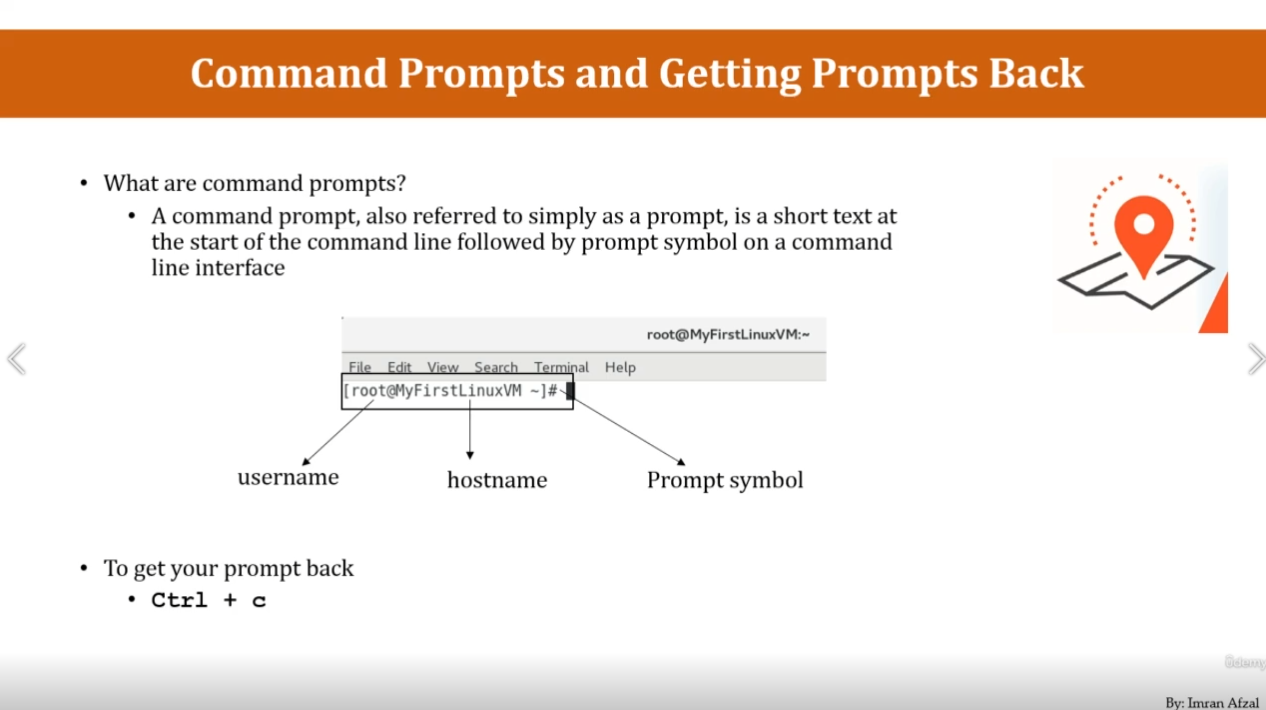
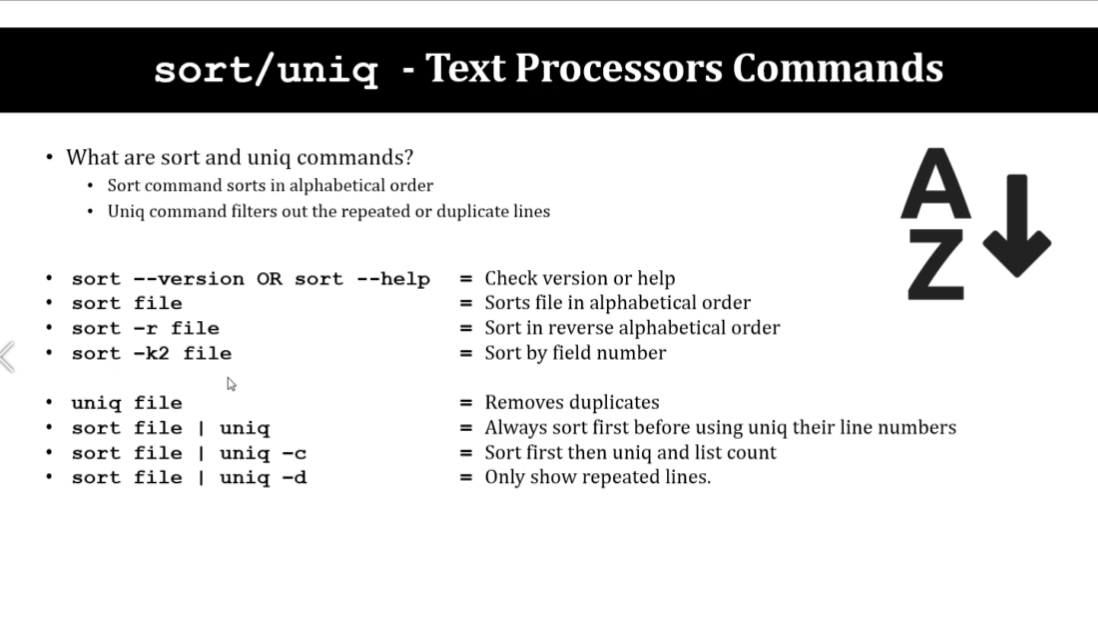
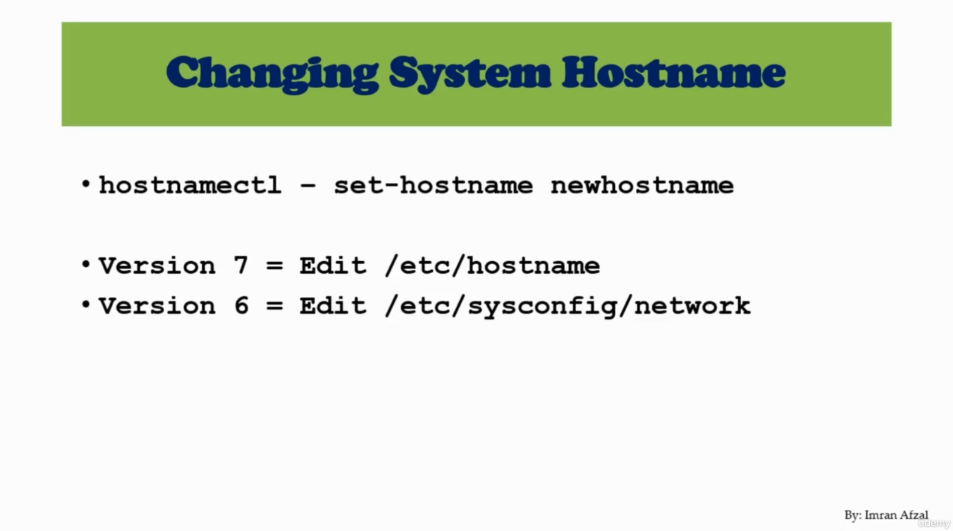
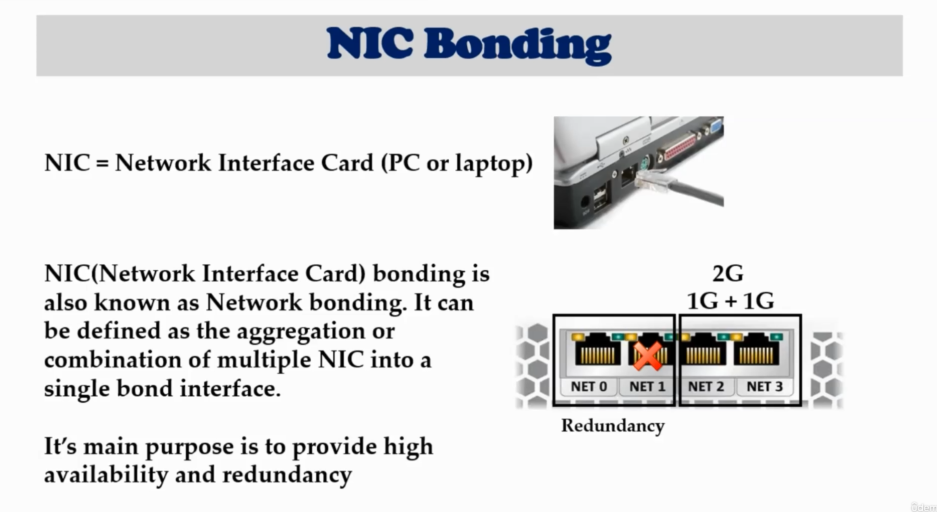
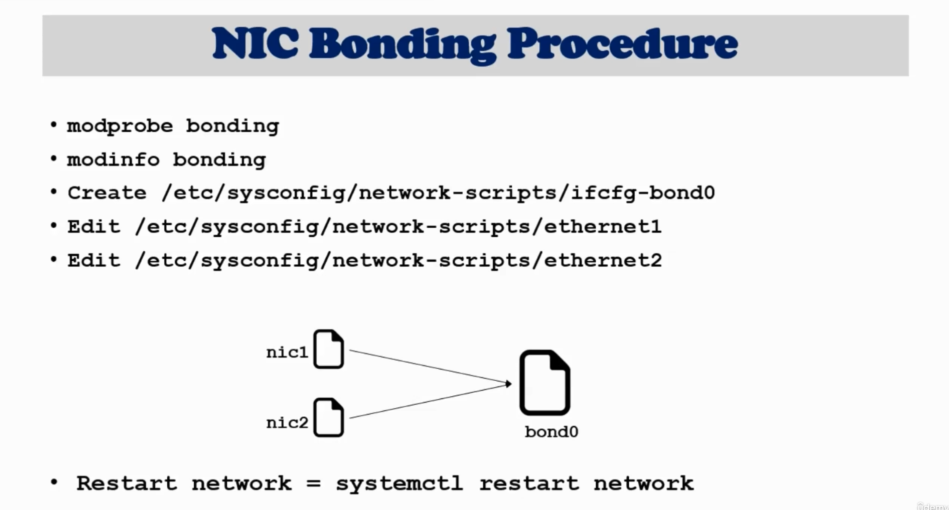
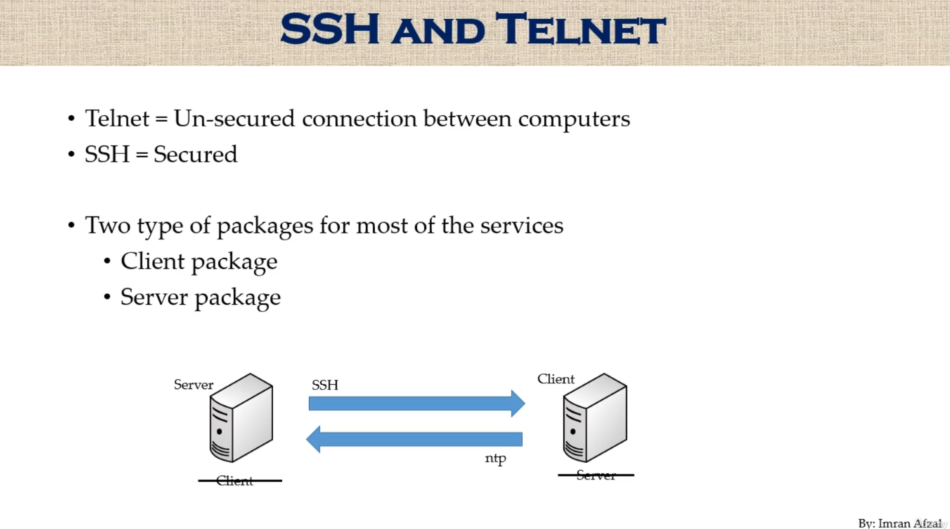
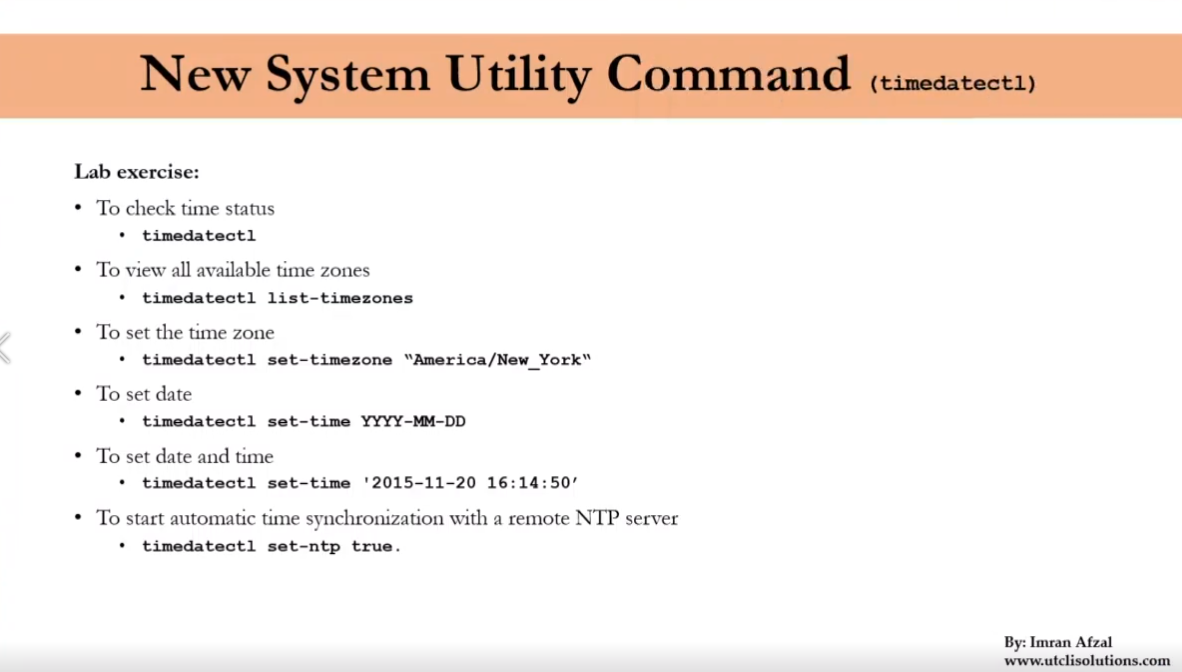
ip a
ip addr
ifup <internet driver name> reboot
cp -R <source_folder> <destination_folder>
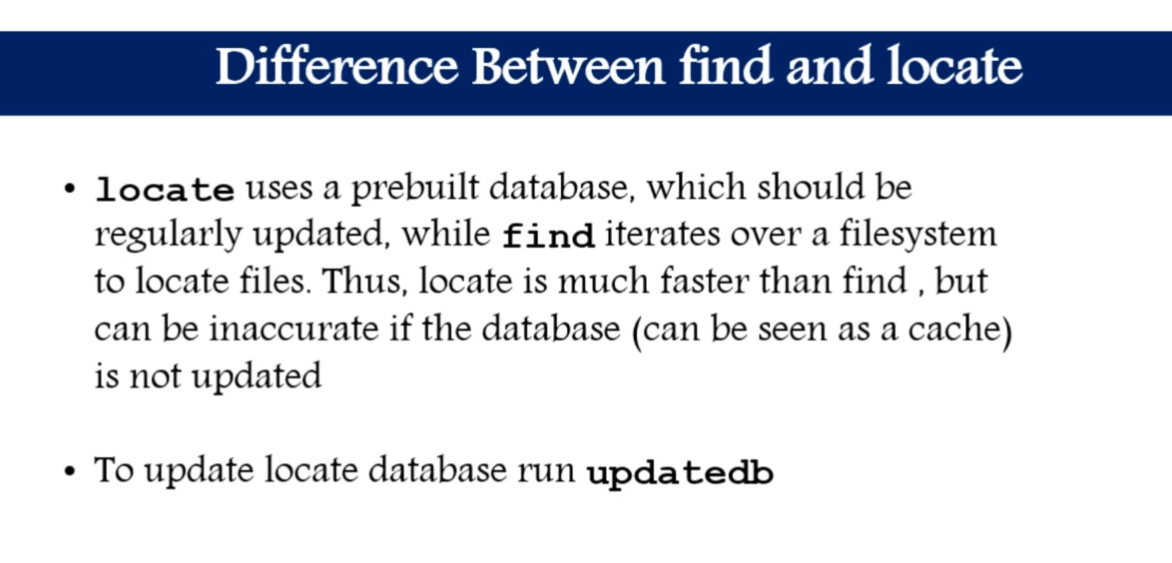
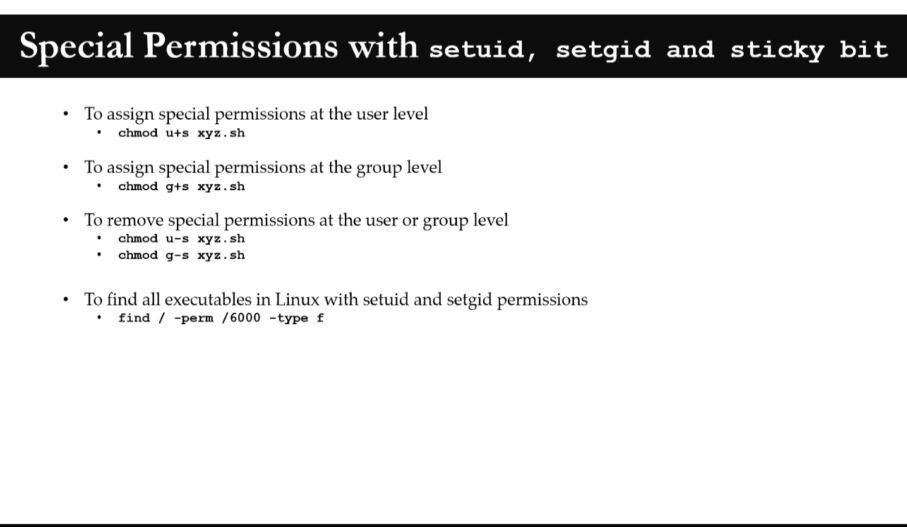
