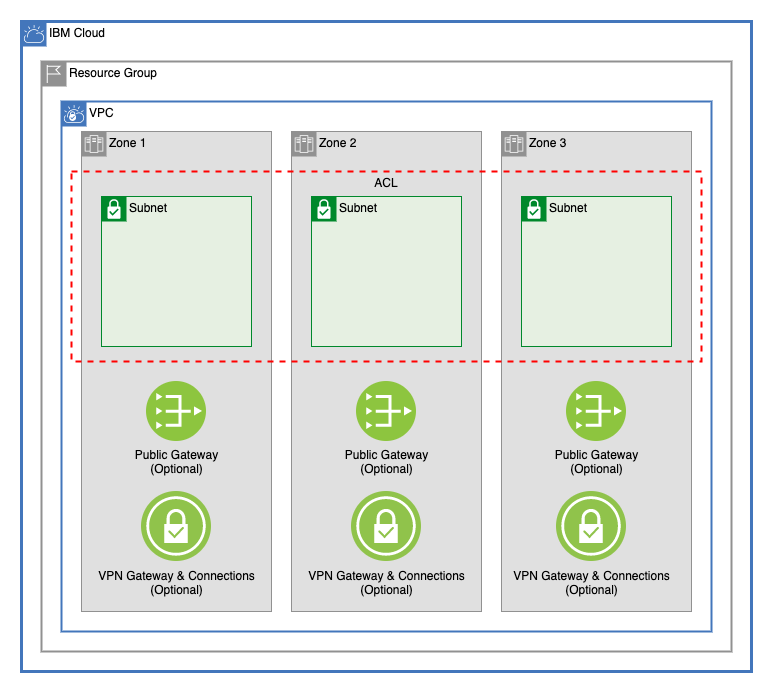
This module creates the following IBM Cloud® Virtual Private Cloud (VPC) network components:
- VPC: Creates a VPC in a resource group and supports classic access. The VPC and components are specified in the main.tf file.
- Public gateways: Optionally create public gateways in the VPC in each of the three zones of the VPC's region.
- Subnets: Create one to three zones in the subnet.tf file.
- Network ACLs: Create network ACLs with multiple rules. By default, VPC network ACLs can have no more than 25 rules.
- VPN gateways: Create VPN gateways on your subnets by using the
vpn_gatewaysvariable. For more information about VPN gateways on VPC, see About site-to-site VPN gateways in the IBM Cloud docs. - VPN gateway connections: Add connections to a VPN gateway.
module vpc {
# Replace "master" with a GIT release version to lock into a specific release
source = "git::https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone-vpc.git?ref=master"
resource_group_id = var.resource_group_id
region = var.region
prefix = var.prefix
tags = var.tags
vpc_name = var.vpc_name
classic_access = var.classic_access
network_acls = var.network_acls
use_public_gateways = var.use_public_gateways
subnets = var.subnets
vpn_gateways = var.vpn_gateways
}You can create a maximum of three zones in the subnet.tf file. The zones are defined as lists in the file, and then are converted to objects before the resources are provisioned. The conversion ensures that the addition or deletion of subnets affects only the added or deleted subnets, as shown in the following example.
module.subnets.ibm_is_subnet.subnet["gcat-multizone-subnet-a"]
module.subnets.ibm_is_subnet.subnet["gcat-multizone-subnet-b"]
module.subnets.ibm_is_subnet.subnet["gcat-multizone-subnet-c"]
module.subnets.ibm_is_vpc_address_prefix.subnet_prefix["gcat-multizone-subnet-a"]
module.subnets.ibm_is_vpc_address_prefix.subnet_prefix["gcat-multizone-subnet-b"]
module.subnets.ibm_is_vpc_address_prefix.subnet_prefix["gcat-multizone-subnet-c"]You need the following permissions to run this module.
- IAM services
- VPC Infrastructure services
Editorplatform access
- No service access
- Resource Group <your resource group>
Viewerresource group access
- VPC Infrastructure services
| Name | Version |
|---|---|
| terraform | >= 1.0.0 |
| ibm | >= 1.45.0 |
| Name | Source | Version |
|---|---|---|
| dynamic_values | ./dynamic_values | n/a |
| unit_tests | ./dynamic_values | n/a |
| Name | Type |
|---|---|
| ibm_is_network_acl.network_acl | resource |
| ibm_is_public_gateway.gateway | resource |
| ibm_is_security_group_rule.default_vpc_rule | resource |
| ibm_is_subnet.subnet | resource |
| ibm_is_vpc.vpc | resource |
| ibm_is_vpc_address_prefix.address_prefixes | resource |
| ibm_is_vpc_address_prefix.subnet_prefix | resource |
| ibm_is_vpc_routing_table.route_table | resource |
| ibm_is_vpc_routing_table_route.routing_table_routes | resource |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| address_prefixes | OPTIONAL - IP range that will be defined for the VPC for a certain location. Use only with manual address prefixes | object({ |
{ |
no |
| classic_access | OPTIONAL - Classic Access to the VPC | bool |
false |
no |
| default_network_acl_name | OPTIONAL - Name of the Default ACL. If null, a name will be automatically generated | string |
null |
no |
| default_routing_table_name | OPTIONAL - Name of the Default Routing Table. If null, a name will be automatically generated | string |
null |
no |
| default_security_group_name | OPTIONAL - Name of the Default Security Group. If null, a name will be automatically generated | string |
null |
no |
| name | Name for VPC | string |
n/a | yes |
| network_acls | List of ACLs to create. Rules can be automatically created to allow inbound and outbound traffic from a VPC tier by adding the name of that tier to the network_connections list. Rules automatically generated by these network connections will be added at the beginning of a list, and will be web-tierlied to traffic first. At least one rule must be provided for each ACL. |
list( |
[ |
no |
| network_cidr | Network CIDR for the VPC. This is used to manage network ACL rules for cluster provisioning. | string |
"10.0.0.0/8" |
no |
| prefix | The prefix that you would like to append to your resources | string |
n/a | yes |
| region | The region to which to deploy the VPC | string |
n/a | yes |
| resource_group_id | The resource group ID where the VPC to be created | string |
n/a | yes |
| routes | OPTIONAL - Allows you to specify the next hop for packets based on their destination address | list( |
[] |
no |
| security_group_rules | A list of security group rules to be added to the default vpc security group | list( |
[ |
no |
| subnets | List of subnets for the vpc. For each item in each array, a subnet will be created. Items can be either CIDR blocks or total ipv4 addressess. Public gateways will be enabled only in zones where a gateway has been created | object({ |
{ |
no |
| tags | List of Tags for the resource created | list(string) |
null |
no |
| use_manual_address_prefixes | OPTIONAL - Use manual address prefixes for VPC | bool |
false |
no |
| use_public_gateways | Create a public gateway in any of the three zones with true. |
object({ |
{ |
no |
| Name | Description |
|---|---|
| network_acls | List of shortnames and IDs of network ACLs |
| public_gateways | Map of public gateways by zone |
| subnet_detail_list | A list of subnets containing names, CIDR blocks, and zones. |
| subnet_ids | The IDs of the subnets |
| subnet_zone_list | A list containing subnet IDs and subnet zones |
| vpc_crn | CRN of VPC created |
| vpc_id | ID of VPC created |
| vpc_name | Name of VPC created |
You can report issues and request features for this module in GitHub issues in the module repo. See Report an issue or request a feature.
To set up your local development environment, see Local development setup in the project documentation.
-brightgreen?style=plastic)