This lab builds on the great work from my colleague Raki Rahman 🏆
TLDR: Start the lab! 🚀
After completing this lab you will:
- Deploy the current Azure Confidential Computing capabilities
- Learn about some common Confidential Computing use cases
- Learn how to deploy and configure Azure Confidential Computing resources
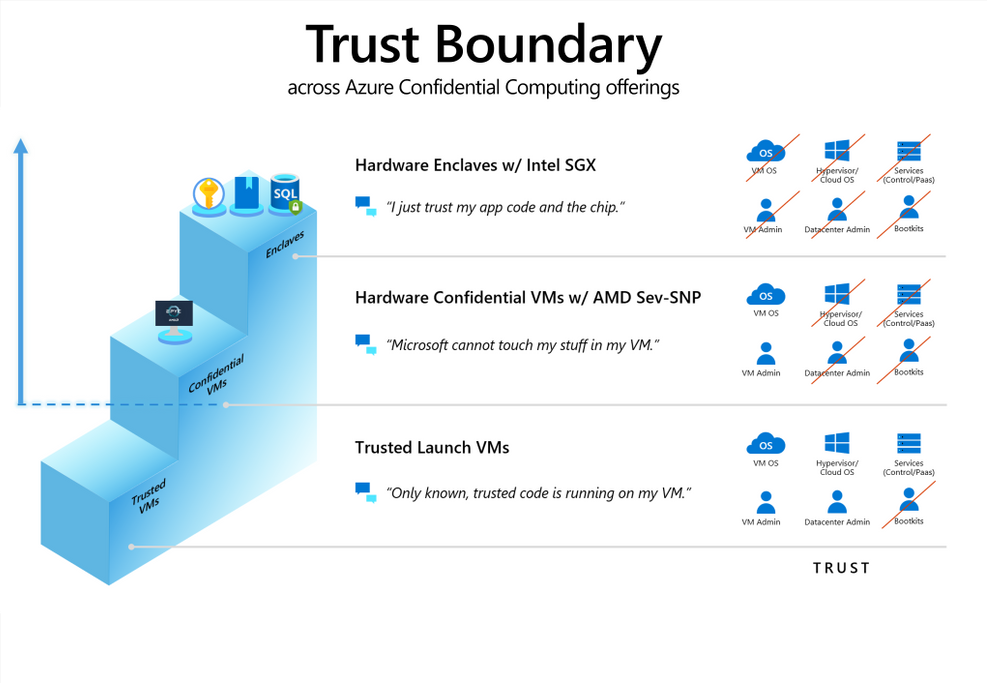
- Learn about the 2 Confidential Computing models (AMD SEV-SNP v Intel SGX)
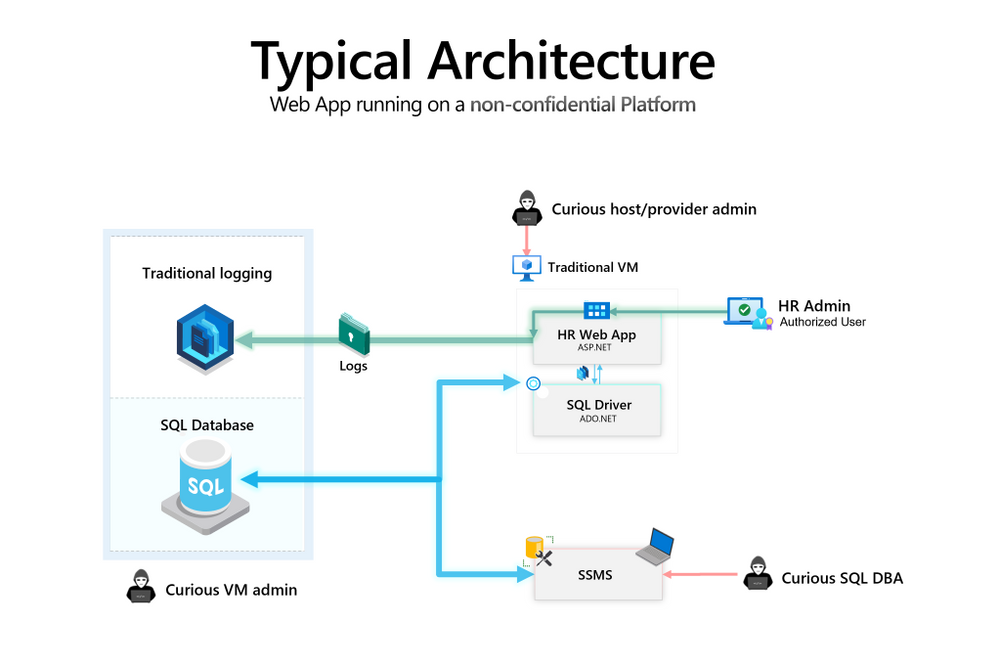
Contoso's Electric Scooter 🛴 business has been growing fast and they need to to keep track of the payroll and benefits for all the new people joining the company. After a few days, the development team have an initial architecture for the new Contoso HR (Human Resources)application:
Following an architecture review, the Contoso Security and Compliance team have identified ways malicious actors could compromise sensitive PII (Personally Identifiable Information) data for example:
- A Curious SQL DBA with db_owner can access sensitive tables, as well as leverage SQL Server Extended Events Sessions to intercept query inputs.
