The new Qualys Agent Checker open-source tool helps security teams and VMware admins work together to ensure the security and compliance of VMware environments. Agent Checker provides a common understanding of the instrumentation of VMware virtual machines by reporting Cloud Agent deployment status for all VMware vCenter-managed virtual machines. Security and admin teams can then identify gaps and ensure that Cloud Agent is installed and running on all VMware virtual machines, so that Qualys Cloud Platform can secure the entire environment.
Agent-Status-Checker maintains multiple Ansible roles and modules that can be deployed to easily configure and manage various parts of the vmwarew and Linux infrastructure. Ansible roles & modules provide a method of modularizing your Ansible code, in other words; it enables you to break up large playbooks into smaller reusable files. This enables you to have a separate role for each component of the infrustructure, and allows you to reuse and share roles with other users. For more information about roles, see Creating Reusable Playbooks in the Ansible Documentation. Module and Roles included bunch of python codes, govc scripts, which help to generate dynamic inventory from vcenter and then getting agent status of all nodes and provided the except report.
get.vm-inventory- login to vCenter from via goVC and generate the VM inventory in csv or excel fromat.get.vm-status- login to vCenter from via goVC and generate the VM inventory with VM status, Running or poweroff.get.agent-installed- login to hosts with dynamic inventory and generare report where agent installed or where not.get.agent-status- login to hosts with dynamic inventory and generare report where agent is running where not.get.agent-status-reporting- login to hosts with dynamic inventory and generare report in excel format with multiple tabs where you can see VM Status, Agent installed and version, running status.
Agent Checker executes and retrieves data only for SSH-enabled VMs. SSH is typically enabled by default on Linux VMs but may not be enabled on Windows and other VMs. Cloud Agent status will be reported as Not Installed for VMs where SSH is not installed, regardless of actual Cloud Agent status.
-
For Linux:
- Package Manager should be working
-
For Mac:
-
For Windows: (In progress)
- Cygwin should be installed with following packages.
Cygwin dowload
- ansible >= 2.8.4 - python3 >= 3.6.10 - wget >= 1.19.1 - pip3 >= 20.2.3
- Cygwin should be installed with following packages.
unzip -d Agent-Status-Checker.zip
-
Go to Agent-Status-Checker/AgentStatusChecker.
cd Agent-Status-Checker/AgentStatusChecker -
Run install_me.sh
bash install_me.shor./install_me.sh -
During script execuation it asks for some user input please follow the setup
-
Promt for confirmation of Satisfied dependencies
-
Take User Credentials
- Username with sudo access:
foo - Password:
*****
- Username with sudo access:
-
After below message we have to enter password(please do not enter sudo password),please make sure password should be same for all three prompt.
e.g
-
"Generate vault encrypted password from user credentials,Password should be same for all three prompt".
-
"Note: Please do not enter sudo password".
- Enter password(foo):
***** - New vault password (foo):
***** - Confirm new vault password (foo):
*****
- Enter password(foo):
-
-
Enter Govc Credentials for login
- Please input the number of GOVC URLs:
X - Please input your GOVC IP 1 :
x.x.x.x - Please input your GOVC username 1 :
xyz - GOVC password 1 :
****
- Please input the number of GOVC URLs:
-
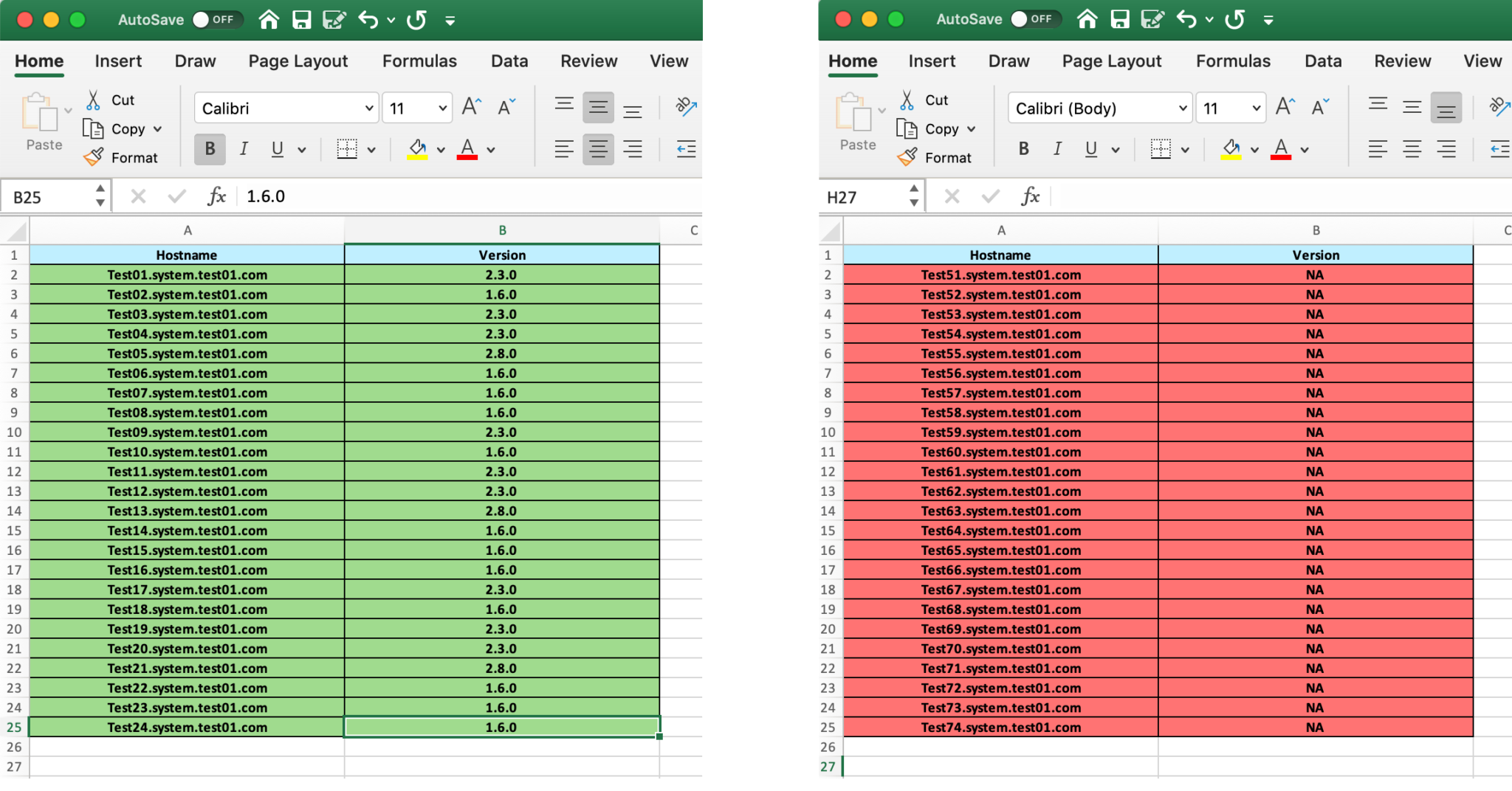
Agent Checker output showing VMware virtual machines with Cloud Agent running (left) and not installed (right).
Purushottam Soni, Vivek Sharma, Cody Yu, Junjie Lu