Lieutenant Keycloak IDP Controller is a Kubernetes controller that runs in a Lieutenant cluster and manages the creation of Keycloak OIDC clients for every registered cluster.
You’ll need a Kubernetes cluster to run against. You can use KIND to get a local cluster for testing, or run against a remote cluster.
Note: Your controller will automatically use the current context in your kubeconfig file (i.e. whatever cluster kubectl cluster-info shows).
- Install Instances of Custom Resources:
# install the CRDs into the cluster
kubectl apply -k https://github.com/projectsyn/lieutenant-operator//config/crd
# apply some objects to the cluster to your discretion
kubectl apply -f config/samples/- Build and push your image to the location specified by
IMG:
make docker-build docker-push IMG=<some-registry>/lieutenant-keycloak-idp-controller:tag- Deploy the controller to the cluster with the image specified by
IMG:
make deploy IMG=<some-registry>/lieutenant-keycloak-idp-controller:tagTo delete the CRDs from the cluster:
make uninstallUnDeploy the controller from the cluster:
make undeployThis project aims to follow the Kubernetes Operator pattern.
It uses Controllers, which provide a reconcile function responsible for synchronizing resources until the desired state is reached on the cluster.
- Install the CRDs into the cluster:
make install- Run your controller (this will run in the foreground, so switch to a new terminal if you want to leave it running):
make runNOTE: You can also run this in one step by running: make install run
If you are editing the API definitions, generate the manifests such as CRs or CRDs using:
make manifestsNOTE: Run make --help for more information on all potential make targets
More information can be found via the Kubebuilder Documentation
For a full E2E development setup the VSHN infrastructure has you covered.
