(cd dns/local/ && docker build -t local-dns -f dns.dga.Dockerfile .)
(cd dns/attacker-dns/ && docker build -t attacker-dns -f dns.dga.Dockerfile .)
(cd machines/victim/ && docker build -t victim -f victim.dga.Dockerfile .)
(cd machines/c2-server/ && docker build -t c2-server .)docker-compose upGo to the skydive UI.
cd victim
python3 dgacollection/DGA.py- Custom Network (dga_environment): 10.0.0.0/24
- DNS victim (serving victim-domain.com): 10.0.0.2
- victim machines (running the DGA): 10.0.0.3
- DNS attackers : 10.0.0.251
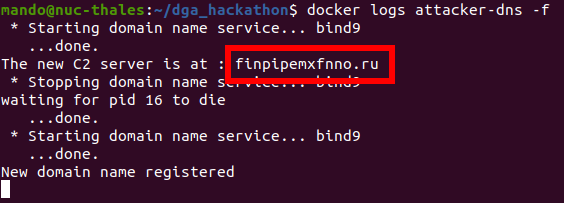
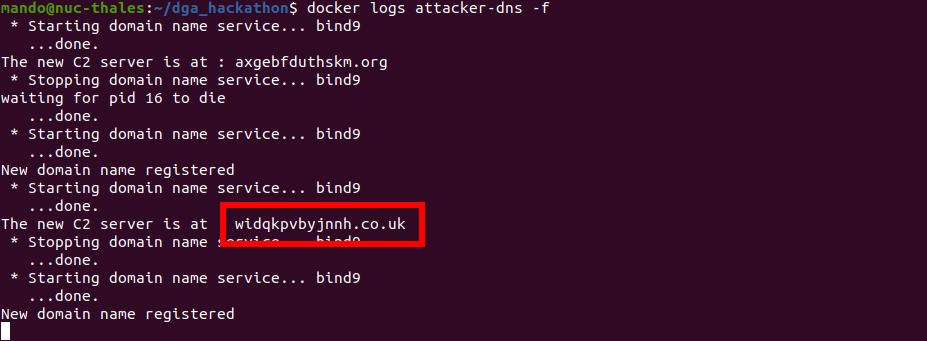
- C2-server (?????????.???): 10.0.0.250
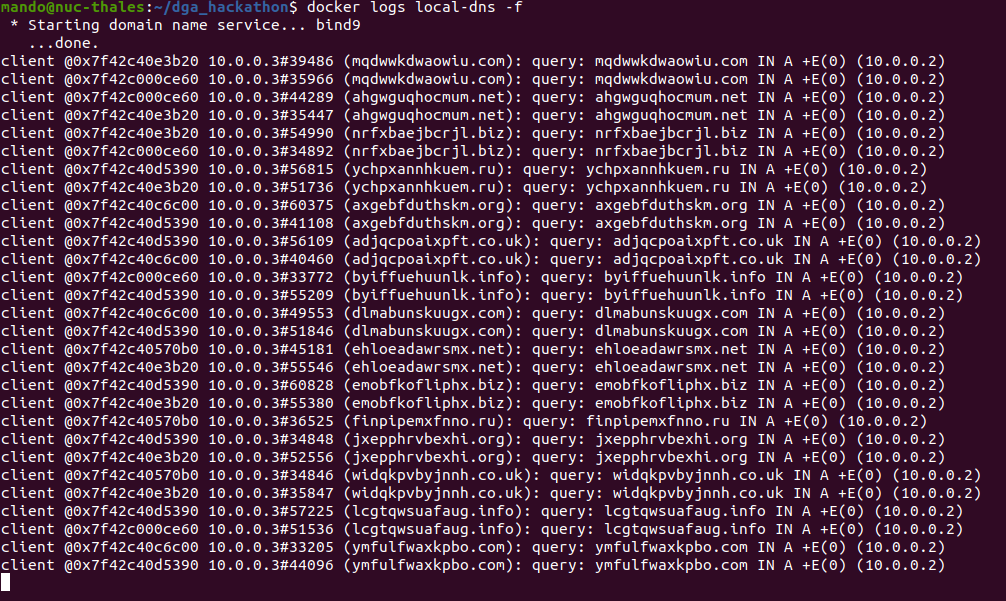
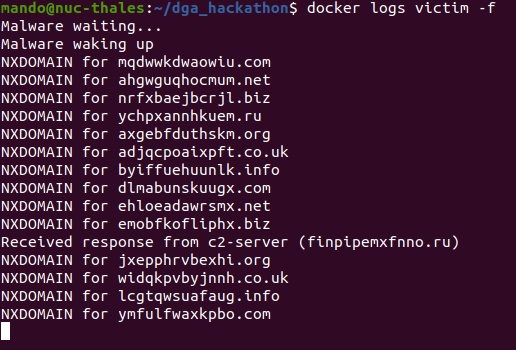
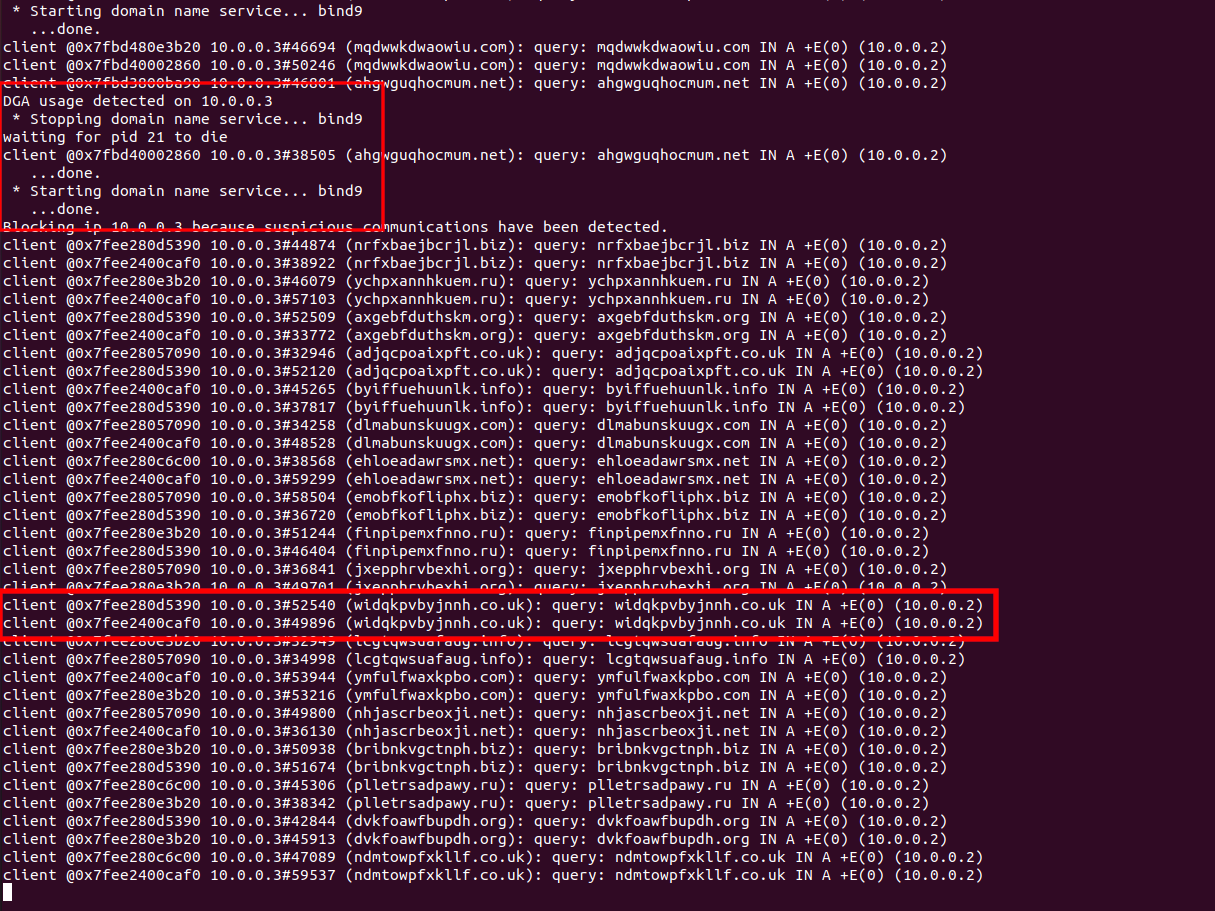
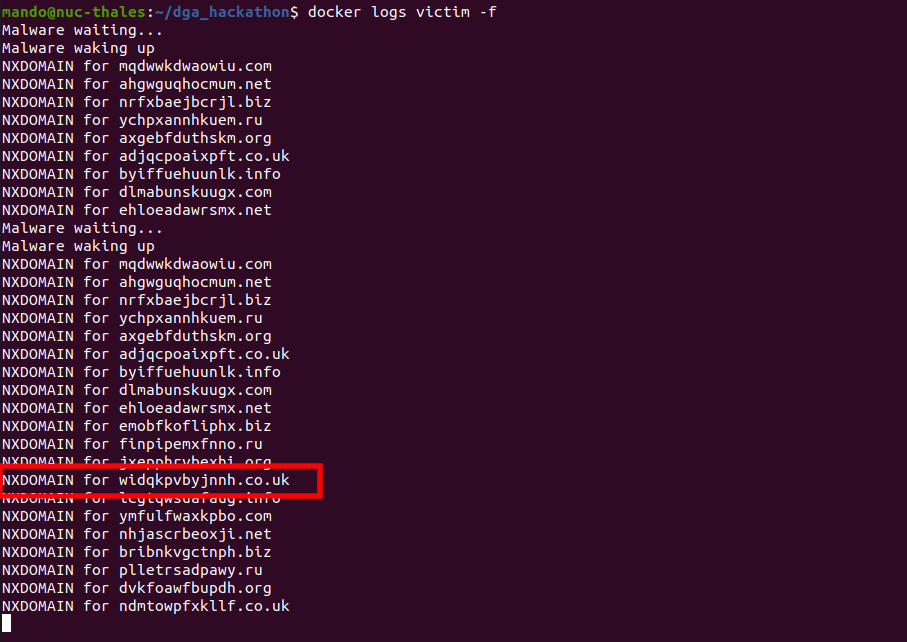
The attacking DNS (10.0.0.251) registers randomly one of the 100 first domains generated for the C2-server (10.0.0.250). When the victim (10.0.0.3) queries the local DNS (10.0.0.3) (who only knows the location of the victim domain), the query is passed to other DNS (including the attacker's one).
That way the victim (in fact the malware) when spraying DNS request will receive NXDOMAIN for most urls except for the one registered by the attacker. In our PoC, we consider that the single fact that the response is not a NXDOMAIN is enough to assess that the malware has successfully connected to the c2-server.
- DGA Collection repo github
- DNS BIND9
- SkyDive for visualization skydive
This project won the technical and public prize of the cybersecurity Hackathon organized by Ecole 42 and Thales (https://ushallnotpass.org/).