This project provides a set of tooling for repeatedly executing and detecting adversary techniques. This project uses the MITRE ATT&CK Enterprise techniques taxonomy (https://attack.mitre.org/techniques/enterprise/) and the MITRE ATT&CK navigator web app (https://github.com/mitre-attack/attack-navigator). This project also makes extensive use of the Atomic Red Team project from Red Canary: (https://github.com/redcanaryco/atomic-red-team), Olaf Hartong's ThreatHunting App for Splunk: (https://github.com/olafhartong/ThreatHunting), Splunk Security Essentials App: (https://splunkbase.splunk.com/app/3435/) and my personal fork of Chris Long's DetectionLab project that includes Phantom in the Terraform scripts for easy spin up: (My Fork: https://github.com/timfrazier1/DetectionLab Original Project: https://github.com/clong/DetectionLab). Once set up, you will be able to repeatedly execute specific techniques, observe the resulting events in Splunk and refine your detection rules and methodology.
Here is a short video demonstrating how it works and what it looks like once set up:
This guide is intended to provide a prescriptive path to getting a minimal adversary simulation setup using Splunk and Phantom (free/community editions). There is obviously much left to the reader once the setup is complete in terms of what techniques to test.
Follow either Option A to use a new fork of Detection Lab with Terraform in AWS (Easiest option), Option B to build your own AWS AMIs or Option C to use Detection Lab locally for getting the basic components in place. Then skip down to "Further Phantom Setup"
This method is still in "beta", but when working, is the easiest method to get all components needed for ATT&CK Sim up and running.
- Clone the DetectionLab fork here: https://github.com/timfrazier1/DetectionLab
- Go here and subscribe to the Splunk Phantom AMI in your AWS account in order to accept the EULA: https://aws.amazon.com/marketplace/pp/Splunk-Inc-Splunk-Phantom/B07K2HPNJG
- Follow the instructions here to set up your Terraform profile and variables: https://github.com/timfrazier1/DetectionLab/blob/master/Terraform/Pre-Built_AMIs.md
- After running "terraform apply" and typing "yes", the build process should begin.
- Please note that this fork of DetectionLab only installs Splunk Universal Forwarder does not have some components enabled (such as OSquery and Bro) for speed of install reasons. This can be easily changed by uncommenting lines 446-450 in the file https://github.com/timfrazier1/DetectionLab/blob/master/Vagrant/bootstrap.sh
- Look for the green output text when the build completes (~20-30 minutes) and you should have your URLs to access Splunk and Phantom.
- Launch Splunk Enterprise AMI on AWS (or on-prem version) (tested with version 7.2.5)
- Commands from Splunk instance CLI
sudo su
yum install git -y
su splunk
cd ~
git clone https://github.com/timfrazier1/AdversarySimulation.git
cd /opt/splunk/etc/apps
git clone https://github.com/daveherrald/SA-attck_nav.git
tar -xzf ~/AdversarySimulation/resources/splunk_apps/phantom-app-for-splunk_275.tgz
tar -xzf ~/AdversarySimulation/resources/splunk_apps/phantom-remote-search_109.tgz
tar -xzf ~/AdversarySimulation/resources/splunk_apps/splunk-app-for-phantom-reporting_100.tgz
tar -xzf ~/AdversarySimulation/resources/splunk_apps/base64_11.tgz
tar -xzf ~/AdversarySimulation/resources/splunk_apps/add-on-for-microsoft-sysmon_810.tgz
tar -xzf ~/AdversarySimulation/resources/splunk_apps/lookup-file-editor_332.tgz
tar -xzf ~/AdversarySimulation/resources/splunk_apps/splunk-common-information-model-cim_4130.tgz
tar -xzf ~/AdversarySimulation/resources/splunk_apps/splunk-security-essentials_252.tgz
tar -xzf ~/AdversarySimulation/resources/splunk_apps/threathunting_141.tgz
/opt/splunk/bin/splunk restart
- From the UI, navigate to "Settings" --> "Access Controls"
- Click "Roles", then "admin"
- Under the "inheritance" section, add the "phantom" role.
