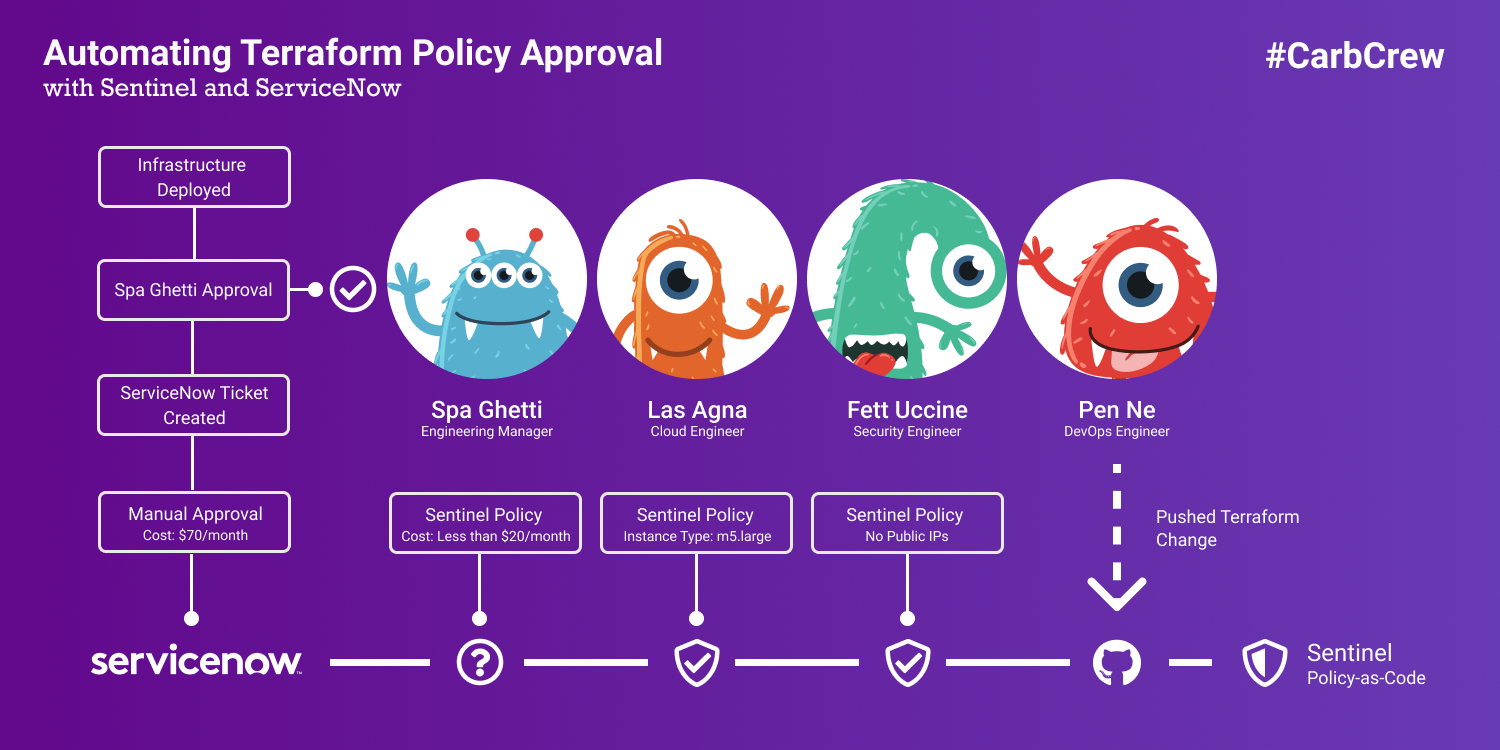
HashiCorp recently created a Terraform ServiceNow integration, which provides essential building blocks for integrating Terraform and ServiceNow. The GIF above depicts the end result and functionally, the following actions.
- Creating a Workspace with ServiceNow
- Adding AWS Credentials and an instance_type in Terraform Cloud
- Manually triggering a Terraform Run
- Sentinel forces a policy override due to the Terraform plan having a monthly cost of more than $20/month
- A manual approval request is created for Spa Ghetti in ServiceNow
- We manually approve the request in ServiceNow
- A REST request is made to the Terraform Policy Override API
Check out the Blog Post on Medium!
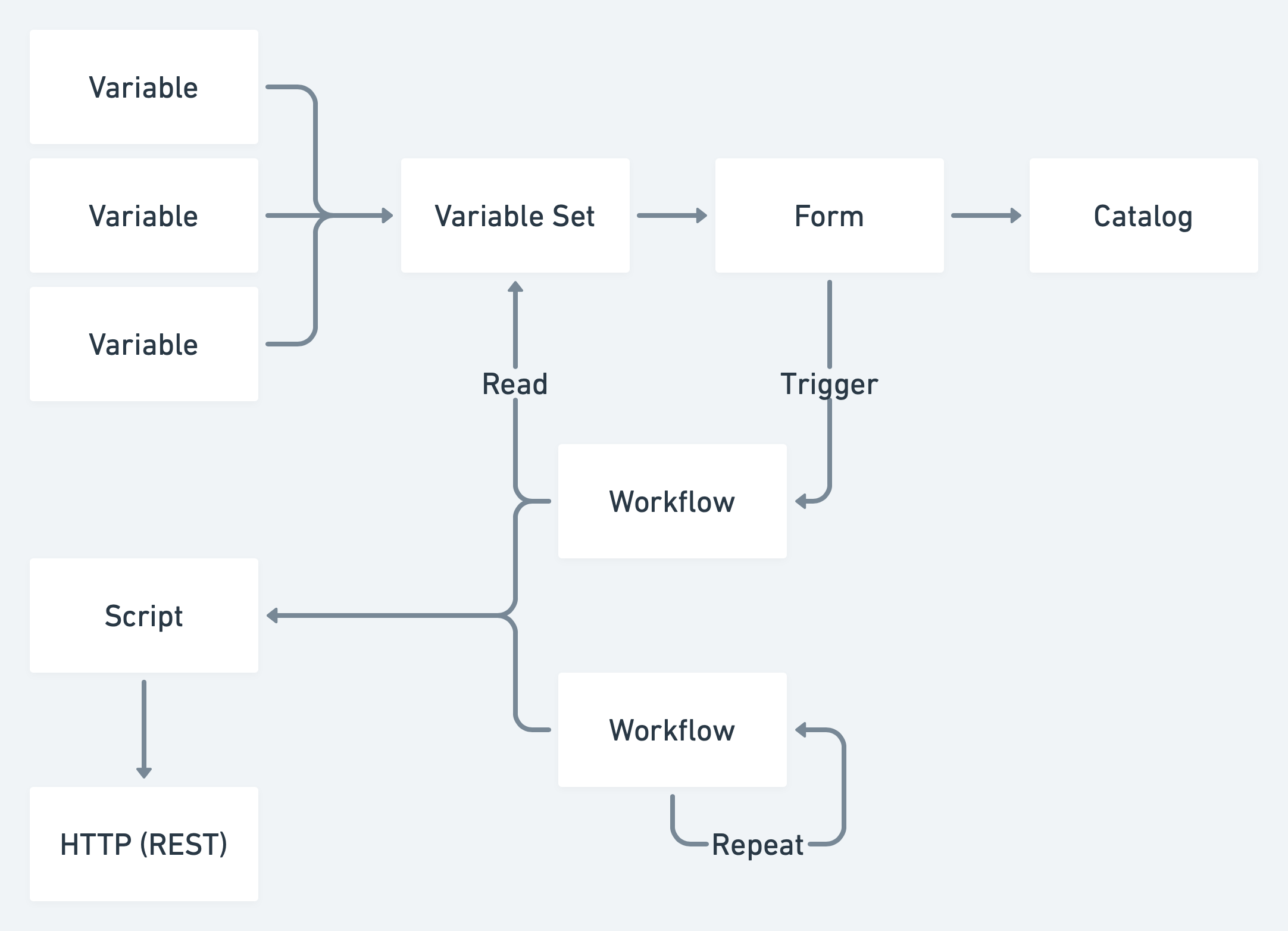
The Terraform ServiceNow Integration builds on top of a few generic constructs from ServiceNow's API.
Catalog: Catalogs are a top-level collection which provides an entry point for users to interact with the integration.
Variables and Variable Sets: Variables and by extension, Variable Sets are embedded within Forms and provide fields for users to enter data. This could be anything from collecting AWS IAM credentials to Workspace names.
Workflows: Workflows allow users to embed an ECMA5 script that can access variables from the invoking object. The two types of workflows utilized in this integration are scheduled on an interval and triggered manually. This allows users to interact with the Terraform API in the form of polling and implicitly. Polling allows us to continuously grab that latest status of a workspace and synchronize that with ServiceNow. Similarly, manual triggers allow users to create workspaces and, in our case, trigger policy overrides.
Scripts: Scripts are pieces of code that need to be shared across workflows. In our case, the integration is utilizing Scripts to wrap the Terraform API interactions in functions that are called from running Workflows.
REST Messages: REST Messages are the last major block and define the available REST requests. This includes setting Headers, Parameters, Method, and more.
For simplicity, we are going to use Terraform Cloud with an Enterprise Trial. However, if you're using a Terraform Enterprise installation you would follow the same steps.
