A plugin set that enables RBA functionality in OpenStack.
Disclaimer: This software plugin was created for research purposes only. It is in no way affiliated with or endorsed by the Open Infrastructure Foundation.
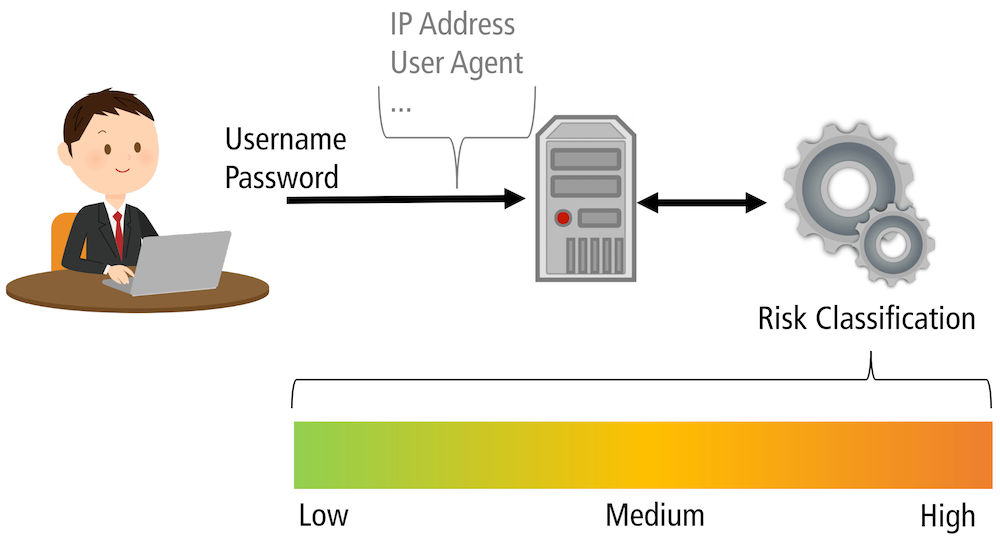
RBA is an adaptive authentication mechanism using contextual information to strengthen password-based authentication. Based on the available information, RBA calculates the risk of how likely the current login attempt is a hacking attempt.
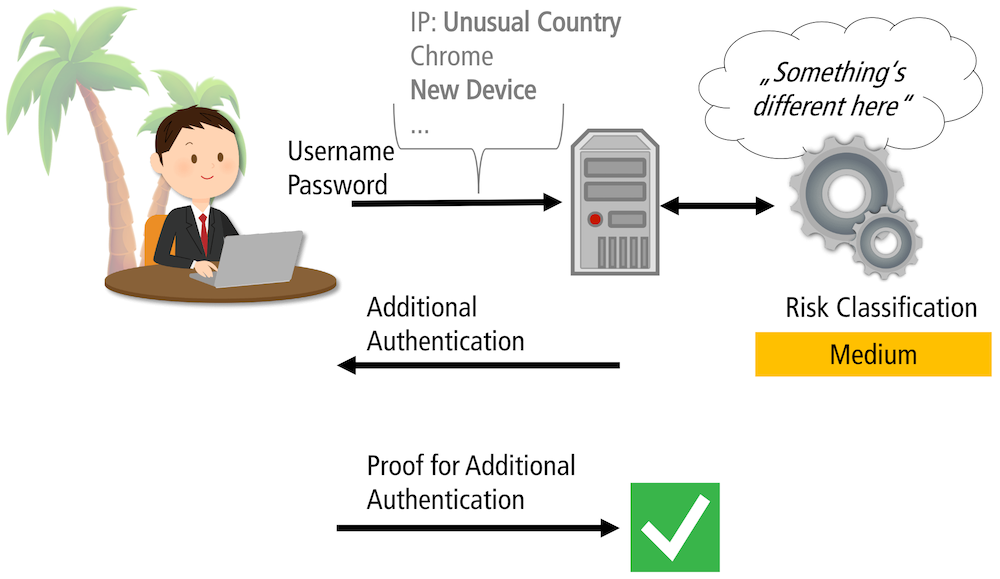
Based on the calculated risk, RBA performs different actions. On a low risk, access is granted without further intervention. On a medium or higher risk, RBA asks for additional information to prove the claimed identity.
In use cases with sensitive information stored on an online service, users find RBA more usable than two-factor authentication (2FA) and equally secure1 (Wiefling et al., 2020). RBA can also achieve very low re-authentication rates for legitimate users, even when blocking more than 99.45% of targeted attackers that know the victim's login credentials, its typical location (city, country), browser, and device. (Wiefling et al., 2021).
Unfortunately, there is a lack of available Open Source RBA solutions which provide good security and usability (Wiefling et al., 2021). Our OpenStack plugins aim to close this gap. This also allows websites with small budget to protect their users with RBA.
