This sample code helps you get started - how to retrieve configuration data and secrets stored in Amazon EC2 System Manager (SSM) Parameter Store. The AWS SAM template creates 3 lambda function with IAM policy and a couple of mock configuration data in SSM paramter store.
This sample includes:
- README.md - this file
- lambda_functions - this folder contains the sample Lambda functions.
- template.yaml - this file contains the Serverless Application Model (SAM) used by AWS Cloudformation that creates 3 Lambda functions, IAM roles & policy and a couple of mock configuration data in SSM paramter store.
- Zip the js files and upload to S3 bucket. Update the S3 bucket name for
lambdaSSMgetparamFunction,lambdaSSMgetparamsFunctionandlambdaSSMgetparamsWithDecryptionFunctionresources.
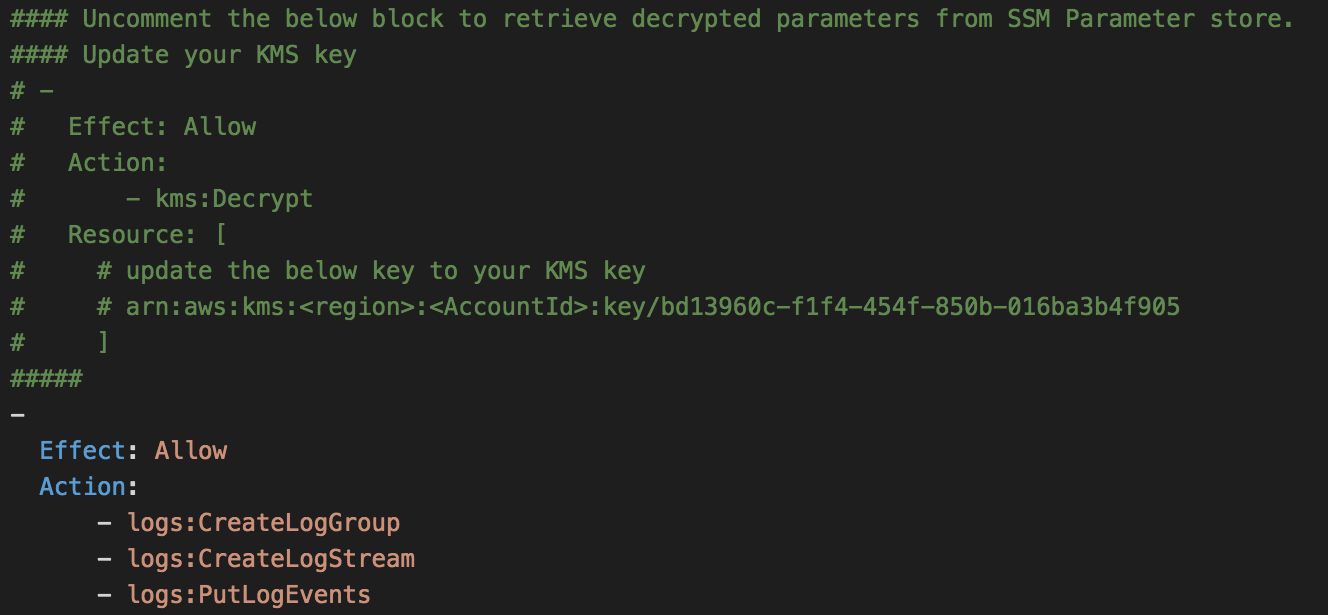
Note: If you dont need to test the "SecureString" functionality of SSM Parameter store, skip step 2 and go to step 3
-
To test
lambda-ssm-getparams-with-decryption-function,- Use the AWS CLI to add "SecureString" parameters to SSM parameter store
aws ssm put-parameter --name dbConnectionString --value <VALUE> --type SecureString --key-id <KMS key id> --region <REGION> aws ssm put-parameter --name dbUsername --value <USERNAME> --type SecureString --key-id <KMS key id> --region <REGION> aws ssm put-parameter --name dbPassword --value <PASSWORD> --type SecureString --key-id <KMS key id> --region <REGION> -
Deploy the solution using AWS SAM Template - template.yaml and test the lambda functions.
Learn more about Serverless Application Model (SAM) and how it works