The Requirements for this project are:
- xclip
- xautomation
- X11
- Xinerama
- Xft
- git
- notify-send
Clone the repository into /opt directory:
sudo git clone https://github.com/Cipher7/dmenu_pentest.git
sudo chmod +x install.sh
sudo ./install.sh
The install.sh will apply the necessary patches followed by making a clean install of the custom dmenu.
After the installation in complete. Assign a shortcut to the dmenu_pentest script by going to the keyboard settings in your linux machine and adding the shortcut. I have chosen the Ctrl+D shortcut forinvoking the script but you can make it whatever you want.
In the keyboard shortcuts just add:
bash /opt/dmenu_pentest/dmenu_pentest.sh
And then assign a shotcut to it!
Now you should be able to call the script with just the shortcut!
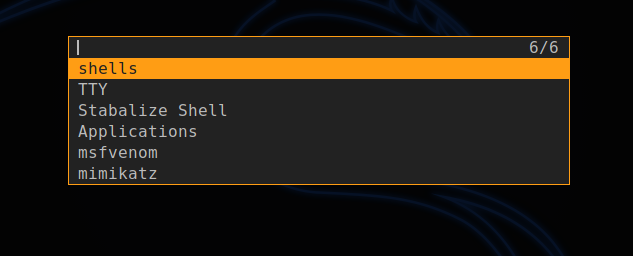
The Menu now can be accessed using just the shortcut you created in the installation phase and arrow keys to move around and the enter key to select an options.
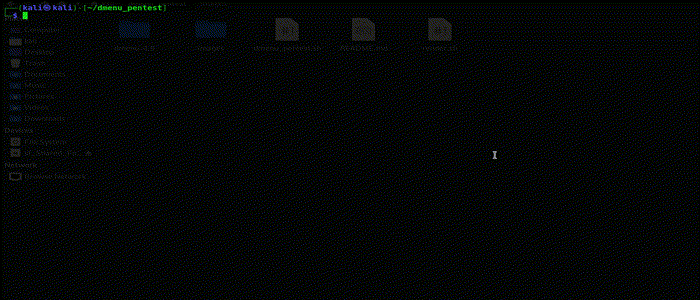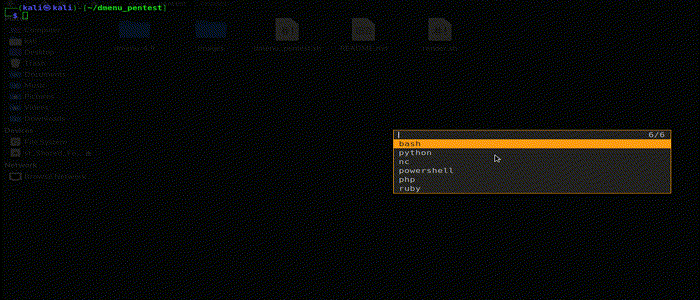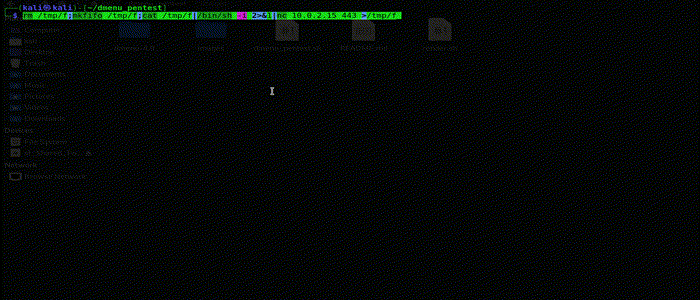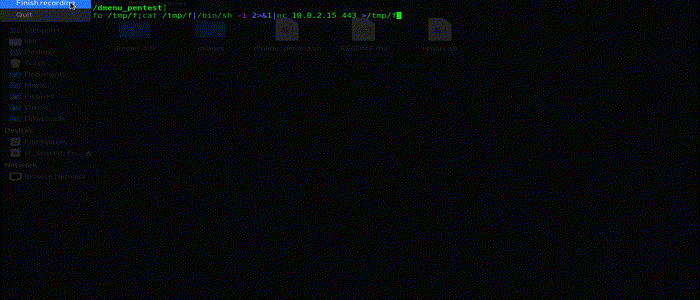
This options allows you to create a one liner reverse shell with your choice of IP and Port and then copies it to your clipboard.