two main commands are used to find files/directories
-
find -
find . -name "pedram.txt" -
locate -
locate "pedram.txt"beforeyum install mlocateandupdatedb
passwd <userId>
-
touch abcd{1..9}.txtcreate 9 files -
rm abcd* -
ls -l abcd* -
rm *.xyz -
ls -l ?bcd* -
ls -l *[cd]*
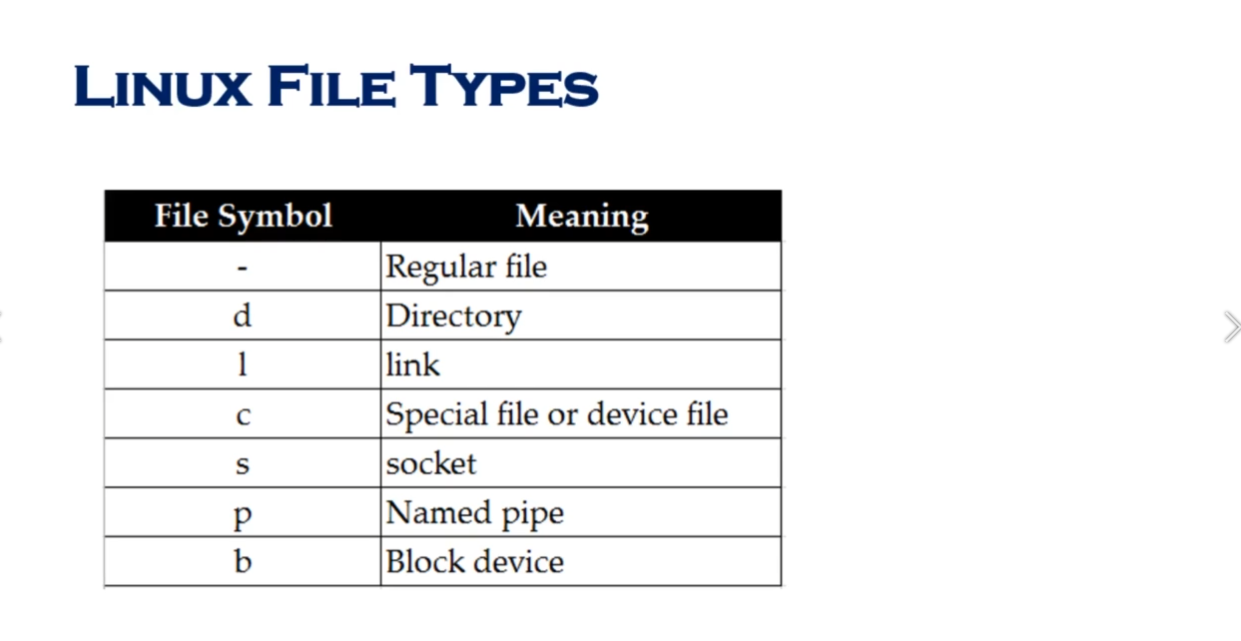
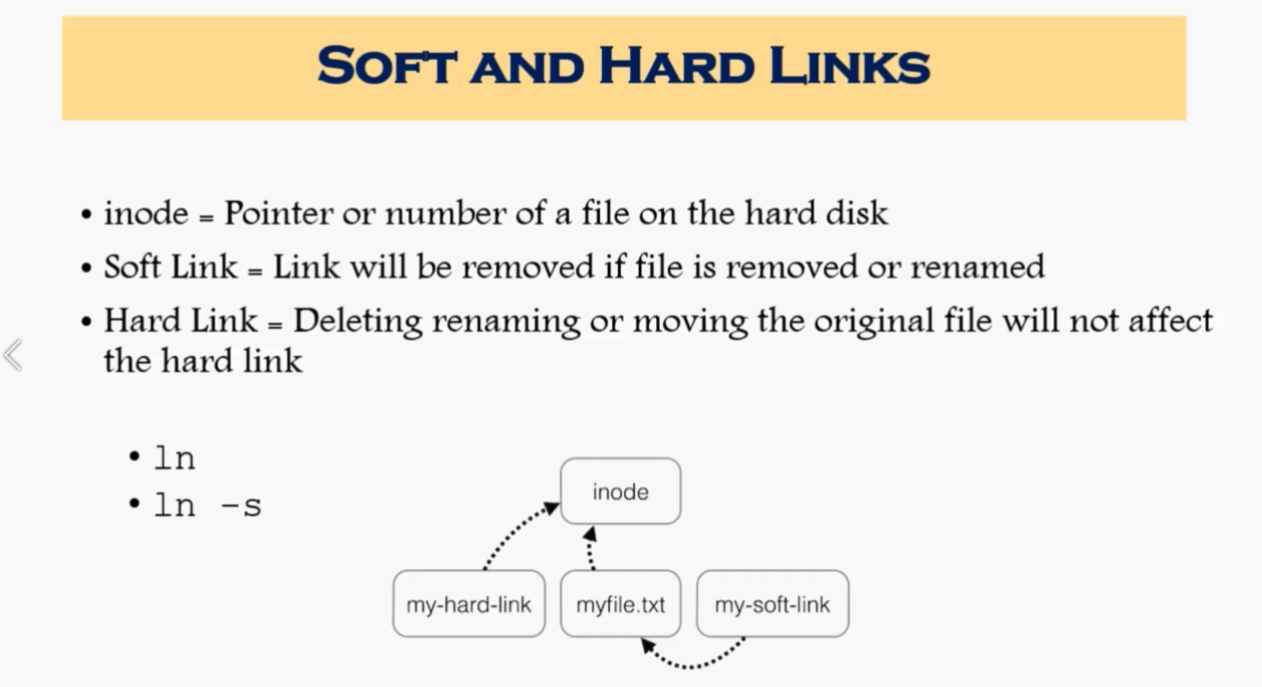
Link is just a shortcut
yu cannot create soft or hard link within the same directory with the same name.
