This example uses:
- Amazon Web Services
- GitHub Actions
- Terraform 0.14+
- Vault 1.5+
- HashiCorp Cloud Platform Vault (managed Vault offering)
- Terraform Cloud (for configuring Vault, uses
vault/directory)
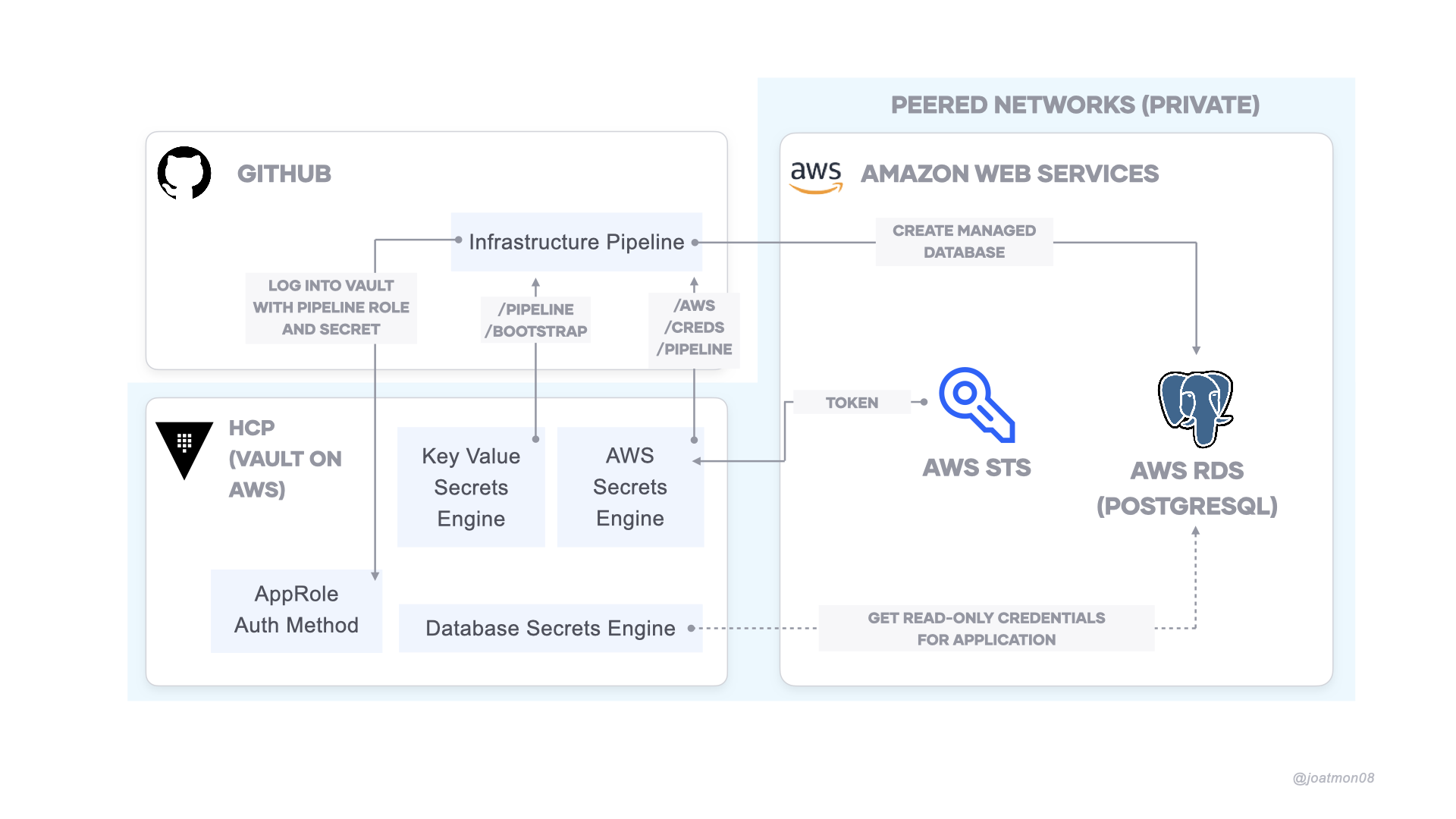
The infrastructure pipeline runs Terraform to create a PostgreSQL database in AWS. It securely retrieves secrets from HashiCorp Vault.
-
In your CLI, set the Vault address, token, and namespace.
$ export VAULT_ADDR= $ export VAULT_TOKEN= $ export VAULT_NAMESPACE=
-
Get Vault secret ID.
$ make get-secret
-
Go to the GitHub repository's secrets.
-
Set the following repository secrets:
VAULT_ADDR: address of VaultVAULT_NAMESPACE:adminVAULT_ROLE_ID:infrastructure-pipelineVAULT_SECRET_ID: add secret ID from CLI
-
Make changes to this repository to execute Terraform.
-
The GitHub Actions workflow accesses Vault over public internet. To access Vault over private connection, you will want to deploy a self-hosted runner or GitHub Enterprise. Vault configures the PostgreSQL database over a private connection.
-
The demo uses HashiCorp Cloud Platform. You can substitute the Vault endpoint with your own Vault instance, as long as it can connect to AWS.## Requirements