- Once you've logged in, you'll want to create a new Terraform organization. I called it service-now-test but feel free to name it anything.
- Navigate to the Organization Settings tab which is located at the top of the screen.
- Enable the 30 day Enterprise Trial for the organization that you created.
- Create a Service Now team within this organization and enable Manage Policies and Manage Workspaces.
- Navigate to the API Tokens page, generate an organization token and save it somewhere locally.
- Navigate to the VCS Providers page and Add a GitHub OAuth Provider.
- Navigate to your GitHub Settings Page
- Click on Developer Settings
- Click on OAuth Apps
- Create a New OAuth App
- Name it Terraform Cloud
- Set Homepage URL to https://app.terraform.io or your Terraform Enterprise endpoint
- Set Authorization Callback URL to https://app.terraform.io
- Copy the OAuth Client ID and Client Secret into Terraform Cloud's respective inputs
- Click on the Connect organization service-now-example wbutton
- Copy the Callback URL from the newly added Terraform Cloud VCS Provider
- Enter the copied callback URL into your GitHub App's Authorization callback URL and hit save.
- Copy and save the OAuth Token ID from Terraform Cloud
You'll need to request the Terraform Service Now Integration repo from HashiCorp which you can then include in a personal or company VCS repository.
- Create an account at developer.servicenow.com
- Request a Madrid Instance from the Developer Portal
- Log into the ServiceNow Account
- Filter for "Studio" using the left hand search bar
- Select "Import from Source Control"
- Enter the GitHub URL
- Enter your username
- Generate a Personal Access Token from GitHub
- Enter the Personal Access Token as your Password
- Use the Left Hand Search Bar to filter for Users
- Select the Users result under Organization
- Click New at the top of the Content Pane
- Set User ID:
spa.ghetti - Set First Name:
Spa - Set Last Name:
Ghetti - Click Submit
- Navigate to the Studio
- Select the Terraform Integration
- Select Create Application File from the Top Left
- Search for and select
REST Message - Name it
TF Policy Checks - Enter
${hostname}/api/v2/policy-checksas the Endpoint - Select the
HTTP Request Tab - Add an
AuthorizationHeader with the value ofBearer ${api_team_token} - Add a
Content-TypeHeader with the value ofapplication/vnd.api+json - Click Submit
- Delete the
Default GETHTTP Method - Create a new HTTP Method
- Name it
Override Policy - Enter
${hostname}/api/v2/policy-checks/${policy_check_id}/actions/overrideas the Endpoint - Select
POSTas the HTTP Method - Click Submit
- Add a Variable Substitution called
api_team_tokenand select Submit - Add a Variable Substitution called
policy_check_idand select Submit
- Navigate to the Studio
- Select the Terraform Integration
- Select Create Application File from the Top Left
- Search for and select
Script Include - Name it
tf_policy - Paste the contents of
service_now/script_tf_policy.jsinto the Script section - Click Submit
- Navigate to the Studio
- Select the Terraform Integration
- Scroll to the Bottom and select the
Poll Run StateWorkflow - Select the Left Hand Hamburger Menu
- Click Checkout
- Paste the contents of
service_now/wf_poll_run_state.jsinto the Script section - Select the Left Hand Hamburger Menu
- Click Publish
- Select
Worker Poll Run Stateunder Workflow Schedule - Select
Periodicallyfrom the Run dropdown - Click Update
- Utilize the left hand search bar to search for Terraform
- Select Configs
- Enter the API Organization Token that we saved earlier
- Enter the name of your Terraform Organization, mine was
service-now-example
- Utilize the left hand search bar to search for Terraform
- Select VS Repositories
- Name it Terraform Example
- Enter
peytoncasper/terraform-servicenow-exampleinto the Identifier - Enter the GitHub OAuth token from earlier
- Utilize the left hand search bar to search for
Service Catalog - Select
CatalogsunderService Catalog - Click the
+in the upper right - Select
Terraform Catalog - Click Add Here
- Utilize the left hand search bar to search for
Service Catalog - Select
CatalogsunderService Catalog - Select the
Terraform Catalog - Select
Create Workspace - Select
Order Now - Navigate to Terraform Cloud
- Select the Workspace
- Add a
AWS_ACCESS_KEY_IDEnvironment Variable - Add a
AWS_SECRET KEYEnvironment Variable - Add an
instance_typeTerraform Variable with a value ofm5.large - Queue a Terraform Apply
- Wait for the
Soft Policy Check - Refresh the ServiceNow Request and Navigate to the Approval that was added
- Approve it
- Sit back and watch Terraform process the Override Request!
[1] https://www.terraform.io/docs/cloud/integrations/service-now/index.html