hard links only work within the same partition
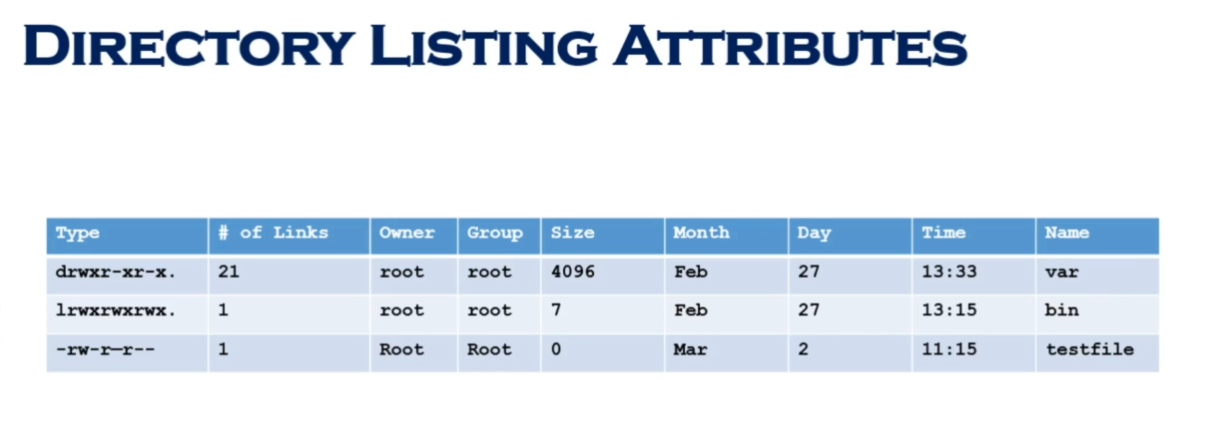
ls -ltrhi i = inode
-
ls -l-l is options -
ls -l DownloadsDownloads is argument
-
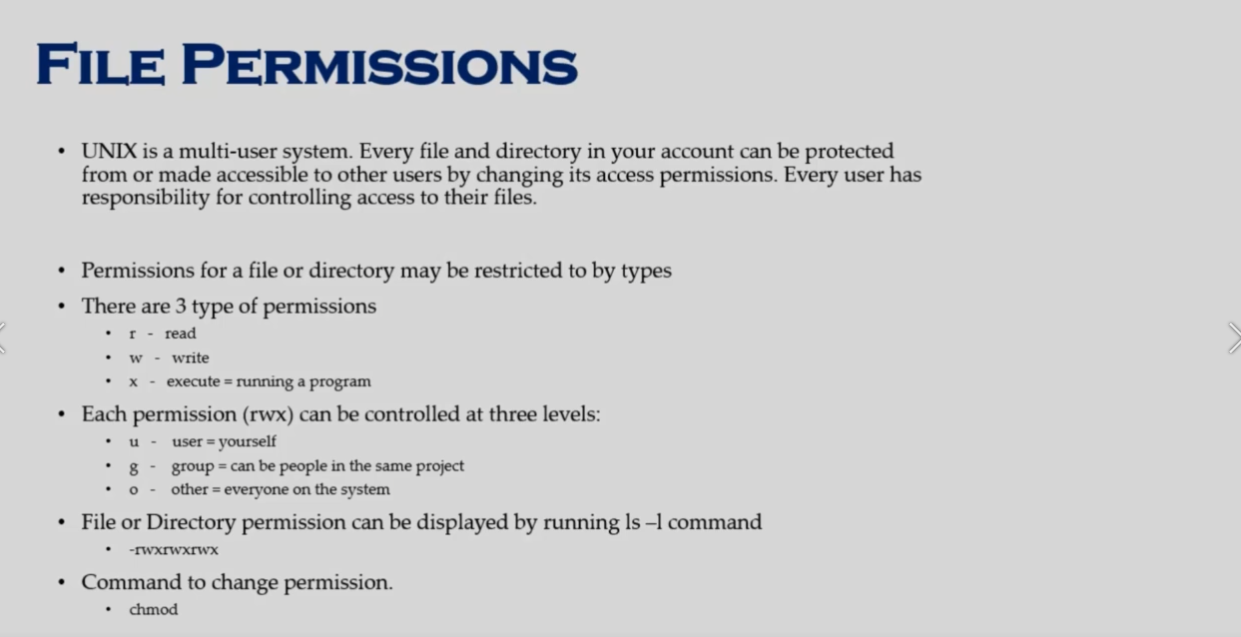
user
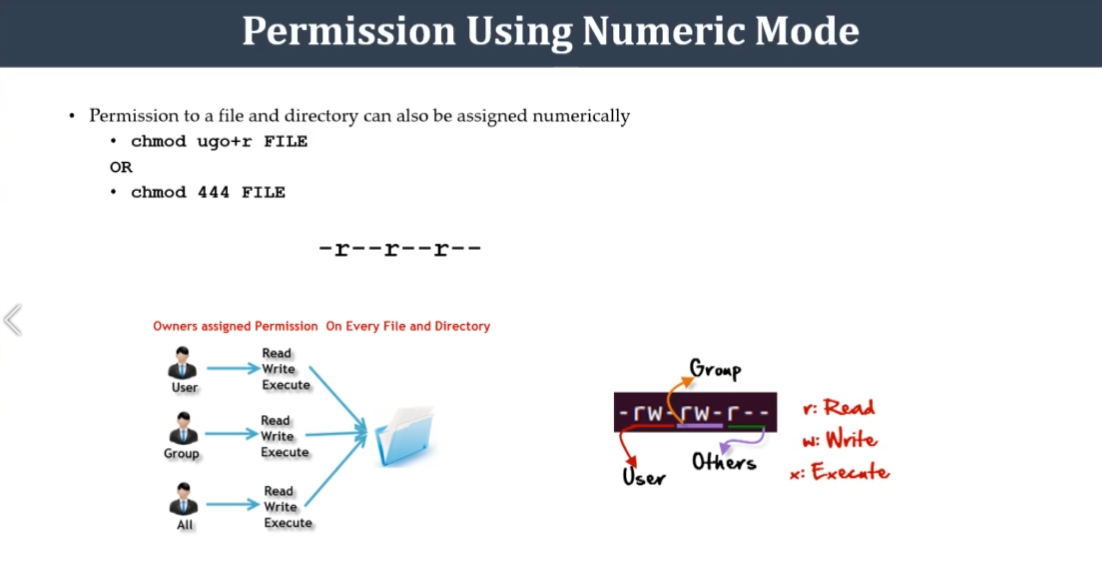
chmod u+rwx <fileName> -
group
chmod g+rwx <fileName> -
others
chmod o-rwx <fileName> -
everyone
chmod a-rwx <fileName>
if a directory does not have execute permission (x) you can not cd to the directory
-
chown <username> <fileName> -
chgrp <username> <fileName>
-
whatis command -
command --help -
man command
-
echo "some text" [>> , >] file.txt -
ls -ltrh > file.txt
-
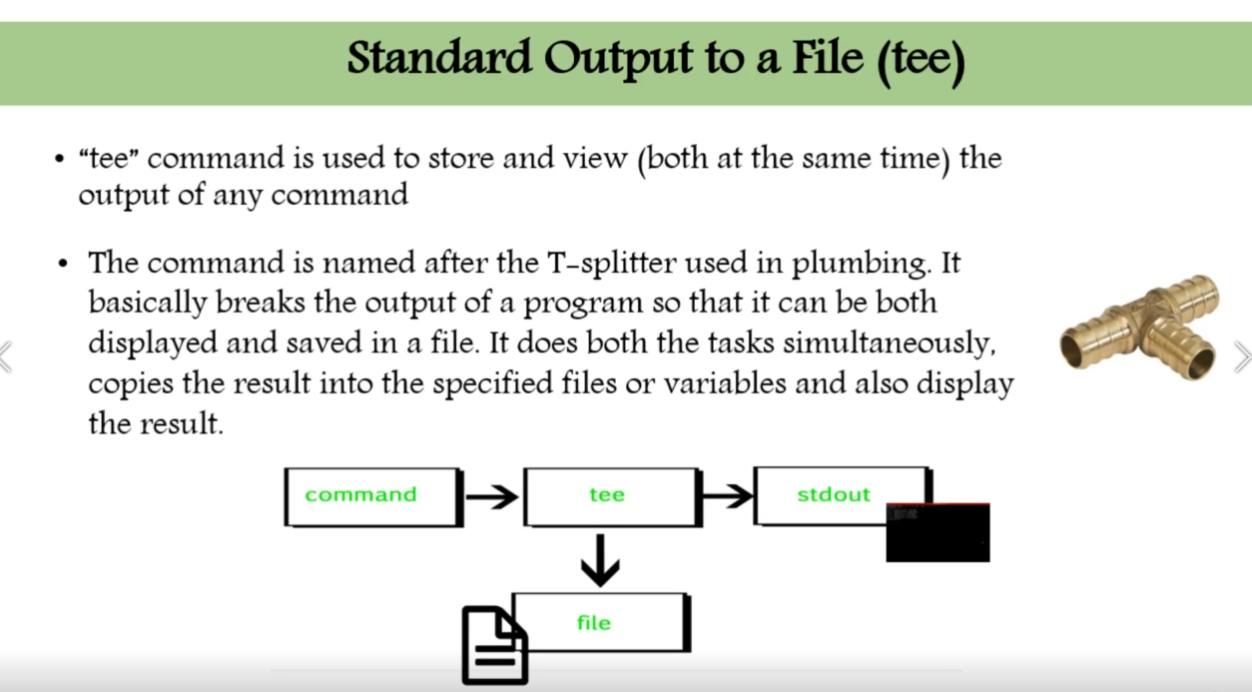
echo "pedram aghasian is the best" | tee file.txt -
echo "also is network specialist" | tee -a file.txt -
echo "also is network specialist" | tee file1 file2 file3
-
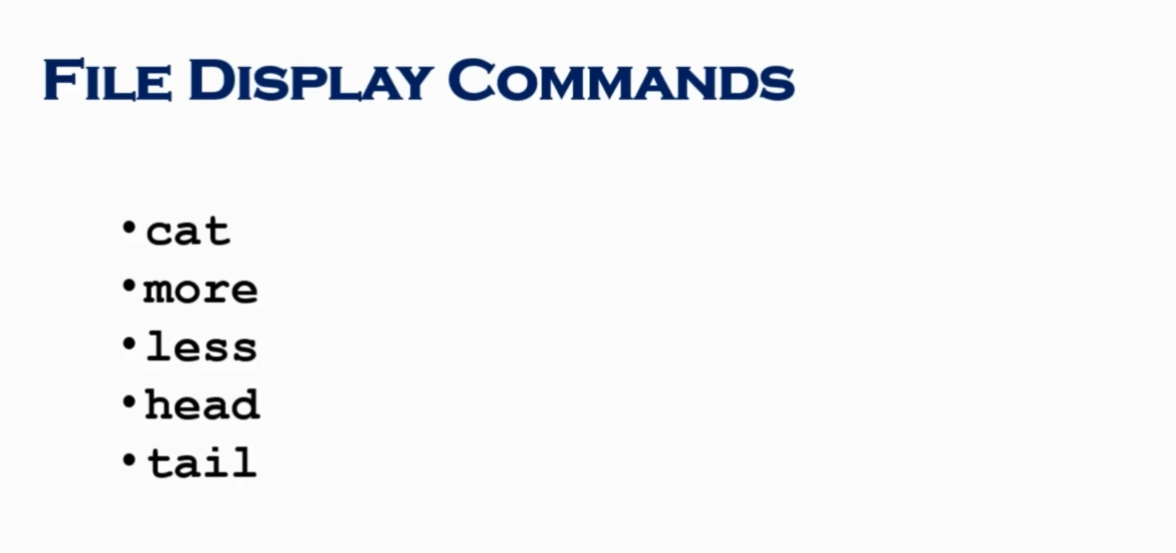
ls -ltrh | more -
ls -ltrh | tail -1
cp file.txt newFile.txtcreate newFile.txt and copy file.txt ino it.cp file.txt /tmpmv file.txt newName.txtrename a file.mv file.txt /tmpcut file.chgrp root file.txtchgown root file.txtchown root:root file.txt
tar : tar takes a bunch of files together and put it in one container, just like in windows you have bunch of files and zip them together, so tar file does not compress as much as the actual gzip command.
