Expose your local resources to kubernetes
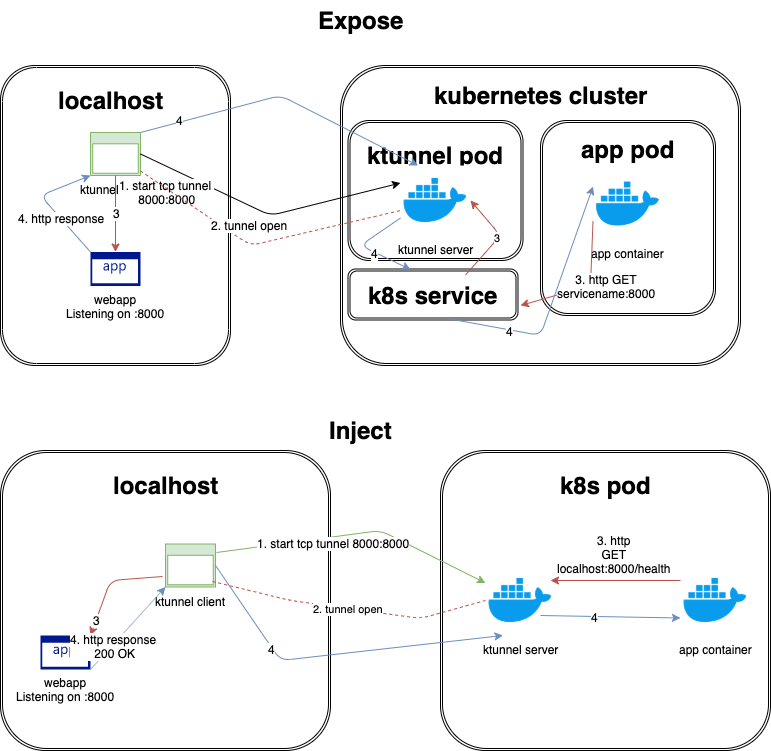
Ktunnel is a CLI tool that establishes a reverse tunnel between a kubernetes cluster and your local machine. It let's you expose your machine as a service in the cluster or expose it to a specific deployment. You can also use the client and server without the orchestration part.
ktunnel was born out of the need to access my development host when running applications on kubernetes. I specifically found it to be a challenge to run a remote pycharm debuuger on pods in a kubernetes development cluster. The aim of this project is to be an holistic solution to this specific problem(accessing the your local machine from a kubernetes pod) - although there are partial solutions to this problem such as inlets and ngrok I found them to be unsuitable and insecure for the task at hand. If you found this tool to be helpful on other scenarios(accessing a seeded development database/mocking a service and whatnot) I would love for us to communicate on that.
These instructions will get you a copy of the project up and running on your local machine for development and testing purposes. See deployment for notes on how to deploy the project on a live system.
You should have proper permissions on the kubernetes cluster
Download here and extract it to a local bin path
Clone the project
git clone https://github.com/omrikiei/ktunnel; cd ktunnel
Build the binary
CGO_ENABLED=0 go build -ldflags="-s -w"
You can them move it to your bin path
sudo mv ./ktunnel /usr/local/bin/ktunnel
Test the commamd
ktunnel -h
This will allow pods in the cluster to access your local web app(listening on port 8000) via http(i.e pods can send requests to myapp:8000)
ktunnel expose myapp 80:8000This will currently only work for deployments with 1 replica - it will expose a listening port on the pod through a tunnel to your local machine
ktunnel inject deployment mydeployment 3306See also the list of contributors who participated in this project.