- Scroll down and click "save" at the bottom.
- Go to the "Overview" tab of the ATT&CKsim app and Reset the layer by checking the "Reset" radio button and clicking Submit
- Unless you have a valid certificate for Phantom, you will need to disable certificate validation by running:
curl -ku 'username:password' https://splunk_server:8089/servicesNS/nobody/phantom/configs/conf-phantom/verify_certs\?output_mode\=json -d value=0
- with the appropriate substitutions, of course
- CAVEAT EMPTOR: Disabling certificate checking is not allowed in Splunk Cloud and does make the setup less secure. See optional section below for help on creating a certificate if you need it.
- Create the "security" index if using the inputs.conf below
- Go to the "Settings" menu, then "Data" --> "Indexes"
- Click the "New Index" button in the top right
- Give it the name "security", leave the rest default and click "Save" at the bottom
- You will need to make sure the lookup for attck_assets is correct, either using "Lookup Editor" Splunk app or manually editing.
- Go to App context menu in upper left and go to "Lookup Editor" app
- Look for the "attck_assets.csv" file and click on it
- change the hostname, os and ip_address to match your test box(es)
- If you haven't set up your test boxes (windows instructions below) then you may not have this yet. I will remind you to revisit later in these instructions.
- Launch Splunk Phantom AMI on AWS (or on-prem)
- Login with admin/password (You should change your password)
- Go to Administration --> User Management --> Users
- Click on "automation" User
- Change "Allowed IPs" to "any" (or appropriate subnet, if you prefer to be more secure)
- Copy everything in the "Authorization Configuration for REST API" section
- Click "Save"
Go back to Splunk:
- Navigate to Apps --> Phantom --> Phantom Server Configuration
- Click "Create Server"
- Paste clipboard into "Authorization Configuration"
- Give it a name (such as Phantom AWS)
- Click "Save"
- If something is wrong, you will get an error here
- You can also click the "Manage" menu under "Actions" on the right hand side and select "Test Connectivity" to explicitly verify that everything is working
- After successful testing, click "Manage" again and "Set Default", as well as "Sync Playbooks"
- Follow the Windows setup guides as needed
- Skip "Option 2: Detection Lab" and go straight to "Further Phantom Setup"
- Stand up AWS AMI for Windows Server 2019 Base
- Download and modify swiftonsecurity sysmon-config:
- Key exclusions of splunk processes under process creation:
-
<Image condition="is">C:\Program Files\Splunk\bin\splunkd.exe</Image> <Image condition="is">C:\Program Files\SplunkUniversalForwarder\bin\splunk-winprintmon.exe</Image> <Image condition="is">C:\Program Files\SplunkUniversalForwarder\bin\splunk-powershell.exe</Image> <ParentImage condition="is">C:\Program Files\SplunkUniversalForwarder\bin\splunkd.exe</ParentImage>
-
- ~~Key inclusion for Mimikatz:~~
- ~~<TargetImage condition="is">C:\windows\system32\lsass.exe</TargetImage>~~
-
Download and install sysmon: https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
.\Sysmon.exe -accepteula -i .\sysmonconfig-export.xml -
Enable powershell logging to match settings at: https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html
-
Download and install Splunk Universal Forwarder: https://www.splunk.com/en_us/download/universal-forwarder.html
wget -OutFile splunkforwarder-7.3.0-657388c7a488-x64-release.msi 'https://www.splunk.com/bin/splunk/DownloadActivityServlet?architecture=x86_64&platform=windows&version=7.3.0&product=universalforwarder&filename=splunkforwarder-7.3.0-657388c7a488-x64-release.msi&wget=true' -
Install Universal Forwarder as local system (accept defaults) - create local admin splunk_svc_acct - point to Splunk AWS Box IP as indexer (enter default port)
-
Modify inputs.conf to include:
# Windows platform specific input processor.
[WinEventLog://Application]
disabled = 0
index = security
[WinEventLog://Security]
disabled = 0
index = security
[WinEventLog://System]
disabled = 0
index = security
[WinEventLog://Microsoft-Windows-TaskScheduler/Operational]
disabled = 0
index = security
[WinEventLog://Microsoft-Windows-WinRM/Operational]
disabled = 0
index = security
[WinEventLog://Microsoft-Windows-Sysmon/Operational]
disabled = 0
renderXml = true
index = security
[WinEventLog://Microsoft-Windows-PowerShell/Operational]
disabled = 0
index = security
blacklist1 = 4105,4106
blacklist2 = EventCode="4103" Message="(?:SplunkUniversalForwarder\\bin\\splunk-powershell.ps1)"
[monitor://C:\var\log\transcripts\]
disabled = false
index = security
sourcetype = powershell_transcript
- WinRM should be turned on and working with http out of the box. You can check with the following command:
winrm get winrm/config- Make sure that under "service", then "Auth" that Kerberos is set to true.
- In order to use HTTP, "AllowUnencrypted" under "service" will also need to be set to true. - Optional: To use HTTPS, we will be following these instructions: https://www.visualstudiogeeks.com/devops/how-to-configure-winrm-for-https-manually - Basically, you will need to run the following in powershell:
```
winrm quickconfig
New-SelfSignedCertificate -DnsName "<YOUR_DNS_NAME>" -CertStoreLocation Cert:\LocalMachine\My
winrm create winrm/config/Listener?Address=*+Transport=HTTPS '@{Hostname="<YOUR_DNS_NAME>"; CertificateThumbprint="<COPIED_CERTIFICATE_THUMBPRINT>"}'
# Add a new firewall rule
port=5986
netsh advfirewall firewall add rule name="Windows Remote Management (HTTPS-In)" dir=in action=allow protocol=TCP localport=$port
```
- Open port 5986 inbound on AWS for Server (sometimes this is already present)
To review WinRM config:
```
winrm get winrm/config -format:pretty
```
- Stand up AWS Workspaces windows 10 box
- Download and install Splunk Universal Forwarder:
https://www.splunk.com/en_us/download/universal-forwarder.html
- with wget:
wget -OutFile splunkforwarder-7.3.0-657388c7a488-x64-release.msi 'https://www.splunk.com/bin/splunk/DownloadActivityServlet?architecture=x86_64&platform=windows&version=7.3.0&product=universalforwarder&filename=splunkforwarder-7.3.0-657388c7a488-x64-release.msi&wget=true' - Install Universal Forwarder as local system (accept defaults)
- create local admin splunk_svc_acct
-
point to Splunk AWS Box IP as deployment Server (enter default port)- point to Splunk AWS Box IP as indexer (enter default port) - - Download and modify Olaf Hartong's sysmon-config. I like this one here: https://github.com/olafhartong/sysmon-configs/blob/master/sysmonconfig-v10.xml
- You may want to add more exclusions for splunk processes such as:
-
<ProcessCreate onmatch="exclude">
C:\Program Files\Splunk\bin\btool.exe
C:\Program Files\Splunk\bin\splunkd.exe
C:\Program Files\SplunkUniversalForwarder\bin\splunk-winprintmon.exe
C:\Program Files\SplunkUniversalForwarder\bin\splunk-powershell.exe C:\Program Files\SplunkUniversalForwarder\bin\splunkd.exe
-
- Download and install sysmon:
https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
sysmon.exe -accepteula -i sysmonconfig-v10.xml
Step 1: Option B: Spin up Detection Lab (skip down to "Step 2: Further Phantom Setup" if not using DetectionLab)
- Follow instructions here to spin up DetectionLab: https://github.com/clong/DetectionLab
- From the console for "logger" vm (or via ssh):
su splunk
cd /opt/splunk/etc/apps
git clone https://github.com/daveherrald/SA-attck_nav.git
- From the UI, Navigate to "Administrator" --> "Account Settings"
- Change Administrator password to a new value
- From the UI, navigate to "Apps" --> "Find More Apps" - Search for "Phantom" and install "Phantom App for Splunk" - Search for "lookup" and install "Lookup File Editor" - Search for "CIM" and install "Splunk Common Information Model (CIM)" - Install Base64 app from Splunkbase: https://splunkbase.splunk.com/app/1922/ - Then restart Splunk
- From the UI, navigate to "Settings" --> "Access Controls"
- Click "Roles", then "admin"
- Under the "inheritance" section, add the "phantom" role.
