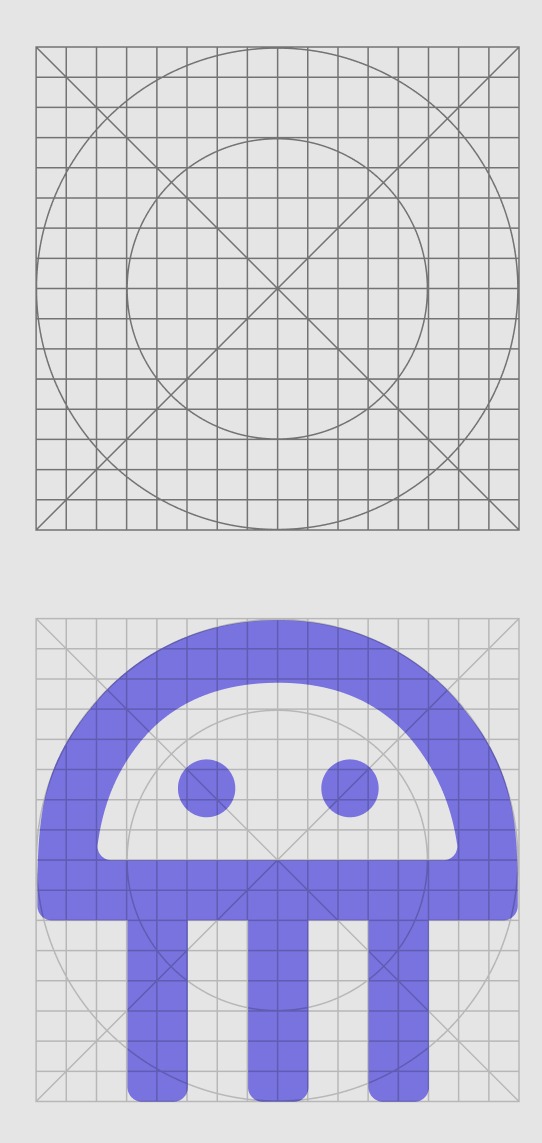
Keyline, minimalistic shapes are the foundation of the grid and define the boldness of our unique line of icons that reflect our values: We are the Experts, We are Bold. This grid was used also for the creation of Aqua Droplet Font.