CredX has become primarily a email generation tool and will be continued at github.com/navisecdelta/
CredCatch is a collection of tools for generating emails from Bing Dorks and scanning password dumps for emails in bulk.
After you've got yourself a list of emails generated by PasswordSpraying toolkit, or many of the email generation/gathering tools, run this tool against those emails and it will scrape dump information from WeLeaksInfo using selenium.
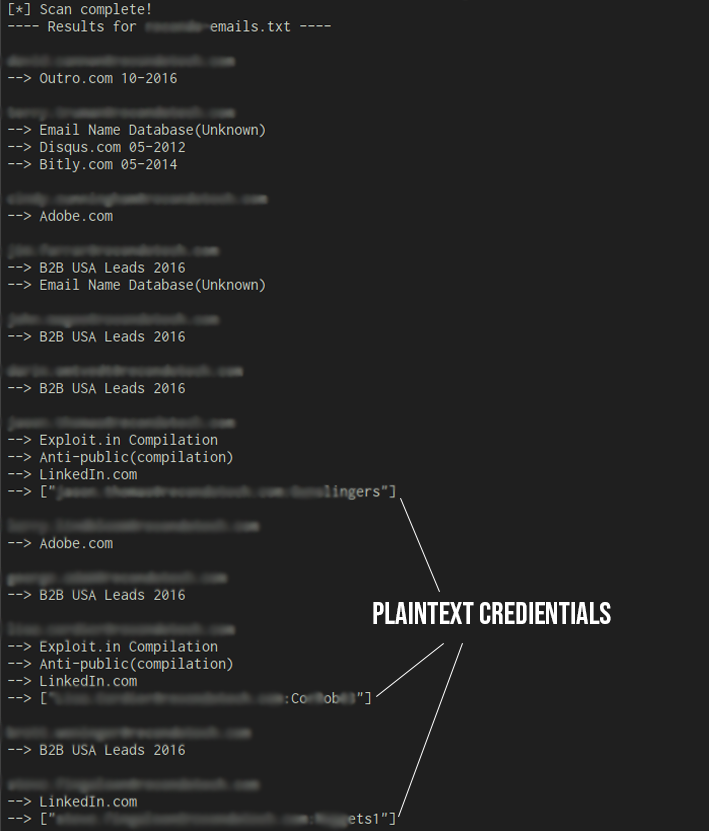
If you have a valid account, you can login and get plaintext credentials.
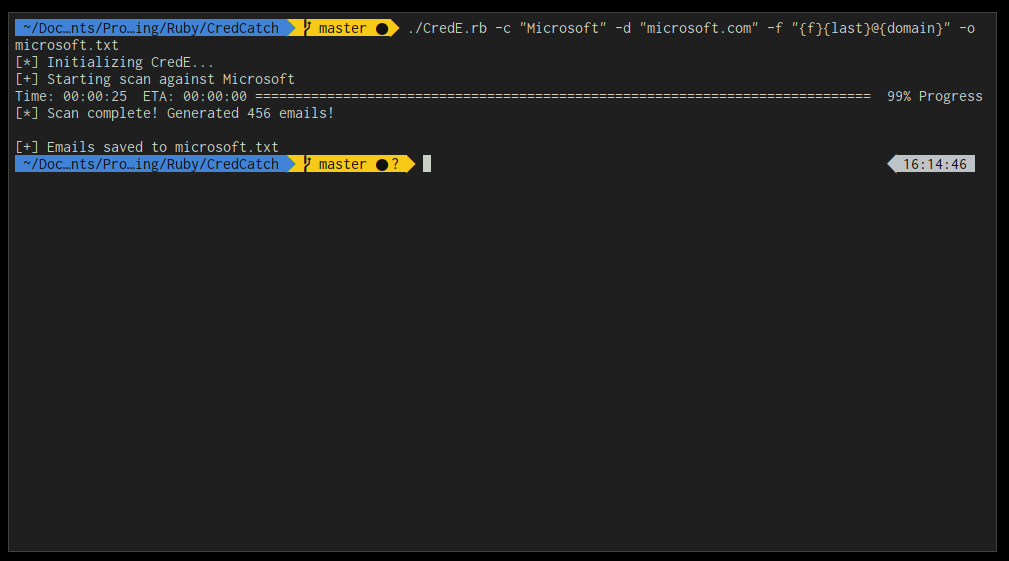
CredE is for Email generation, similar to https://github.com/byt3bl33d3r/SprayingToolkit, but fully headless, no more mitmdump, and no more clicking through 27 pages of Google, (no disrespect byt3bl33d3r :)
./CredE.rb -c "Company, Inc" -d "company.com" -f "{f}{last}@{domain}" -o company_emails.txt
Easy as that!
CredX is for searching breaches and pulling plaintext credientials. It uses selenium-webdriver, so you will need that. There are multiple ways to use CredX.
CredX can be used exclusively without using CredE, however CredE is nice if you want emails by themselves. You can also use the -o flag with CredX to save emails during a --find scan.
- Just pull breaches (Like HIBP for multiple emails) -> Pulls from WeLeaks, no plaintext credientials
- Pull breaches and then pull plaintext credientials from BreahCompilation (See Breachcompilation integration)
- Pull breaches and plaintext credientials from Weleaks (you need a paid account), this uses the session token.
- Do any of the following, except perform the email scraping/generation at the same time. (--find)
./CredX.rb --find -c "Company Name" -d "company.com" -f "{f}{last}@{domain}"
or
./CredX.rb emails.txt
(If you specify the path in the settings.json, then specifying it is not needed)
./CredX.rb --find -c "Company Name" -d "company.com" -f "{f}{last}@{domain} --breachpath /path/to/breachcompilation"
or
./CredX.rb --breachpath /path/to/breachcompilation emails.txt"
./CredX.rb -s session_token emails.txt
or
/CredX.rb -s session_token --find -c "Company Name" -d "company.com" -f "{first}.{last}@{domain}"
If you've ever used the BreachCompilation database, you'll know it has some good stuff in it. If you don't have it, you can download it with this magnet link:
magnet:?xt=urn:btih:7ffbcd8cee06aba2ce6561688cf68ce2addca0a3&dn=BreachCompilation&tr=udp%3A%2F%2Ftracker.openbittorrent.com%3A80&tr=udp%3A%2F%2Ftracker.leechers-paradise.org%3A6969&tr=udp%3A%2F%2Ftracker.coppersurfer.tk%3A6969&tr=udp%3A%2F%2Fglotorrents.pw%3A6969&tr=udp%3A%2F%2Ftracker.opentrackr.org%3A1337
Once you've got this saved, you can either specify it's path with the ./CredCatch.rb -b /path/to/breachcompilation, or cp settings.json.example settings.json, and add in your path to settings.json.