- Create your isolated realm on the testing Keycloak https://id.test.vshn.net/auth/admin/master/console/#/master/add-realm.
- Create a user for the controller in the admin realm https://id.test.vshn.net/auth/admin/master/console/#/master/users/add-user.
Configure as follows:
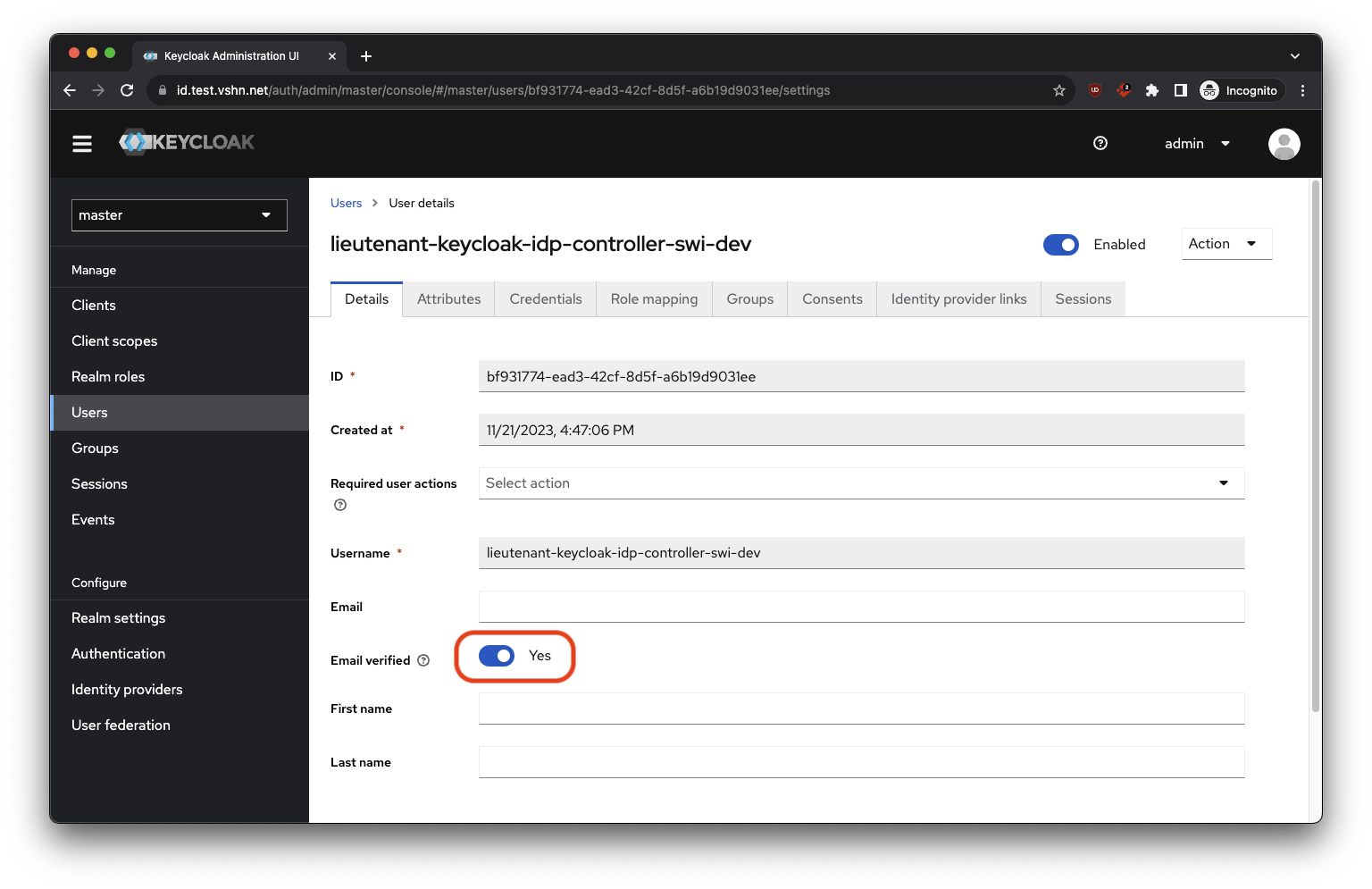
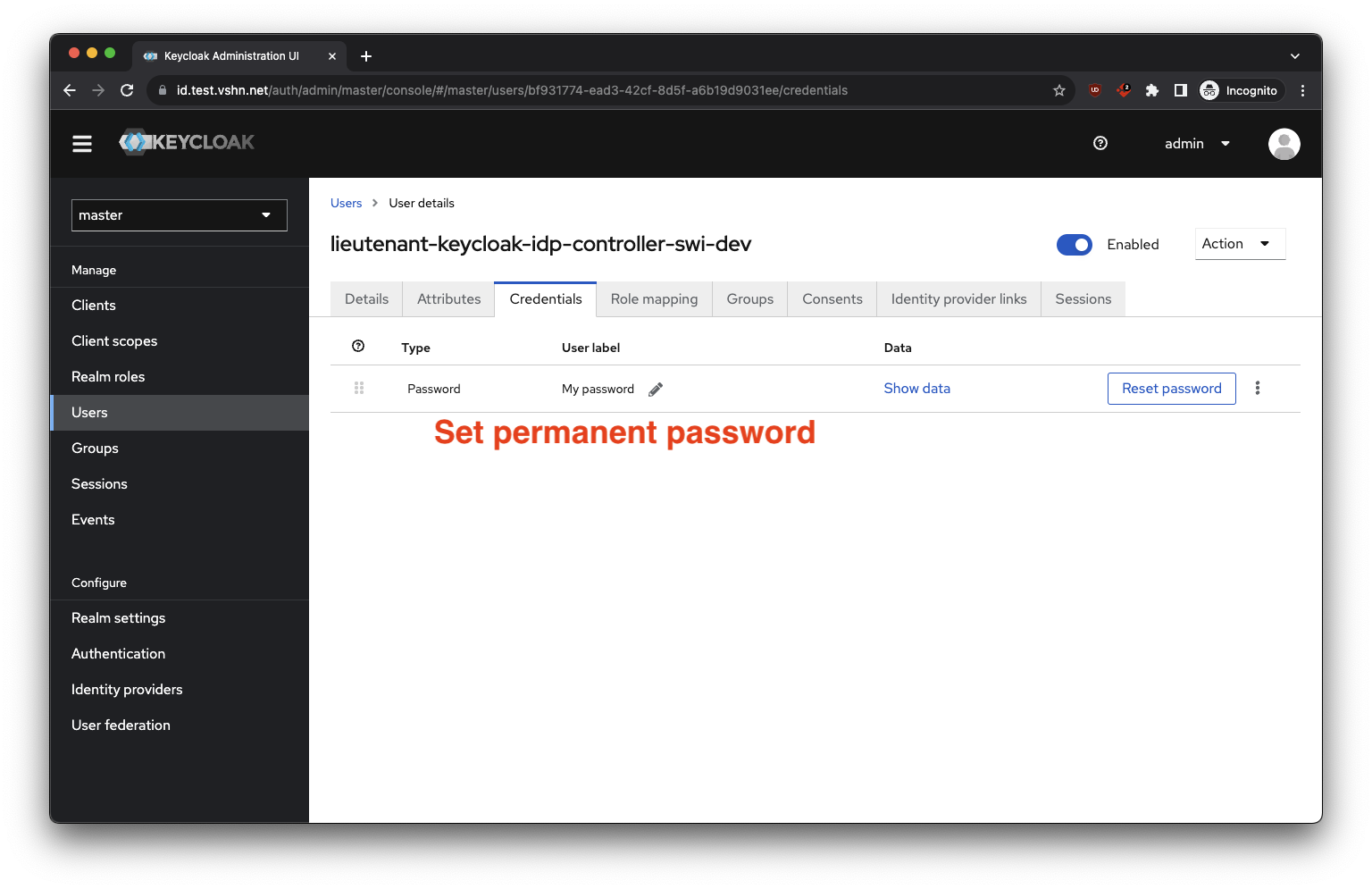
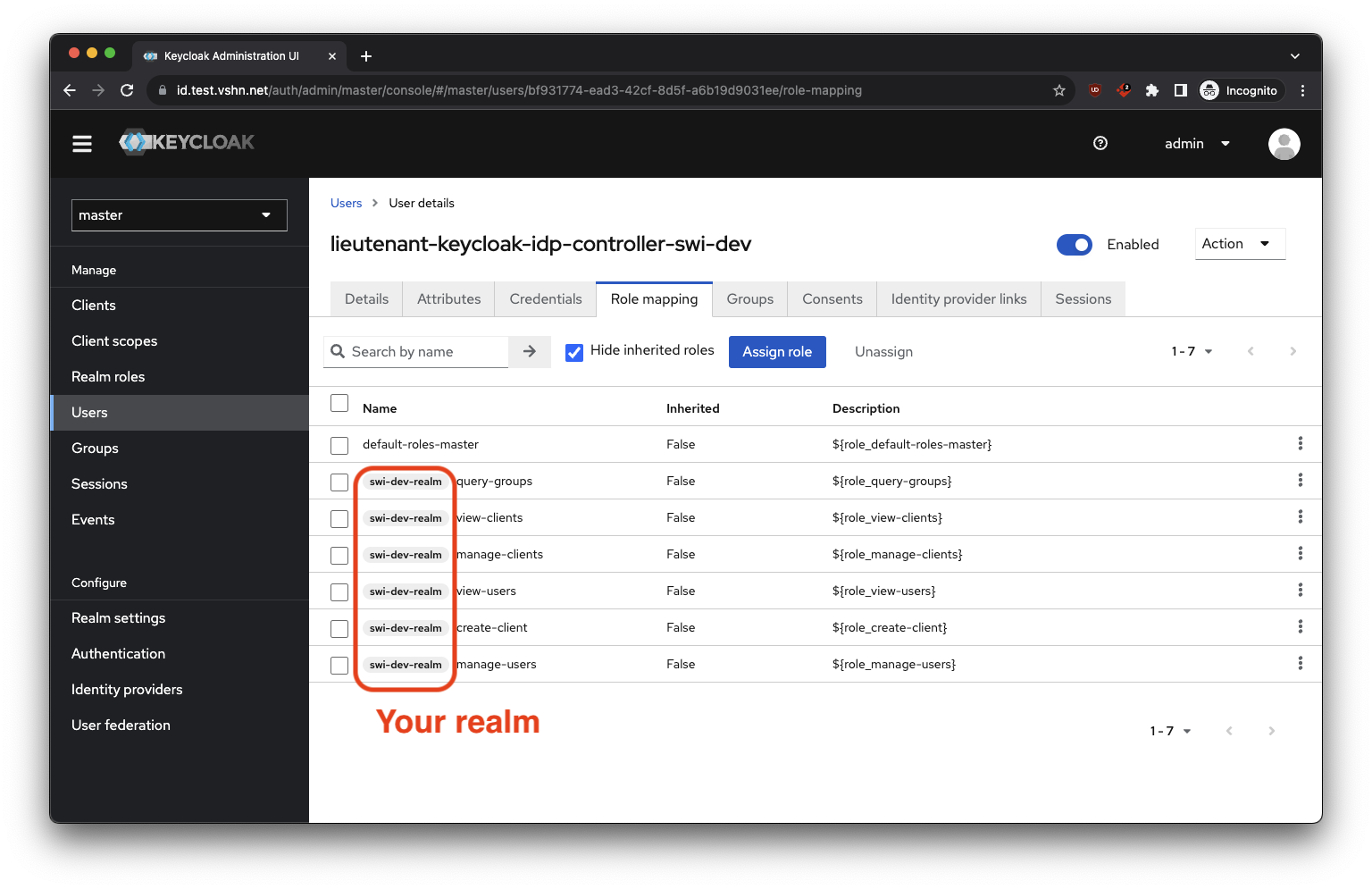
- Sign in to the
lieutenant-devcluster at https://syn-lieutenant-dev.apps.cloudscale-lpg-2.appuio.cloud/. - Run the controller with the following command:
REALM=your-realm-name
KEYCLOAK_USER=your-controller-user
KEYCLOAK_PASSWORD=your-controller-password
make RUN_ARGS="--keycloak-realm=$REALM --keycloak-base-url=https://id.test.vshn.net --keycloak-user=$KEYCLOAK_USER --keycloak-password=$KEYCLOAK_PASSWORD --keycloak-login-realm=master --keycloak-legacy-wildfly-support=true --vault-address=https://vault-dev.syn.vshn.net/ --vault-token=$(kubectl create token -n lieutenant lieutenant-keycloak-idp-controller)" run