| services | platforms | author | level | client | service | endpoint |
|---|---|---|---|---|---|---|
active-directory |
dotnet |
TiagoBrenck |
400 |
.NET Framework 4.7 Console, JavaScript SPA |
ASP.NET Web API |
AAD V2 |
Calling a downstream web API from another web API in Microsoft identity platform using the On-Behalf-Of flow
This newer sample takes advantage of the Microsoft identity platform (formerly Azure AD v2.0).
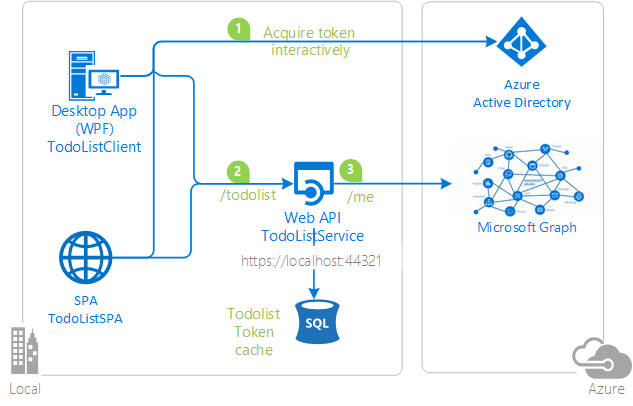
This sample demonstrates a .NET Framework Desktop and JavaScript SPA application calling an ASP.NET Web API, which in turn call the Microsoft Graph. All these are secured using the Microsoft identity platform.
- The .Net client desktop application and the JavaScript SPA application both use the Microsoft Authentication Library (MSAL) to obtain an access token from Azure Active Directory (Azure AD) for the authenticated users:
- The access token is used as a bearer token to authenticate the user when calling the ASP.NET Web API and the Microsoft Graph API.
- This sample also uses the name Application ID (client ID) across multiple client applications, a feature supported by the new Microsoft Identity Platform (Azure AD V2)
Looking for previous versions of this code sample? Check out the tags on the releases GitHub page.
The flow is as follows:
- Sign-in the user in the client application
- Acquire a token to the Asp.net Web API (
TodoListService) and call it. - The Asp.Net Web API then calls another downstream Web API (The Microsoft Graph).
The TodoListService uses a database to:
-
Store the todo list
-
Illustrate token cache serialization in a service
-
TodoListClientuses MSAL.NET to acquire an access token for the user in order to call TodoListService Web API. For more information about how to acquire tokens interactively, see Acquiring tokens interactively Public client application flows. -
TodoListSPA, the single page application, uses MSAL.js to acquire the access token to call TodoListService Web API. -
Then
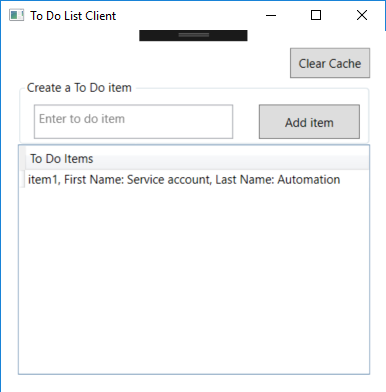
TodoListServicealso uses MSAL.NET to get an access token to act on behalf of the user to call the Microsoft Graph. For details, see Service to service calls on behalf of the user. It then decorates the todolist item entered by the user, with the First name and the Last name of the user. Below is a screenshot of what happens when the user named automation service account entered "item1" in the textbox.
Both flows use the OAuth 2.0 protocol to obtain the tokens. For more information about how the protocols work in this scenario and other scenarios, see Authentication Scenarios for Azure AD.
Looking for previous versions of this code sample? Check out the tags on the releases GitHub page.
From your shell or command line:
git clone https://github.com/Azure-Samples/ms-identity-aspnet-webapi-onbehalfof.gitor download and extract the repository .zip file.
Given that the name of the sample is quiet long, and so are the names of the referenced NuGet packages, you might want to clone it in a folder close to the root of your hard drive, to avoid file size limitations on Windows.
There are two projects in this sample. Each needs to be separately registered in your Azure AD tenant. To register these projects, you can:
- either follow the steps Step 2: Register the sample with your Azure Active Directory tenant and Step 3: Configure the sample to use your Azure AD tenant
- or use PowerShell scripts that:
- automatically creates the Azure AD applications and related objects (passwords, permissions, dependencies) for you
- modify the Visual Studio projects' configuration files.
If you want to use this automation:
-
On Windows, run PowerShell and navigate to the root of the cloned directory
-
In PowerShell run:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope Process -Force
-
Run the script to create your Azure AD application and configure the code of the sample application accordingly.