- Scroll down and click "save" at the bottom.
- Unless you have a valid certificate for Phantom, you will need to disable certificate validation by running:
curl -ku 'username:password' https://<splunk-address>:8089/servicesNS/nobody/phantom/configs/conf-phantom/verify_certs\?output_mode\=json -d value=0
- with the appropriate substitutions, of course
- CAVEAT EMPTOR: Disabling certificate checking is not allowed in Splunk Cloud and does make the setup less secure.
- Create the "security" index if using the inputs.conf below
- Will need to make sure the lookup for attck_assets is correct, either using "Lookup Editor" Splunk app or manually editing.
- Go to Apps --> Lookup Editor
- Under the "Lookups" title and to the right, click on the filter labeled "App: All" and select "Adversary Simulator"
- Click the only lookup there, "attck_assets.csv"
- Adjust these lines to match your environment
- Possibly still needed(?): Modify the file
/opt/splunk/etc/apps/phantom/bin/ta_addonphantom/modalert_phantom_forward_helper.py- Comment out the "return results" line and uncomment the "return 0" line
- Launch Splunk Phantom AMI on AWS (or on-prem)
- Login with admin/password (You should change your password)
- Go to Administration --> User Management --> Users
- Click on "automation" User
- Change "Allowed IPs" to "any" (or appropriate subnet, if you prefer to be more secure)
- Copy everything in the "Authorization Configuration for REST API" section
- Click "Save"
Go back to Splunk:
- Navigate to Apps --> Phantom --> Phantom Server Configuration
- Click "Create Server"
- Paste clipboard into "Authorization Configuration"
- Give it a name (such as Phantom AWS)
- Click "Save"
- If something is wrong, you will get an error here
Back in Phantom: (Assumption is that the Phantom VM has internet connectivity to download Atomic Red Team)
- Setting up Win RM
- Go to Apps from the main menu
- Search for "Windows" and find the Windows Remote Management app under unconfigured Apps
- Click "Configure New Asset" on the right hand side and give the asset a name while in the "Asset Info" tab
- Under "Asset Settings", point to your Win Server hostname for test connectivity
- For AWS Windows box following above Windows Setup:
- Use HTTP or HTTPS as default protocol depending on how you set it up above
- If HTTPS, change port to 5986
- Leave domain blank
- Use NTLM transport and input your admin user and password
- For DetectionLab Windows box:
- Use the Win10 box IP address for testing
- Use HTTP as default protocol and leave port as 5985
- Use WIN10 as the domain
- Use NTLM transport and input "vagrant" user and "vagrant" password
- Save and "Test connectivity" to validate
- Setting up Splunk connectivity from Phantom
- From main menu, go to Apps
- Search for "Splunk" and click on "unconfigured apps" to find it
- Click "Configure new asset" on the right hand side
- Give it a name with no spaces under "asset info" then click "asset settings" tab
- Put in the IP/Hostname, username and password for your Splunk instance
- Change the timezone to UTC (unless you have this set differently in Splunk)
- Go to the Ingest Settings tab and select (or define) a label to assign to the inbound Splunk events
- Click "Save" go back to the "Asset Settings" tab and then click "Test Connectivity" at the bottom to validate that it is working
- Setting up Atomic Red Team app
- Download https://github.com/timfrazier1/AdversarySimulation/blob/master/phatomicredteam.tgz