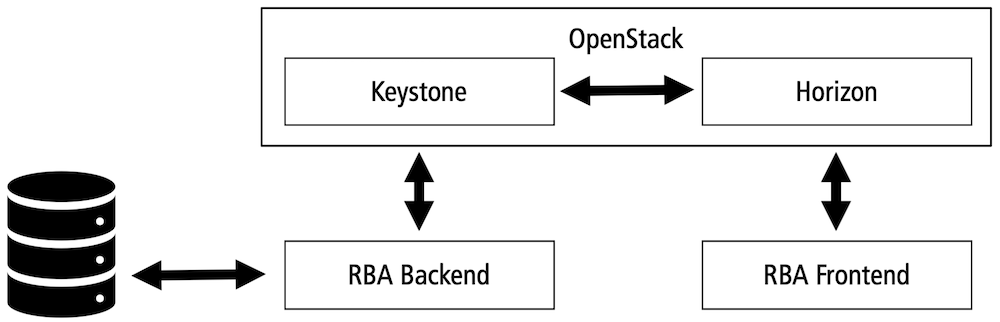
The RBA OpenStack plugin consists of two components which integrate the frontend and the backend functionality:
The backend component enhances the Keystone identity service. It calculates the risk scores based on the collected features and determines whether additional authentication should be requested. Keystone manages all identity related tasks within OpenStack. Therefore, the component adds an additional and independent RBA authentication option to Keystone's multi-factor-authentication (MFA) mechanism. Following this, you can use RBA in addition to other authentication factors as you like.
The frontend component enhances the Horizon Dashboard. It uses the keystoneauth library to communicate with Keystone's REST API. In so doing, it forwards the collected feature data to the backend plugin. Based on the risk decision of the backend component, the frontend plugin can request additional authentication factors. The offered additional authentication factors can be configured in the plugin.
Most of the installations can be done beside already existing Keystone and Horizon installations.
Only the Keystoneauth library will need the replacement with the Keystoneauth fork containing the RBA method. Clone the Keystoneauth fork and install it with the pip package manager:
cd keystoneauth
pip install .
Then clone the keystone_rba_plugin and password_rba-horizon packages and follow their installation guides.
The RBA implementation is based on scientific results of the following publications:
Stephan Wiefling, Paul René Jørgensen, Sigurd Thunem, and Luigi Lo Iacono. Pump Up Password Security! Evaluating and Enhancing Risk-Based Authentication on a Real-World Large-Scale Online Service. In: ACM TOPS. 2022. doi: 10.1145/3546069
Stephan Wiefling, Markus Dürmuth, and Luigi Lo Iacono. What’s in Score for Website Users: A Data-driven Long-term Study on Risk-based Authentication Characteristics. In: FC ’21. 2021. doi:10.1007/978-3-662-64331-0_19.
Michele Campobasso and Luca Allodi. Impersonation-as-a-Service: Characterizing the Emerging Criminal Infrastructure for User Impersonation at Scale. In: CCS '20. 2020. doi:10.1145/3372297.3417892.
Stephan Wiefling, Tanvi Patil, Markus Dürmuth, and Luigi Lo Iacono. Evaluation of Risk-based Re-Authentication Methods. In: IFIP SEC '20. 2020. doi:10.1007/978-3-030-58201-2_19.
Stephan Wiefling, Markus Dürmuth, and Luigi Lo Iacono. More Than Just Good Passwords? A Study on Usability and Security Perceptions of Risk-Based Authentication. In: ACSAC '20. 2020. doi:doi.org/10.1145/3427228.3427243.
Stephan Wiefling, Luigi Lo Iacono, and Markus Dürmuth. Is This Really You? An Empirical Study on Risk-Based Authentication Applied in the Wild. In: IFIP SEC '19. 2019. doi:10.1007/978-3-030-22312-0_10.
David Freeman, Sakshi Jain, Markus Duermuth, Battista Biggio, and Giorgio Giacinto. Who Are You? A Statistical Approach to Measuring User Authenticity. In: NDSS '16. 2016. doi:10.14722/ndss.2016.23240.
We provide more information on how to integrate the software, and the pitfalls that we discovered when working on putting RBA algorithms into software projects in the following publication:
Risk-Based Authentication for OpenStack: A Fully Functional Implementation and Guiding Example (2023)
Vincent Unsel, Stephan Wiefling, Nils Gruschka, and Luigi Lo Iacono.
13th ACM Conference on Data and Application Security and Privacy (CODASPY '23), Charlotte, NC, USA.
@inproceedings{Unsel_Risk_2023,
title = {{Risk-Based Authentication for OpenStack: A Fully Functional Implementation and Guiding Example}},
author = {Unsel, Vincent and Wiefling, Stephan and Gruschka, Nils and Lo Iacono, Luigi},
booktitle = {{13th ACM Conference on Data and Application Security and Privacy}},
year = {2023},
series = {{CODASPY} '23},
location = {Charlotte, NC, USA},
publisher = {ACM},
doi = {10.1145/3577923.35836},
month = apr,
year = {2023}
}We provide this software without warranty. However, if you like to integrate such a RBA solution into your own online service, feel free to contact us for support or consulting.
E-Mail: das@h-brs.de
The RBA illustrations on this page are licensed under a Creative Commons Attribution 4.0 International License.
When using these illustrations, you need to give appropriate credit based on the media type. The required attributions are stated below.
© 2021 Stephan Wiefling/riskbasedauthentication.org (CC BY 4.0).
When using one or more of the illustrations in a publication, you have to cite the following journal article:
Stephan Wiefling, Markus Dürmuth, and Luigi Lo Iacono. Verify It’s You: How Users Perceive Risk-Based Authentication. IEEE Security & Privacy, 19(6), pp. 47-57, November 2021. doi:10.1109/MSEC.2021.3077954
Footnotes
-
Except for very high security demands, like online banking, where users preferred 2FA to RBA. ↩