-
In PowerShell run:
.\AppCreationScripts\Configure.ps1
Other ways of running the scripts are described in App Creation Scripts
-
Open the Visual Studio solution and click start to run the code.
If you don't want to use this automation, follow the steps below.
As a first step you'll need to:
- Sign in to the Azure portal using either a work or school account or a personal Microsoft account.
- If your account is present in more than one Azure AD tenant, select your profile at the top right corner in the menu on top of the page, and then switch directory. Change your portal session to the desired Azure AD tenant.
-
Navigate to the Microsoft identity platform for developers App registrations page.
-
Select New registration.
-
When the Register an application page appears, enter your application's registration information:
- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example
TodoListService-OBO-sample-v2. - Change Supported account types to Accounts in any organizational directory.
- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example
-
Select Register to create the application.
-
On the app Overview page, find the Application (client) ID value and record it for later. You'll need it to configure the Visual Studio configuration file for this project.
-
From the Certificates & secrets page, in the Client secrets section, choose New client secret:
- Type a key description (of instance
app secret), - Select a key duration of either In 1 year, In 2 years, or Never Expires.
- When you press the Add button, the key value will be displayed, copy, and save the value in a safe location.
- You'll need this key later to configure the project in Visual Studio. This key value will not be displayed again, nor retrievable by any other means, so record it as soon as it is visible from the Azure portal.
- Type a key description (of instance
-
Select the API permissions section
- Click the Add a permission button and then,
- Ensure that the Microsoft APIs tab is selected
- In the Commonly used Microsoft APIs section, click on Microsoft Graph
- In the Delegated permissions section, ensure that the right permissions are checked: User.Read. Use the search box if necessary.
- Select the Add permissions button
-
Select the Expose an API section, and:
- Select Add a scope
- accept the proposed Application ID URI (api://{clientId}) by selecting Save and Continue
- Enter the following parameters
- for Scope name use
user_impersonation - Keep Admins and users for Who can consent
- in Admin consent display name type
Access TodoListService-OBO-sample-v2 as a user - in Admin consent description type
Allow the application to access TodoListService-OBO-sample-v2 on behalf of the signed-in user. - in User consent display name type
Access TodoListService-OBO-sample-v2 as a user - in User consent description type
Allow the application to access TodoListService-OBO-sample-v2 on your behalf. - Keep State as Enabled
- Select Add scope
- for Scope name use
- Navigate to the Microsoft identity platform for developers App registrations page.
- Select New registration.
- When the Register an application page appears, enter your application's registration information:
- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example
TodoListClient-OBO-sample-v2. - Change Supported account types to Accounts in any organizational directory.
Note that there are more than one redirect URIs. You'll need to add them from the Authentication tab later after the app has been created successfully.
- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example
- Select Register to create the application.
- On the app Overview page, find the Application (client) ID value and record it for later. You'll need it to configure the Visual Studio configuration file for this project.
- From the app's Overview page, select the Authentication section.
- In the Redirect URIs section, select Web in the combo-box and enter the following redirect URIs.
https://login.microsoftonline.com/common/oauth2/nativeclienturn:ietf:wg:oauth:2.0:oob
- For the
urn:ietf:wg:oauth:2.0:oobRedirect URI, select typePublic client (mobile & desktop)(this is for the desktop client). - In the Advanced settings | Implicit grant section, check ID tokens as this sample requires the Implicit grant flow to be enabled to sign-in the user, and call an API.
- In the Redirect URIs section, select Web in the combo-box and enter the following redirect URIs.
- Select Save.
- Select the API permissions section
- Click the Add a permission button and then,
- Ensure that the My APIs tab is selected
- In the list of APIs, select the API
TodoListService-OBO-sample-v2. - In the Delegated permissions section, ensure that the right permissions are checked: Access 'TodoListService-OBO-sample-v2'. Use the search box if necessary.
- Select the Add permissions button
- Navigate to the Microsoft identity platform for developers App registrations page.
- Select New registration.
- When the Register an application page appears, enter your application's registration information:
- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example
TodoListSPA-OBO-sample-v2. - Change Supported account types to Accounts in any organizational directory.
Note that there are more than one redirect URIs. You'll need to add them from the Authentication tab later after the app has been created successfully.
- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example
- Select Register to create the application.
- On the app Overview page, find the Application (client) ID value and record it for later. You'll need it to configure the Visual Studio configuration file for this project.
- From the app's Overview page, select the Authentication section.
- In the Redirect URIs section, select Web in the combo-box and enter the following redirect URI.
https://localhost:44377
- In the Advanced settings | Implicit grant section, check Access tokens and ID tokens as this sample requires the Implicit grant flow to be enabled to sign-in the user, and call an API.
