This sample demonstrates how to create a Linux Virtual Machine in a virtual network that privately accesses Azure File Share and an ADLS Gen 2 blob storage account using two Azure Private Endpoints. Azure Private Endpoint is a network interface that connects you privately and securely to a service powered by Azure Private Link. Private Endpoint uses a private IP address from your virtual network, effectively bringing the service into your virtual network. The service could be an Azure service such as Azure Storage, Azure Cosmos DB, SQL, etc. or your own Private Link Service. For more information, see What is Azure Private Link?. For more information on the DNS configuration of a private endpoint, see Azure Private Endpoint DNS configuration.
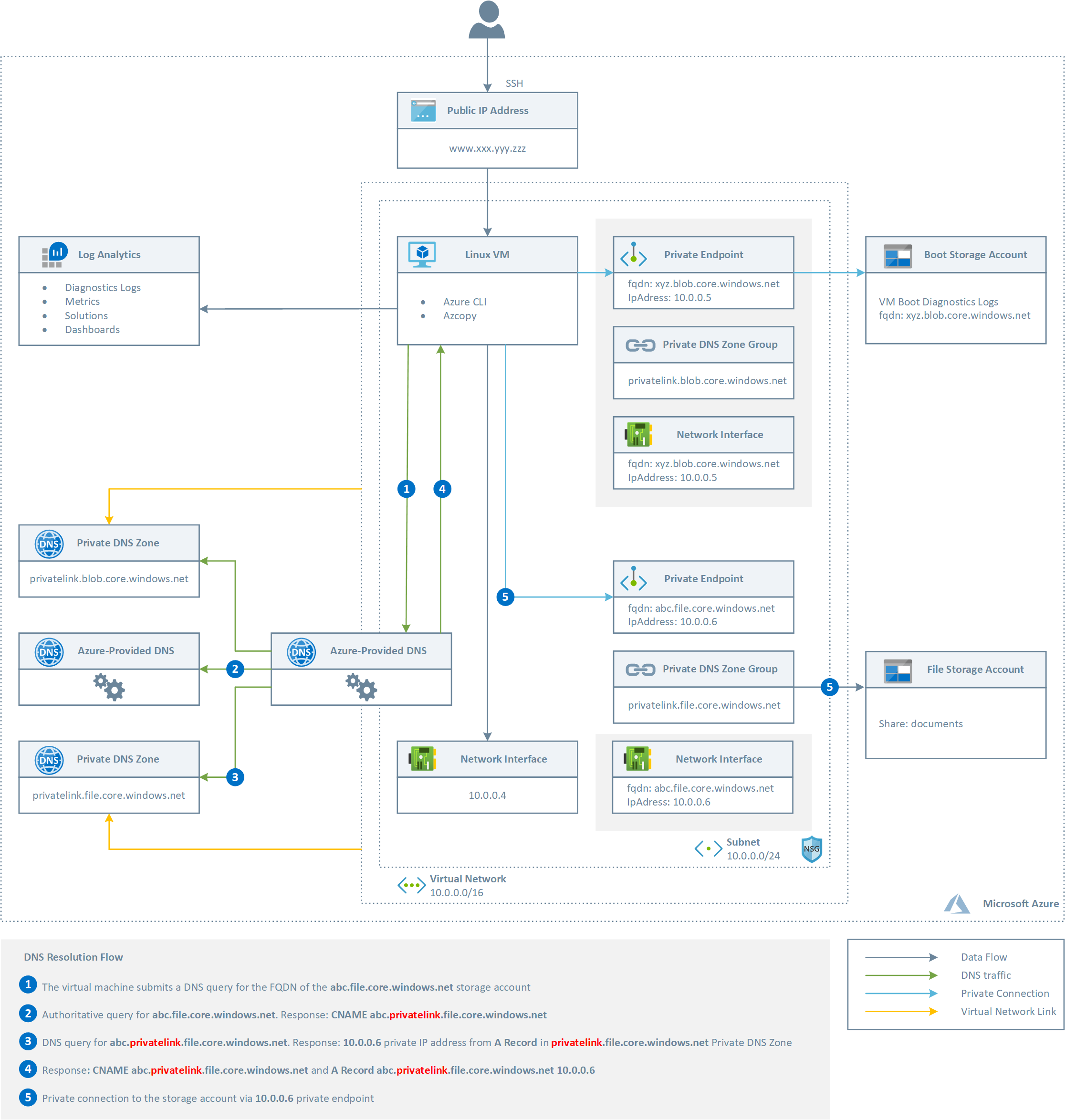
The following picture shows the architecture and network topology of the sample.