tar cvf <fileName>.tar <path>- extract tar file :
tar xvf file.tar
gzip : is actually compress files
- compress tar file :
gzip file.tar - upCompress file :
gunzip file.tar.gzorgzip -d file.tar.gz
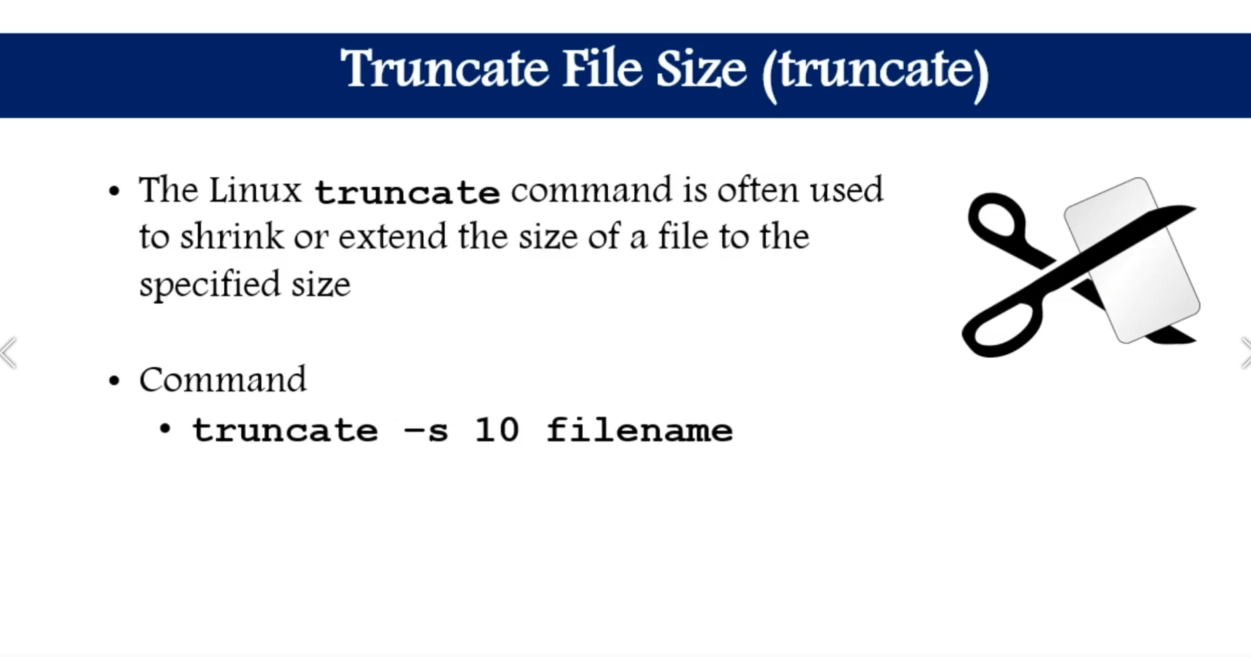
shrink or extend a file : truncate -s <size bit> filename
vi Editor
Exit from Vi shift + z + z
Undo u
-
replace a word and just show the result
sed 's/oedram/pedram/g' <fileName> -
replace a word and write to that file
sed -i 's/oedram/pedram/g' <fileName> -
delete a word
sed 's/pedram//g' <fileName> -
delete all the line which have specific word
sed '/pedram/d' <fileName> -
remove empty lines from a file
sed '/^$/d' <fileName> -
remove first line of the file
sed '1d' <fileName> -
remove first two line of the file
sed '1,2d' <fileName> -
replace tabs with space
sed 's/\t/ /g' <fileName> -
just show line 12 be bad
sed -n 12,18p <fileName> -
make empty line after every line
sed G <fileName> -
replace every word except word in line number 8
sed '8!s/oedram/pedram/g' <fileName> -
in vim editor
:%s/oedram/pedram/g
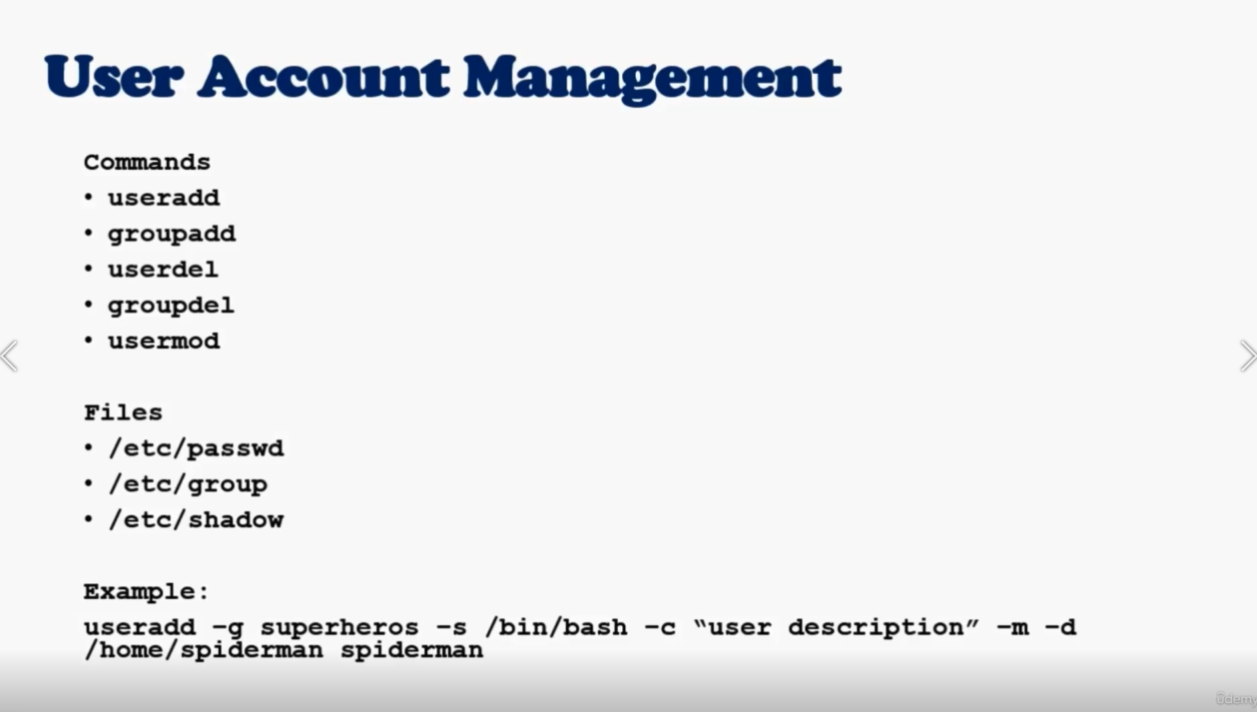
create user
- create user
useradd spiderman - get use id
id spiderman - assign a password
passwd 123456
modify user
- modify a user account
usermod -G <groupName> <userName>
delete user
- delete a use with homeDir
userdel -r spiderman - show all groups
cat /etc/groupsorgrep spederman /etc/group
create group
- create a group
groupadd superheros - show all groups
cat /etc/groups
delete group
- delete a group
groupdel superheros
cat /etc/passwd
username: password : userId : groupId : description : homeDir : shell
cat /etc/group
groupName: groupPassword: groupId : users are part of this group
cat /etc/shadow
show information about users passwords
grant root access to the user
/etc/sudoers: and add the user
root ALL=(ALL) ALL
pedram ALL=(ALL) ALL
- or add the user to the sudoers group
usermod -aG wheel pedram
- then with your username you can run sudoers command :
sudo pedram
who: information about how many people are logged in; when there is height load an the system and you want to see who are logged to the system.last: tell you all the details are the users that logged in.
last | awk '{print $1}' | sort | uniq
w: give you little more information.fingeridorid username: get information about yourself.
wall+ message + (ctrl + d) : broadcast a message to all users who loggedIn.write username: send message directly to the user.
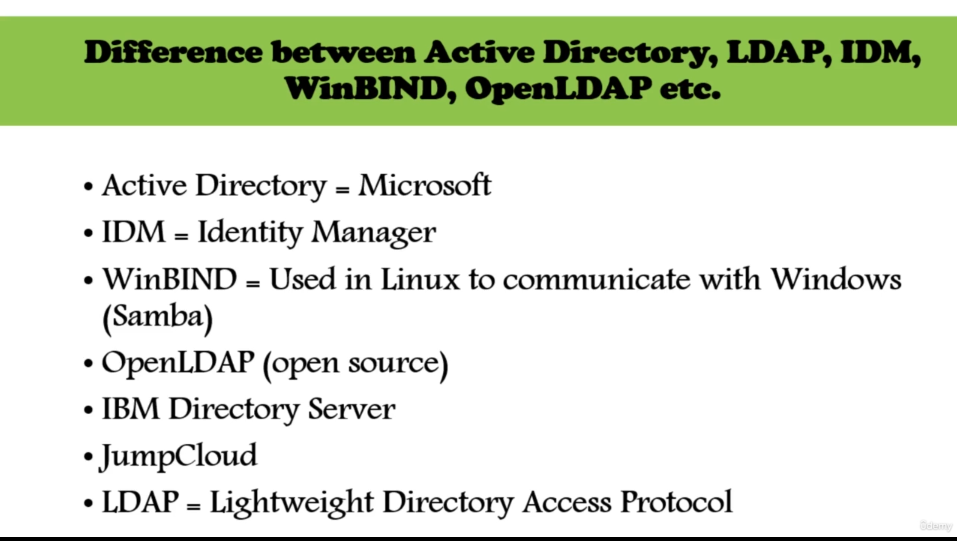
LDAP is a Protocol NOT Directory service
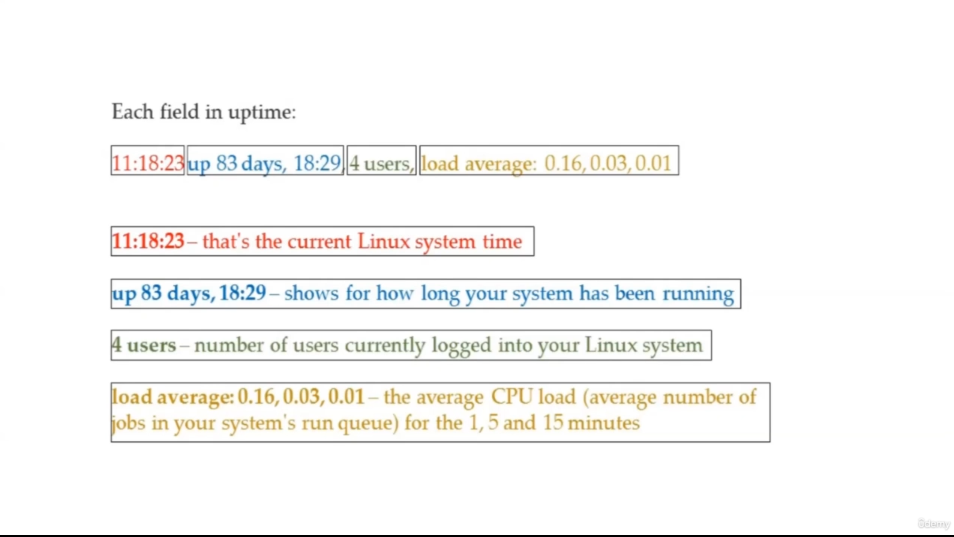
uptime
which
which <command> tell you about command
bc
bc command line calculator
Application or service
it's like a program that's run into your computer, for example NTP - NFS - rsyslog - Apache.
In Windows, daemons are called services, and behave exactly how daemons were previously described. They exist and operate independent of a user’s login session, and its status can be observed under the Services tab of Windows Task Manager.
Script
script is something that written in a file, and they can be execute.
Process
when you run an application it actually generate process with process id.
An instance of a particular executable that is being executed: For example this could be an .exe program file or a Linux binary. A given application may have several processes running simultaneously.
