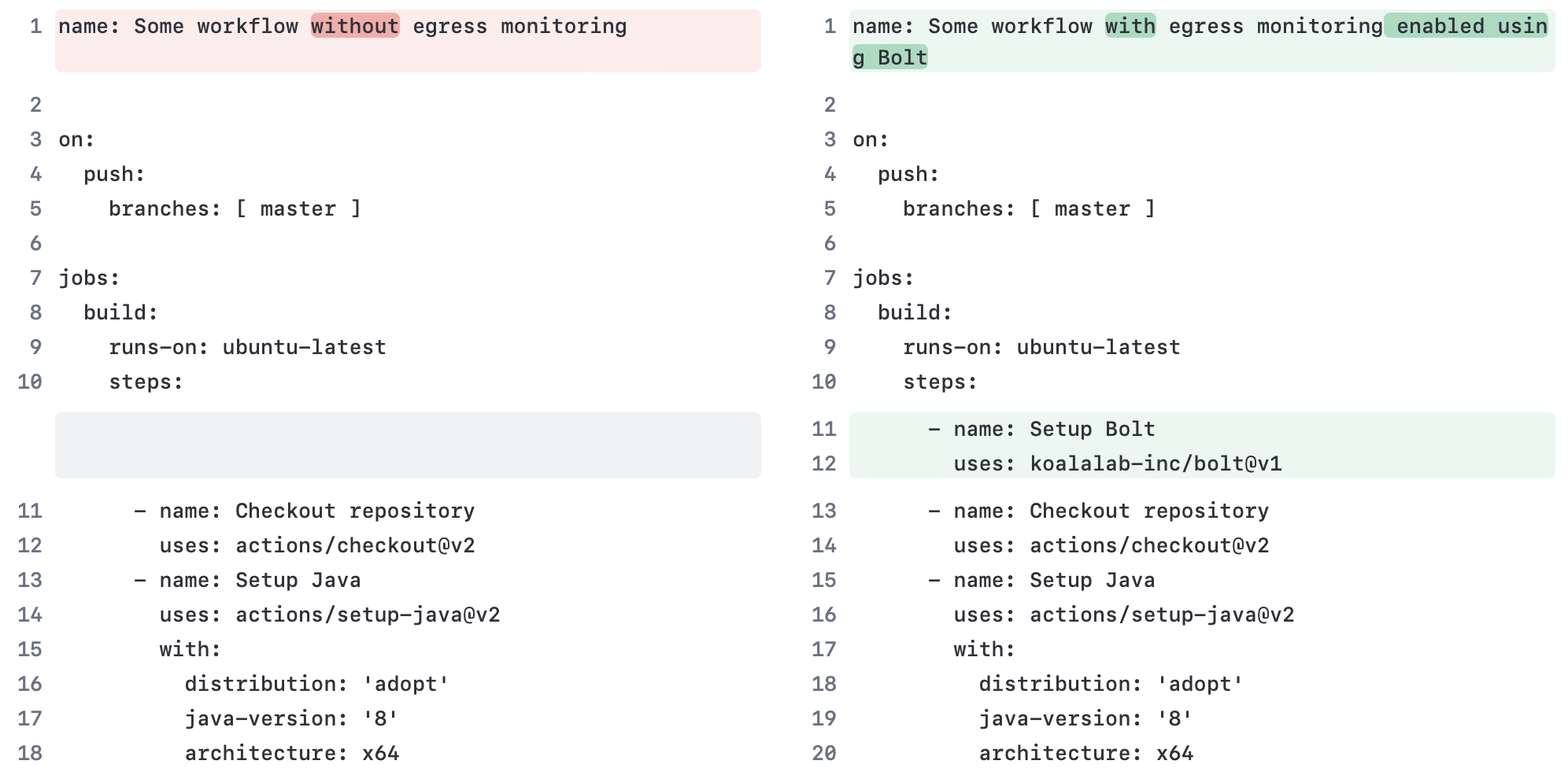
Add this step to jobs in your Github workflow file(s) to secure your runner:
- name: Setup Bolt
uses: koalalab-inc/bolt@v1Bolt is a transparent egress gateway that can be used to control the egress traffic from GitHub hosted runners. It is packaged as a GitHub Action, which means you can easily add it to your workflows and start controlling the egress traffic from your pipelines.