- Go to Apps from the main menu
- Click the "Install App" button in the upper right
- Select the downloaded "phatomicredteam.tgz" file
- Once app is installed, find "Atomic Red Team" in unconfigured Apps
- Click "Configure new Asset" on the right hand side
- Give your asset a name with no spaces under "asset info" then click "asset settings" tab
- Leave the default URL as https://github.com/redcanaryco/atomic-red-team.git if you want to use the main ART repo, otherwise, use your own fork
- Hit "Save" and then "Test Connectivity" to build the list of tests
- You should see a "Repo Created Successfully" message
- Setting up the Playbook
- From the main menu, go to Administration -> Administration Settings -> Source Control
- Select "configure new repository", then paste https://github.com/timfrazier1/AdvSimPlaybooks into the URL field
- Use "AdvSim" as the name and "master" as the branch
- Check the "read-only" box and click "Save"
- From the main menu, go to "Playbooks"
- On the listing screen, click the "Repo" column and select "AdvSim" to see the playbooks associated with the repo
- In the "Status" column, click the dropdown next to "Inactive" and select "Active"
- If you want, you can click on "Modular Simulation" to view the playbook in the editor
- Go back to your Splunk Web interface
- Select "Attack Board" from the app navigator
- Find the test you want to execute, right click on it and select "run test" at the bottom of the menu
- In the Simulation Runner app, fill in the dropdown boxes appropriately and then click "Submit"
- You should see something like this in the "Job Status" panel:
sendtophantom - Alert action script completed in duration=2902 ms with exit code=0
- If you don't see "exit code=0", there is some error in executing the tests
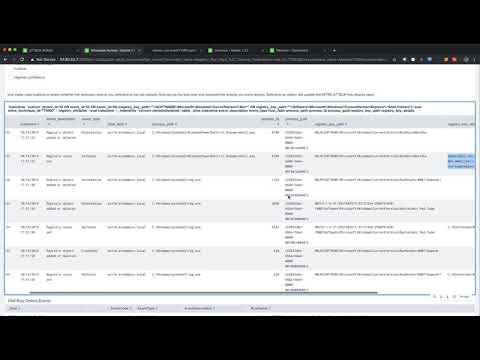
- Assuming you get exit code=0, you should see at least one event in the next panel, "Phantom POST-ed events matching GUID".
- If you don't have any events, Phantom is not POSTing to SPLUNK
- If you only have one event, hover over this panel and then click the circle arrow in the bottom right to refresh this panel. You will need to do this until you see two events in the panel to get your time bracket. The test should only take about 10-20 seconds to complete.
- If you have refreshed after 30-60 seconds and you still don't have at least two events in the panel, you will need to switch over to Phantom to figure out why the test did not complete successfully.
Here is a short video demonstrating how it works and what it looks like once set up:
- Run the following as root:
yum install -y https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
yum install -y certbot python2-certbot-nginx python2-certbot-dns-google
certbot --nginx certonly
#Feed in your domain name and then cd to the new directory with the certs once Created
cp /opt/phantom/etc/ssl/certs/httpd_cert.crt /opt/phantom/etc/ssl/certs/httpd_cert.crt.bak
cp fullchain.pem /opt/phantom/etc/ssl/certs/httpd_cert.crt
cp /opt/phantom/etc/ssl/private/httpd_cert.key /opt/phantom/etc/ssl/private/httpd_cert.key.bak
cp privkey.pem /opt/phantom/etc/ssl/private/httpd_cert.key
service nginx reload
FYI: to renew certificate at a later date, simply run:
certbot renew
cp <path_to_new_cert>/fullchain.pem /opt/phantom/etc/ssl/certs/httpd_cert.crt
cp <path_to_new_cert>/privkey.pem /opt/phantom/etc/ssl/private/httpd_cert.key
service nginx reload