PE-Packer is a simple packer for Windows PE files. The new PE file after packing can obstruct the process of reverse engineering.
It will do the following things when packing a PE file:
- Transforming the original import table.
- Encrypting sections.
- Clearing section names.
- Installing the shell-entry.
When running a packed PE file, the shell-entry will decrypt and load the original program as follows:
- Decrypting sections.
- Initializing the original import table.
- Relocation.
Before packing, using some disassembly tools can disassemble the executable file to analyze the code, such as IDA Pro.
After packing, the reverse analysis will be obstructed.
This project is just a demo for beginners to study Windows PE Format and Assembly Language. It still has some compatibility problems and bugs that cannot be used in practice.
The project must configure on/for Windows 32-bit and can only process 32-bit .exe programs now.
- Install MASM32.
- Install MinGW-w64, select
i686architecture. - Install CMake.
- Set the
PATHenvironment variables of these three tools.
mkdir -p build
cd build
cmake .. -D CMAKE_C_COMPILER=gcc -G "MinGW Makefiles"
cmake --build .Or run the build.ps1 file directly:
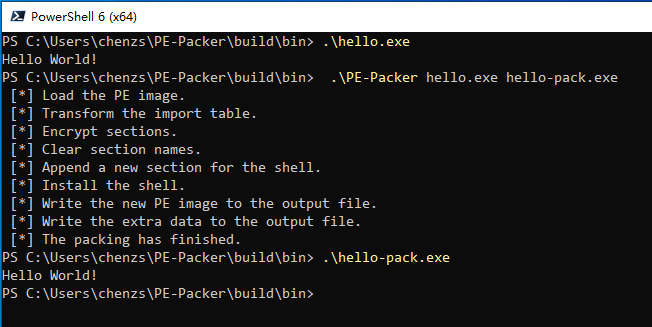
PS> .\build.ps1To pack a program, you must specify its input name and the output name.
PE-Packer <input-file> <output-file>For example:
PE-Packer hello.exe hello-pack.exeYou can use Doxygen to generate the document.
PE Format - Windows Dev Center
Distributed under the GNU General Public License. See LICENSE for more information.
@software{chenzs108_2021_4698355,
author = {Chen Zhenshuo},
title = {czs108/PE-Packer: v1.0.0-beta},
month = apr,
year = 2021,
publisher = {Zenodo},
version = {v1.0.0-beta},
doi = {10.5281/zenodo.4698355},
url = {https://doi.org/10.5281/zenodo.4698355}
}GitHub: https://github.com/czs108
E-Mail: chenzs108@outlook.com
WeChat: chenzs108