This is an opinionated terraform module for provisioning a VPC on AWS for my use case. Before you try it out yourself, please remember it...
- has been designed for my usage
- might not work for other people
- please raise pull requests or issues around the module, but I cannot guarantee when or if I will be able to incorporate them
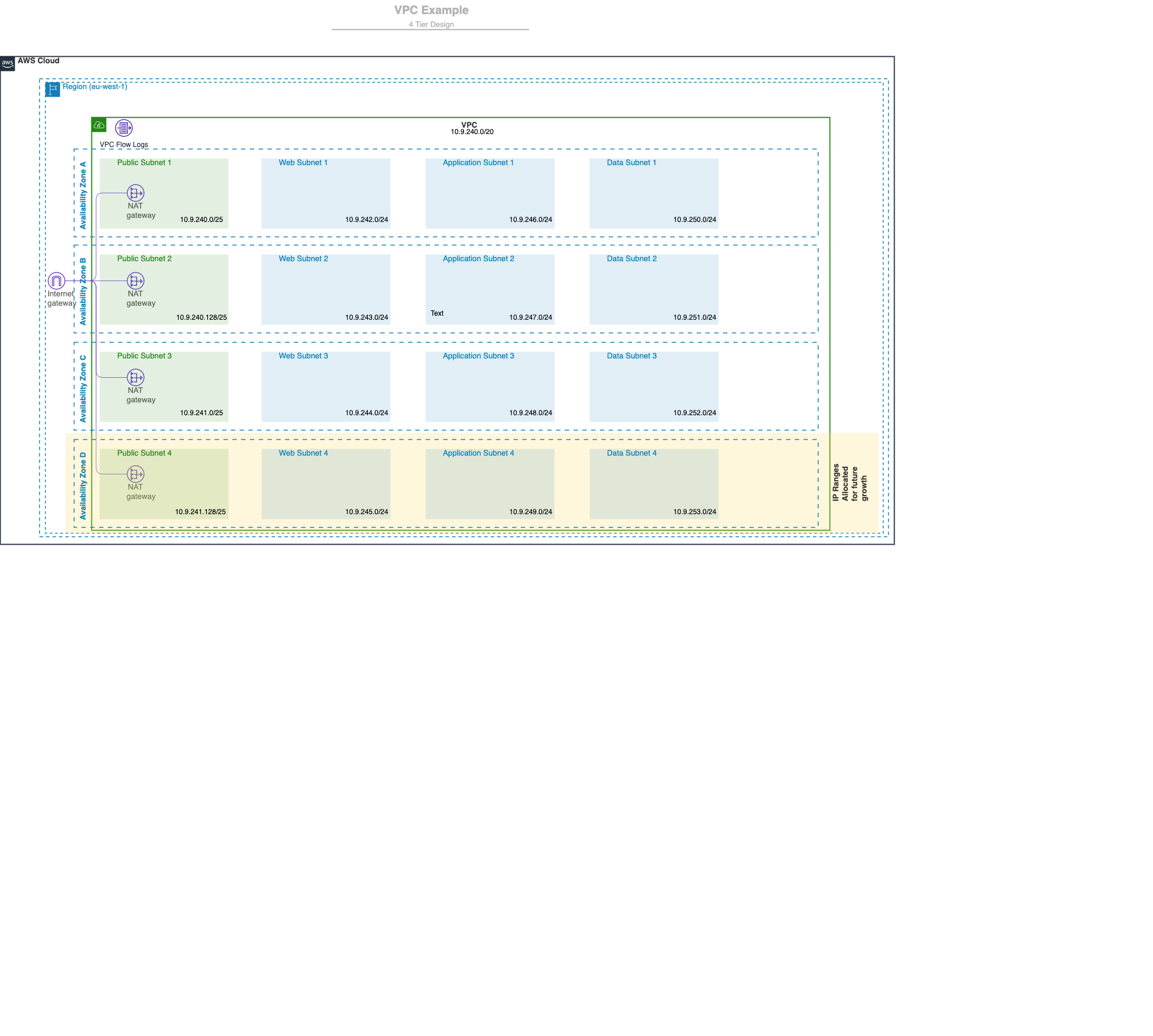
Here is a visual presentation of what it looks like
Applications used within this repo to help with CHANGELOG creation and also checking files within the repo
This Module can deploy a 4-tier VPC layout, if you do not wish to have the 4th tier, do not add in the CIDR ranges to private_cidr_blocks03
- Public Subnet - DMZ
- Private Subnet 01 - Web Subnet
- Private Subnet 02 - Application Subnet
- Private Subnet 03 - Data Subnet
| Name | Version |
|---|---|
| terraform | >= 1.5 |
| aws | 5.56.1 |
| Name | Version |
|---|---|
| aws | 5.56.1 |
No modules.
