NGINX Agent is a companion daemon for your NGINX Open Source or NGINX Plus instance. It enables:
- Remote management of NGINX configurations
- Collection and reporting of real-time NGINX performance and operating system metrics
- Notifications of NGINX events
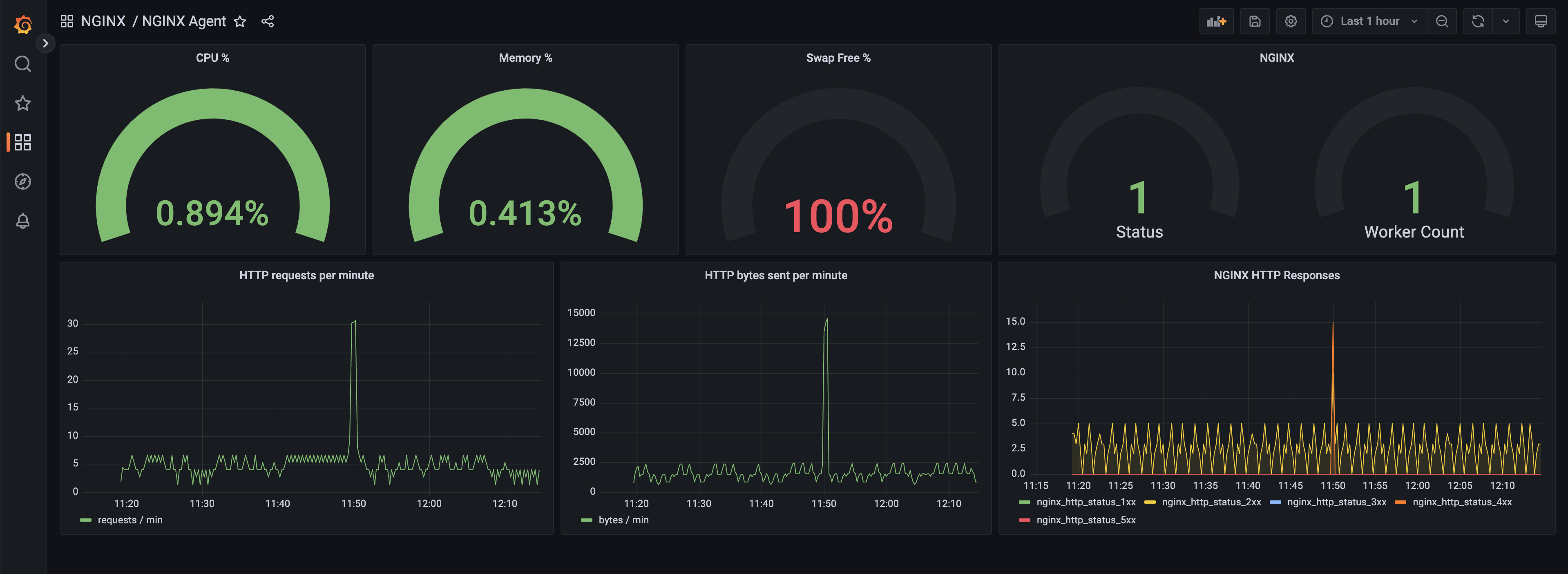 Grafana dashboard showing metrics reported by NGINX Agent
Grafana dashboard showing metrics reported by NGINX Agent
- How it Works
- Installation
- Getting Started with NGINX Agent
- Development Environment Setup
- NGINX Agent Technical Specifications
- Community
- Contributing
- Change Log
- License
NGINX Agent runs as a companion process on a system running NGINX. It provides gRPC and REST interfaces for configuration management and metrics collection from the NGINX process and operating system. NGINX Agent enables remote interaction with NGINX using common Linux tools and unlocks the ability to build sophisticated monitoring and control systems that can manage large collections of NGINX instances.
NGINX Agent provides an API interface for submission of updated configuration files. Upon receipt of a new file, it checks the output of nginx -V to determine the location of existing configurations. It then validates the new configuration with nginx -t before applying it via a NOHUP signal to the NGINX master process.
NGINX Agent interfaces with NGINX process information and parses NGINX logs to calculate and report metrics. When interfacing with NGINX Plus, NGINX Agent pulls relevant information from the NGINX Plus API. Reported metrics may be aggregated by Prometheus and visualized with tools like Grafana.