The ARM template deploys the following resources:
- Virtual Network: this virtual network has a single subnet that hosts an Linux (Ubuntu) virtual machine
- Network Security Group: this resource contains an inbound rule to allow the access to the virtual machine on port 22 (SSH)
- The virtual machine is created with a managed identity which is assigned the contributor role at the resource group scope level
- A Public IP for the Linux virtual machine
- The NIC used by the Linux virtual machine that makes use of the Public IP
- A Linux virtual machine used for testing the connectivity to the storage account via a private endpoint
- A Log Analytics workspace used to monitor the health status of the Linux virtual machine
- An ADLS Gen 2 storage account used to store the Azure File Share
- An ADLS Gen 2 storage account used to store the boot diagnostics logs of the virtual machine as blobs
- A Private DNS Zone for File Storage Account private endpoints (privatelink.file.core.windows.net)
- A Private DNS Zone for Blob Storage Account private endpoints (privatelink.blob.core.windows.net)
- A Private Endpoint to let the virtual machine access the Azure File Share via a private IP address
- A Private Endpoint to let the virtual machine store boot diagnostics logs to the second storage account via a private IP address
- A Private DNS Zone Group for the File Storage Account private endpoint
- A Private DNS Zone Group for the Blob Storage Account private endpoint
The PrivateDnsZoneGroup resource type establishes a relationship between the Private Endpoint and the Private the privatelink.* DNS zone for the name resolution of the fully qualified name of the resource referenced by the Private Endpoint.
- When creating a Private Endpoint, the related A record will automatically be created in the target Private DNS Zone with the private IP address of the network interface associated to the Private Endpoint and the name of the Azure resource referenced by the Private Endpoint
- When deleting a Private Endpoint, the related A record gets automatically deleted from the corresponding Private DNS Zone.
The two storage accounts are accessed via a different endpoint, hence their private endpoints need different Private DNS Zone:
| Storage Service | Zone Name |
|---|---|
| Blob service | privatelink.blob.core.windows.net |
| File service | privatelink.file.core.windows.net |
For more information, see Use private endpoints for Azure Storage.
The ARM template uses the Azure Custom Script Extension to download and run the following Bash script on the virtual machine. The script performs the following steps:
- Validates the parameters received by the Custom Script extension
- Updates the system and upgrades packages
- Installs curl and traceroute packages
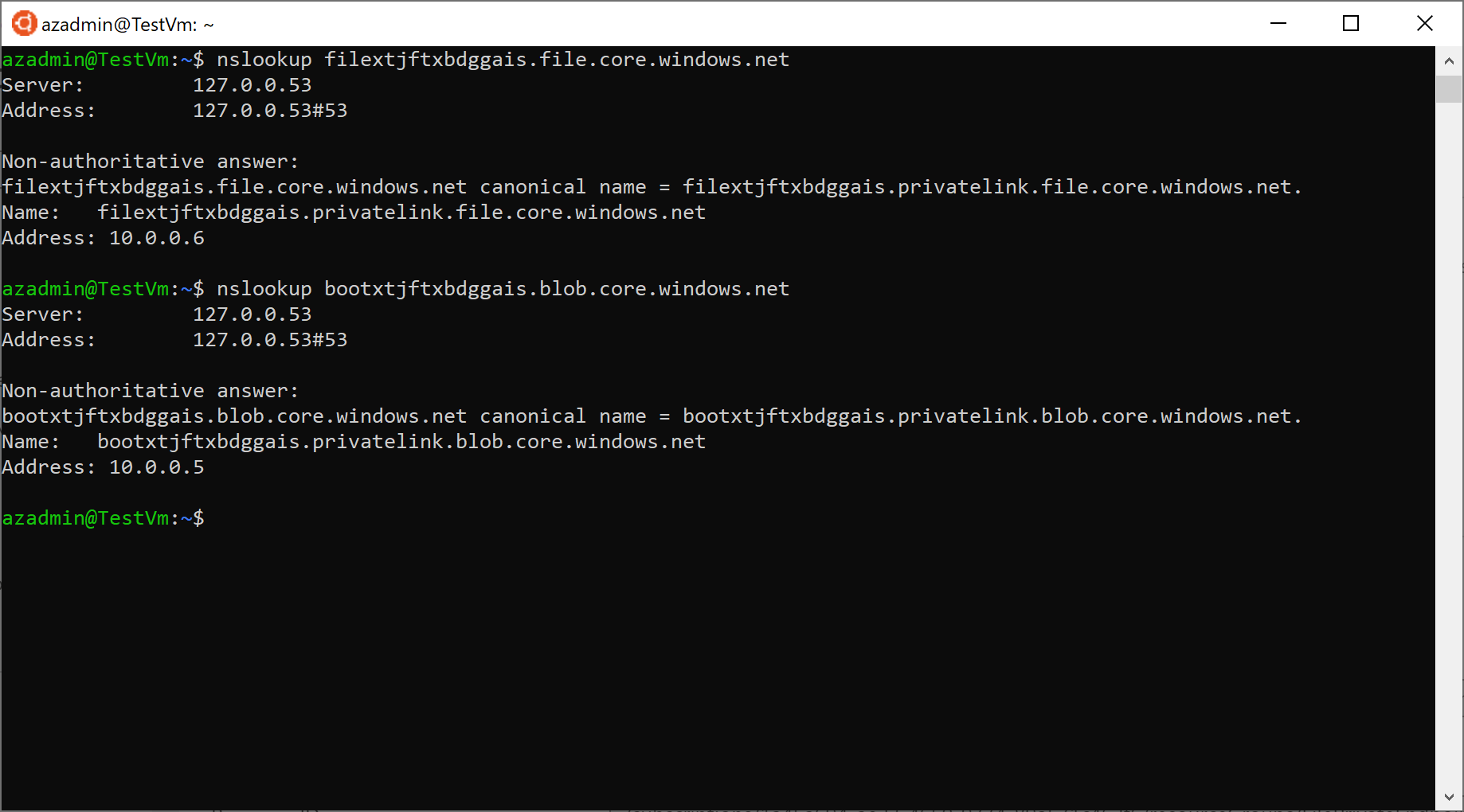
- Runs the nslookup command against the public URL of the ADLS Gen 2 storage account to verify that this gets resolved to a private address
- Runs the nslookup command against the public URL of the second storage account to verify that this gets resolved to a private address