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| availability_zones | AWS region to launch servers. | list(any) |
[ |
no |
| aws_region | AWS region to launch servers. | string |
"eu-west-1" |
no |
| dhcp_domain_name | Enter a domain name (such as example.com). | string |
"" |
no |
| dhcp_domain_name_servers | Enter up to 4 DNS server IP addresses or AmazonProvidedDNS for AWS Defaults | list(any) |
[ |
no |
| dhcp_netbios_name_servers | Enter up to four NetBIOS name server IP addresses | list(any) |
[] |
no |
| dhcp_netbios_node_type | Enter the NetBIOS node type, for example, 2 | string |
"" |
no |
| dhcp_ntp_servers | Enter up to four Network Time Protocol (NTP) server IP addresses | list(any) |
[] |
no |
| enable_vpc_s3_endpoint | Create VPC S3 Endpoint | bool |
false |
no |
| environment_tag | Define the type of environment | string |
"" |
no |
| k8s_clustername | EKS/k8s Cluster Name | string |
null |
no |
| master_cidr_block | VPC CIDR Block | string |
"" |
no |
| nat_gateway | Create NAT Gateway | bool |
false |
no |
| one_nat_gateway_per_az | Should be true if you want one NAT Gateway per availability zone. | bool |
true |
no |
| private01_tier_name | Tag value for tier subnet | string |
"web" |
no |
| private02_tier_name | Tag value for tier subnet | string |
"app" |
no |
| private03_tier_name | Tag value for tier subnet | string |
"data" |
no |
| private_cidr_blocks01 | CIDR Blocks for Private Subnets | list(any) |
[] |
no |
| private_cidr_blocks02 | CIDR Blocks for Private Subnets | list(any) |
[] |
no |
| private_cidr_blocks03 | CIDR Blocks for Private Subnets | list(any) |
[] |
no |
| private_routing_tables_tags | A map of tags to assign to private routing tables. | map(string) |
{} |
no |
| private_subnet_tags | A map of tags to assign to private subnets. | map(string) |
{} |
no |
| project_tag | Project code name or name | string |
"" |
no |
| public_cidr_blocks | CIDR Blocks for Public Subnets | list(any) |
[] |
no |
| public_routing_tables_tags | A map of tags to assign to public routing tables. | map(string) |
{} |
no |
| public_subnet_tags | A map of tags to assign to public subnets. | map(string) |
{} |
no |
| public_tier_name | Tag value for tier subnet | string |
"dmz" |
no |
| single_nat_gateway | Should be true if you want to provision for your entire VPC | bool |
false |
no |
| tags | A map of tags to add to all resources. | map(string) |
{} |
no |
| vpc_enable_dns_hostnames | Enable VPC DNS hostnames | bool |
true |
no |
| vpc_enable_dns_support | Enable VPC DNS Support | bool |
true |
no |
| vpc_tags | A map of tags to add to VPC resource. | map(string) |
{} |
no |
| vpcflow_log_accepted_retention | How many day's worth of VPC Flow logs to keep for accepted connections | string |
"14" |
no |
| vpcflow_log_rejected_retention | How many day's worth of VPC Flow logs to keep for rejected connections | string |
"14" |
no |
| Name | Description |
|---|---|
| all_subnet_ids | List all used subnet ids |
| aws_region | AWS Region being used |
| nat_gw_eips | List all NAT Gateway Public IPs |
| private01_routing_table_ids | Routing table ids for private 01 subnets |
| private01_tier_name | Tag being used for describing private subnet 01 tier |
| private02_routing_table_ids | Routing table ids for private 02 subnets |
| private02_tier_name | Tag being used for describing private subnet 02 tier |
| private03_routing_table_ids | Routing table ids for private 03 subnets |
| private03_tier_name | Tag being used for describing private subnet 03 tier |
| private_subnet01_ids | List all used private 01 subnet ids |
| private_subnet02_ids | List all used private 02 subnet ids |
| private_subnet03_ids | List all used private 03 subnet ids |
| private_subnet_ids | List all used private subnet ids |
| public_routing_table_ids | Routing table ids for public subnets |
| public_subnet_ids | List all used public subnet ids |
| public_tier_name | Tag being used for describing public subnet tier |
| vpc_cidr | CIDR Range being used by VPC |
| vpc_id | AWS VPC ID |