When running alongside an open source instance of NGINX, NGINX Agent requires that NGINX Access and Error logs are turned on and contain all default variables.
For NGINX Agent to work properly with an NGINX Plus instance, the API needs to be configured in that instance's nginx.conf. See Instance Metrics Overview for more details. Once NGINX Plus is configured with the /api/ endpoint, NGINX Agent will automatically use it on startup.
NGINX Agent allows a gRPC connected control system to register a listener for a specific event. The control mechanism is then invoked when NGINX Agent sends an associated system signal. The source of a notification can be either the NGINX instance or NGINX Agent itself. Here's a list of currently supported events:
| Event | Description |
|---|---|
| AGENT_START_MESSAGE | NGINX Agent process started |
| AGENT_STOP_MESSAGE | NGINX Agent process stopped |
| NGINX_FOUND_MESSAGE | NGINX master process detected on system |
| NGINX_STOP_MESSAGE | NGINX master process stopped |
| NGINX_RELOAD_SUCCESS_MESSAGE | NGINX master process reloaded successfully |
| NGINX_RELOAD_FAILED_MESSAGE | NGINX master process failed to reload |
| NGINX_WORKER_START_MESSAGE | New NGINX worker process started |
| NGINX_WORKER_STOP_MESSAGE | NGINX worker process stopped |
| CONFIG_APPLY_SUCCESS_MESSAGE | Successfully applied new NGINX configuration |
| CONFIG_APPLY_FAILURE_MESSAGE | Failed to apply new NGINX configuration |
| CONFIG_ROLLBACK_SUCCESS_MESSAGE | Successfully rolled back NGINX configuration |
| CONFIG_ROLLBACK_FAILURE_MESSAGE | Failed to roll back NGINX configuration |
NGINX Agent interfaces directly with an NGINX server process installed on the same system. If you don't have it already, follow these steps to install NGINX Open Source or NGINX Plus. Once installed, ensure the NGINX instance is running.
NGINX Agent is written in Go and requires Go 1.19 or higher to be installed. You can download Go from the official website.
To install NGINX Agent on your system, go to Releases and download nginx-agent.tar.gz. Create a new subdirectory and extract the archive into it. Change into the subdirectory matching the package manager format appropriate for your operating system distribution.
Depending on OS distribution and CPU architecture type, use your system's package manager to install the package. Some examples:
Debian, Ubuntu, and other distributions using the dpkg package manager.
sudo dpkg -i nginx-agent-<agent-version>.deb
RHEL, CentOS RHEL, Amazon Linux, Oracle Linux, and other distributions using the yum package manager
sudo yum localinstall nginx-agent-<agent-version>.rpm
RHEL and other distributions using the rpm package manager
sudo rpm -i nginx-agent-<agent-version>.rpm
Alpine Linux
sudo apk add nginx-agent-<agent-version>.apk
FreeBSD
sudo pkg add nginx-agent-<agent-version>
To start the NGINX Agent on systemd systems, run the following command:
sudo systemctl start nginx-agent
To enable the NGINX Agent to start on boot, run the following command:
sudo systemctl enable nginx-agent
NGINX Agent uses formatted log files to collect metrics. Expanding log formats and instance counts will also increase the size of NGINX Agent log files. We recommend adding a separate partition for /var/log/nginx-agent. Without log rotation or storage on a separate partition, log files could use up all the free drive space and cause your system to become unresponsive to certain services.
Follow these steps to configure and run NGINX Agent and a mock interface ("control plane") to which the NGINX Agent will report.
Follow steps in the Installation section to download, install, and run NGINX and NGINX Agent.
Using your preferred method, clone the NGINX Agent repository into your development directory. See Cloning a GitHub Repository for additional help.
