SSHConfig is software that allows you to configure SSH configuration files on GUI.
It is created in Qt 5.15, so it requires Qt 5.15 library.
This article uses Manjaro ARM(AArch64) and SUSE Linux Enterprise(x86_64).
you should be able to install it on other Linux distributions as well.
(Ex. Mobian, Fedora, Debian, ... etc)
Note:
Currently, "AcceptEnv", "Subsystem", and "Match" keywords are not supported.
These settings can be written from the SSHConfig "editor" function.
I recommend using openSSH version 8.4 or later.
If you want to know which version of openSSH you are using, execute following command in terminal.
ssh -V
Common to Linux PC, PinePhone.
- Qt5 Core
- Qt5 Gui
- Qt5 Widgets
- Qt5 D-Bus
- Qt5 Concurrent
- Qt5 Quick
- Qt5 QuickControls2
- Qt5 Qml
- Qt5 QmlModels
- Qt5 Network (Use libRemoteWindow.so, SSHConfigServer)
- Qt5 Linguist (Translation)
- https://www.qt.io/
- This software uses Qt, and Qt used is under LGPL license.
- You will find its license file in following directory.
ThirdPartyLicenses/Qt.txt
- Polkit-Qt1 (Use SSHConfigHelper)
- https://api.kde.org/polkit-qt-1/html/
- This software uses Polkit-Qt1, and Polkit-Qt1 used is under LGPL license.
- You will find its license file in following directory.
ThirdPartyLicenses/Polkit-Qt1.txt.txt
- Polkit (Use SSHConfigHelper)
- https://www.freedesktop.org/software/polkit/docs/latest/
- Polkit-Qt1 uses Polkit, and Polkit used is under LGPL license.
- You will find its license file in following directory.
ThirdPartyLicenses/Polkit.txt
libbsd (Use SSHConfigServer)(Currently not used)https://libbsd.freedesktop.orgThis software uses a portion of libbsd, and the portion of libbsd used is under ISC license.You will find its license file in following directory.
ThirdPartyLicenses/libbsd_readpassphrase.txt
Get the latest updates.
sudo zypper update
sudo dnf update
sudo apt update && sudo apt upgrade
sudo pacman -Syu
Install the dependencies required to build the SSHConfig and SSHConfig Server.
# SUSE Linux Enterprise / openSUSE
sudo zypper install \
coreutils gcc cmake polkit-devel libpolkit-qt5-1-devel \
libqt5-qtbase-common-devel libqt5-linguist libqt5-linguist-devel \
libQt5Core-devel libQt5Gui-devel libQt5Widgets-devel libQt5DBus-devel \
libQt5QuickControls2-devel libQt5Network-devel libQt5Xml-devel \
libQt5Concurrent-devel libqt5-qtdeclarative-tools
# Fedora
sudo dnf install \
gcc coreutils cmake polkit-devel polkit-qt5-1-devel \
qt5ct qt5-linguist qt5-qtdeclarative-devel \
qt5-qtbase-devel qt5-qtquickcontrols2-devel qqc2-desktop-style
# Debian Bullseye
sudo apt install \
gcc coreutils cmake \
libpolkit-agent-1-dev libpolkit-gobject-1-dev libpolkit-qt5-1-dev \
qt5-qmake qt5-qmake-bin qttools5-dev-tools qt5ct \
qtdeclarative5-dev qtdeclarative5-dev-tools \
qtbase5-dev qtbase5-dev-tools qtquickcontrols2-5-dev\
qml-module-qtquick2 qml-module-qtquick-window2 qml-module-qtquick-controls2 qml-module-qtquick-controls \
qml-module-qtquick-layouts qml-module-qtquick-dialogs qml-module-qt-labs-settings qml-module-qt-labs-platform
# Manjaro (for x64)
sudo pacman -S --needed \
pkgconfig coreutils gcc cmake polkit polkit-qt5 \
qt5ct qt5-tools qt5-base qt5-quickcontrols2 qt5-declarative qt5-wayland \
qml-material
# Manjaro ARM (for PinePhone)
sudo pacman -S --needed \
pkgconfig coreutils gcc cmake polkit polkit-qt5 \
qt5ct qt5-tools qt5-base qt5-quickcontrols2 qt5-declarative qt5-wayland \
qml-material
Download the source code from SSHConfig's Github.
git clone https://github.com/presire/SSHConfig.git SSHConfig
cd SSHConfig
mkdir build && cd build
Use the "qmake" or "cmake" command to compile the source code of SSHConfig.
The default installation directory is /usr/local.
In the following example, the installation directory is the home directory. (Ex. ~/InstallSoftware/SSHConfig)
# for PC
qmake ../SSHConfigTop.pro prefix=<The directory you want to install in>
or
qmake-qt5 ../SSHConfigTop.pro prefix=<The directory you want to install in>
or
cmake -DCMAKE_INSTALL_PREFIX=<The directory you want to install in> \
..
# for PinePhone
qmake ../SSHConfigTop.pro machine=pinephone prefix=<The directory you want to install in>
or
cmake -DMACHINE=pinephone -DCMAKE_INSTALL_PREFIX=<The directory you want to install in> \
..
make -j $(nproc)
make install
or
sudo make install
# If you are installing to any directory.
cd <path to SSHConfig directory>/share/applications
cp SSHConfig.desktop ~/.local/share/applications
or
sudo cp SSHConfig.desktop /usr/share/applications
First, check if SSHConfig Polkit action file exists /usr/share/polkit-1/actions/org.presire.sshconfig.policy.
If SSHConfig is installed in arbitrary directory, copy the Polkit action file in /usr/share/polkit-1/actions directory.
sudo cp /<SSHConfig installation directory>/share/polkit-1/actions/org.presire.sshconfig.policy \
/usr/share/polkit-1/actions
Next, check if SSHConfig D-Bus startup file exists /usr/share/dbus-1/system-services/org.presire.sshconfig.service.
If SSHConfig is installed in arbitrary directory, copy the D-Bus startup file in /usr/share/dbus-1/system-services directory.
sudo cp /<SSHConfig installation directory>/share/dbus-1/system-services/org.presire.sshconfig.service \
/usr/share/dbus-1/system-services
Last, check if SSHConfig D-Bus Configuration file (for System Bus) exists /usr/share/dbus-1/system.d/org.presire.sshconfig.conf directory.
If SSHConfig is installed in arbitrary directory, copy the D-Bus Configuration file in /usr/share/dbus-1/system.d directory.
sudo cp /<SSHConfig installation directory>/share/dbus-1/system.d/org.presire.sshconfig.conf \
/usr/share/dbus-1/system.d
On remote server running ssh, download source code from SSHConfig's Github.
git clone https://github.com/presire/SSHConfig.git SSHConfig
cd SSHConfig/SSHConfigServer
mkdir build && cd build
Use the "qmake" or "cmake" command to compile the source code of SSHConfig.