- In the Redirect URIs section, select Web in the combo-box and enter the following redirect URI.
- Select Save.
- Select the API permissions section
- Click the Add a permission button and then,
- Ensure that the My APIs tab is selected
- In the list of APIs, select the API
TodoListService-OBO-sample-v2. - In the Delegated permissions section, ensure that the right permissions are checked: Access 'TodoListService-OBO-sample-v2'. Use the search box if necessary.
- Select the Add permissions button
For the middle tier web API (TodoListService-OBO-sample-v2) to be able to call the downstream web APIs, the user must grant the middle tier permission to do so in the form of consent.
However, since the middle tier has no interactive UI of its own, you need to explicitly bind the client app registration in Azure AD, with the registration for the web API.
This binding merges the consent required by both the client and middle tier into a single dialog, which will be presented to the user by the client.
You can do so by adding the "Client ID" of the client app, to the manifest of the web API in the knownClientApplications property. Here's how:
- In the Azure portal, navigate to your
TodoListService-OBO-sample-v2app registration, and in the Expose an API section, click on Add a client application. Client IDs of the client applications (TodoListClient-OBO-sample-v2,TodoListSPA-OBO-sample-v2) as elements of the array. - Click Add application
In the steps below, "ClientID" is the same as "Application ID" or "AppId".
Open the solution in Visual Studio to configure the projects
Note: if you used the setup scripts, the changes below will have been applied for you
- Open the
TodoListService\Web.Configfile - Find the app key
ida:Tenantand replace the existing value with your Azure AD tenant name. - Find the app key
ida:Audienceand replace the existing value with the App URI you registered earlier for theTodoListService-OBO-sample-v2app. - Find the app key
ida:AppKeyand replace the existing value with the key you saved during the creation of theTodoListService-OBO-sample-v2app, in the Azure portal. - Find the app key
ida:ClientIDand replace the existing value with the application ID (clientId) of theTodoListService-OBO-sample-v2application copied from the Azure portal.
Note: if you used the setup scripts, the changes below will have been applied for you
- Open the
TodoListClient\App.Configfile - Find the app key
ida:Tenantand replace the existing value with your Azure AD tenant name. - Find the app key
ida:ClientIdand replace the existing value with the application ID (clientId) of theTodoListClient-OBO-sample-v2application copied from the Azure portal. - Find the app key
todo:TodoListScopeand replace the existing value with 'api://{clientId}/.default'. - Find the app key
todo:TodoListBaseAddressand replace the existing value with the base address of the TodoListService-OBO project (by defaulthttps://localhost:44321/).
Note: if you used the setup scripts, the changes below will have been applied for you
-
Open the
TodoListSPA\appconfig.jsfile -
Find the app key
authorityand replace the existing value with your authority url, for examplehttps://login.microsoftonline.com/<your_tenant_name>. -
Find the app key
clientIdand replace the existing value with the application ID (clientId) of theTodoListSPA-OBO-sample-v2application copied from the Azure portal. -
Find the app key
redirectUriand replace the existing value with the base address of the TodoListClient-OBO project (by defaulthttps://localhost:44377/). -
Find the app key
resourceIdand replace the existing value with the App URI you registered earlier for theTodoListSPA-OBO-sample-v2app. -
Find the app key
resourceBaseAddressand replace the existing value with the base address of the TodoListService-OBO project (by defaulthttps://localhost:44321/). -
Find the app key
webApiScopeand replace the existing value with "api://{clientId}/.default".While running the SPA app in the browser, take care to allow popups from this app.
Clean the solution, rebuild the solution, and run it. You might want to go into the solution properties and set both projects, or the three projects, as startup projects, with the service project starting first.
Explore the sample by signing in, adding items to the To Do list, Clearing the cache (which removes the user account), and starting again. The ToDo list service will take the user's access token, received from the client, and use it to get another access token so it can act On Behalf Of the user in the Microsoft Graph API. This sample caches the user's access token at the To Do list service, so it does not request a new access token on every request. This cache is a database cache.
[Optionally], when you have added a few items with the TodoList Client, login to the todoListSPA with the same credentials as the todoListClient, and observe the id-Token, and the content of the Todo List as stored on the service, but as Json. This will help you understand the information circulating on the network.
There are many key points in this sample to make the On-Behalf-Of-(OBO) flow work properly and in this section we will explain these key points for each project. Though we have three applications in the solution, you will notice that we only registered two applications in Azure AD. This is because Azure AD now allows multiple types of applications, like in this case a desktop and a javascript SPA application, to share the same app registration in the Azure AD's app registration portal.