Typically, an executing program can exist in one of three states: Running: Active Sleeping: Inactive Zombie: A process that has completed execution, but still has an entry in the process table
Daemon
is constituently runs in the background.
A process which runs in the background and is not interactive. They have no controlling terminal on their own from the user’s perspective from the desktop. They continue to exist and operate regardless of any user being logged into the server if the computer is on.
Threads
every process could have multiple threads.
Job
a job is something that is created by scheduler like a workorder to run those application and services.
netstat -rnv
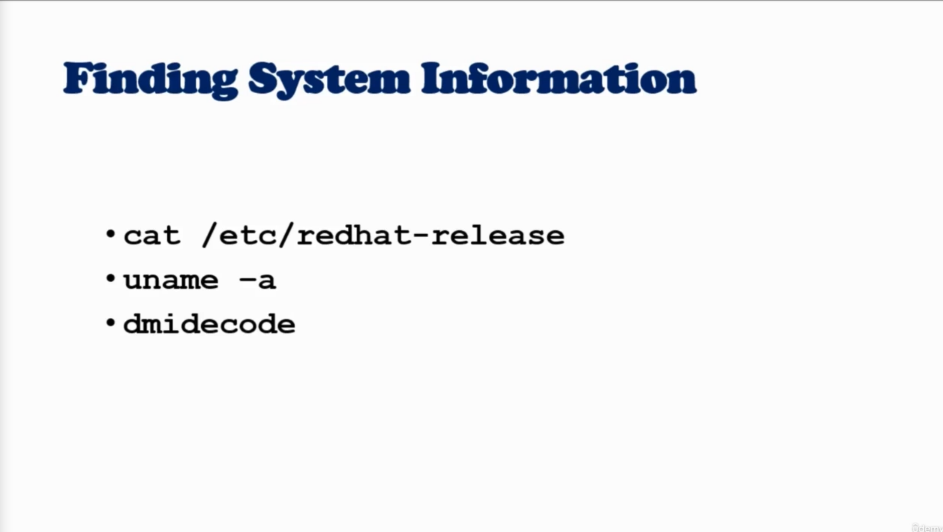
cat /etc/os-release
watch and save all terminal activity script activity.lgo
for exit of exit
which passwdls - l /usr/bin/passwd- with user pedram run
passwd - go to another terminal and
ps -ef | grep passwd - you see this command run by root
#!/bin/bash
# commands
pwd
echo
hostname
echo
ls -ltrh
# define variables
fullName = 'pedram aghasian'
echo my name is $fullName#!/bin/bash
a = `hostname`
echo Hell, my hostname is $a
echo
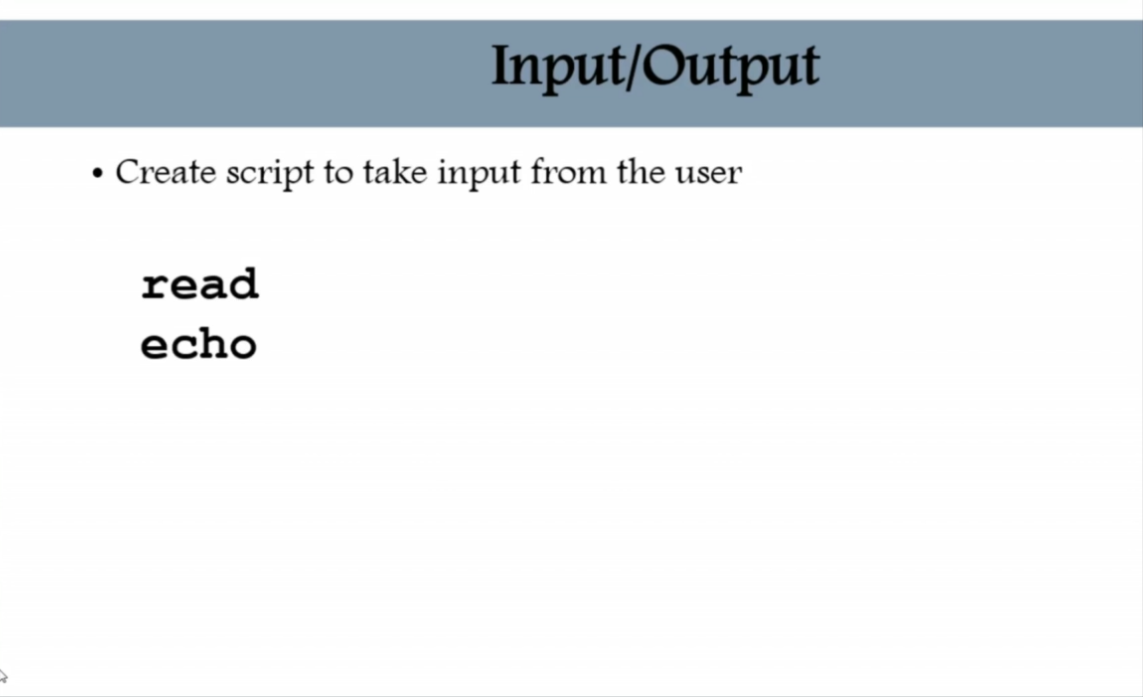
echo What is your name ?
read NAME
echo
echo Hello $NAME
echo#!/bin/bash
count = 100
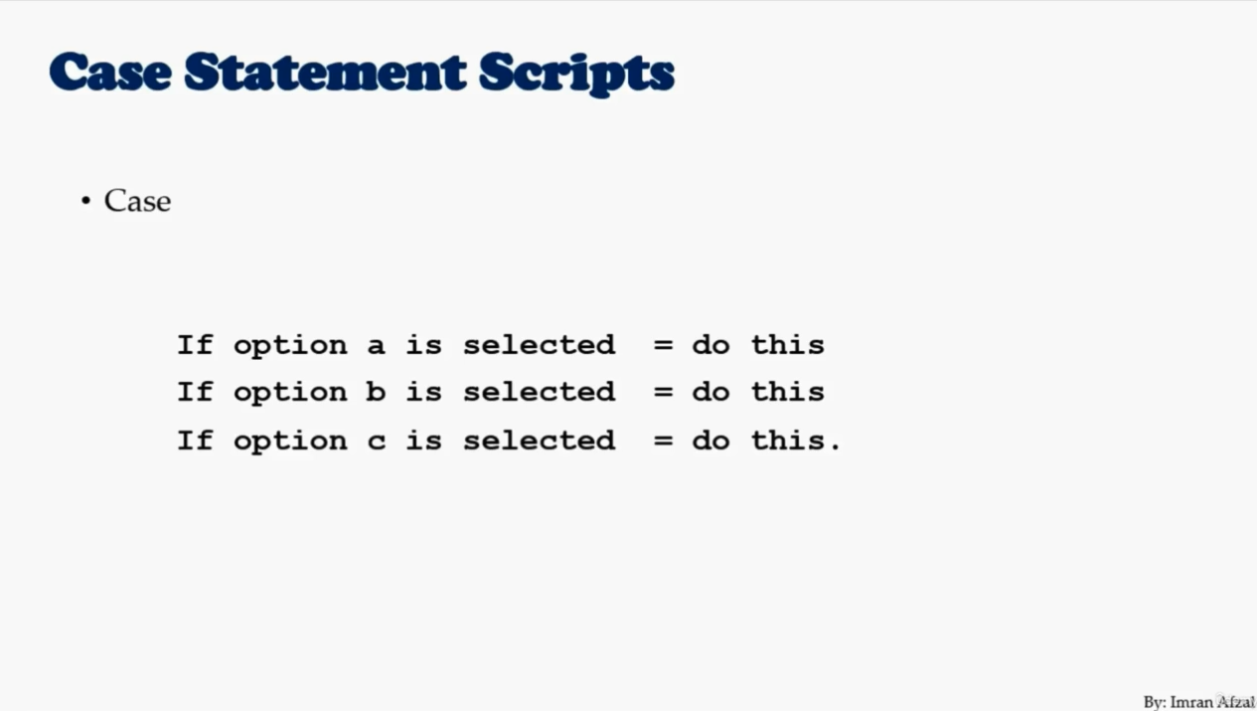
if [ $count -eq 100 ]
then
echo Count is 100
else
echo Count is not 100
fi#!/bin/bash
clear
if [ -e /home/pedram/secrete.txt ]
then
echo "file secrete.txt is exist"
else
echo "secrete.txt is not exits"
fi#!/bin/bash
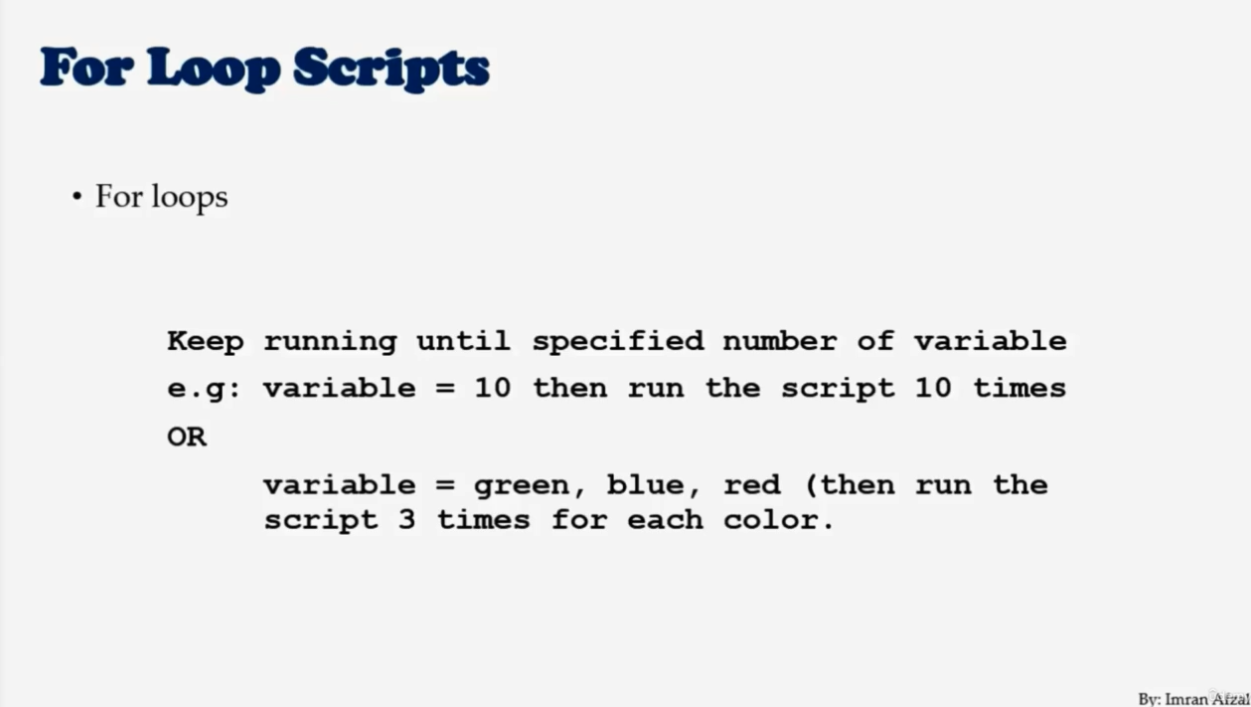
for i in 1 2 3 4 5
do
echo $i
done#!/bin/bash
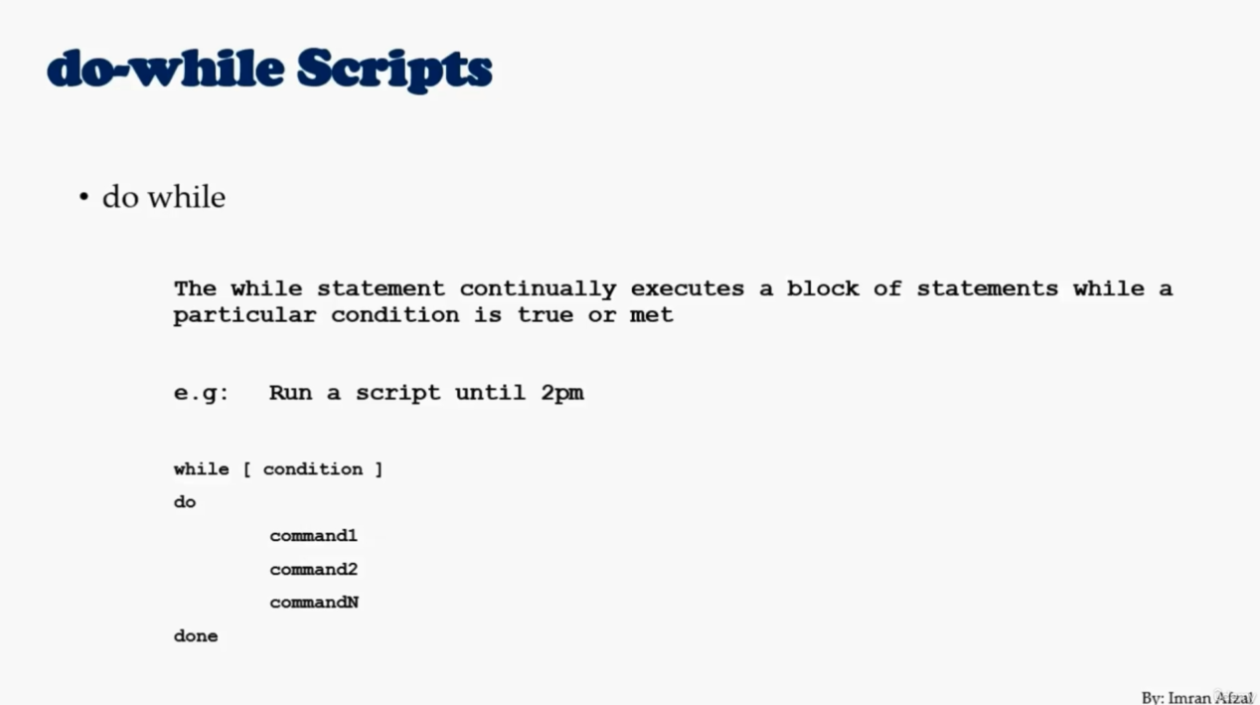
c = 1
while [ $c -le 5]
do
echo welcome $c
((c++))
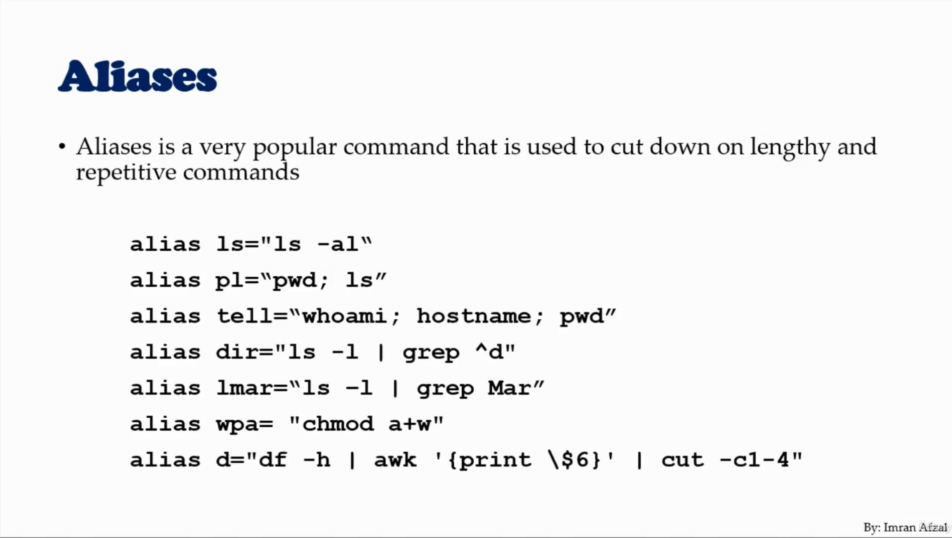
donealias show all aliases
unalias <aliasName> delete an alias
- show history
history - run commands witch in history
!<command number> !405 - history location
cat /home/pedram/.bash_history
netstat -rnv
tcpdump -i <interface>
what if server is up but page is down ?? in this case you should use curl command.
you can use curl -O <url> instead of wget for downloading.
Configure FTP
on Ubuntu
sudo apt install vsftpdapt list | grep vsftpdsudo service vsftpd statuscp /etc/vsftpd.conf /etc/vsrftpd.conf.origsudo nano /etc/vsftpd.conf
listen=NO
listen ipv6=YES
anonymous_enable=NO
local_enable=YES
write_enable=YES
local_umask=022
dirmessage_enable=YES
use_localtime=YES xferlog_enable=YES
connect_from_port_20=YES
chroot_local_user=YES
secure_chroot_dir=/var/run/vsftpd/empty
pam_service_name=vsftpd
rsa_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
rsa_private_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
ssl_enable=NO
pasv_enable=Yes
pasv_min_port=10000
pasv_max_port=10100
allow_writeable_chroot=YES
systemctl enable vsftpd
FTP Client Configure
if see this error follow as blew
500 Illegal PORT command.
go to passive mode in ftp> pass
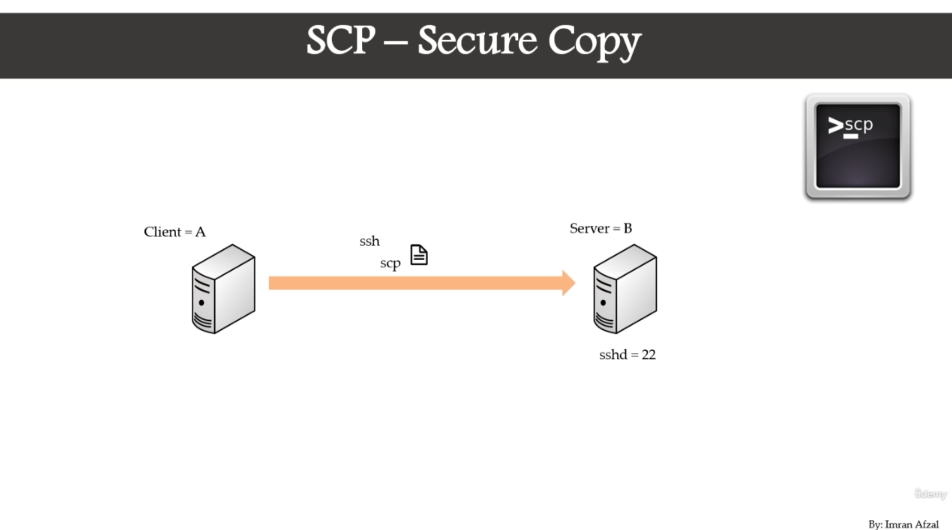
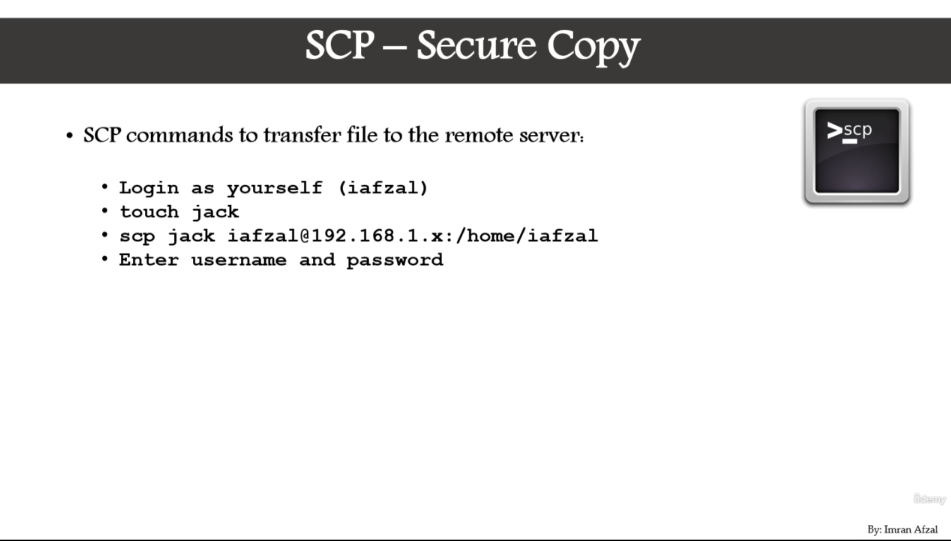
SCP use SSH protocol
configure SCP
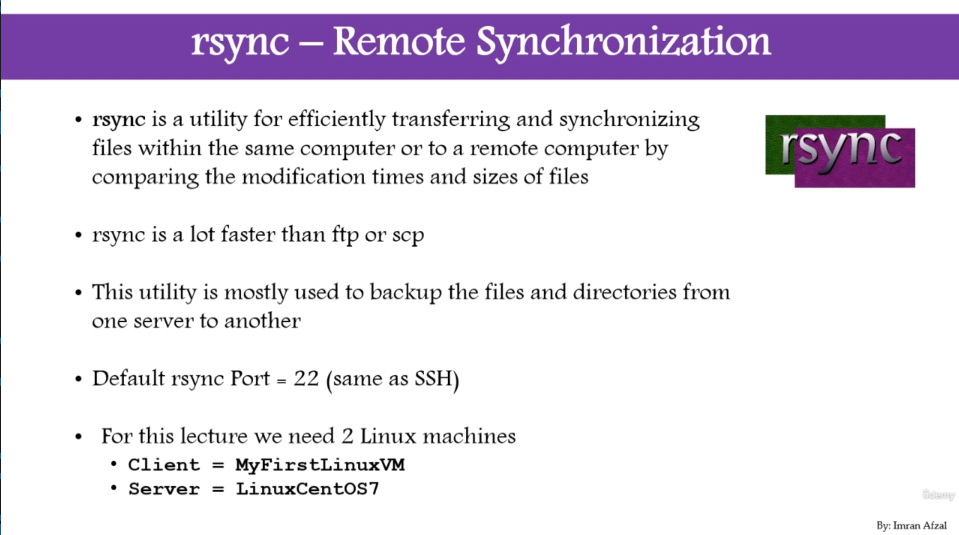
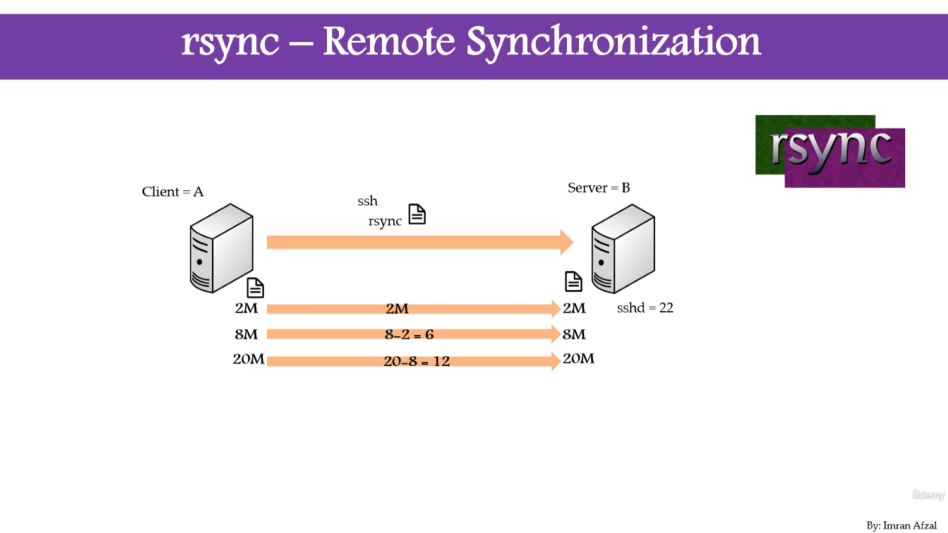
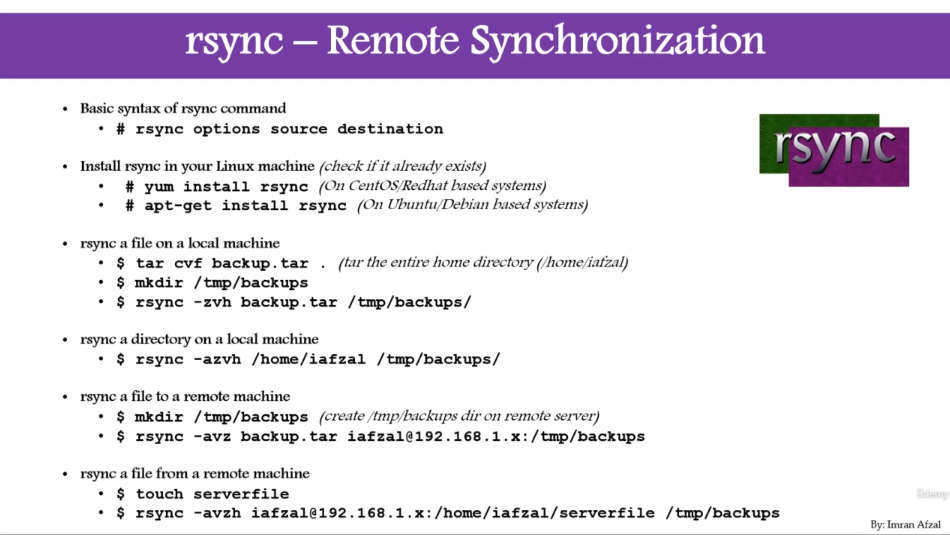
rsync use SSH protocol
configure rsync
- make a directory
- copy all your content to that directory
- go to your local repo directory and run
dpkg-scanpackages . /dev/null > Release - give you current directory size
du -sh . - give you system space
df -h vim /etc/apt/source.list- add the blew line to that file
deb [trusted=yes] file:///opt/debs ./
dpkg and apt are both package management tools for Ubuntu and other Debian-based Linux distributions.