The default installation directory is /usr/local.
Default installation location of SSHConfigServer configuration file is /etc/sshconfig/sshconfig.json.
Also, default installation location of Systemd service file for SSHConfigServer is /etc/systemd/system/sshconfigd.service.
# for PC and PinePHone
qmake ../SSHConfigServer.pro prefix=<The directory you want to install in>
or
cmake -DCMAKE_INSTALL_PREFIX=<The directory you want to install in> \
..
make -j $(nproc)
make install
The following build options also exist for SSHConfigServer builds.
-
sysconfdir (qmake) or -DSYSCONFDIR (cmake)
Specify path to SSHConfigServer configuration file is located. -
systemd (qmake) or -DSYSTEMD (cmake)
Specify path to systemd service of SSHConfigServer is located. -
user (qmake) or -DUSER (cmake)
Specify user who executes systemd service of SSHConfigServer. -
group (qmake) or -DGROUP (cmake)
Specify group who executes systemd service of SSHConfigServer. -
pid (qmake) or -DPID (cmake)
Specify PID when systemd service of SSHConfigServer is executed.
For example, following build command modifies configuration file (~/config/sshconfig) and process ID file (/tmp/SSHConfigServer.pid).
qmake ../SSHConfigServer.pro prefix=<The directory you want to install in>
sysconfdir=$HOME/config/sshconfig pid=/tmp
or
cmake -DCMAKE_INSTALL_PREFIX=<The directory you want to install in> \
-DSYSCONFDIR=$HOME/config/sshconfig -DPID=/tmp
..
Reload daemon after installation.
Or, restart server.
sudo systemctl daemon-reload
or
sudo systemctl restart (sudo shutdown -r now)
To start SSHConfigServer, execute following command.
sudo systemctl start sshconfigd.service
or
sudo systemctl restart sshconfigd.service
To start SSHConfigServer automatically at server startup, do the following.
sudo systemctl enable sshconfigd.service
Alternatively, SSHConfig Server can be started by executing following command on terminal.
sudo SSHConfigServer --sysconfdir=<Directory sshconfig.json is located>
or
sudo SSHConfigServer --sysconfdir=<Directory sshconfig.json is located> --locale=jp
SSHConfig configuration file is located in ~/.config/SSHConfig/settings.ini.
This file describes main screen settings and server connection settings.
In the /usr/share/dbus-1/system-services/org.presire.sshconfig.service,
adding --locale=jp option to Exec keyword will cause SSHConfigHelper's messages output will be in Japanese.
[D-BUS Service]
Name=org.presire.sshconfig
Exec=/path/to/SSHConfigHelper --locale=jp
User=root
attention (heed)
If you are using SELinux (Fedora, etc...), you must Add a policy to SELinux.
Below is how to add policies to SELinux.
-
Go to the directory where te files for SSHConfig Helper are located.
This is located in the top directory of the project.
cd /<SSHConfig's top source directory>/SELinux -
Add policy packages to SELinux.
sudo semodule -i sshconfig.pp
You can also compile and add policy module as follows.
-
Go to directory where "te" file for SSHConfig Helper.
This is located in the top directory of the project.
cd /<SSHConfig's top source directory>/SELinux -
Install necessary libraries.
sudo dnf install checkpolicy policycoreutils -
Compile policy module.
checkmodule -M -m -o sshconfig.mod sshconfig.te -
Create policy package.
semodule_package -o sshconfig.pp -m sshconfig.mod -
Add policy package to SELinux.
sudo semodule -i sshconfig.pp
Check the added policy module.
sudo semodule -l | grep -i sshconfig
You can also delete the added policy module.
sudo semodule -r sshconfig.pp
It is deprecated to disable SELinux as described below.
sudo setenforce 0
/etc/sshconfig/sshconfig.json
It is recommended that permissions on this file be set to 600.
-
PORT
Port number used for TCP or SSL connections. -
USESSL
Whether to use SSL connection. -
USECERT
Whether to use server certificate when SSL connection. -
CERTFILE
Full path to server certificate when using server certificate. -
USEKEY
Whether to use the private key when SSL connection. -
KEYFILE
Full path to private key when using private key. -
USEPASSPHRASE
Whether to use passphrase when using private key. -
PASSPHRASE
Input passphrase when using private key.
{
"PORT": {
"value": 61060
},
"USESSL": {
"value": false
},
"USECERT": {
"value": false
},
"CERTFILE": {
"value": ""
},
"USEKEY": {
"value": false
},
"KEYFILE": {
"value": ""
},
"USEPASSPHRASE": {
"value": false
},
"PASSPHRASE": {
"value": ""
},
}
Open a firewall port on remote server.
sudo firewall-cmd --permanent --add-port=<Port Number>/tcp
# Ex. The default port of the SSHConfig server is open.
sudo firewall-cmd --permanent --add-port=61060/tcp
Reload changes in the firewall.
sudo firewall-cmd --reload
For SSHConfig application, format of sshd_config file shall follow rules below.
--Enable item--
Port 22
Port 22 # Blank spaces may be present at the beginning of item.
Port 22 # Any number of blank spaces are allowed.
--Commented item--
When commenting item, must be no space between "#" and item name.
#Port 22 # Correct.
#Port 22 # Correct.
# Port 22 # Worst.
--Comment statement--
Comment text should have at least one space between "#" and comment text.
# This is comment statement # Correct.
# This is comment statement # Correct.
#This is comment statement # Worst.
ChallengeResponseAuthentication is deprecated and KbdInteractiveAuthentication is recommended instead.
SSHConfig application follows rules below.
# If both are commented or not described,
# changes are made to KbdInteractiveAuthentication.
#ChallengeResponseAuthentication yes
#KbdInteractiveAuthentication yes
# If ChallengeResponseAuthentication is enabled and KbdInteractiveAuthentication commented,
# changes are made to ChallengeResponseAuthentication.
ChallengeResponseAuthentication yes
#KbdInteractiveAuthentication yes
# If both are enabled,
# then, ChallengeResponseAuthentication is commented and
# changes are made to KbdInteractiveAuthentication.
ChallengeResponseAuthentication yes
KbdInteractiveAuthentication yes
Make sure you can execute SSHConfig.
