OWASP ZAP Image For OpenShift
Overview
The public docker registry version of OWASP's Zed Attack Proxy (ZAP) is not compatible with OpenShift without using privleged containers. This Docker image resolves that issue.
Running
The semantics of running this are identical to the public OWASP ZAP docker image, so look at the Wiki page HERE.
Deploying In OpenShift
oc new-build -l 'role=jenkins-slave' https://github.com/puzzle/owasp-zap-openshift.gitConfiguring In OpenShift Jenkins
- Log in to Jenkins with an account which has permissions to manage the Jenkins instance
- Install the following plugins:
- HTML Publisher Plugin
- Restart Jenkins
- Log back in to Jenkins and navigate to
Manage Jenkins -> Configure System - Scroll down to the
Kubernetescloud configuration - Add a new "Pod Template" as shown below:
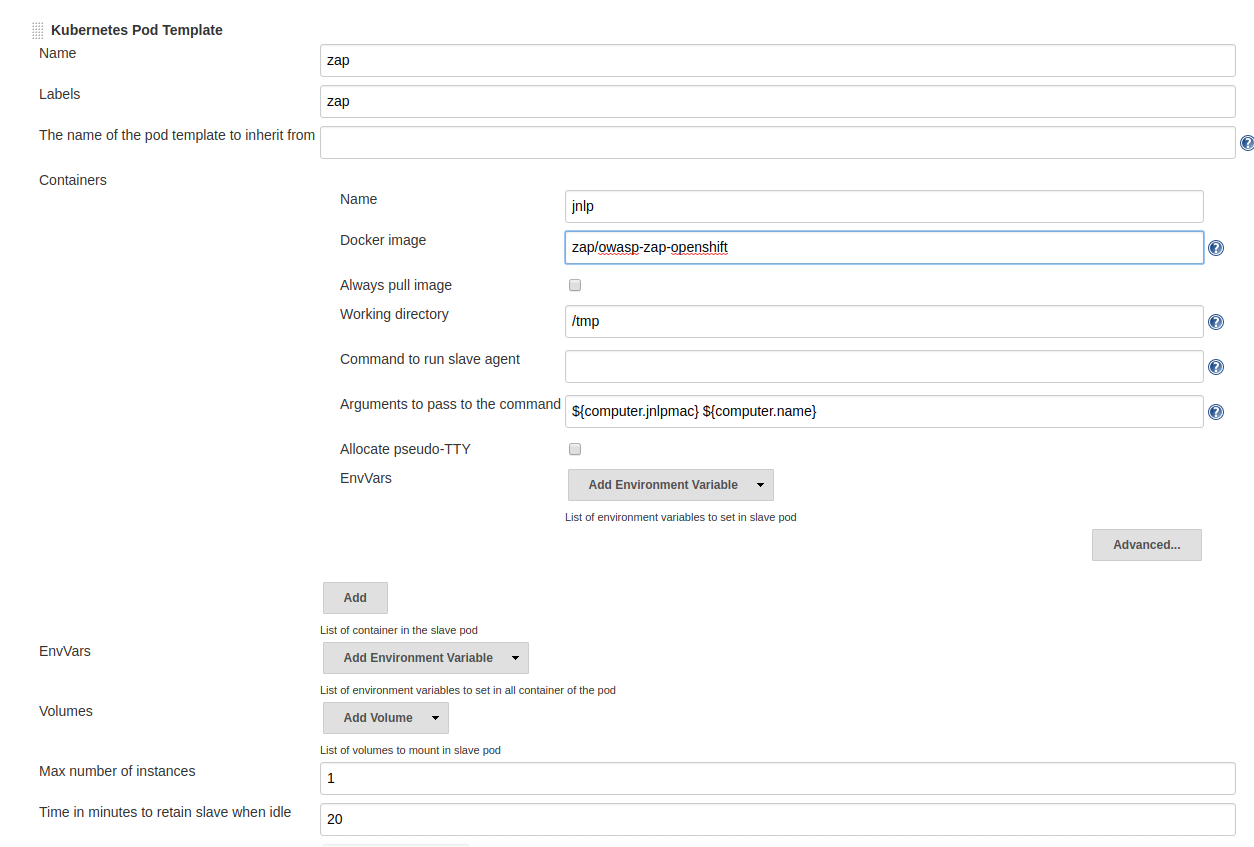
Using it in your Jenkinsfile
stage('Get a ZAP Pod') {
node('zap') {
stage('Scan Web Application') {
dir('/zap') {
def retVal = sh returnStatus: true, script: '/zap/zap-baseline.py -r baseline.html -t http://<some-web-site>'
echo "Return value is: ${retVal}"
echo "copy and archive report"
sh script: "cp /zap/wrk/baseline.html ."
archiveArtifacts baseline.html
}
}
}
}Baseline Scan with user
When loading a context file which defines project specific user and authentication mechanism the following command executes a baseline scan logging into the application with the defined users
def retVal = sh returnStatus: true, script: '/zap/zap-baseline.py -r baseline.html -t http://<some-web-site> -n <contextfile>'
Full Scan with user
When loading a context file which defines project specific user and authentication mechanism the following command executes a full scan logging into the application with the defined users and processes a active scan
def retVal = sh returnStatus: true, script: '/zap/zap-full-scan.py -r fullscan.html -t http://<some-web-site> -n <contextfile>'