dpkg (Debian Package Manager) is the low-level tool for installing, removing, and managing Debian packages. It is used to install, remove and manage Debian packages. It works on the package files themselves, and does not have the advanced dependency resolution capabilities of apt.
apt (Advanced Packaging Tool) is a higher-level tool that is built on top of dpkg. It provides a more user-friendly interface for managing packages, and also includes advanced features such as dependency resolution, package searching, and automatic updates. It is the recommended tool for managing packages on Ubuntu and other Debian-based Linux distributions.
In short, dpkg is the underlying package management system for Ubuntu and apt is a user-friendly front-end for managing packages on Ubuntu.
- check if a package is installed
dpkg -l | grep package-name
apt list --installed package-name
- remove package
sudo apt remove package-name
sudo apt autoremove
sudo dpkg -r package-name for deleting packages which installed with dpkg -i
- check dependency of a package
apt-cache showpkg package-name
apt-cache search package-name
apt show package-name
- install package
sudo apt install package-name
sudo dpkg -i package-name.deb
install dependency with this sudo apt-get install -f command and then run sudo dpkg -i .deb
- show configuration of package which installed
dpkg -L package-name
dpkg-query -L package-name
sudo find / -user root -group root -name "*package-name*"
- which package this command belongs to
dpkg -S /usr/bin/pwd
- search about a package on the repository
apt-cache search package-name
apt-cache policy package-name
In short, apt update updates the package list, apt upgrade upgrades the packages. It is a good practice to run apt update regularly to keep your package list up to date and apt upgrade periodically to keep your system up to date.
sudo apt-get install example=1.0
show apt history
apt history
cat /var/log/apt/history.log
-
nslookup www.google.com -
dig www.google.com
NTP prot 123
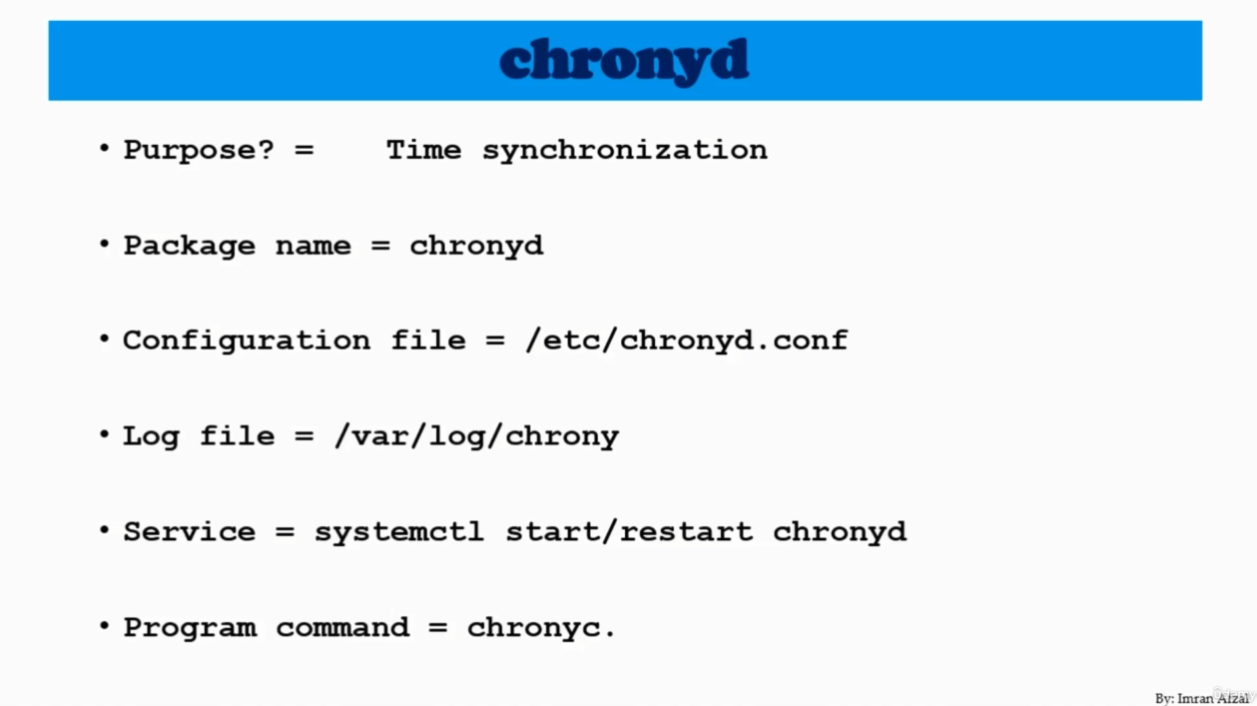
In conclusion, while ntpd is a more traditional and comprehensive NTP implementation, chronyd provides a faster and more efficient solution for NTP synchronization, making it a better choice for resource-constrained systems and systems that require fast and efficient NTP synchronization.
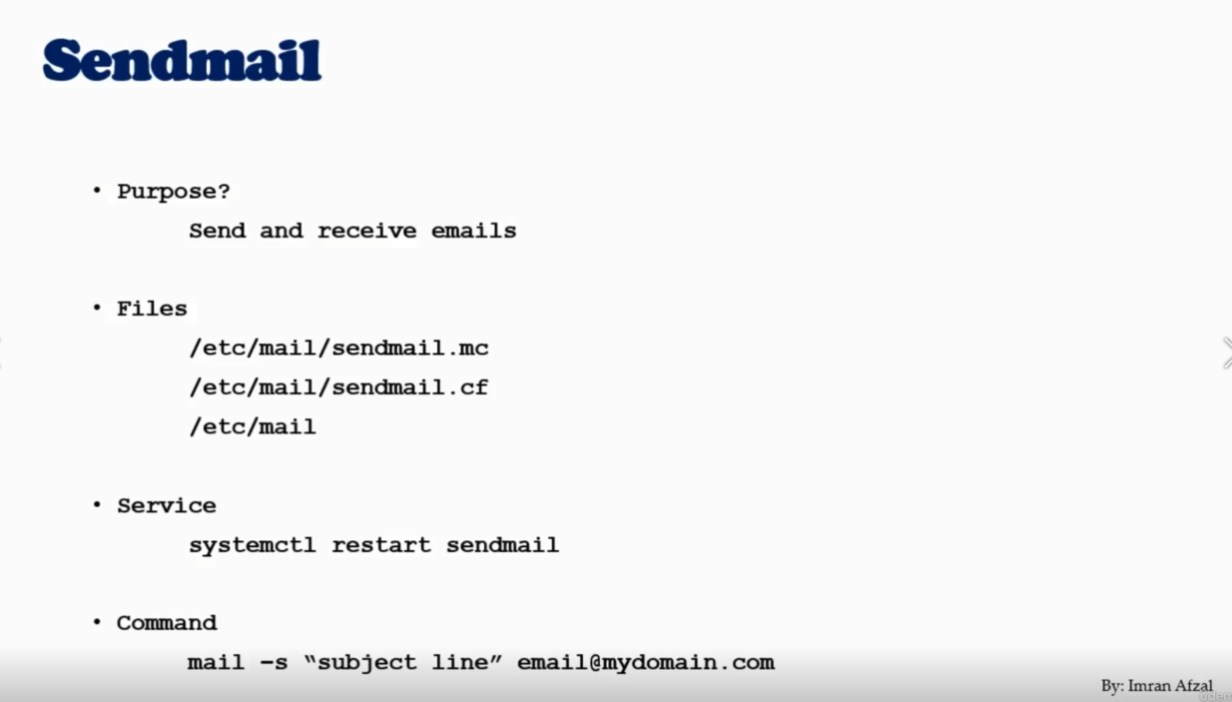
you should always got to /etc/mail/sendmail.mc and make your change into that file and then compile that. go not go straight to /etc/mail/sendmail.cf
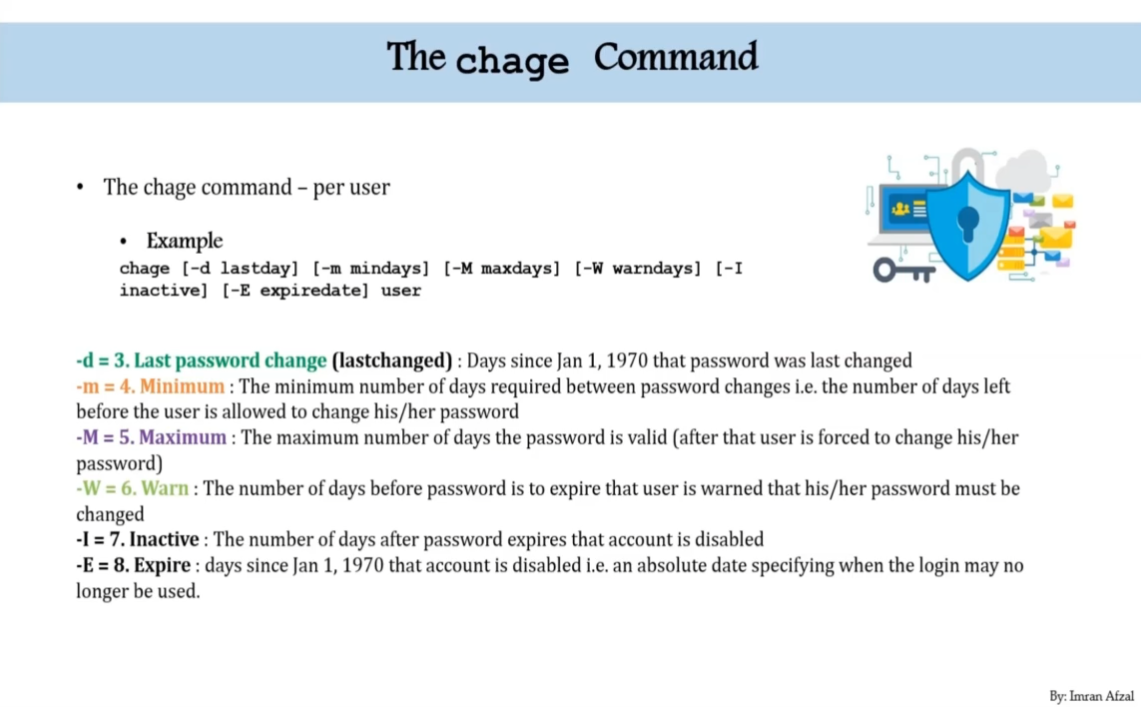
user account
- see all users :
cat /etc/passwd - change user password polices with
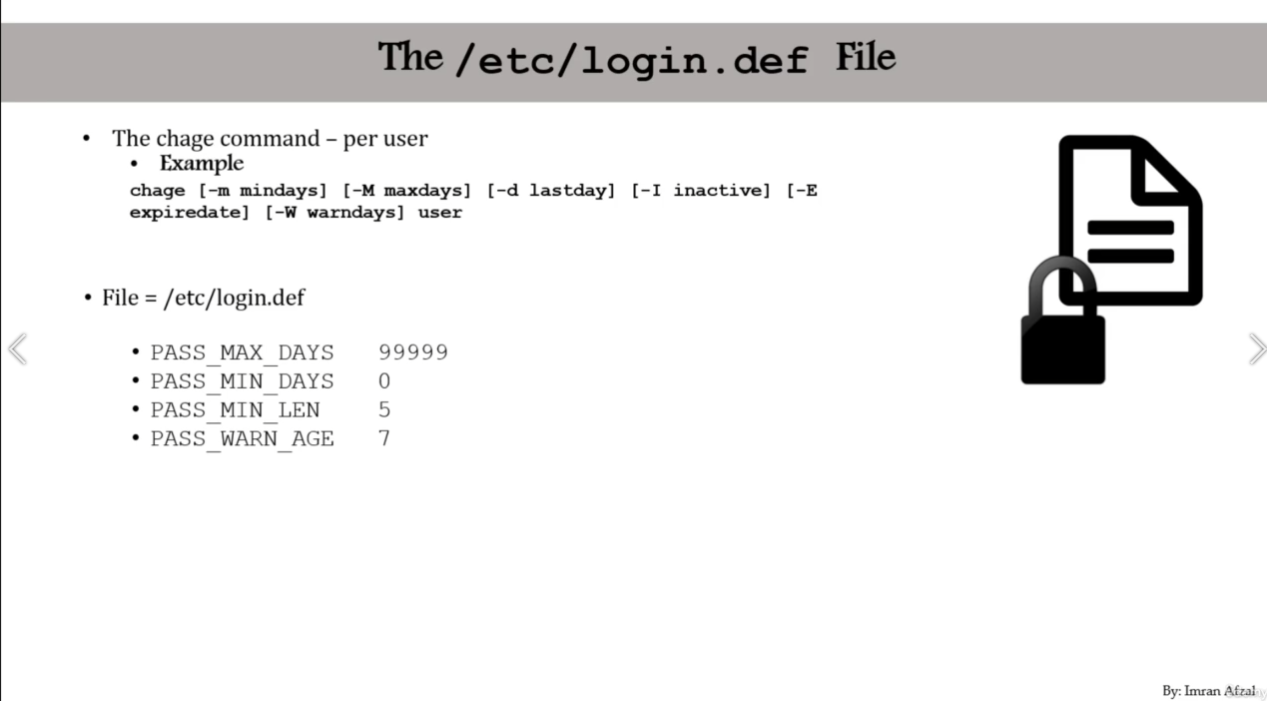
chageorchage -l <username> - or change system password polices for all users
/etc/login.defs - learn about
/etc/pam.d
Remove un-wanted packages
- list all packages
apt list --installed | wc -l
Stop un-used Services
- show all services
systemctl -a
Check on Listening Ports
- show all open port
netstat - tunlp
Secure SSH Configuration
- go to
/etc/sshand secure ssh protocol
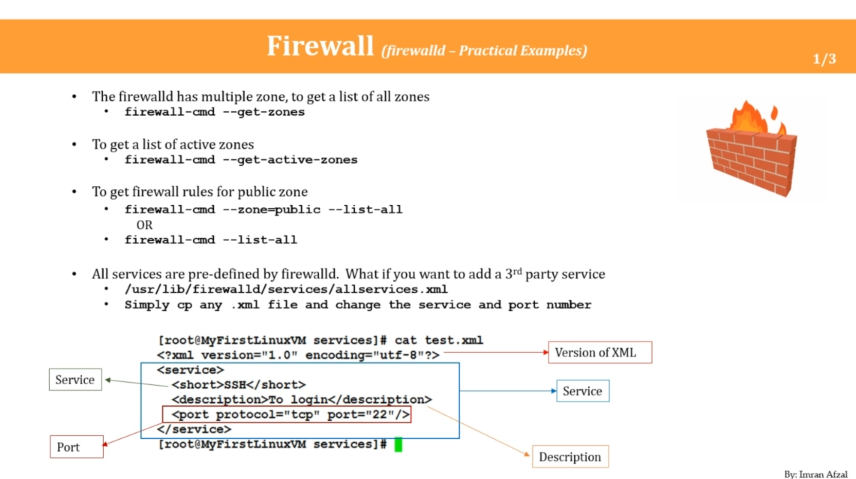
Enable Firewall (iptables/firewalld)
-
firewall gui
firewall-config -
firewall cli
firewall-cmd --help -
iptables --help
Enable SELinux
Change Listening Port Number
Keep your system update
get your gateway netstat -rnv
apt install imageMagick
display <imageName>
7-31
7-32
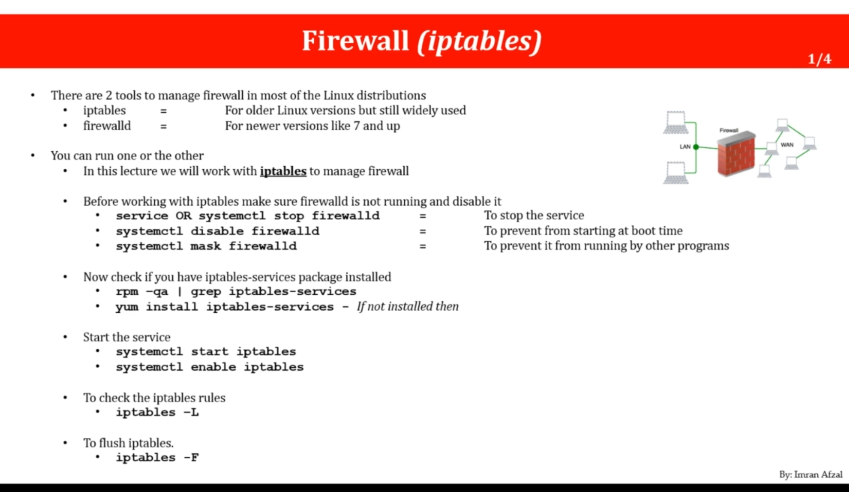