(Destop entry or SSHConfig.sh or SSHConfig binary)
Note:
To run the SSHConfig binary directly, add directory containing libRemoteWindow.so to "LD_LIBRARY_PATH" environment variable.
| SSHConfig Main (Server Mode) | SSHConfig Main(1) (Client Mode) | SSHConfig Main(2) (Client Mode) |
|---|---|---|
 |
 |
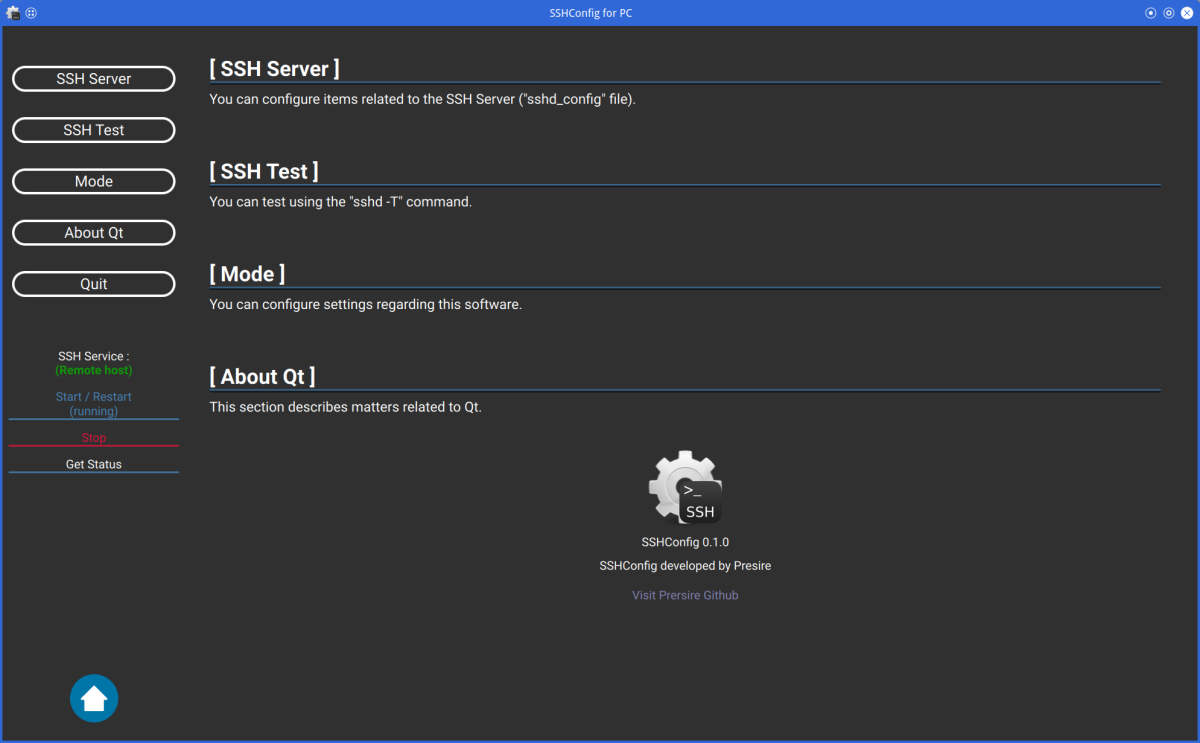 |
Select the item you wish to set from buttons on the left side of main screen.
You can start (restart) and stop SSH by clicking on the labels under the buttons.
To start (restart) and stop SSH on remote server, you must enter the remote connection settings.
You can return to Home Screen by pressing [Home] button or [Shift] + [Esc] buttons.
If your mouse has [Forward] or [Back] button, you can go back and forward through each menu screen.
| SSHConfig Configuration(1) (Server Mode) | SSHConfig Configuration(2) (Server Mode) | SSHConfig Configuration(3) (Server Mode) |
|---|---|---|
 |
 |
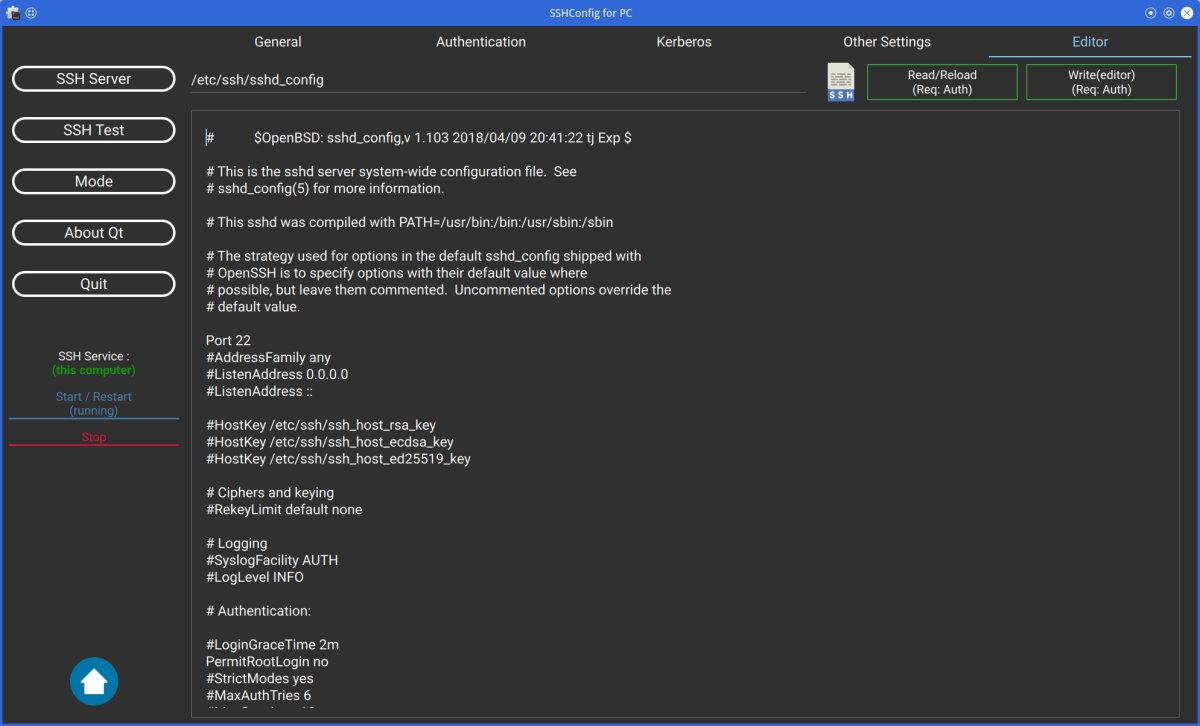 |
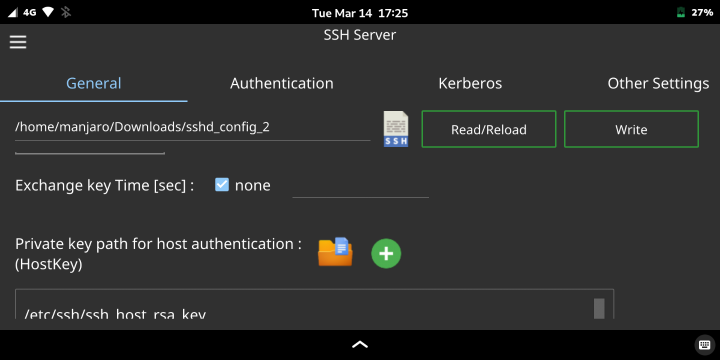
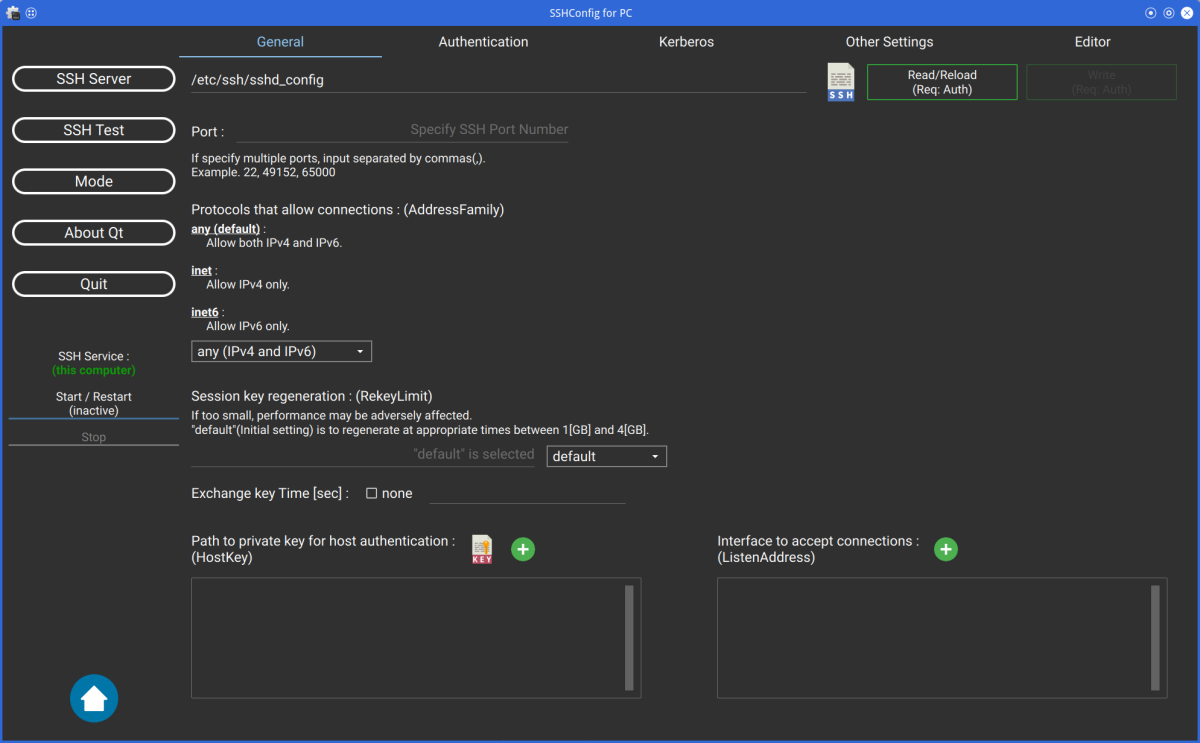
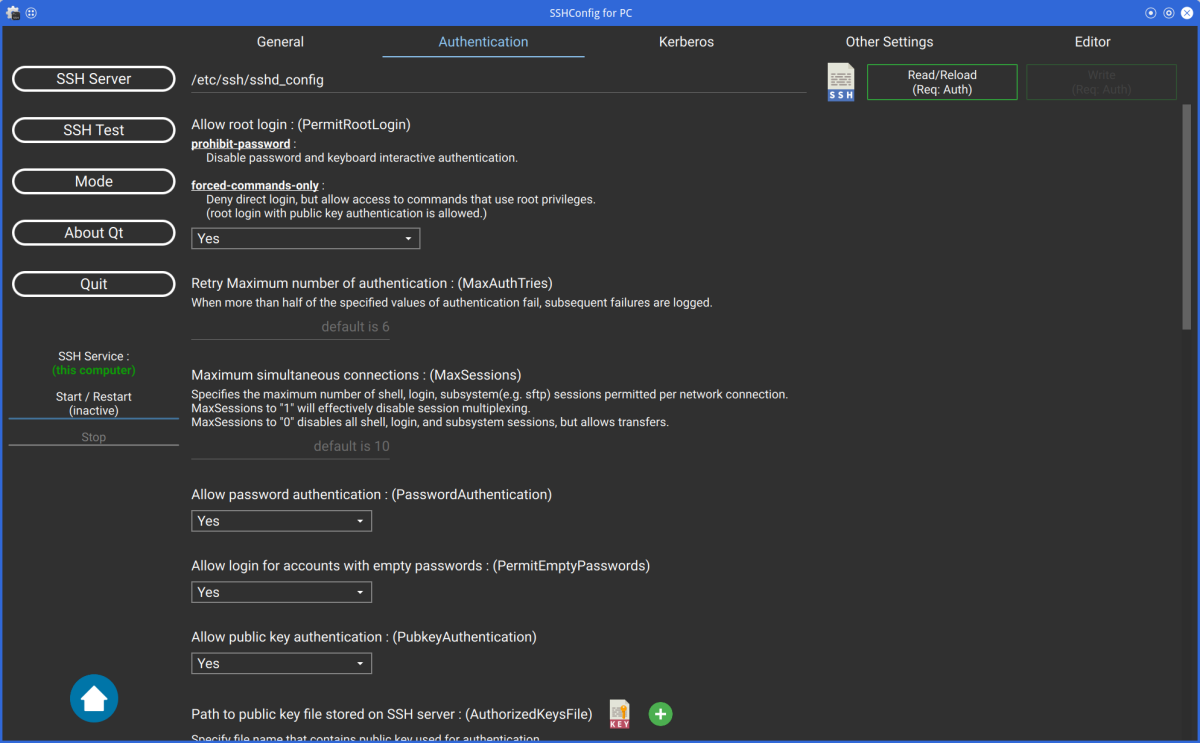
Click the [SSH Server] button to configure various SSH settings.
Currently, "AcceptEnv", "Subsystem", and "Match" keywords are not supported.
These settings can be written from the "editor" tab.
When select the "Editor" tab, write button name is "Write (Editor)".
This means that only changes made in the "Editor" tab will be written.
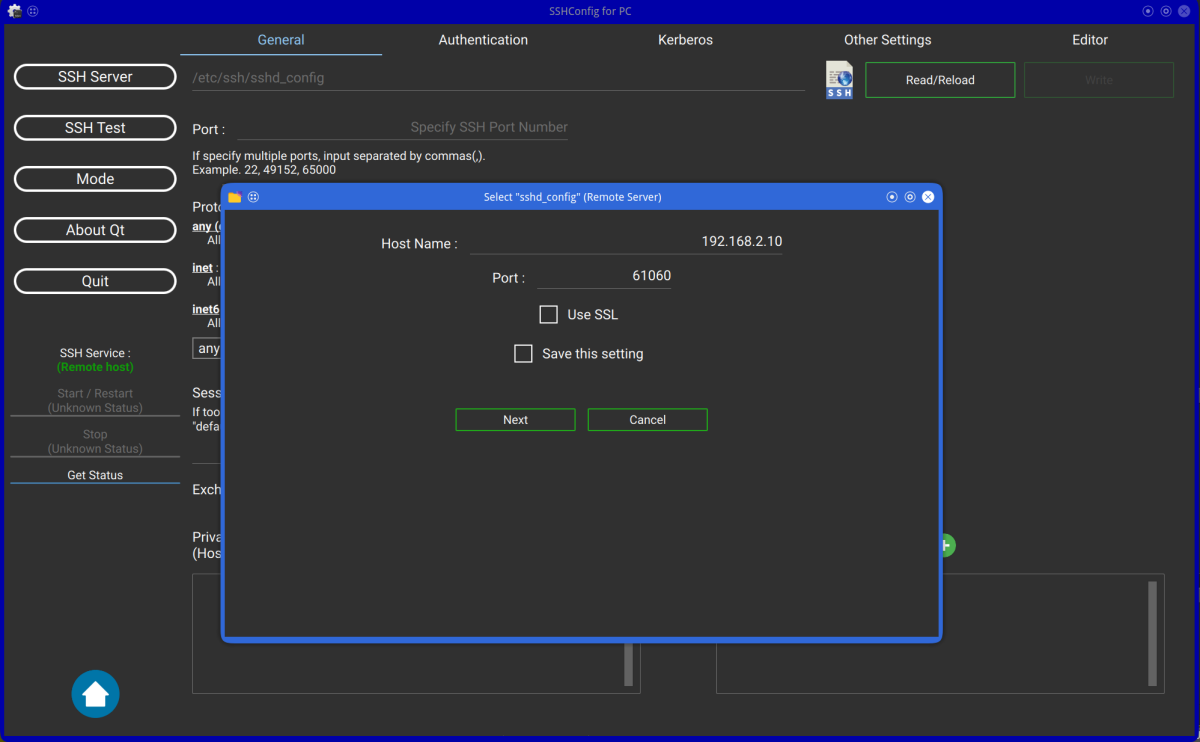
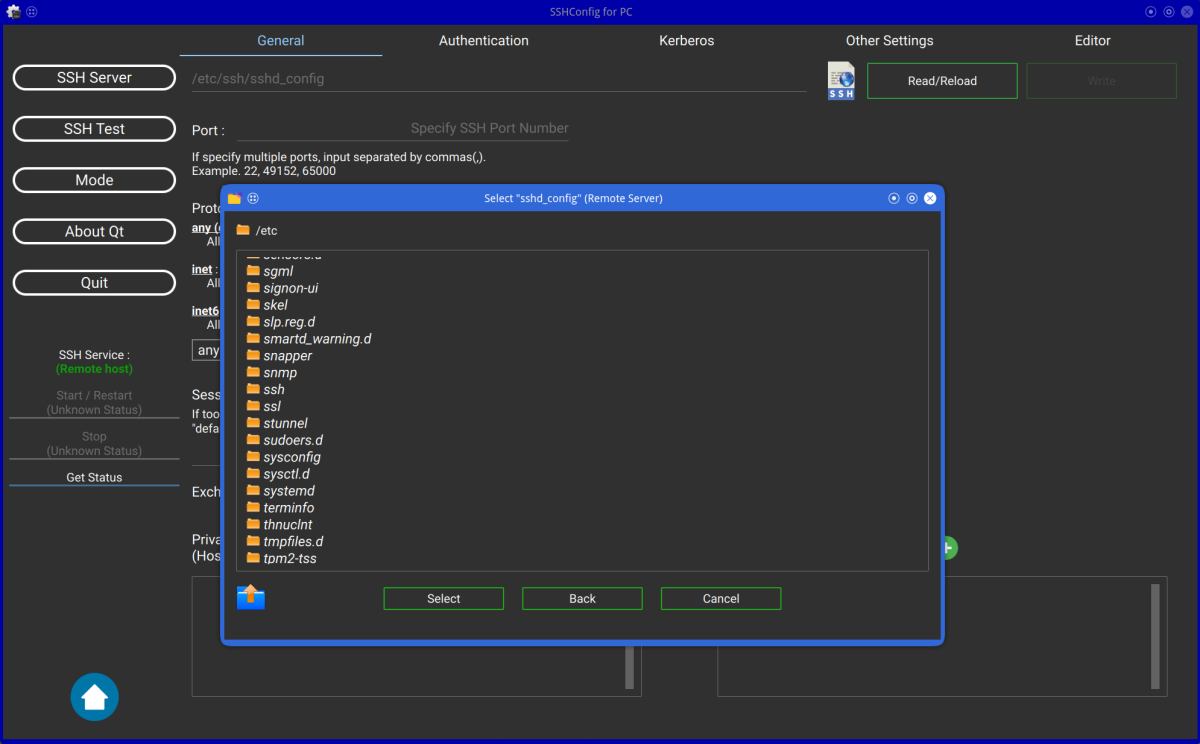
If you configure SSH on remote server, click the file icon and select the sshd_config file on remote server.
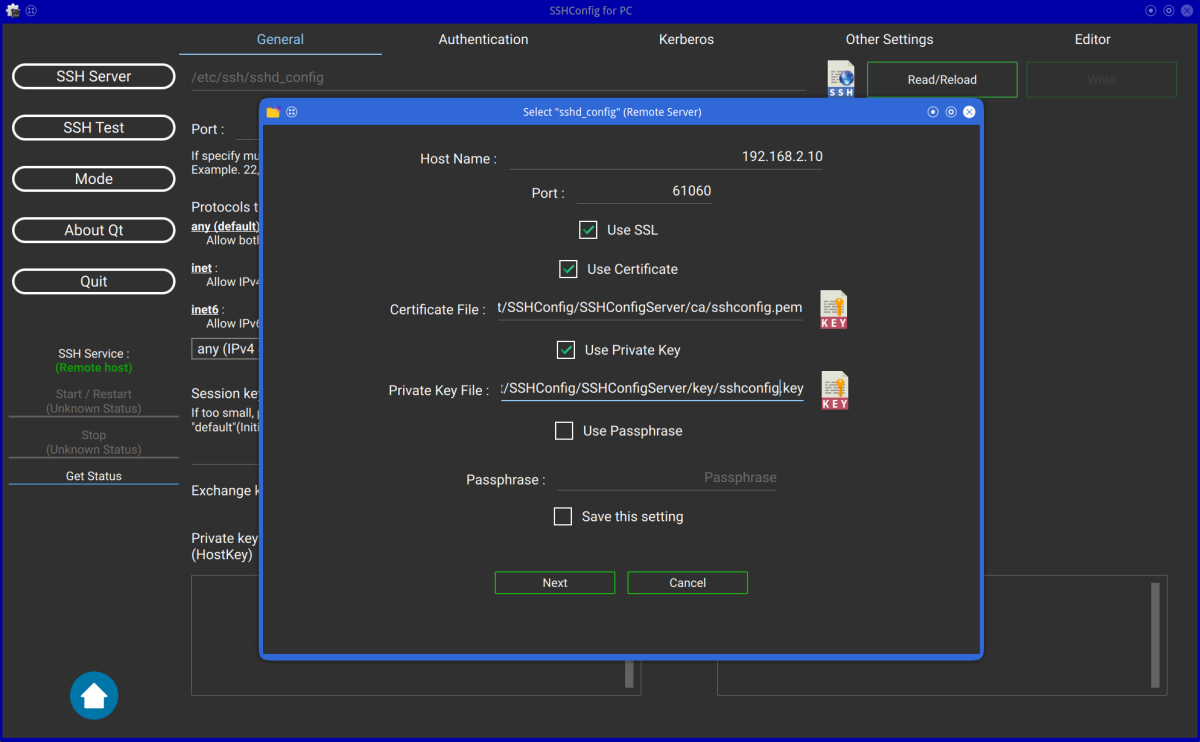
| SSHConfig Configuration(1) (Client Mode) | SSHConfig Configuration(2) with SSL/TLS (Client Mode) | SSHConfig Configuration(3) (Client Mode) |
|---|---|---|
 |
 |
 |
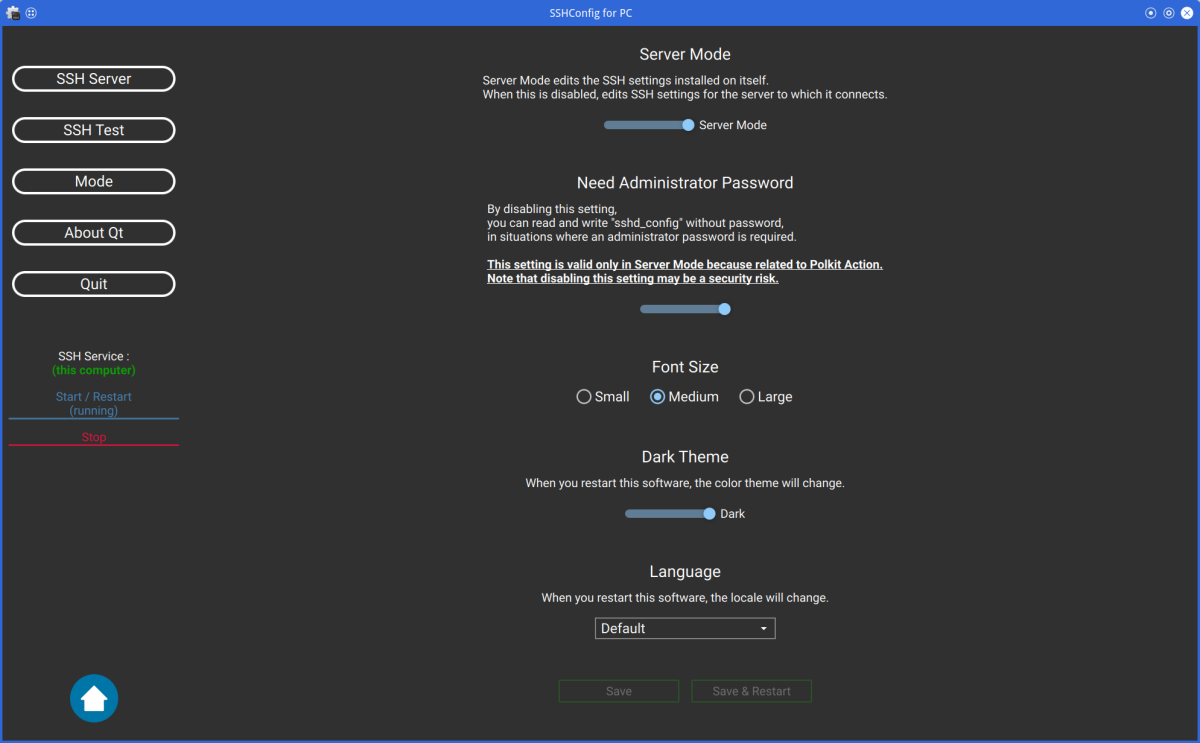
- Server Mode
When "Server Mode" is enabled, locally installed SSH can be configured.
When "Server Mode" is disabled, you can configure SSH installed on remote server.
- Need Administrator Password
When "Server Mode" is enabled, the sshd_config file can be edited without administrative privileges,
even if the file requires administrative privileges.
- Font Size
Change font size. (plus or minus 3 points)
- Dark Theme
Change to Dark Theme.
To reflect the settings, the application must be restarted.
- Language
Change the language of application.
Currently, only English and Japanese can be changed.
To reflect the settings, the application must be restarted.
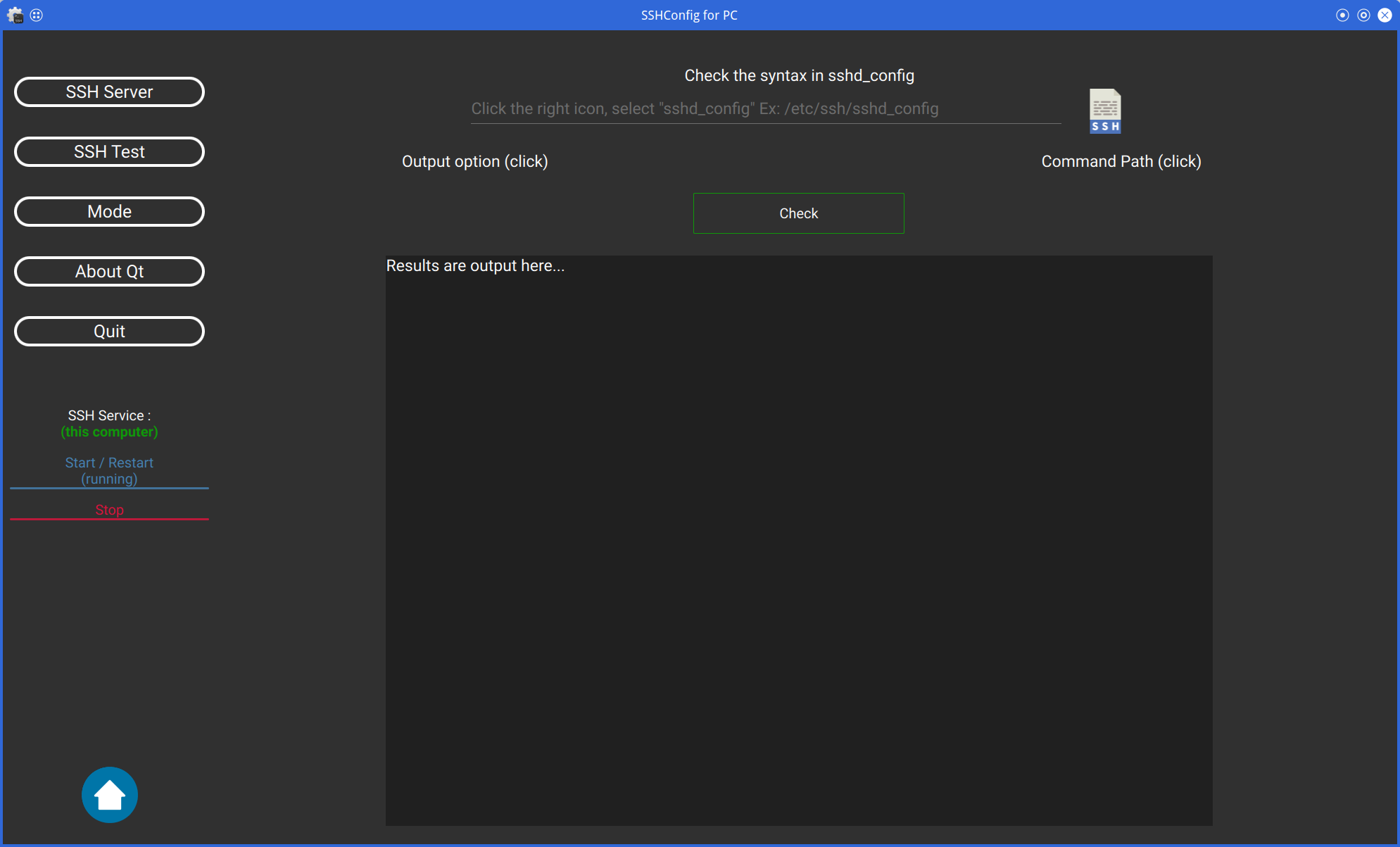
| Testing sshd_config(1) (Server Mode) | Testing sshd_config(2) (Server Mode) | Testing sshd_config(3) (Server Mode) |
|---|---|---|
 |
 |
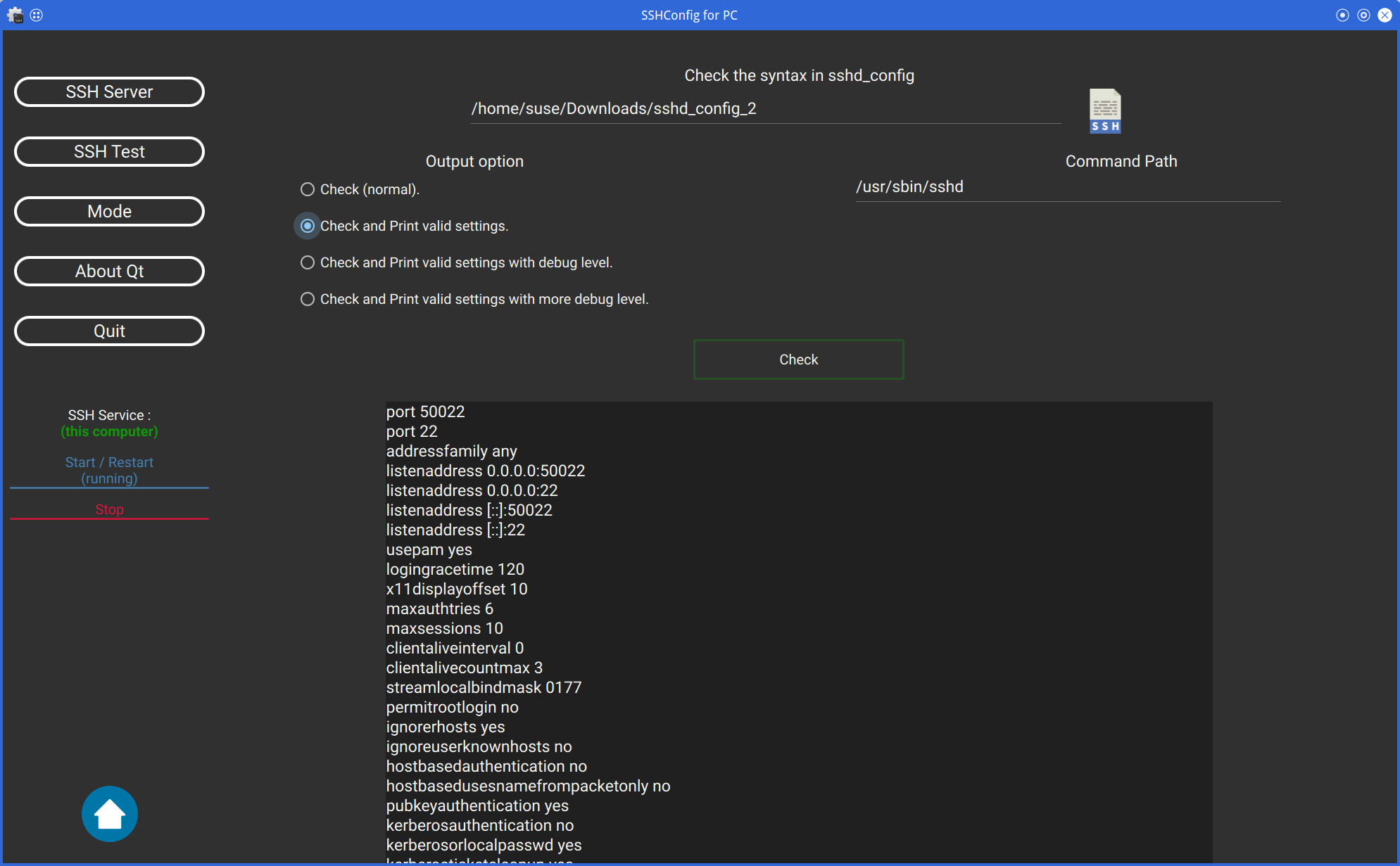 |
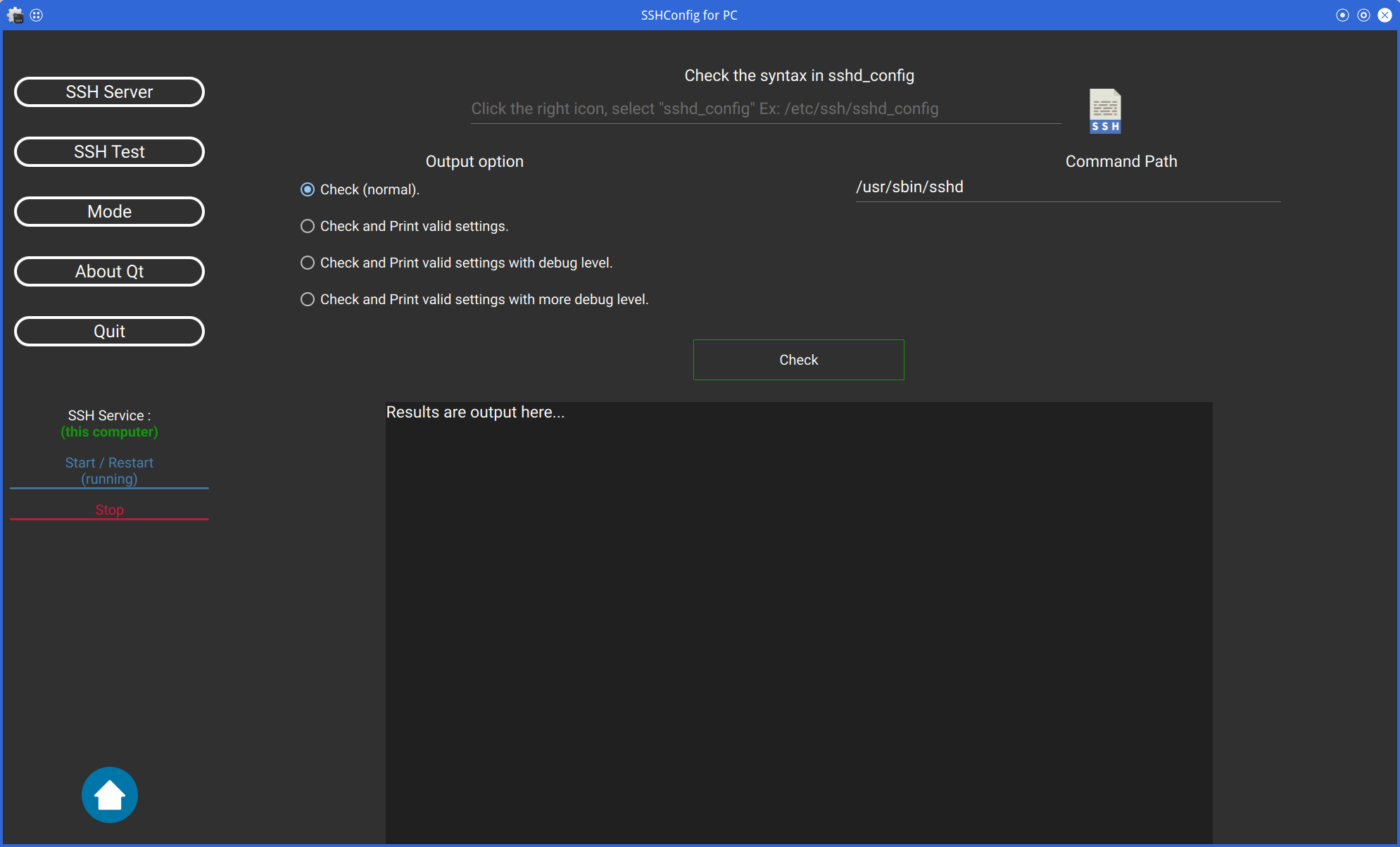
The sshd command can be used to check that the sshd_config file is written correctly.
You can also specify the options for the sshd command and the path to the sshd command.
Of course, you can also check the sshd_config file on the remote server.
Then, please disable "Server Mode".
| SSHConfig Main for PinePhone(1) | SSHConfig Main for PinePhone(2) | SSHConfig Main for PinePhone(3) |
|---|---|---|
 |
 |
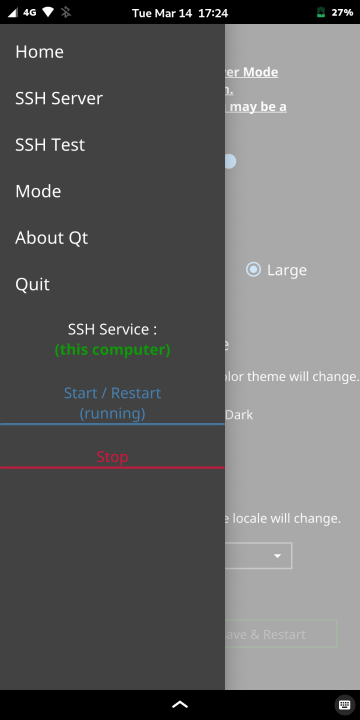 |
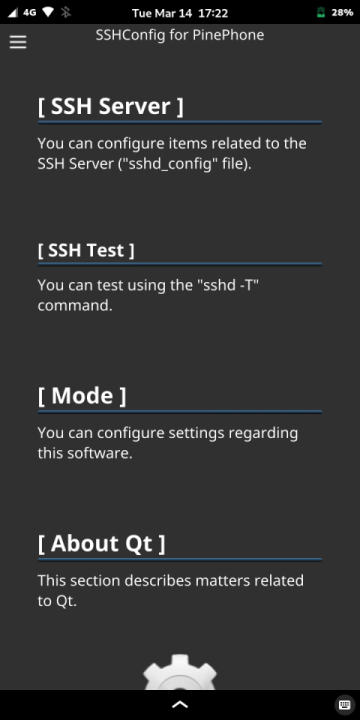
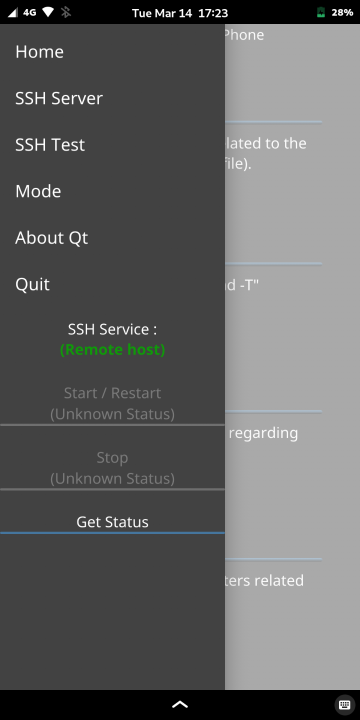
There are no buttons on the left of the main screen, and the Drawer is in the upper left corner.
Tap this Drawer or flick the PinePhone from the left edge to the right to open the menu.
Same as the PC version.
Same as the PC version.
Same as the PC version.
- Communication control with TCP and SSL/TLS is unstable at times, so the logic needs to be changed.
This is especially the case when stopping ssh(d).service with the systemd service.
- Correct minor drawing errors, etc. as soon as found.
- Allow editing of SSH client as well as SSH server.
- "AcceptEnv", "Subsystem" and "Match" keywords should be supported.