This project represents the .NET desktop UI part of the flow, where users would sign-in and interact with the Web API (TodoListService). The API that this app calls ((TodoListService)) also requests data from another API (Microsoft Graph) by using an access token obtained for the signed-in user using the On-Behalf-Of (OBO) flow . The first key point to pay attention is the MainWindow initialization. Here is the code snippet:
private readonly IPublicClientApplication _app;
public MainWindow()
{
InitializeComponent();
_app = PublicClientApplicationBuilder.Create(clientId)
.WithAuthority(authority)
.Build();
TokenCacheHelper.EnableSerialization(_app.UserTokenCache);
GetTodoList();
}Important things to notice:
- We create an
IPublicClientApplicationusing MSAL Build Pattern passing theclientIdandauthorityin the builder. ThisIPublicClientApplicationwill be responsible of acquiring access tokens later in the code. IPublicClientApplicationalso has a token cache, that will cache access tokens and refresh tokens for the signed-in user. This is done so that the application can fetch access tokens after they have expired without prompting the user to sign-in again.- Our
UserTokenCacheimplementation uses the local file system for caching. Other popular options for caching tokens areDatabaseorDistributed InMemory cache.
Then we have the SignIn method, where the login screen is presented to the user and they can provide their credentials.
private static readonly string[] Scopes = { "https://<yourTenant>.onmicrosoft.com/TodoListService-OBO/.default" };
private async void SignIn(object sender = null, RoutedEventArgs args = null)
{
AuthenticationResult result = await _app.AcquireTokenInteractive(Scopes)
.WithAccount(accounts.FirstOrDefault())
.WithPrompt(Prompt.SelectAccount)
.ExecuteAsync()
.ConfigureAwait(false);
}Important things to notice:
- The scope
.defaultis a built-in scope for every application that refers to the static list of permissions configured on the application registration. In our scenario here, it enables the user to grant consent for permissions for both the Web API and the downstream API (Microsoft Graph). For example, the permissions for the Web API and the downstream API (Microsoft Graph) are listed below:- TodoListService-OBO-sample-v2
- user_impersonation
- Microsoft Graph
- user.read
- TodoListService-OBO-sample-v2
- When you use the
.defaultscope, the end user is prompted for a combined set of permissions that include scopes from both the TodoListService-OBO and Microsoft Graph. - We call the AcquireTokenInteractive which will present a window to the user to provide their credentials. When it acquires the access token, MSAL also saves this token in its token cache.
The method to add a new Todo is where we consume our TodoListService-OBO Web API, that will consume the downstream Microsoft Graph using an access token obtained using the On-Behalf-Of (OBO) flow.
To check if the user is signed in, we use the method GetAccountsAsync:
var accounts = (await _app.GetAccountsAsync()).ToList();
if (!accounts.Any())
{
MessageBox.Show("Please sign in first");
return;
}Now we call the AcquireTokenSilent method to get the cached access token we had obtained earlier during our sign-in. With this token, we can then create a HTTP POST request to our Web API attaching it on the header as Bearer.
AuthenticationResult result = null;
try
{
result = await _app.AcquireTokenSilent(Scopes, accounts.FirstOrDefault())
.ExecuteAsync()
.ConfigureAwait(false);
}
catch (MsalUiRequiredException)
{
MessageBox.Show("Please re-sign");
}
catch (MsalException ex)
{
// An unexpected error occurred.
}
HttpClient httpClient = new HttpClient();
httpClient.DefaultRequestHeaders.Authorization = new AuthenticationHeaderValue("Bearer", result.AccessToken);
HttpContent content = new FormUrlEncodedContent(new[] { new KeyValuePair<string, string>("Title", TodoText.Text) });
HttpResponseMessage response = await httpClient.PostAsync(todoListBaseAddress + "/api/todolist", content);
if (response.IsSuccessStatusCode)
{
TodoText.Text = "";
GetTodoList();
}
else
{
MessageBox.Show("An error occurred : " + response.ReasonPhrase);
}Important things to notice:
- After the Sign-In, the user token will be cached and it can be acquired again by calling AcquireTokenSilent.
MsalUiRequiredExceptionwill be thrown if there is no token for that user with the specified scope in the cache, or it got expired. This case requires the user to Sign-In again.
The TodoListService is our Web API project that will make a call to the downstream Microsoft Graph API using an access token obtained via the On-Behalf-Of (OBO) flow. The client that called TodoListService, sends a Bearer token on the HTTP header and this token will be used to impersonate the user and acquire another acess token for Microsoft Graph API.
