A Firefox extension that automatically completes (fudges) Duo two-factor authentication. Only for MyUCLA login.
Forked from Easy Duo Authentication, which sadly only works with Chrome. Special thanks to Enoch Xu for making the Duo login automatic and for introducing me to the extension.
Duo 2FA uses a one-time password algorithm called HOTP (HMAC-based One-time Password) to generate passcodes. For HOTP, the authenticator and the authenticated share a secret key K (an arbitrary byte string) and a counter C. Each one-time passcode is calculated as such:
HOTP(K, C) = truncate(HMACH(K, C))
C += 1
Once the authenticated inputs a passcode, the authenticator will verify the passcode by calculating HOTP(K, C) for C in a reasonable interval [C, C+n]. If a match is found, then the authentication succeeds. Therefore, if we manage to get the secret key from Duo, we can calculate the exact same passcodes as Duo would.
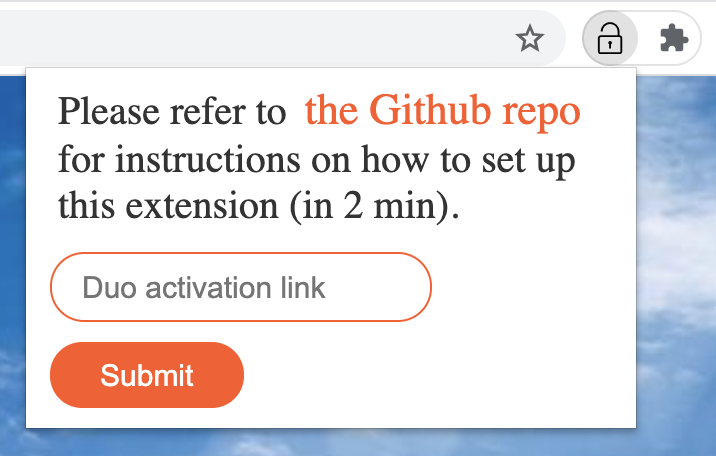
- Click here to install Duo Fudge. Only for Firefox.
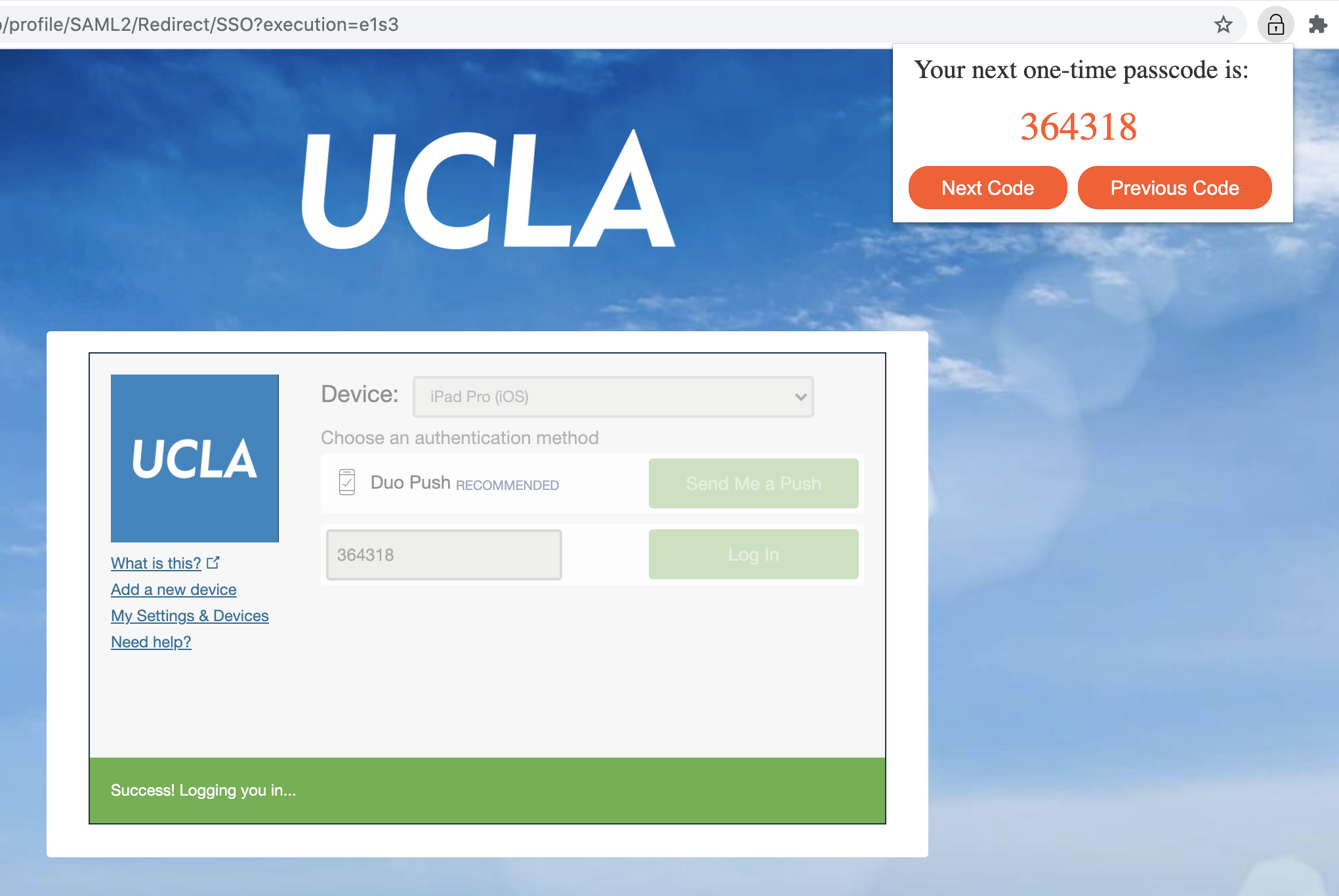
If you open the extension, it should look like this (pretend it's Firefox).
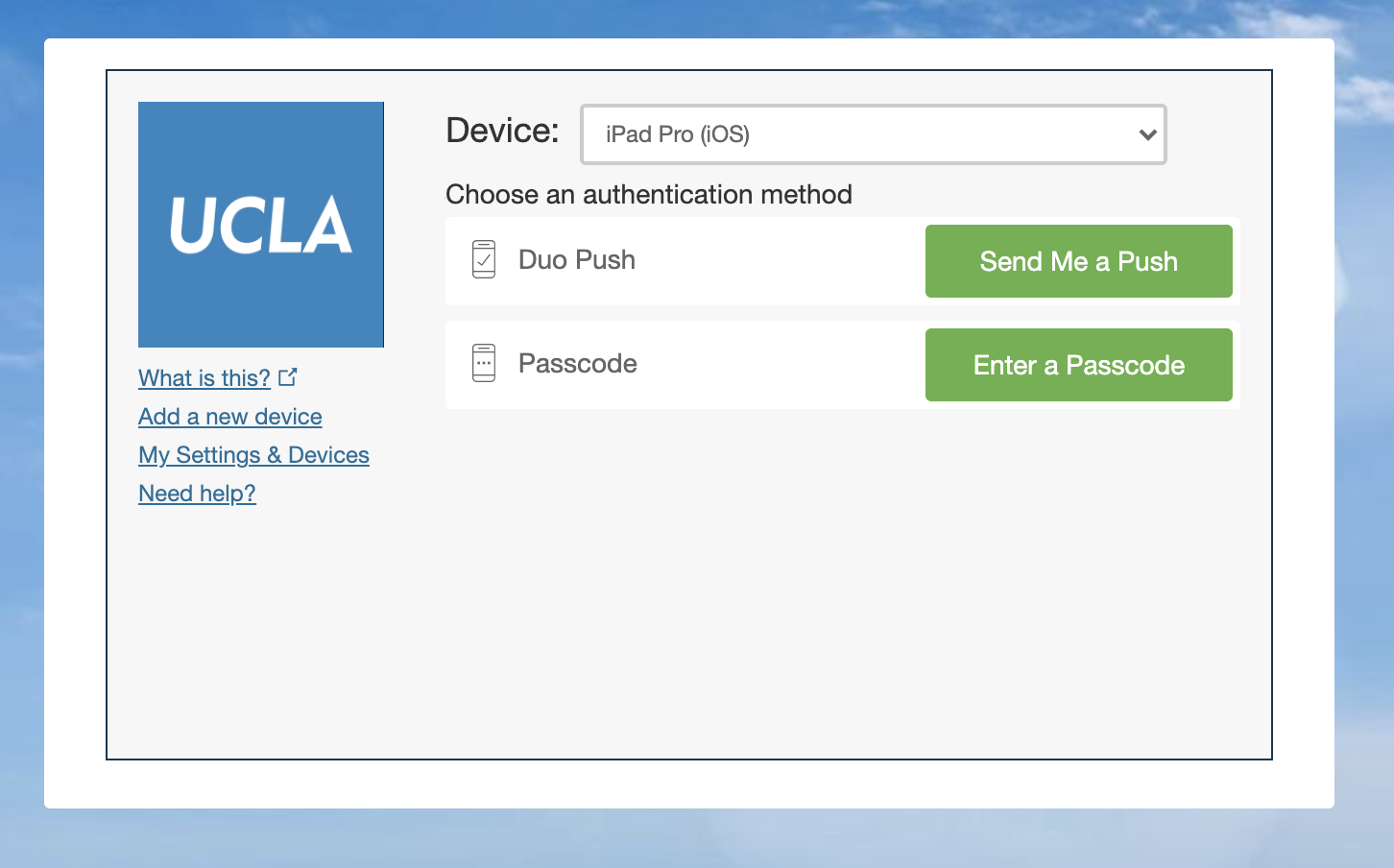
- Log in to a Duo authentication page, click