Note
Supports both public and private repositories
Complex CI/CD environments are under increasing threat due to increase in software supply chain attacks. Modern CI/CDs (GitHub CI) allow third-party code in highly privledged CI environment.
GitHub hosted runners are a great way to run your CI/CD pipelines. However, they are not without their limitations. One of the most notable limitations is the lack of egress control. This means that any code running on a GitHub hosted runner can make requests to any external service. This can be a security risk, especially when running untrusted code.
You can start using Bolt by adding the koalalab-inc/bolt action as the first step in the jobs you want to monitor. The action will install and start the Bolt service on the runner. Checkout the configuration options and defaults here.
- name: Setup Bolt
uses: koalalab-inc/bolt@v1You can configuree the Bolt action using inputs. Here is an example of how to configure the action.
- name: Setup Bolt
uses: koalalab-inc/bolt@v1
with:
mode: 'audit'
default_policy: 'block-all'
allow_http: 'false'
egress_rules: |
- name: 'Allow GitHub subs'
destination: '*.github.com'
action: 'allow'| Option | Description |
|---|---|
mode |
Configure the mode of operation for the Bolt gateway. It can be audit or active. Default: audit |
default_policy |
It can be either block-all or allow-all. Default: block-all |
allow_http |
Whether to allow non-secure HTTP requests or not. Default: false |
egress_rules |
A list of custom egress rules to be applied. Default: []. |
You can define custom egress rules to control the egress traffic from your pipelines. Here is an example of how to define custom egress rules.
In audit mode, the Bolt gateway will log the egress traffic as per the defined rules. In active mode, the Bolt gateway will enforce the defined rules.
Egress rule options:
| Option | Description |
|---|---|
name |
A name for the rule |
destination |
The destination domain or IP address. * wilcard is supported in destination. |
action |
The action to be taken. It can be allow or block |
It is an ordered list of rules. The first rule that matches the destination will be applied.
- name: Setup Bolt
uses: koalalab-inc/bolt@v1
with:
mode: 'audit'
default_policy: 'block-all'
allow_http: 'false'
egress_rules: |
- name: 'Allow GitHub subdomains'
destination: '*.github.com'
action: 'allow'
- name: 'Block api subdomain'
destination: 'api.example.com'
action: 'block'
- name: 'Allow other subdomains'
destination: '*.example.com'
action: 'allow'Once the job is over, bolt will add a egress traffic report to the job summary. The report will show the egress traffic and the rules that were applied. A sample report is shown below.
| Option | Value |
|---|---|
| Mode | audit |
| Default Policy | block-all |
| Allow HTTP | false |
- name: 'Allow ifconfig.me'
action: 'allow'
destinatiom: 'ifconfig.me'Note
Running in Audit mode. Unverified destinations will be blocked in Active mode.
| Destination | Scheme | Rule | Action |
|---|---|---|---|
| github.com | https | Reqd by GitHub Action | ✅ |
| packages.microsoft.com | https | Default Policy - block-all | Unknown Destination |
| results-receiver.actions.githubusercontent.com | https | Reqd by GitHub Action | ✅ |
| ppa.launchpadcontent.net | https | Default Policy - block-all | Unknown Destination |
| esm.ubuntu.com | https | Default Policy - block-all | Unknown Destination |
| azure.archive.ubuntu.com | http | allow_http is False | Unknown Destination |
| www.google.com | https | Default Policy - block-all | Unknown Destination |
| ifconfig.me | https | Allow ifconfig.me | ✅ |
| pipelinesghubeus6.actions.githubusercontent.com | https | Reqd by GitHub Action | ✅ |