It created one liners in :
- bash
- nc
- php
- powershell
- python
- ruby
This option copies a TTY shell to your clipboard.
It creates tty for:
- python
- python3
- os-system
Selecting this option will instantly stabalize your shell and give it a tty.
This option allows you to start an application from your system. If this options is run by a non-rootuser, it will prompt you for the sudo password and then execute the application as root.
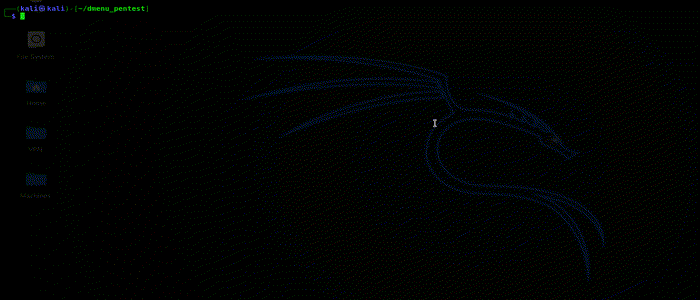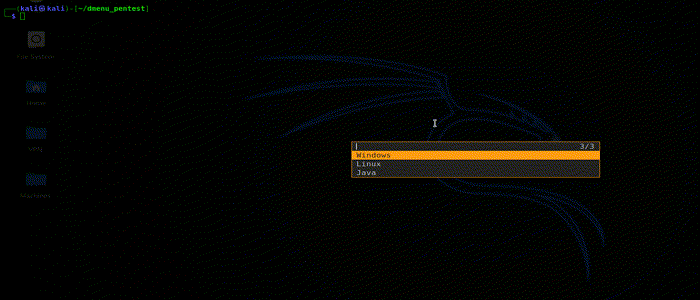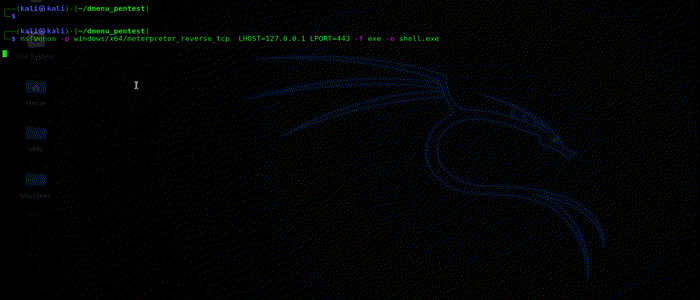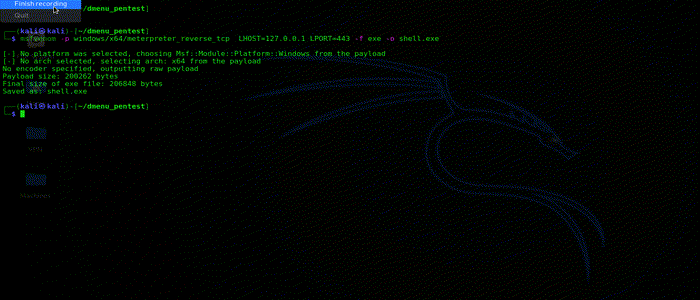
This option will allow you to create a msfvenom payload , by going through its options and selecting you IP and port. This will create a one liner msfvenom command for that payload and copy it to your clipboard. You can now just paste it in your terminal and create a msfvenom payload.
This currently supports:
-
Windows (x86 and x64)
- bind
- reverse
-
Linux (x86 and x64)
- bind
- reverse
-
Java
- jsp_reverse_shell
Copies the selected command to your clipboard.
Currently supports:
- privilege::debug
- sekurlsa::logonPasswords
- lsadump::sam
- Leo Smith : Thank you for the bug fixes and introducing me to dMenu!
- John Hammond : For the idea of adding xautomation