Add a new device.
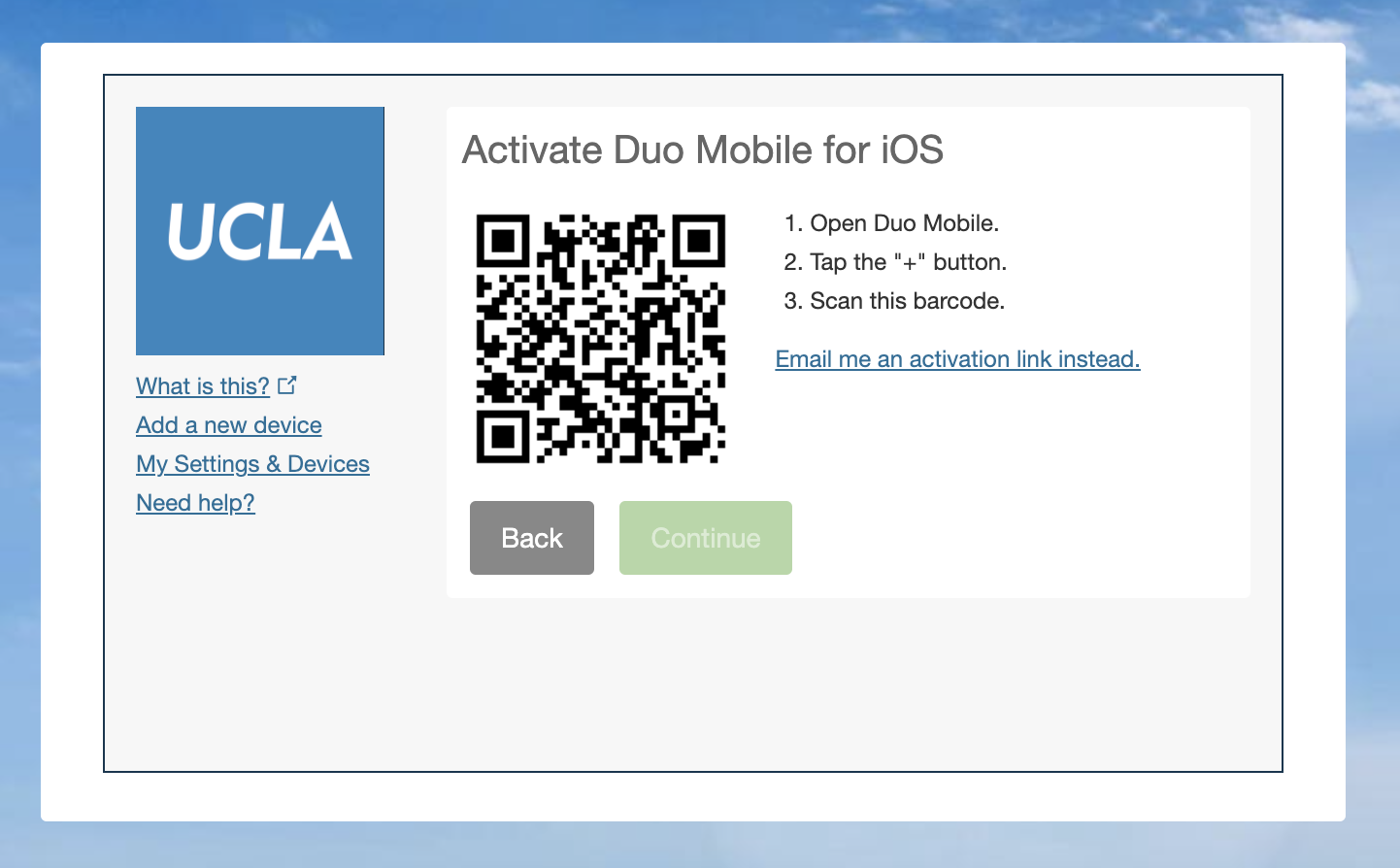
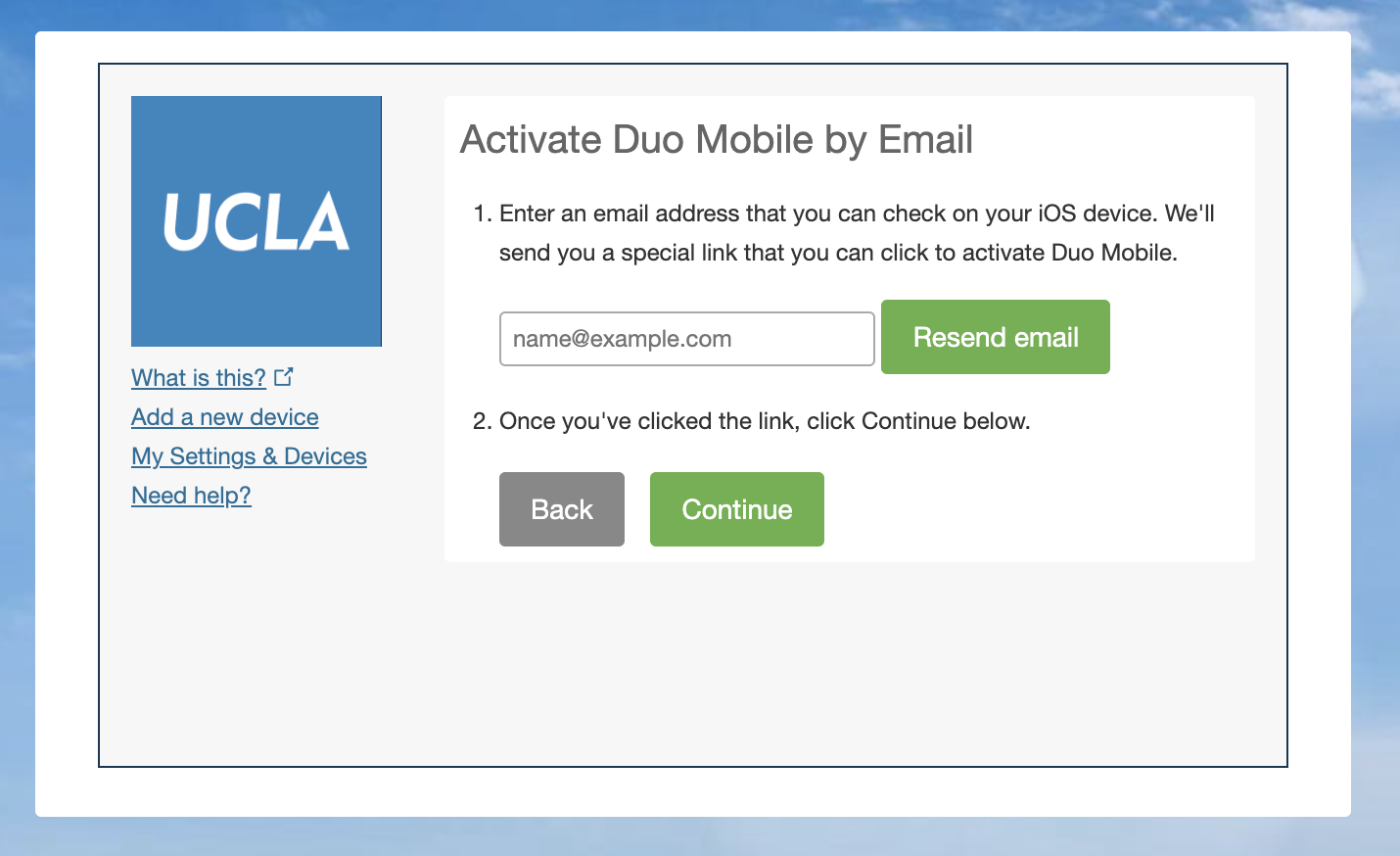
Choose Tablet, choose either iOS or Android, and click Continue. Then, click I have Duo Mobile installed, and click Email me an activation link instead. Enter your email and get a one-time activation link (in the form https://m-x.duosecurity.com/x).
- In Firefox, open the extension and sumbit the one-time activation link. Wait until a "set up successful" message appears.