The first key point to pay attention in this project is the Startup configuration:
public void ConfigureAuth(IAppBuilder app)
{
app.UseWindowsAzureActiveDirectoryBearerAuthentication(
new WindowsAzureActiveDirectoryBearerAuthenticationOptions
{
Tenant = ConfigurationManager.AppSettings["ida:Tenant"],
TokenValidationParameters = new TokenValidationParameters
{
SaveSigninToken = true,
ValidAudience = ConfigurationManager.AppSettings["ida:Audience"]
}
});
}Important things to notice:
- Notice that we are setting
SaveSigninTokentotrueon theTokenValidationParameters. This is essential to get theBearertoken from the HTTP header later, using the identity bootstrap context:ClaimsPrincipal.Current.Identities.First().BootstrapContext
The logic to call Microsoft Graph on behalf of a user is inside the method CallGraphAPIOnBehalfOfUser. In this sample, we are getting the user's first name and last name and adding them in the todo's title.
The one thing that you will notice is that we are using a different type of token cache provider in the Web API, which caches tokens in a SQL Server database. The implementation of this caching mechanism is incapsulated in the MSALPerUserSqlTokenCacheProvider class.
private async Task<UserProfile> CallGraphAPIOnBehalfOfUser()
{
string[] scopes = { "user.read" };
UserProfile profile = null;
try
{
var app = ConfidentialClientApplicationBuilder.Create(clientId)
.WithAuthority(authority)
.WithClientSecret(appKey)
.WithRedirectUri(redirectUri)
.Build();
MSALPerUserSqlTokenCacheProvider sqlCache = new MSALPerUserSqlTokenCacheProvider(app.UserTokenCache, db, ClaimsPrincipal.Current);
var bootstrapContext = ClaimsPrincipal.Current.Identities.First().BootstrapContext as System.IdentityModel.Tokens.BootstrapContext;
UserAssertion userAssertion = new UserAssertion(bootstrapContext.Token, "urn:ietf:params:oauth:grant-type:jwt-bearer");
AuthenticationResult result = await app.AcquireTokenOnBehalfOf(scopes, userAssertion)
.ExecuteAsync();
string accessToken = result.AccessToken;
if (accessToken == null)
{
throw new Exception("Access Token could not be acquired.");
}
string requestUrl = String.Format(CultureInfo.InvariantCulture, graphUserUrl, HttpUtility.UrlEncode(tenant));
HttpClient client = new HttpClient();
HttpRequestMessage request = new HttpRequestMessage(HttpMethod.Get, requestUrl);
request.Headers.Authorization = new AuthenticationHeaderValue("Bearer", accessToken);
HttpResponseMessage response = await client.SendAsync(request);
if (response.IsSuccessStatusCode)
{
string responseString = await response.Content.ReadAsStringAsync();
profile = JsonConvert.DeserializeObject<UserProfile>(responseString);
return (profile);
}
throw new Exception("An unexpected error occurred calling the Graph API.");
}
catch (Exception ex)
{
throw ex;
}
}Important things to notice:
- We are using the scope
user.readto get the user's profile on Microsoft Graph. - The
ConfidentialClientApplicationis built using the Build pattern introduced in MSAL v3.x, passing theclientId,authority,appKeyandredirectUrito the builder. All of these values are related to the TodoListService. We don't use anything related to the TodoListClient application here. - We hook the
ConfidentialClientApplicationUserTokenCacheon ourMSALPerUserSqlTokenCacheProvider, so we can store the cache on the database. Other alternatives for cache storage could beInMemoryorSession. - We instantiate a
UserAssertionusing theBearertoken sent by the client andurn:ietf:params:oauth:grant-type:jwt-beareras assertion type (read more here). This class represents the credential of the user being impersonated. - The method
AcquireTokenOnBehalfOfwill try to get a token for the impersonated user. If all the validations pass and the impersonated user have consented the requested scope (user.readon our sample), an access token will be returned and be used on Microsoft Graph request on behalf on the user.
The project TodoListSPA has the same role as TodoListClient. It represents the UI part of the flow, where users can interact with and consumes TodoListService Web API. This project is using MSAL.js and uses the method loginPopup to establish a user context.
The first key point in this project is the UserAgentApplication instantiation. Here is the code:
var config = {
popUp: true,
webApiScope: "https://<yourTenant>/TodoListService-OBO/.default",
auth: {
authority: "https://login.microsoftonline.com/<yourTenant>",
clientId: "<TodoListSPA_ClientId>",
redirectUri: "http://localhost:16969/",
},
cache: {
cacheLocation: "localStorage",
storeAuthStateInCookie: true
}
}
const clientApplication = new Msal.UserAgentApplication(config);Important things to notice:
- We are using the ConfigurationOptions introduced on MSAL.js to initialize the client application.
