This is currently an experimental project.
This repository contains everything needed to configure an environment in order to build and release Jenkins versions.
The purpose of this project is to define the same process to build and release Jenkins regardless that we are in the 'release', 'security' or in any development environment.
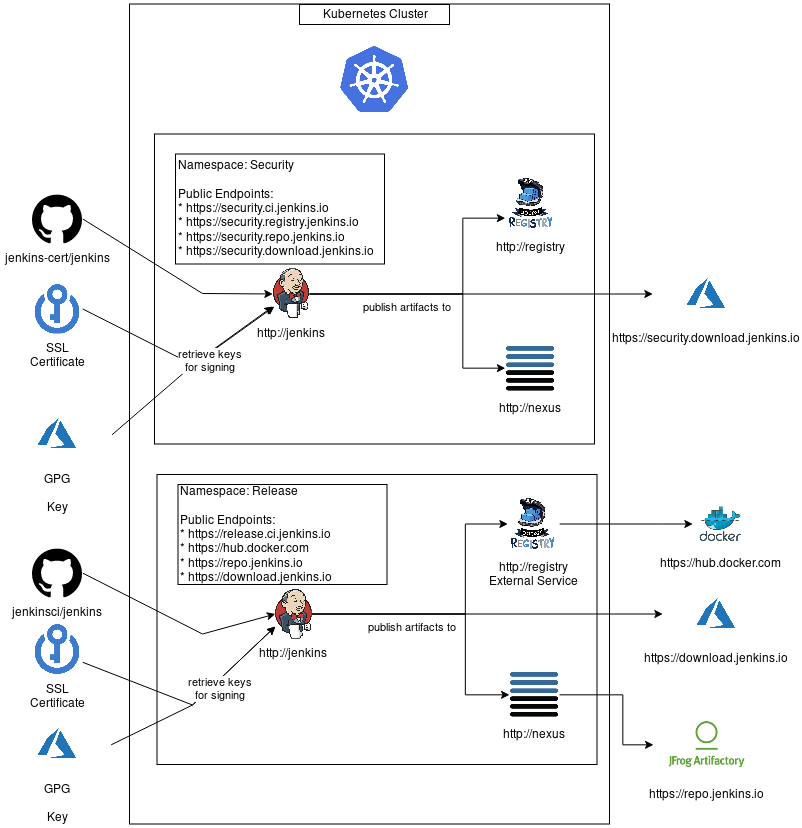
The idea is to deploy, configure, and isolate all services needed to build and release a specific version inside a kubernetes namespace. So we can use the same internal endpoints everywhere (http://jenkins, http://nexus, http://registry,etc.) and use the kubernetes service type "externalName" to map an internal services like http://nexus to external services like https://repo.jenkins.io when needed.
The only thing that would need to change depending on the environment would be the credentials used to access those various services and a flag that define if we deploy services or just map some internal endpoint with an external services docker hub or repo.jenkins.io.
The benefits of this approach are multiple:
- The process to release a new version is totally transparent
- Everybody can deploy a release environment even on Minikube
- We can have a clear separation of who has access to which environment
The following diagram shows a big picture of what the environments could looks like where security environment deploy all services on kubernetes and 'release' just deploy a jenkins instance and the other services are mapped with external services.
In order to use this repository, you gonna need
- kubernetes
- Jenkins-x
- Helm
- Sops
- Make
- Azure Key Vault with a ssl cert
- Azure Blob Storage with a password protected gpg key
Once you have all the requirements, you can:
- Create myvalues.yaml based on myvalues.release.yaml ! Never commit myvalues.yaml
- Install jenkins-x on your cluster
make init - Install your build environment
make install - Import your jenkins git repository
make import(currently set to olblak/jenkins) - Retrieve your jenkins url
jx get urls - Use jenkins password defined in myvalues.yaml or in ~/.jx/adminSecrets.yaml
- Look at the build job
- Jenkins should contains following plugins by default
- ssh-agent
- pipeline-utility-steps
- ldap
As of today, we use nexus repository as jenkins-x already deploys it by default
- Automate Artifactory configuration with:
- A remote maven repository named 'repo1' in front of https://repo.jenkins-ci.org/repo1/, in order to retrieve and cache existing maven artifacts
- A local maven repository named 'sandbox', in order to publish new artifacts and share them with collaborators
- Install Artifactory service with different behaviour depending on the environment we are.
- Default Artifactory service which redirect to local artifactory instance
- Release environment that defines an ExternalName service type that redirect to repo.jenkins-ci.org
- Configure olblak/jenkins to push artifacts on the local artifactory called 'artifactory'
- Non-release environment should be able to sign with a dumb gpg certificate in order to remove Azure Storage Account requirement
- Non-release environment should be able to sign with a dumb ssl certificate in order to remove Azure Key Vault requirement
Various
- ExternalName Service type
- Github Webhook Proxy
- ssh-authentication-git
- PR
- SSO