Client-Side Encryption: The Key to Confidentiality for Cloud Storage
This project aims to demonstrate how businesses can maintain data privacy controls for data in the Cloud through self-managed encryption keys . Our open-source Crypto-Middleware package is based on the Web Cryptography API, designed for web applications who require encrypting files on your device before transmission.
The end result is End-to-End encryption for your sensitive data.
- Maintain Confidentiality, Integrity & Authenticity
- Large File Encryption & Decryption
- High Entropy
- Browser only, no server side encryption.
- Large file encryption & decryption without exhausting memory > 5GB
- Optional Public Key Encryption to share your secret keys
Cloud breaches have exposed millions of plaintext data across industries, with inherent risks in relying on cloud infrastructure for data security. SecureFile demonstrates this by using our opensource browser middleware acting as a secure proxy to read, encrypting and save data before it leaves the client's environment, ensuring cloud providers only handle encrypted data without access to decryption keys.
Install the middleware only DOCS :
https://securesend.gitbook.io/crypto-middleware-npm-package
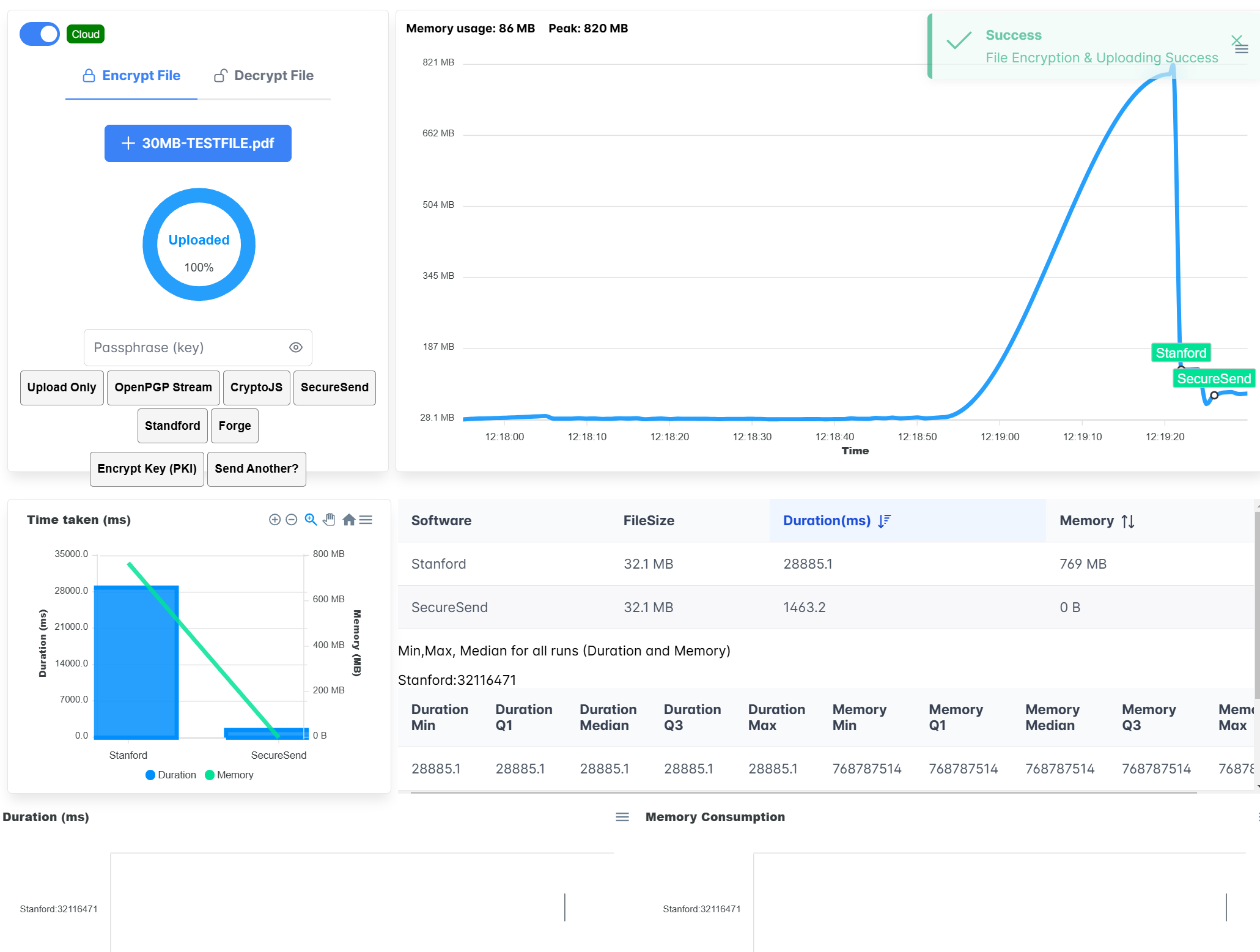
Demo application with performance benchmark suite
| Title | Location | Description | Usage |
|---|---|---|---|
| Crypto-Middleware | ./crypto-middleware | Middleware proxies your File object in a stream and outputs a encrypted Readable stream. | npm i crypto-middleware |
| SecureFile | ./demo | Client side application demonstrating ways in which Crypto-middleware can be sued with comparison and monitoring included. | cd demonpm installnpm run dev |
| Crypto-CLI | ./crypto-cli | NodeJS terminal proof of concept wrapper around openssl. | node index |
- Browser that supports Streams API (Chrome 89+, Edge 89+, FireFox 102+, Opera 76+, sorry Safari) https://caniuse.com/?search=streams
- NodeJS Version 16.00 or above for building 'SecureFile' for demonstration
- Thats it!
git clone https://github.com/hkuspace-pu/Secure-File-RishiUttam-COMP3000HK.git
cd Secure-File-RishiUttam-COMP3000HK
npm install
npm run dev
Our tool compares some popular cryptographic js implementation libraries such as:
- OpenPGP (https://github.com/openpgpjs/openpgpjs)
- CryptoJS (https://github.com/brix/crypto-js)
- Stanford University (https://crypto.stanford.edu/sjcl/)
- ForgeJS (https://github.com/digitalbazaar/forge)
- SecureSend (Our demo, this page!)
If you would like to use the cloud to upload your encrypted files, set your AWS keys within the .env file located in the project root
```properties
VITE_APP_accessKeyId=<Your Access Key ID>
VITE_APP_MY_secretAccessKey=<Your secret access Key>
VITE_APP_S3REGION=<Your S3 Region>
VITE_APP_S3REGION=<Your S3 Bucket>
```
Currently we support only AWS S3 keys, as a proof of concept, practically we can support any provider with API/SDK access.
{% hint style="info" %}
Your keys are stored within the .env file and when required are used in memory only, they are not stored, coped or transmitted anywhere else. Make sure you set a secure bucket policy and do not use your root access keys. If you do not want to use the Cloud to upload your files, you can toggle to use local disk.
.png) {% endhint %}
{% endhint %}
.png)