Start the mock control plane by running the following command from the agent source code root directory:
go run sdk/examples/server.go
# Command Output
INFO[0000] http listening at 54790 # mock control plane port
INFO[0000] gRPC listening at 54789 # gRPC control plane port which NGINX Agent will report to
If it doesn't already exist, create the /etc/nginx-agent/ directory and copy the nginx-agent.conf file into it from the project root directory.
sudo mkdir /etc/nginx-agent
sudo cp <project_root_directory>/nginx-agent.conf /etc/nginx-agent/
Create the agent-dynamic.conf file in the /etc/nginx-agent/ directory, which is required for NGINX Agent to run.
sudo touch /etc/nginx-agent/agent-dynamic.conf
Add the the following settings to /etc/nginx-agent/nginx-agent.conf:
server:
host: 127.0.0.1 # mock control plane host
grpcPort: 54789 # mock control plane gRPC port
# gRPC TLS options - DISABLING TLS IS NOT RECOMMENDED FOR PRODUCTION
tls:
enable: false
skip_verify: trueThe NGINX Agent REST interface can be exposed by validating the following lines in the /etc/nginx-agent/nginx-agent.conf file are present:
api:
port: 8081 # port to expose REST API
# REST TLS parameters
cert: "<TLS-CERTIFICATE>.crt"
key: "<PRIVATE-KEY>.key"The mock control plane can use either gRPC or REST protocols to communicate with NGINX Agent.
If already running, restart NGINX Agent to apply the new configuration. Alternatively, if NGINX Agent is not running, you may run it from the source code root directory.
Open another terminal window and start the NGINX Agent. Issue the following command from the agent source code root directory.
sudo make run
# Command Output snippet
WARN[0000] Log level is info
INFO[0000] setting displayName to XXX
INFO[0000] NGINX Agent at with pid 12345, clientID=XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX name=XXX
INFO[0000] NginxBinary initializing
INFO[0000] Commander initializing
INFO[0000] Comms initializing
INFO[0000] OneTimeRegistration initializing
INFO[0000] Registering XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX
INFO[0000] Metrics initializing
INFO[0000] MetricsThrottle initializing
INFO[0000] DataPlaneStatus initializing
INFO[0000] MetricsThrottle waiting for report ready
INFO[0000] Metrics waiting for handshake to be completed
INFO[0000] ProcessWatcher initializing
INFO[0000] Extensions initializing
INFO[0000] FileWatcher initializing
INFO[0000] FileWatchThrottle initializing
INFO[0001] Events initializing
INFO[0001] OneTimeRegistration completed
Open a web browser to view the mock control plane at http://localhost:54790. The following links will be shown in the web interface:
- registered - shows registration information of the dataplane
- nginxes - lists the NGINX instances on the dataplane
- configs - shows the protobuf payload for NGINX configuration sent to the management plane
- configs/chunked - shows the split up payloads sent to the management plane
- configs/raw - shows the actual configuration as it would live on the dataplane
- metrics - shows a buffer of metrics sent to the management plane (similar to what will be sent back in the REST API)
For more NGINX Agent use-cases, refer to https://github.com/nginx/agent/tree/main/sdk/examples
While most Linux or FreeBSD operating systems can be used to contribute to the NGINX Agent project, the following steps have been designed for Ubuntu. Ubuntu is packaged with most libraries required to build and run NGINX Agent, and is the recommended platform for NGINX Agent development.
Follow steps in the Installation section to download and install NGINX. Once installed ensure NGINX instance is running.
Follow steps in the Getting Started with NGINX Agent section to clone the NGINX Agent Repository
Depending on the operating system distribution, it may be necessary to install the following packages in order to build NGINX Agent.
Change to the NGINX Agent source directory:
cd <path_to_development_directory>/agent
Install Make:
sudo apt install make
NGINX Agent is written in Go. You may download Go and follow installation instructions on the same page or run:
sudo apt install golang-go
Run the following commands to build and run NGINX Agent:
make build
sudo make run
NGINX Agent can run in most environments. For a list of supported distributions, see the NGINX Technical Specs guide.
NGINX Agent can be deployed in the following environments:
- Bare Metal
- Container
- Public Cloud: AWS, Google Cloud Platform, and Microsoft Azure
- Virtual Machine
NGINX Agent works with all supported versions of NGINX Open Source and NGINX Plus.
Minimum system sizing recommendations for NGINX Agent:
| CPU | Memory | Network | Storage |
|---|---|---|---|
| 1 CPU core | 1 GB RAM | 1 GbE NIC | 20 GB |
-
Our Slack channel #nginx-agent, is the go-to place to start asking questions and sharing your thoughts.
-
Our GitHub issues page offers space for a more technical discussion at your own pace.
Get involved with the project by contributing! Please see our contributing guide for details.
See our changelog to keep track of updates.