- (Optional) Back to the
Activate Duo Mobile by Emailpage, clickContinue, and change the device name (e.g. toDuo Fudge).
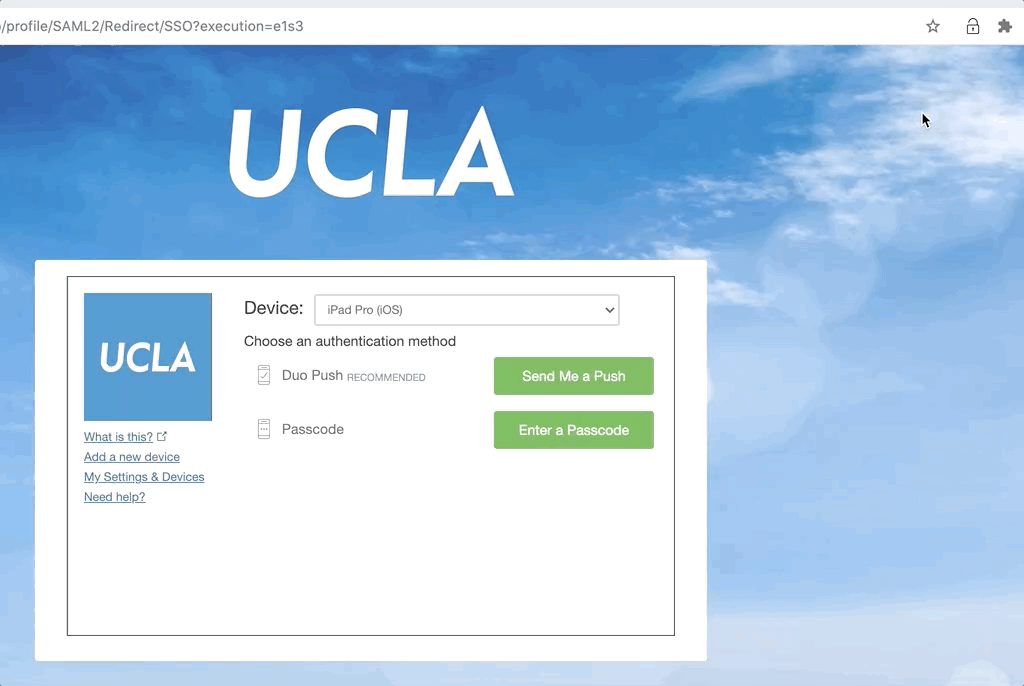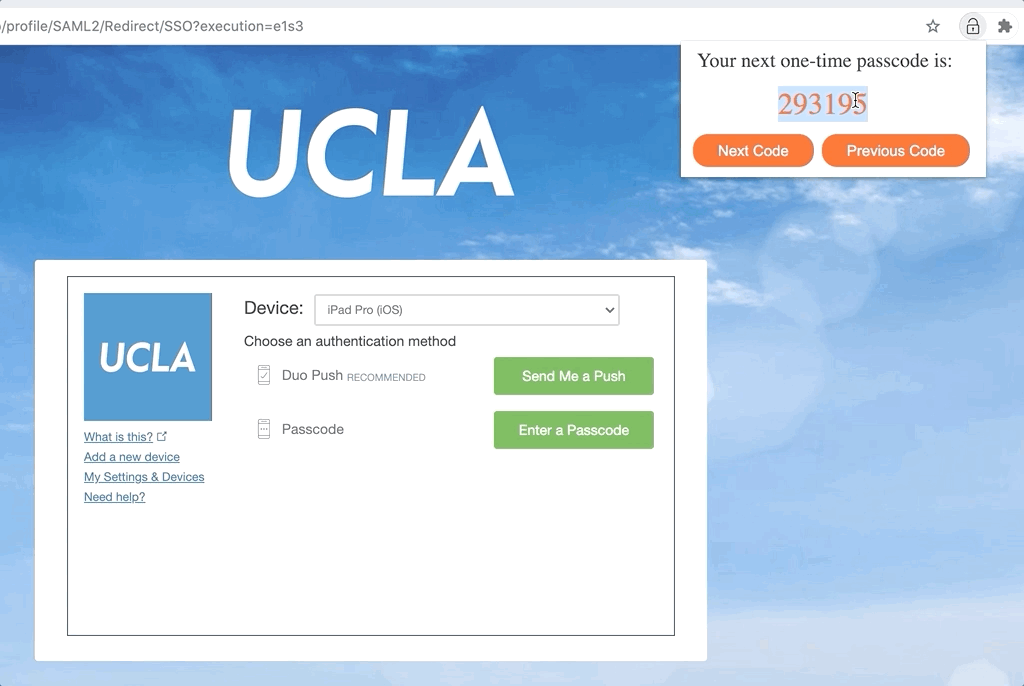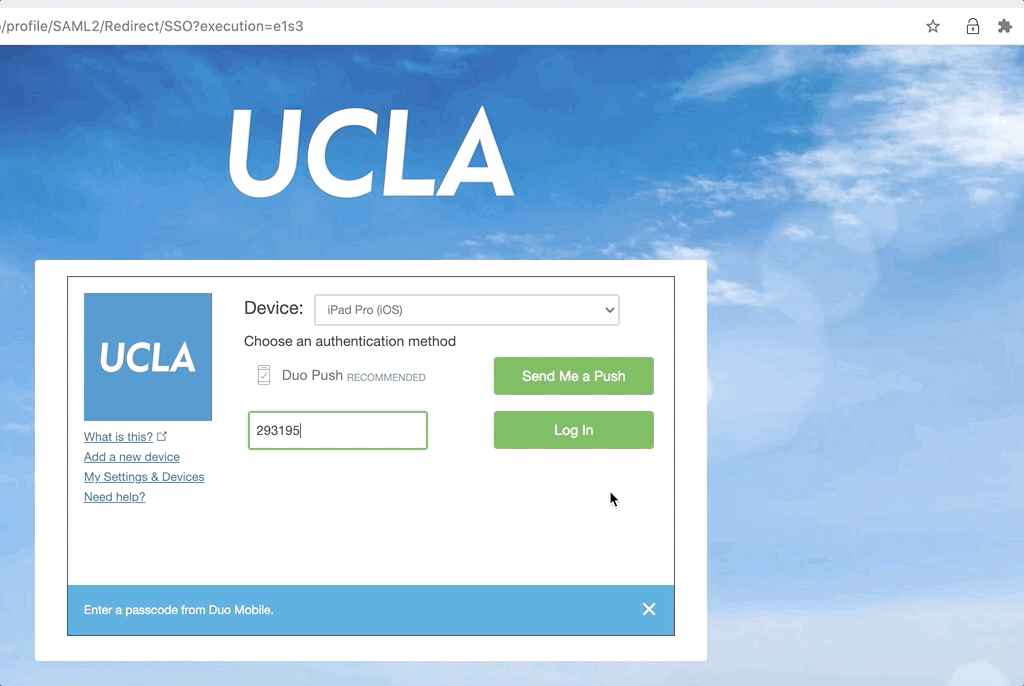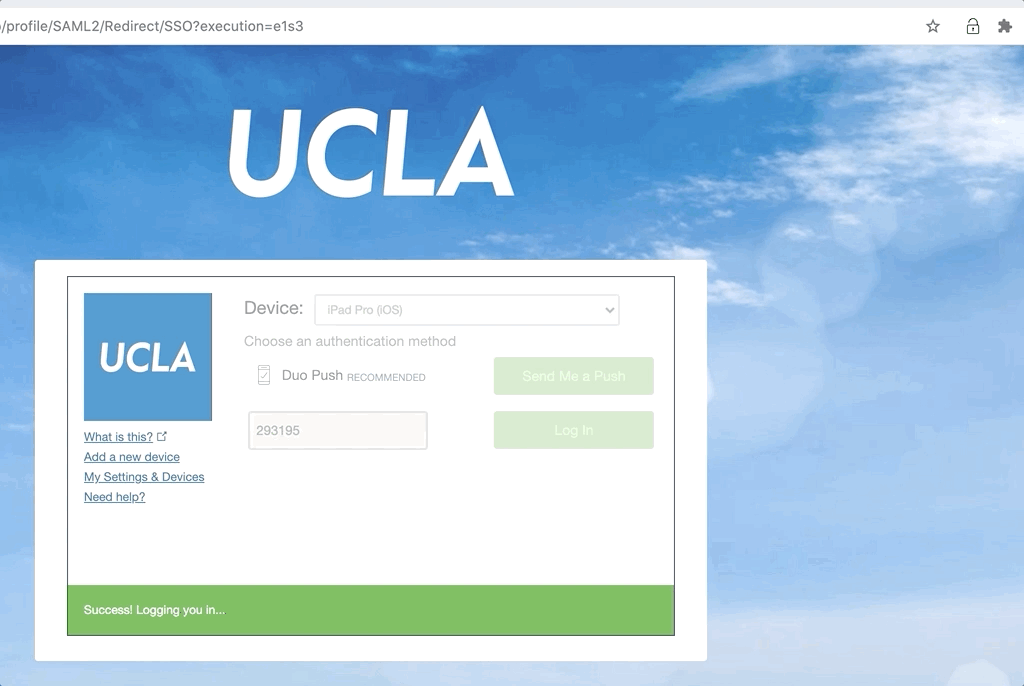
- You're all set! Now every time authenticating with Duo, open the extension to get your passcode. Regardless of the current device (it doesn't need to be the one you just added), paste the passcode and log in.
- Incorporated ideas/codes from https://github.com/revalo/duo-bypass and https://github.com/jiangts/JS-OTP.
- Used CORS Anywhere (https://github.com/Rob--W/cors-anywhere), a reverse proxy that deals with the Cross-Origin Resource Sharing mechanism.
- Don’t open the extension or click the “Next Code” button for too many times without logging in (i.e., don’t go too ahead of the Duo server), otherwise Duo may not recognize the new passcodes anymore. In this case, click the “Previous Code” button to go back and find the right passcode.
- If you catch any problems or have any advice, please contact me at y.shen@ucla.edu or sparkshen0807@gmail.com. Thank you so much!