- The
configis found atappconfig.jsfile. - We are using
localStorageto store the cache. The other option would besessionStorage.
The entry point in this project, is the method displayTodoList(), triggered when the user clicks on the Display the todo list button. This method checks if the user is logged and prompts the login screen in case they are not. The config is found at appconfig.js file.
const loginRequest = {
scopes: [config.webApiScope],
prompt: "select_account",
}
function displayTodoList() {
var account = clientApplication.getAccount();
if (account) {
onLogin(null, account);
}
else {
clientApplication.loginPopup(loginRequest).then(function (loginResponse) {
if (loginResponse.account) {
onLogin(null, loginResponse.account);
}
});
}
}Important things to notice:
- To find out if the user is logged in, we use the method
getAccount()which returns an object Account when the user is logged in. - To prompt the login screen, we call the method
loginPopup()passing theloginRequestobject for configuration. The method returns an AuthResponse promise. Another option to prompt it is usingloginRedirect(), however this method requires a slightly different configuration. You can read more about these two methods on MSAL.js documentation.
Once the user have logged in, they can call our TodoListService Web API sending the Bearer token on the HTTP header. Here is the code:
const accessTokenRequest = {
scopes: [config.webApiScope]
}
function acquireAnAccessTokenAndCallTheProtectedService() {
clientApplication.acquireTokenSilent(accessTokenRequest)
.then(response => {
callServiceWithToken(response.accessToken, webApiConfig.resourceBaseAddress + "api/todolist");
})
.catch(err => {
if (err.name === "InteractionRequiredAuthError") {
clientApplication.acquireTokenPopup(accessTokenRequest).then(
function (response) {
callServiceWithToken(response.accessToken, webApiConfig.resourceBaseAddress + "api/todolist");
}).catch(function (error) {
console.log(error);
});
} else {
showError("acquireToken", err.errorMessage);
}
});
}
function callServiceWithToken(token, endpoint) {
var headers = new Headers();
var bearer = "Bearer " + token;
headers.append("Authorization", bearer);
var options = {
method: "GET",
headers: headers
};
// Note that fetch API is not available in all browsers
fetch(endpoint, options)
.then(function (response) {
var contentType = response.headers.get("content-type");
if (response.status === 200 && contentType && contentType.indexOf("application/json") !== -1) {
// Case where we got the content from the API (as JSon)
response.json()
.then(function (data) {
// Display response in the page
})
.catch(function (error) {
showError(endpoint, error);
});
} else if (response.status === 403 && contentType && contentType.indexOf("text/plain; charset=utf-8") !== -1) {
response.text()
.then(function (data) {
var claims = data;
clientApplication.acquireTokenPopup(claims).then(function (response) {
onAccessToken(null, response.accessToken, null);
}).catch(function (error) {
console.log(error);
});
})
.catch(function (error) {
showError(endpoint, error);
});
} else {
response.text()
.then(function (data) {
// Display response in the page
showError(endpoint, data);
})
.catch(function (error) {
showError(endpoint, error);
});
}
})
.catch(function (error) {
showError(endpoint, error);
});
}This project has two WebApp / Web API projects. To deploy them to Azure Web Sites, you'll need, for each one, to:
- create an Azure Web Site
- publish the Web App / Web APIs to the web site, and
- update its client(s) to call the web site instead of IIS Express.
- Sign in to the Azure portal.
- Click
Create a resourcein the top left-hand corner, select Web --> Web App, and give your web site a name, for example,TodoListService-OBO-sample-v2-contoso.azurewebsites.net. - Thereafter select the
Subscription,Resource Group,App service plan and Location.OSwill be Windows andPublishwill be Code. - Click
Createand wait for the App Service to be created. - Once you get the
Deployment succeedednotification, then click onGo to resourceto navigate to the newly created App service. - The following steps provide instructions to create a Sql database that the sample needs. If you already have a Sql Server and database present and a connection string available, skip the steps till we ask you to provide the connections string in the
Application Settings. - Click
Create a resourcein the top left-hand corner again, select Databases --> SQL Database, to create a new database. Follow theQuickstart tutorialif needed. - You can name the Sql server and database whatever you want to.
- Select or create a database server, and enter server login credentials. Carefully note down the username and password for the Sql server as you'll need it when constructing your Sql conenction string later.
- Wait for the
Deployment succeedednotification, then click onGo to resourceto navigate to the newly created database's manage screen. - Click on Connection Strings on left menu and copy the ADO.NET (SQL authentication) connection string. Populate User ID={your_username};Password={your_password}; with values your provided during database creation.Copy this connection string.