ufw, iptables, and firewalld are all firewall configuration tools that are commonly used on Linux systems. Here are some differences between them:
ufw (Uncomplicated Firewall): This is the default firewall configuration tool for Ubuntu. It is designed to be easy to use and is based on iptables. It uses a simple command-line interface and is designed to provide a basic level of protection. It can be used to set up rules that allow or block incoming and outgoing traffic.
iptables: This is a traditional Linux firewall tool that has been around for a long time. It uses a more complex command-line interface and provides more granular control over the firewall configuration. It can be used to set up rules that allow or block incoming and outgoing traffic, as well as to perform more advanced network address translation (NAT) and packet filtering.
firewalld: This is the default firewall configuration tool for many newer Linux distributions, such as Fedora, RHEL, and CentOS. It is designed to be more dynamic and flexible than ufw and iptables. It uses a command-line interface as well as a graphical interface to allow for easy configuration of firewall rules. It can be used to set up rules that allow or block incoming and outgoing traffic, as well as to perform more advanced features such as port forwarding, masquerading, and network zones.
In summary, while all of these tools can be used to configure a firewall on a Linux system, they differ in their complexity, ease of use, and level of flexibility. ufw is the simplest and easiest to use, while firewalld is the most flexible and dynamic. iptables is the most powerful and provides the most granular control, but it has a steeper learning curve.
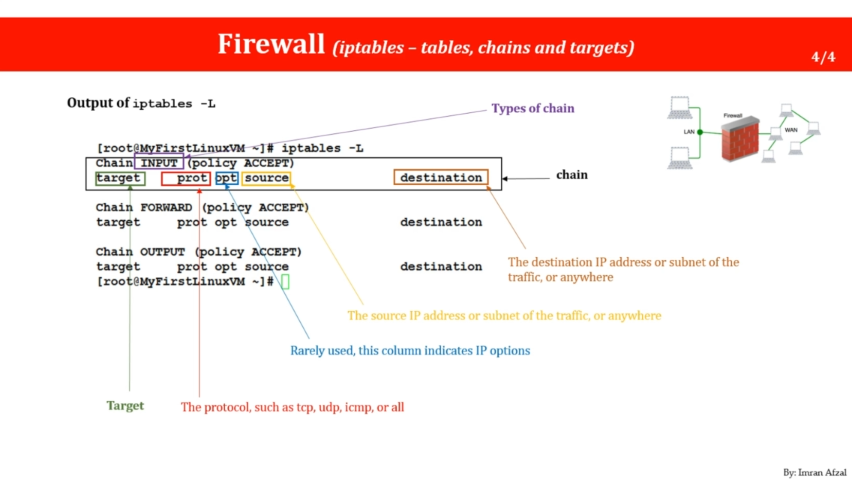
check which firewall is installed
- sudo ufw status
- sudo iptables -L
- sudo firewall-cmd --state
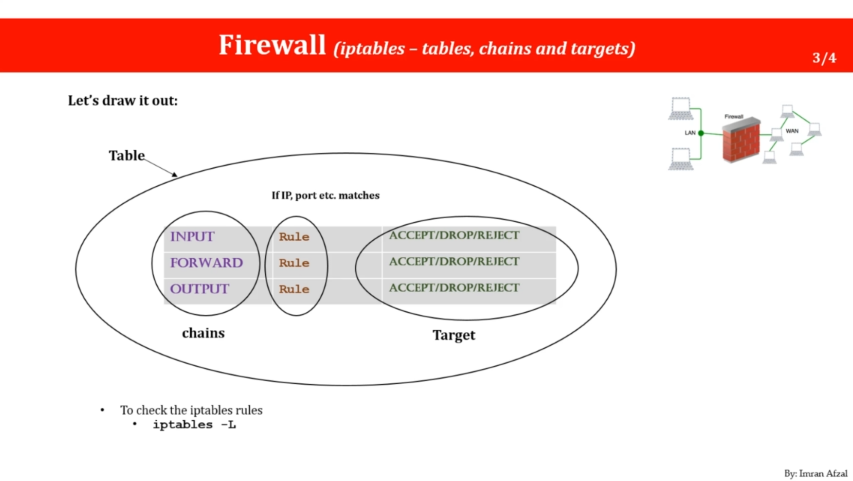
Tables: Think of tables like different boxes that hold different kinds of toys. Each box has a label on it, such as "Toy Cars," "Stuffed Animals," or "Board Games." In iptables, the different boxes are called tables, and each table holds a different set of rules for filtering packets.
Chains: Within each table, there are different chains, which are like shelves inside the box. Each shelf has a label on it, such as "Red Cars," "Big Stuffed Animals," or "Puzzle Games." In iptables, the different shelves are called chains, and each chain holds a set of rules that apply to a specific type of packet.
In summary, the input chain filters incoming packets that are directed towards the local system, the output chain filters outgoing packets that are generated by the local system, and the forward chainfilters packets that are passing through the local system from one network to another.
Targets: Finally, targets are like bins that the toys can be sorted into based on their characteristics. For example, there might be a bin labeled "Broken Toys" for toys that are damaged, or a bin labeled "Toys for Charity" for toys that are being donated. In iptables, the different bins are called targets, and each target specifies what should happen to a packet that matches the rules in the chain.
So to sum up, in iptables, tables are like boxes that hold different sets of rules, chains are like shelves inside the box that hold rules for specific types of packets, and targets are like bins that determine what should happen to packets that match the rules in the chain.
7-37 9:11