#!/bin/bash
# Variables
fileServicePrimaryEndpoint=$1
blobServicePrimaryEndpoint=$2
# Parameters validation
if [[ -z $fileServicePrimaryEndpoint ]]; then
echo "fileServicePrimaryEndpoint parameter cannot be null or empty"
exit 1
fi
if [[ -z $blobServicePrimaryEndpoint ]]; then
echo "blobServicePrimaryEndpoint parameter cannot be null or empty"
exit 1
fi
# Eliminate debconf warnings
echo 'debconf debconf/frontend select Noninteractive' | debconf-set-selections
# Update the system
sudo apt-get update -y
# Upgrade packages
sudo apt-get upgrade -y
# Run nslookup to verify that public hostname of the Service Bus namespace
# is properly mapped to the private address of the provate endpoint
nslookup $fileServicePrimaryEndpoint
# Run nslookup to verify that public hostname of the Blob storage account
# is properly mapped to the private address of the provate endpoint
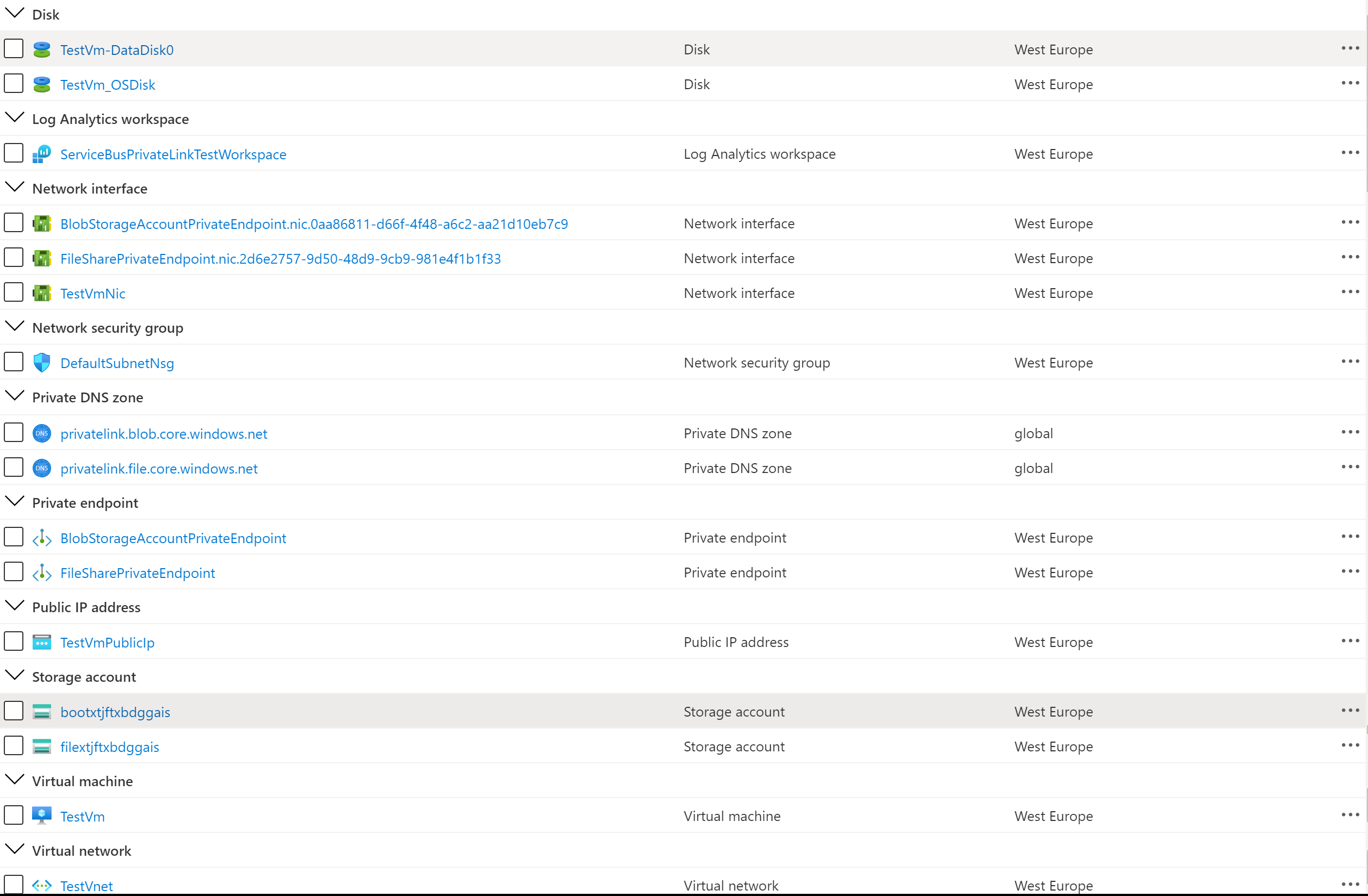
nslookup $blobServicePrimaryEndpointYou can use the template.json ARM template and parameters.json file included in this repository to deploy the sample. Make sure to edit the parameters.json file to customize the installation. You can also use the deploy.sh Bash script under the scripts folder to deploy the ARM template. The following figure shows the resources deployed by the ARM template in the target resource group.
if you open an ssh session to the Linux virtual machine and manually run the nslookup command, you should see an output like the following: