Note
This plugin is DEPRECATED as of February 12, 2024.
We recommend using the AWS SAM build images directly using Jenkins Pipeline.
See here for more information.
The AWS Serverless Application Model (SAM) is an open-source framework you can use to build serverless applications on AWS.
This plugin helps you automate the deployments of your applications that are defined using SAM.
- Custom build step
samDeployPipeline step- Deploy SAM applications to AWS
- Package SAM applications to a S3 bucket
- Use specific or auto-created S3 bucket (if not given, a bucket will be automatically created in your account for you)
- Template parameters support
- Template tags support
- Deploy to a specific region
- Use an S3 prefix for packaged artifacts to have fine-grained control of where artifacts are uploaded
- Use a specific KMS key for encrypting packaged artifacts at rest in S3
- Configurable deployment role
- Navigate to your Jenkins server
- On the left, click "Manage Jenkins"
- Scroll down to find "Manage Plugins" and click it
- Look for the "AWS SAM" plugin
In order to deploy to AWS you must have an AWS account. Visit https://aws.amazon.com if you do not have one.
Before you can start building, you must have your AWS credentials set up in Jenkins. To do this:
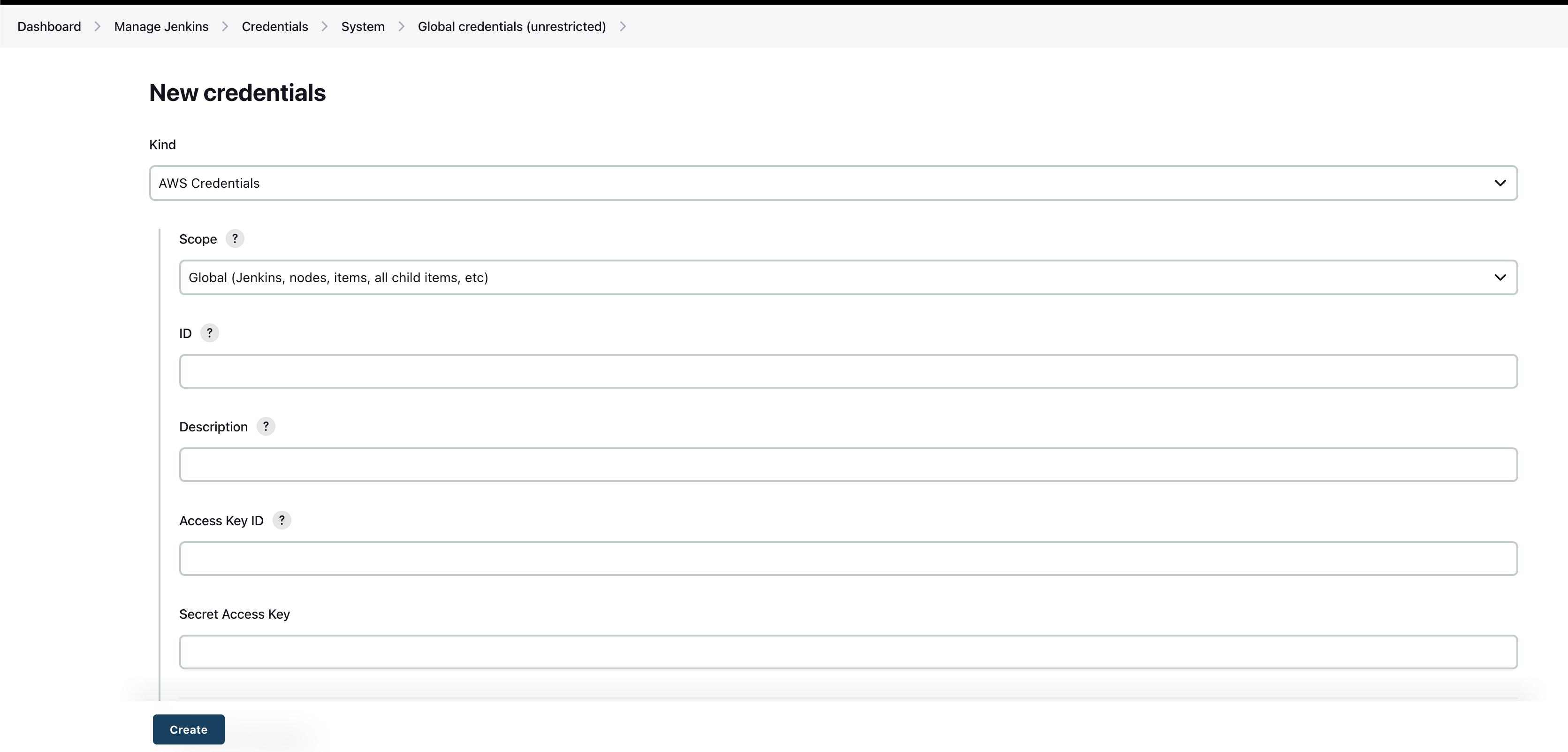
- From the main page of your jenkins server go to "Manage Jenkins" > "Manage Credentials" and then click on "Global" domain.
- Click "Add Credentials."
- Select from the "Kind" dropdown "AWS Credentials". If "AWS Credentials" do not exist, please check if you have
AWS SAMplugin installed - Finish the form with your AWS access keys and click "OK."
For deployment you'll need access to an S3 bucket (or permission to create one), CloudFormation and ChangeSet IAM lifecycle actions, as well as any IAM permissions required to create the resources in your SAM (CloudFormation) template.
Version: '2012-10-17'
Statement:
- Sid: SAMS3Actions
Resource: '*'
Effect: Allow
Action:
- s3:CreateBucket
- s3:GetBucketLocation
- s3:ListBucket
- s3:PutObject
- s3:PutObjectAcl
- s3:PutObjectTaggingVersion: '2012-10-17'
Statement:
- Sid: SAMCloudFormationActions
Resource: '*'
Effect: Allow
Action:
- cloudformation:ValidateTemplate
- cloudformation:DescribeStacks
- cloudformation:CreateChangeSet
- cloudformation:DescribeChangeSet
- cloudformation:ExecuteChangeSetThere are a few steps to configuring your build.
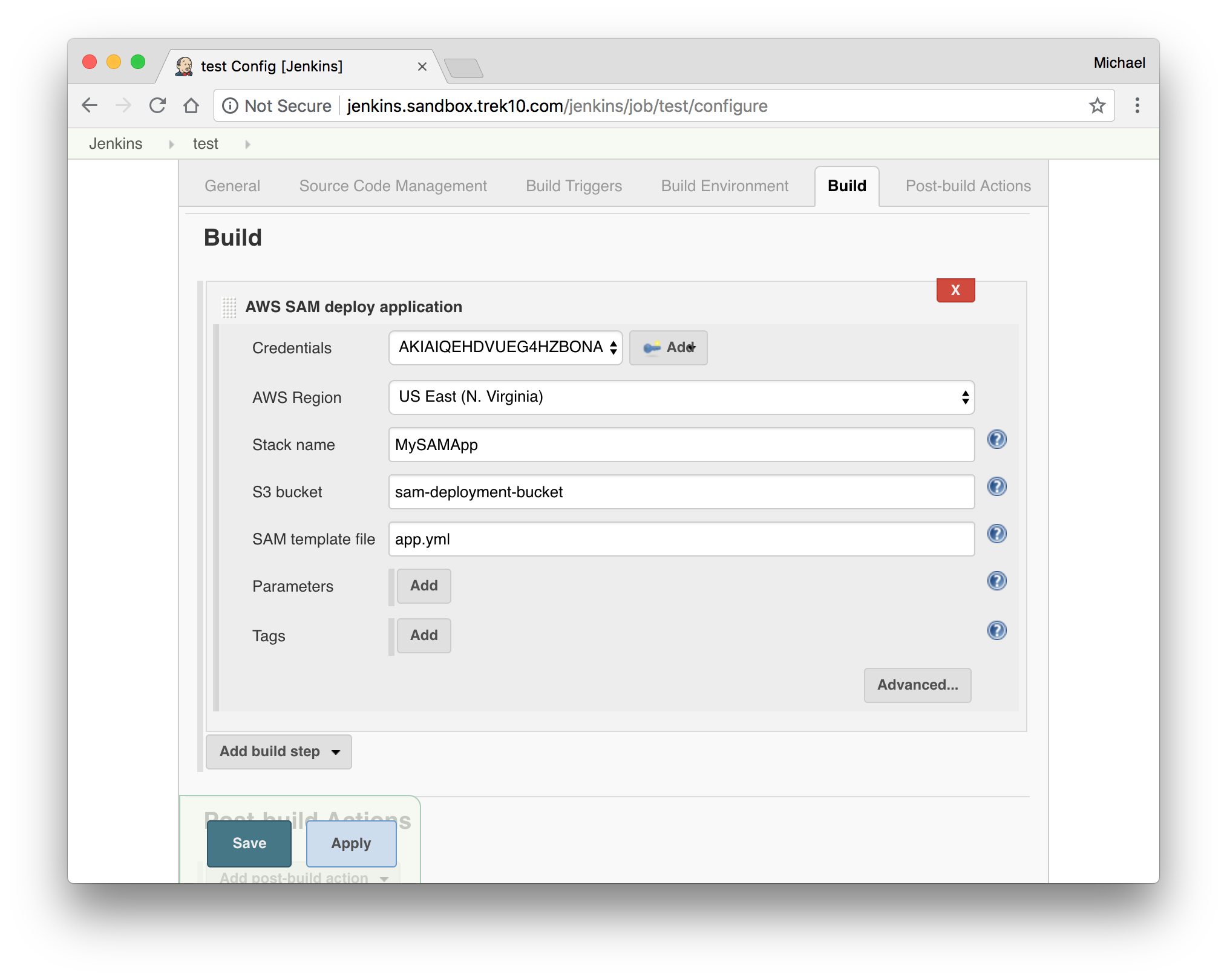
- In your project configuration, scroll down to build steps.
- Add the "AWS SAM deploy application" build step.
- Select your AWS Credentials from the dropdown.
- Select the target region to deploy to.
- Give the build step a stack name.
- Optional: Enter an S3 bucket name to package the artifacts to.
- If you leave this blank, the S3 bucket will be auto-generated.
- Give the path to the SAM template file.
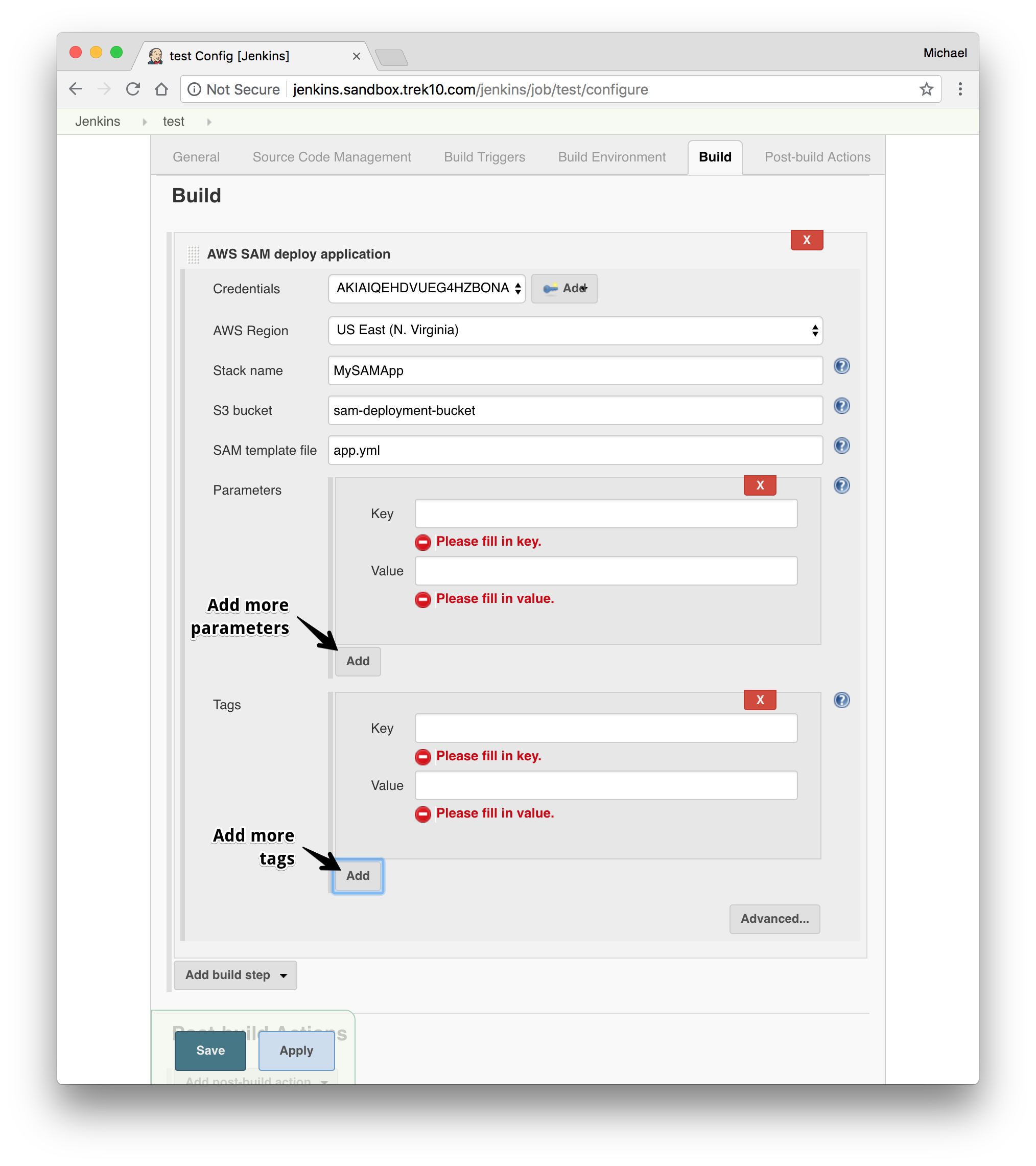
- Optional: If your template has parameters, add parameters where necessary.
- Optional: Add any tags to the stack you'd like.
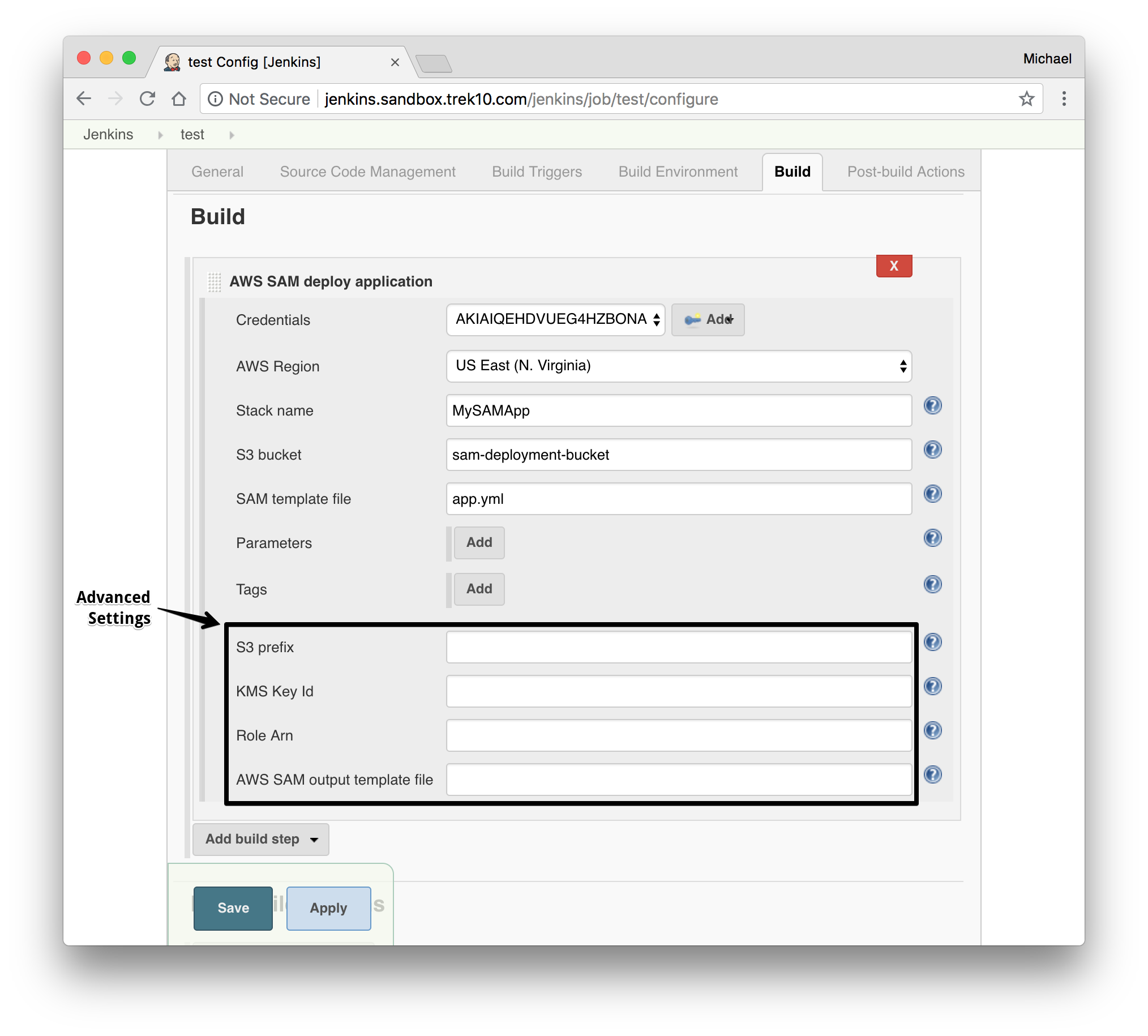
- Optional: Finish the "Advanced" configuration
- Give an S3 prefix to package the artifacts in the bucket under.
- Give a KMS Key ID to encrypt the packaged artifacts.
- Give a Role Arn that will be assumed by CloudFormation when executing the changeset.
- Select an output template file for the package step to output to.