This policy detects hosts vulnerable to CVE-2016-2118 (commonly known as
Badlock) by checking if a known vulnerable package version is currently
installed. The remediation policy keeps samba at the latest version
available.
Note: This policy currently covers centos 5 and 6. Please consider contributing support for more platforms.
This policy installs using a traditionally (but horribly written) Makefile To
install simply clone this repository, and then run make install
MASTERFILES=</path/to/policy_root>.
For example:
make install MASTERFILES=/tmp/example-a10042
After installing the policy into your policy set you need to add it to inputs so that it will be parsed.
If your running CFEngine 3.7.3, 3.8.1 or greater. You can use the augments
file to add it to inputs.
For example:
{
"inputs": [
"services/cfengine-CVE-2016-2118/main.cf"
]
}This bundle checks to see if the installed version of samba matches a known
vulnerable version as defined in data/$(sys.flavor).json for example:
data/centos_6.json. There are of course other methods like a package manager
itself that could be used to look for vulnerable versions.
This is an autorun bundle, so if your running the Masterfiles Policy Framework,
(the default policy CFEngine ships with) you can simply define the
services_autorun class.
{
"inputs": [
"services/cfengine-CVE-2016-2118/main.cf"
],
"classes": {
"services_autorun": [ "any" ]
}
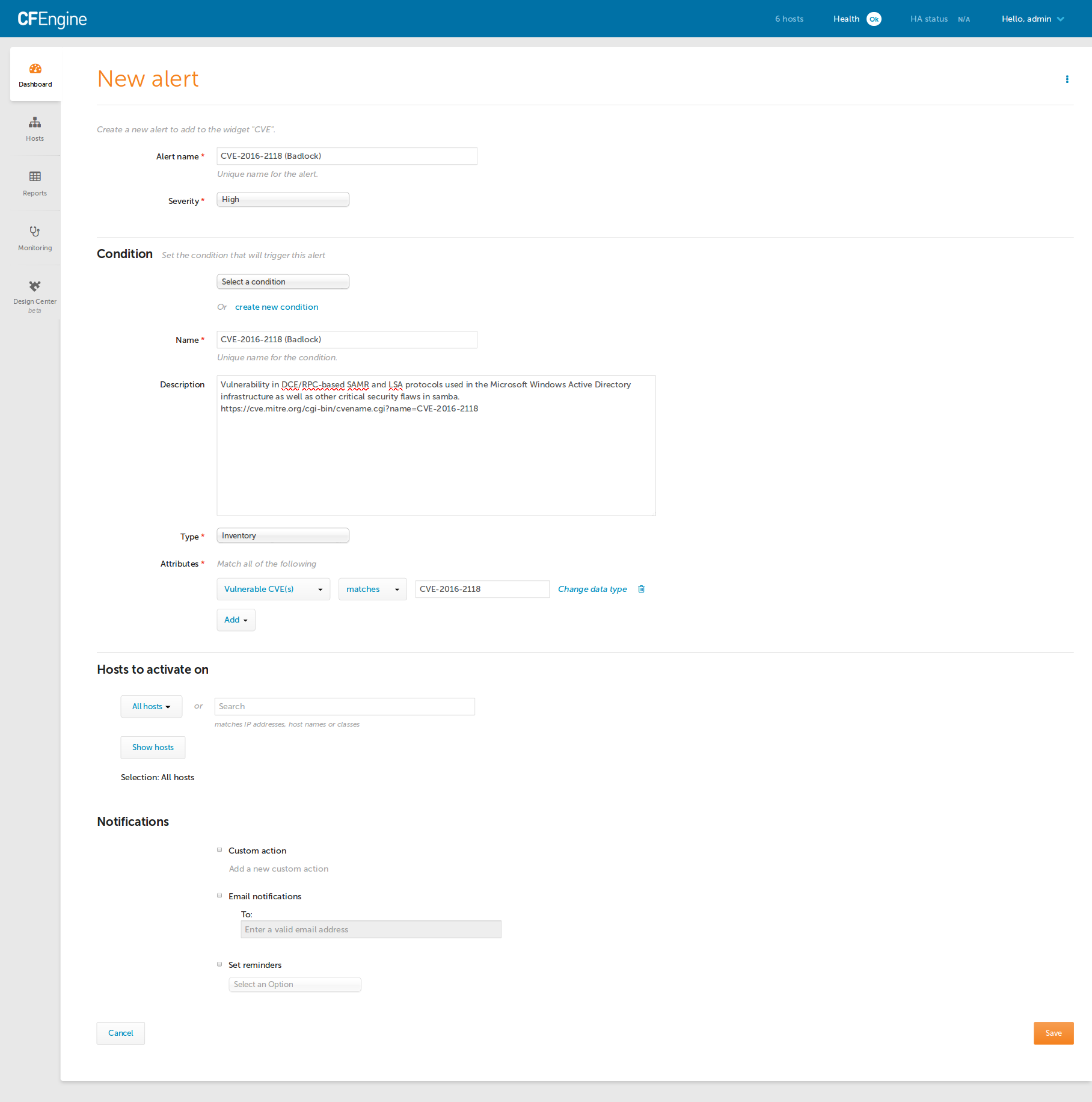
}**NOTE:** When the policy runs and detects a vulnerable host it emits a report
and defines the class CVE_2016_2118.
For example:
R: Detected Vulnerability: CVE-2016-2118
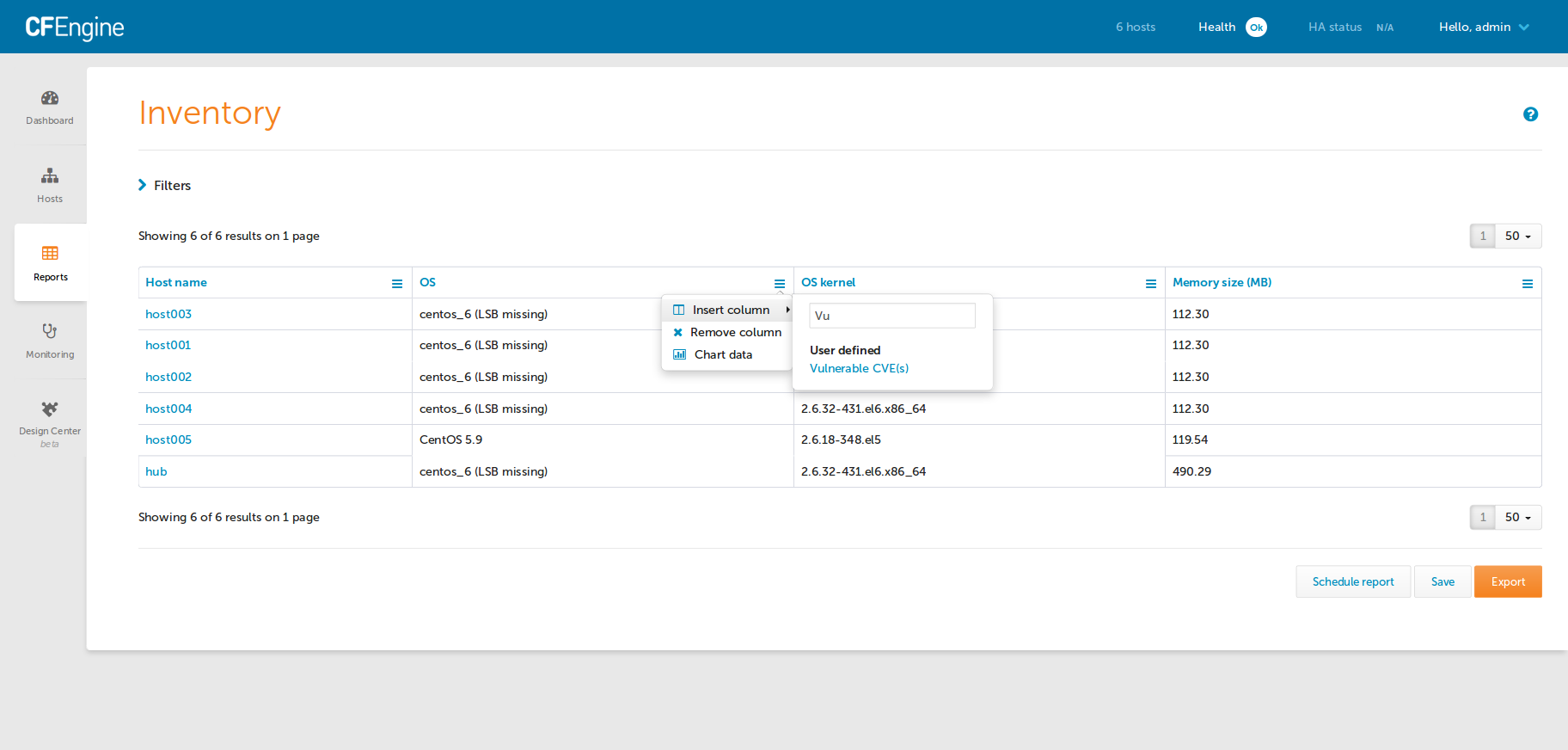
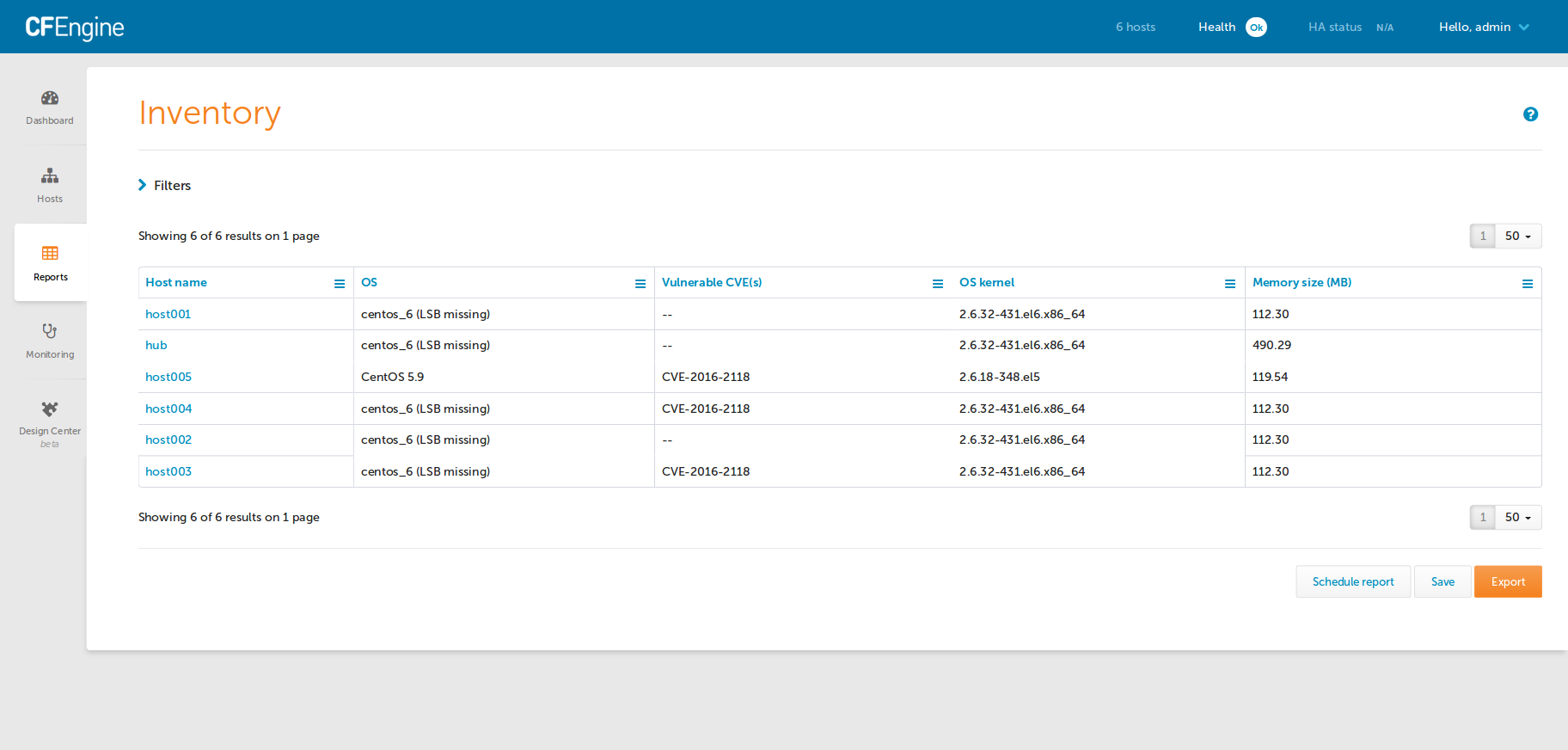
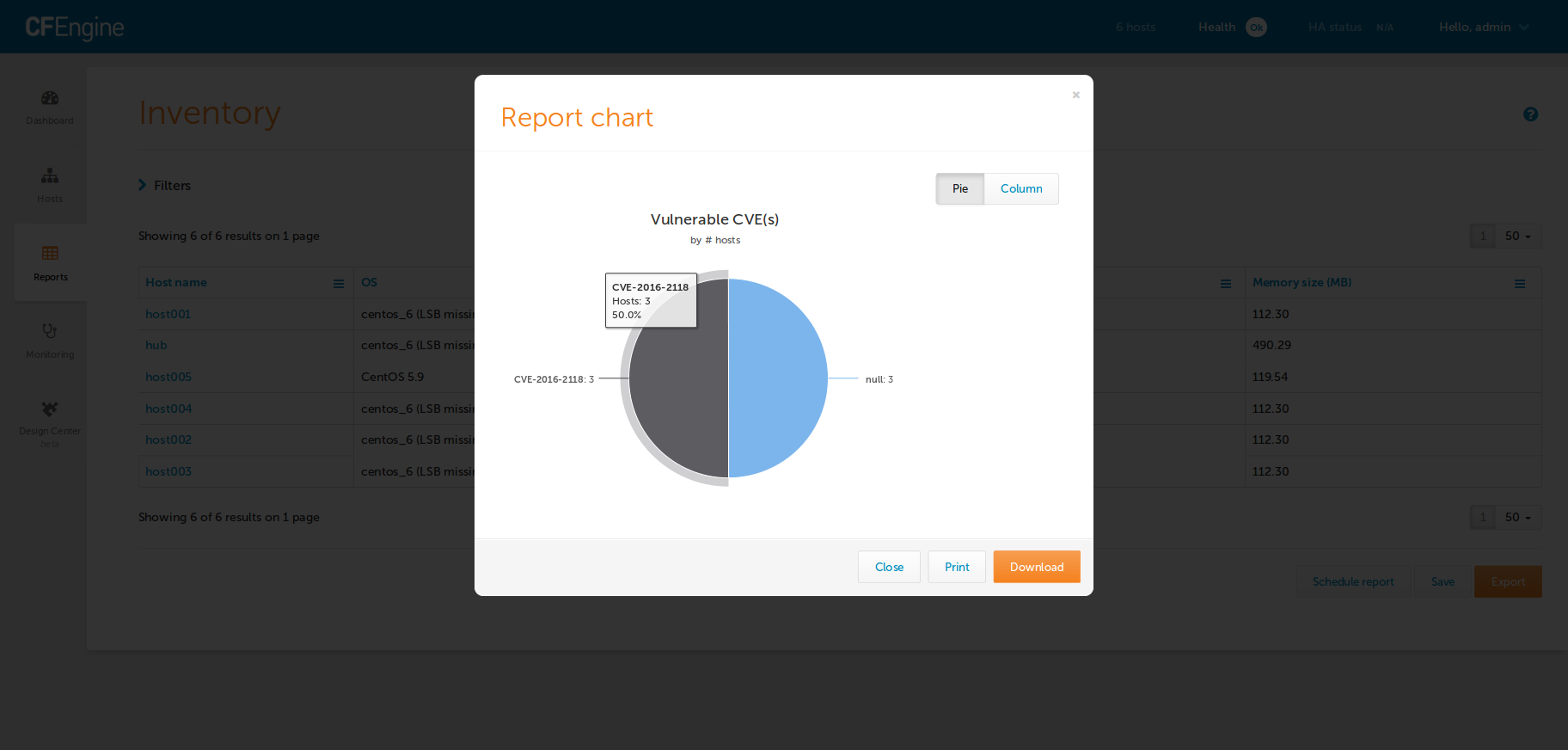
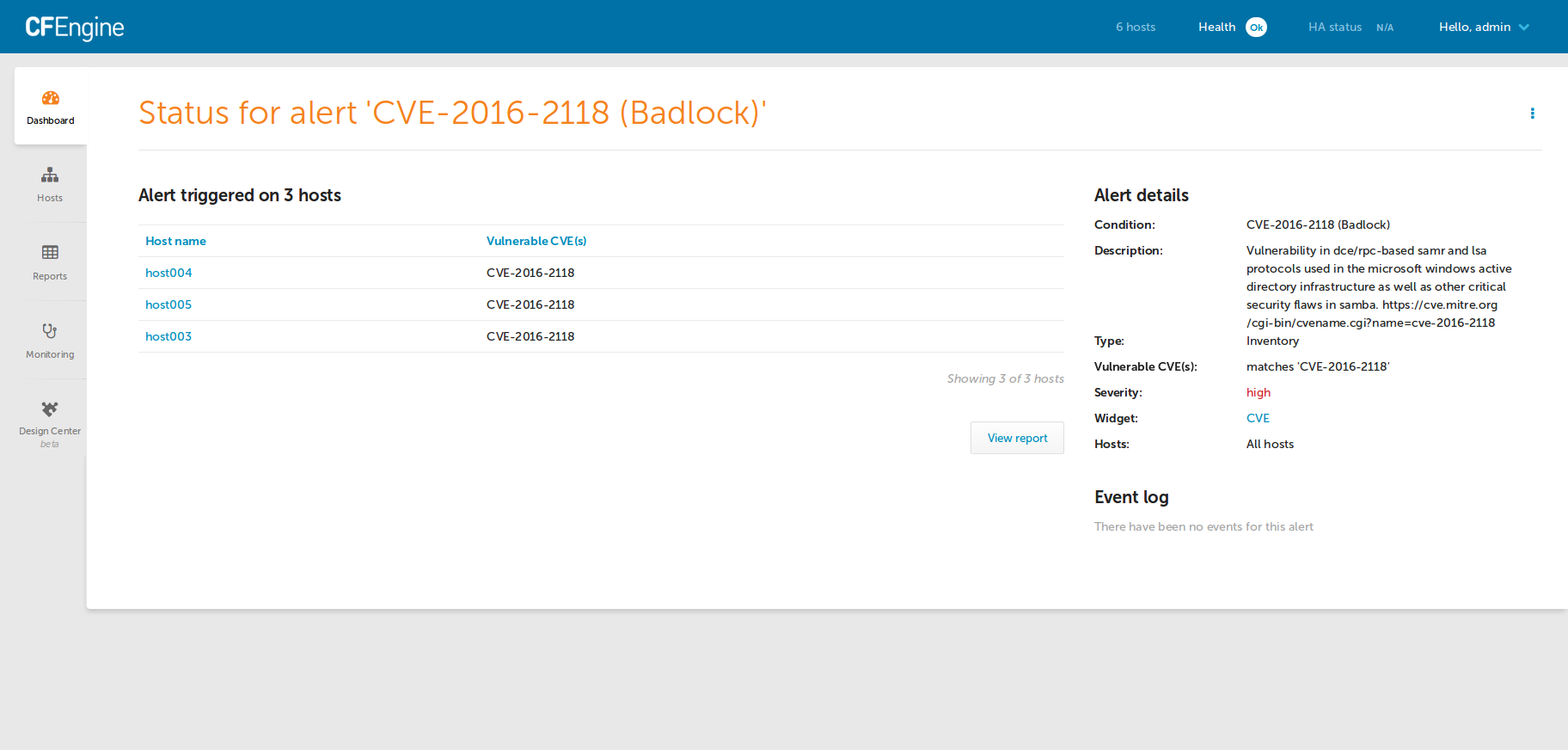
CFEngine Enterprise users will see the Inventory Reporting interface in Mission
Portal augmented with a new Vulnerable CVE(s) attribute.
For example:
remediate_CVE_2016_2118 is also an autorun bundle, but only when the
the remediate_CVE_2016_2118 class is defined.
There are numerous ways you can flexibly express which hosts and during what time periods automatic remediation is allowed.
If your running 3.7.3, 3.8.1 or greater you can enable it for your entire
infrastructure by adding it to the augments file.
{
"inputs": [
"services/cfengine-CVE-2016-2118/main.cf"
],
"classes": {
"services_autorun": [ "any" ],
"remediate_CVE_2016_2118": [ "any" ]
}
}The policy looks for the list of packages that are known to be vulnerable in a
json data file named for the systems flavor as identified by $(sys.flavor),
for example =centos_6=.