- Once the web site is created, locate it it in the Dashboard and click it to open App Services Overview screen.
- Click on Configuration in the left menu of the App service and add the copied Sql connection string in the Connection strings section as
DefaultConnection. - Choose
SQLAzurein the Type dropdown. Save the setting. - From the Overview tab of the App Service, download the publish profile by clicking the Get publish profile link and save it. Other deployment mechanisms, such as from source control, can also be used.
- Switch to Visual Studio and go to the TodoListService-OBO-sample-v2 project. Right click on the project in the Solution Explorer and select Publish. Click Import Profile on the bottom bar, and import the publish profile that you downloaded earlier.
- Click on Configure and in the
Connection tab, update the Destination URL so that it is ahttpsin the home page url, for example https://TodoListService-OBO-sample-v2-contoso.azurewebsites.net. Click Next. - On the Settings tab, make sure
Enable Organizational Authenticationis NOT selected. - Under Databases, select the connection that you created on Azure Portal (if it does not show on the dropdown, click on the button and add it).
- Make sure
Use this connection string at runtimeandExecute Code First Migrationsare checked. - Click Save. Click on Publish on the main screen.
- Visual Studio will publish the project and automatically open a browser to the URL of the project. Give it a minute for the migrations to run. If you see the default web page of the project, the publication was successful.
- Navigate back to to the Azure portal. In the left-hand navigation pane, select the Azure Active Directory service, and then select App registrations (Preview).
- In the resultant screen, select the
TodoListService-OBO-sample-v2application. - From the Branding menu, update the Home page URL, to the address of your service, for example https://TodoListService-OBO-sample-v2-contoso.azurewebsites.net. Save the configuration.
- Add the same URL in the list of values of the Authentication -> Redirect URIs menu. If you have multiple redirect urls, make sure that there a new entry using the App service's Uri for each redirect url.
Update the TodoListClient-OBO-sample-v2 to call the TodoListService-OBO-sample-v2 Running in Azure Web Sites
- In Visual Studio, go to the
TodoListClient-OBO-sample-v2project. - Open
TodoListClient\App.Config. Only one change is needed - update thetodo:TodoListBaseAddresskey value to be the address of the website you published, for example, https://TodoListService-OBO-sample-v2-contoso.azurewebsites.net. - Run the client! If you are trying multiple different client types (for example, .Net, Windows Store, Android, iOS) you can have them all call this one published web API.
Update the TodoListSPA-OBO-sample-v2 to call the TodoListService-OBO-sample-v2 Running in Azure Web Sites
- In Visual Studio, go to the
TodoListSPA-OBO-sample-v2project. - Open
TodoListSPA\appconfig.js. Only one change is needed - update thetodo:TodoListBaseAddresskey value to be the address of the website you published, for example, https://TodoListService-OBO-sample-v2-contoso.azurewebsites.net. - Run the client! If you are trying multiple different client types (for example, .Net, Windows Store, Android, iOS) you can have them all call this one published web API.
- Sign in to the Azure portal.
- Click
Create a resourcein the top left-hand corner, select Web --> Web App, and give your web site a name, for example,TodoListSPA-OBO-sample-v2-contoso.azurewebsites.net. - Thereafter select the
Subscription,Resource Group,App service plan and Location.OSwill be Windows andPublishwill be Code. - Click
Createand wait for the App Service to be created. - Once you get the
Deployment succeedednotification, then click onGo to resourceto navigate to the newly created App service. - Once the web site is created, locate it it in the Dashboard and click it to open App Services Overview screen.
- From the Overview tab of the App Service, download the publish profile by clicking the Get publish profile link and save it. Other deployment mechanisms, such as from source control, can also be used.
- Switch to Visual Studio and go to the TodoListSPA-OBO-sample-v2 project. Right click on the project in the Solution Explorer and select Publish. Click Import Profile on the bottom bar, and import the publish profile that you downloaded earlier.
- Click on Configure and in the
Connection tab, update the Destination URL so that it is ahttpsin the home page url, for example https://TodoListSPA-OBO-sample-v2-contoso.azurewebsites.net. Click Next. - On the Settings tab, make sure
Enable Organizational Authenticationis NOT selected. Click Save. Click on Publish on the main screen. - Visual Studio will publish the project and automatically open a browser to the URL of the project. If you see the default web page of the project, the publication was successful.
- Navigate back to to the Azure portal. In the left-hand navigation pane, select the Azure Active Directory service, and then select App registrations (Preview).
- In the resultant screen, select the
TodoListSPA-OBO-sample-v2application. - From the Branding menu, update the Home page URL, to the address of your service, for example https://TodoListSPA-OBO-sample-v2-contoso.azurewebsites.net. Save the configuration.
- Add the same URL in the list of values of the Authentication -> Redirect URIs menu. If you have multiple redirect urls, make sure that there a new entry using the App service's Uri for each redirect url.
First, in Visual Studio 2017 create an empty solution to host the projects. Then, follow these steps to create each project.
- In Visual Studio 2017, create a new
Visual C#ASP.NET Web Application (.NET Framework)project. In the next screen, choose theWeb APIproject template. And while on this screen, click the Change Authentication button, select 'Work or School Accounts', 'Cloud - Single Organization', enter the name of your Azure AD tenant. You will be prompted to sign in to your Azure AD tenant. NOTE: You must sign in with a user that is in the tenant; you cannot, during this step, sign in with a Microsoft account. - Add the Microsoft Authentication Library (MSAL) NuGet, Microsoft.Identity.Client, EntityFramework, and Microsoft.AspNet.WebApi.Cors to the project.
- Add reference of the
System.IdentityModelassembly in the project. - In the
Modelsfolder, add a new class calledTodoItem.cs. Copy the implementation of TodoItem from this sample into the class. - In the
Modelsfolder, add a new class calledUserProfile.cs. Copy the implementation of UserProfile from this sample into the class. - Create a new folder named
DAL. In theDALfolder, add a new class calledTodoListServiceContext.cs. Copy the implementation of TodoListServiceContext from this sample into the class. - Create a new folder named
Utils. In theUtilsfolder, add three new classes (ClaimConstants.cs,ClaimsPrincipalExtensions.csandMSALPerUserSqlTokenCacheProvider) and copy their implementations from this sample. - Add a new, empty, Web API 2 Controller called
TodoListController. - Copy the implementation of the TodoListController from this sample into the controller. Don't forget to add the
[Authorize]attribute to the class. - In
web.configmake sure that the keyida:AADInstance,ida:Tenant,ida:ClientID, andida:AppKeyexist, and are populated. For the global Azure cloud, the value ofida:AADInstanceishttps://login.onmicrosoft.com/{0}. - In
web.config, in<appSettings>, create keys forida:GraphUserUrland set the its value tohttps://graph.microsoft.com/v1.0/me/.
- In the solution, create a new Windows --> Windows Classic Desktop -> WPF App(.NET Framework) called TodoListClient.
- Add the Microsoft Authentication Library (MSAL) NuGet, Microsoft.Identity.Client to the project.
- Add assembly references to
System.Net.Http,System.Web.Extensions, andSystem.Configuration. - Add a new class to the project called
TodoItem.cs. Copy the code from the sample project file of the same name into this class, completely replacing the code in the file in the new project. - Add a new class to the project called
FileCache.cs. Copy the code from the sample project file of the same name into this class, completely replacing the code in the file in the new project. - Copy the markup from `MainWindow.xaml' in the sample project into the file of the same name in the new project, completely replacing the markup in the file in the new project.
- Copy the code from
MainWindow.xaml.csin the sample project into the file of the same name in the new project, completely replacing the code in the file in the new project. - In
app.configcreate keys forida:AADInstance,ida:Tenant,ida:ClientId,ida:RedirectUri,todo:TodoListScope, andtodo:TodoListBaseAddressand set them accordingly. For the global Azure cloud, the value ofida:AADInstanceishttps://login.onmicrosoft.com/{0}.
Finally, in the properties of the solution itself, set both projects as startup projects.
Use Stack Overflow to get support from the community.
Ask your questions on Stack Overflow first and browse existing issues to see if someone has asked your question before.
Make sure that your questions or comments are tagged with [msal dotnet].
If you find a bug in the sample, please raise the issue on GitHub Issues.
To provide a recommendation, visit the following User Voice page.
If you'd like to contribute to this sample, see CONTRIBUTING.MD.
This project has adopted the Microsoft Open Source Code of Conduct. For more information, see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.
- Other samples for Azure AD v2.0 are available from https://aka.ms/aaddevsamplesv2
- Microsoft identity platform and Implicit grant flow
- Microsoft identity platform and OAuth 2.0 On-Behalf-Of flow
- The conceptual documentation for MSAL.NET is available from https://aka.ms/msalnet
- the documentation for Azure AD v2.0 is available from https://aka.ms/aadv2
- Why update to Microsoft identity platform (v2.0)? For more information about how OAuth 2.0 protocols work in this scenario and other scenarios, see Authentication Scenarios for Azure AD.