- A Curious VM admin with access to application logs can read / manipulate sensitive application logs (e.g. erase a subset of the history).
- A Curious host / provider admin with access to the underlying Hypervisor can access the VM including application binaries and in-memory data.
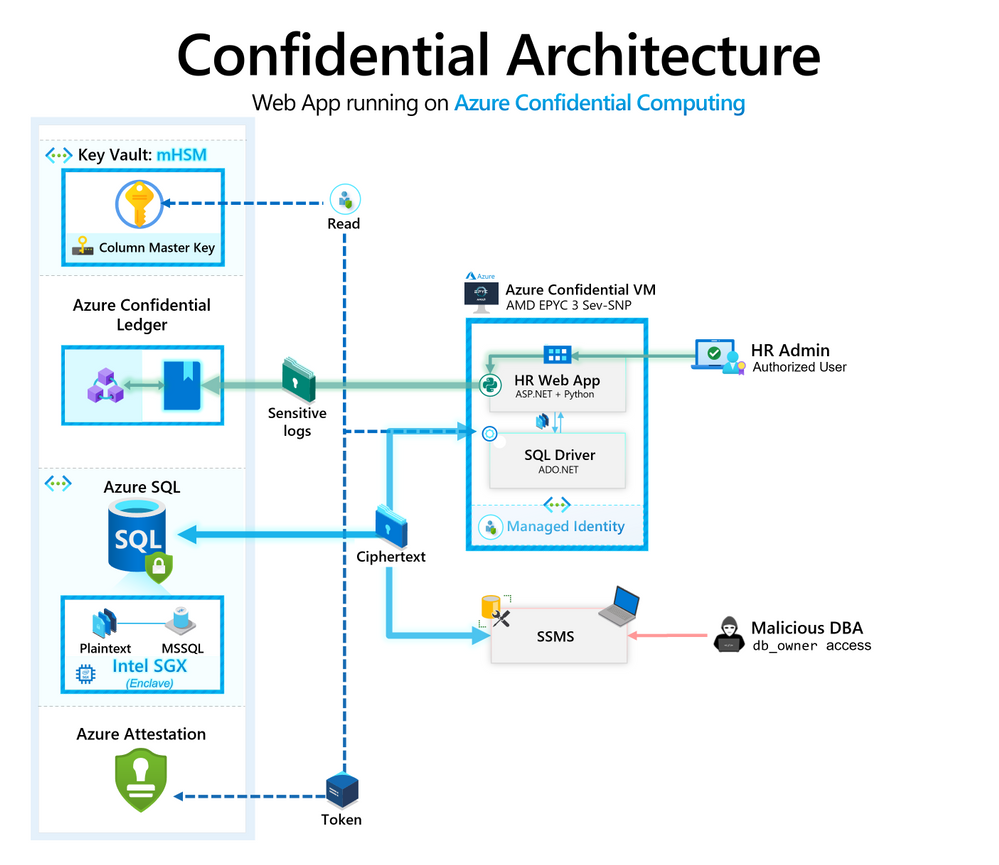
Because Contoso already use Azure, the team have updated the app architecture to use Azure Confidential Computing capabilities to secure their sensitive information:
The app architecture now implements these Azure capabilities:
| Service | Feature | Benefit |
|---|---|---|
| Azure SQL DB | Always Encrypted with secure enclaves | Host a confidential database with sensitive columns encrypted using a CMK (Column Master Key) |
| Azure Key Vault | Managed HSM (Hardware Security Module)(Public preview) | Store the Always Encrypted CMK for the sensitive Azure SQL database |
| Azure Confidential VM | AMD SEV-SNP (Secure Encrypted Virtualisation - Secure Nested Paging) | Host a web app that queries the sensitive database, and persists sensitive logs (database query history) |
| Azure Confidential Ledger | N/A | Append-only, immutable ledger to store sensitive application logs |
Applying these capabilities the HR application can securely process and store sensitive data by reducing the level of trust required:
Now that we have a plan let's start the lab! 🚀