Use Sentinel. Run Failed Login Attempt Query. Turn on Fusion Machine Learning.
Lab consists of a Run Failed Login Attempt Query & Turn on Fusion Machine Learning using Microsoft Azure Sentinel (SIEM). We will monitor activity of Microsoft 365 Security with Microsoft Sentinel. A Log Analytics workspace is required to house all of the data that Microsoft Sentinel will be ingesting and using for its detections, analytics, and other features.- Microsoft Azure Sentinel Portal
- Password Lockout Settings modified by anyone assigned the following roles:
- Log Analytics Contributor
- Log Analytics Reader
- Global Administrator
Select Log Workspace Analytics:
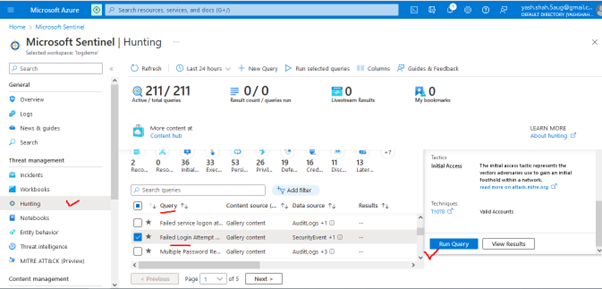
Select Query:
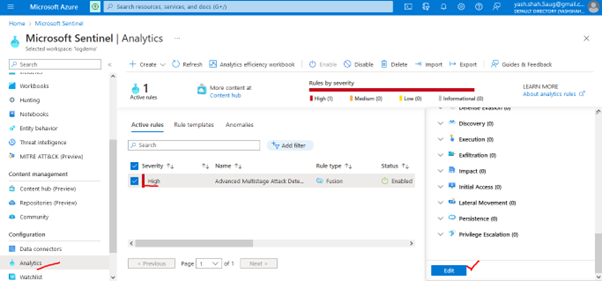
Active Rules of Query:
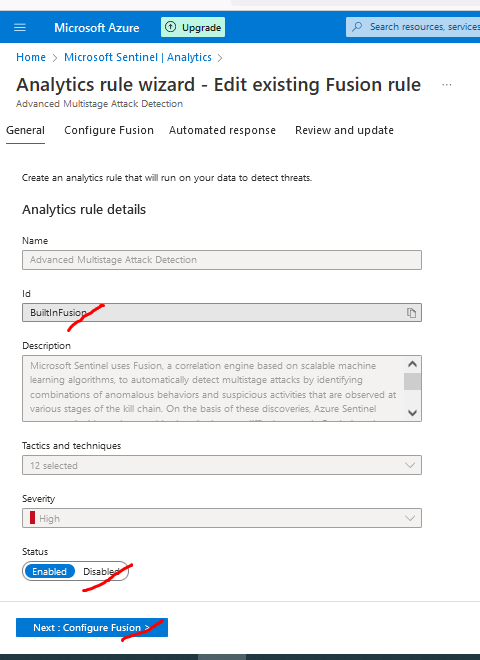
Enable Status:
Result:
