- In the Github page for the template, press the
Use this templatebutton. Select the visibility level and presscreate repository from template. - Now Clone it to your local machine
- In the upper-right corner of any page, click your profile photo, then click Settings.
- In the left sidebar, click Developer settings.
- In the left sidebar, under Personal access tokens, click Tokens (classic).
- Click Generate new token (classic).
- Optionally, under Token name, enter a name for the token.
- Under Expiration, select an expiration for the token. (If you do not want to have to go through this process again, I recommend having no expiration date.)
- Select the scopes you'd like to grant this token. To use your token to access repositories from the command line, select repo. A token with no assigned scopes can only access public information. I chose to give the token full permission for all scopes to remove any chance for future issues. For more information, see "Available scopes".
- Click Generate token.
- Copy the token for safekeeping until you are able to create a secret in AWS Secrets Manager to house it.
- Because we are storing sensitive information in Secrets Manager, please respect your fellow classmates and do not attempt to view their secret. Whenever a secret is viewed the last retrieved date will update, so if you have not accessed your token and the date has changed, you may want to revoke that token's access and create a new one.
- Navigate to the AWS login page
- Select the role that you will be housing your project in. I believe for most that will be Shibboleth-aws-capstone-admin
- Click Sign In
- In the search bar type in Secrets Manager
- Click on Secrets Manager
- Click on the orange "Store a new secret" button
- Underneath "Secret type" select Other type of secret
- You will be creating two separate keys: gitHubOwner and gitHubOAuthToken
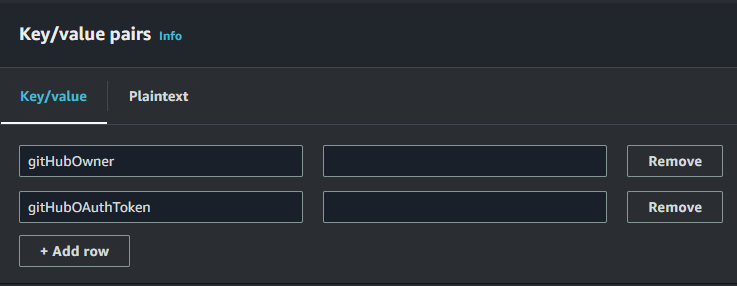
- The value for gitHubOwner should be your github profile name
- The value for gitHubOAuthToken should be the token you copied at the end othe Github OAuth Token setup
- Click the orange "Next" button in the bottom right corner
- For "Secret name" put <REPLACE_PROJECT_NAME>-githubPersonalAccess
- A description is not required, but you may add one if you want
- Click the orange "Next" button in the bottom right corner for step 2 & 3
- Check to make sure everything looks correct on the Review page and click on the orange "Store" button when you are ready to create your secret
Note: Each service folder has its own README file for specific setup directions and notes.
- From the root folder, fill out the project name in the package.json file.
- From the root folder, run
npm installto install your linting packages. - Navigate to the back-end folder and follow the instructions.
- Navigate to the buildspecs folder and follow the instructions.
- Commit changes to Github.
- Navigate to the pipeline folder and follow the instructions.
- Verify your CICD has completed successfully from the AWS Cloudformation console. Once it has completed building, your project stack will automatically start building.
- Verify your project has built successfully by going to the AWS Codepipeline console and finding your project CICD pipeline.
With proper setup, the CI/CD process should be automated. This process requires managing sourcecode through git and the use of webhooks to trigger that automation through the AWS CodePipeline.
You can deploy the serverless project by merging changes into your CI/CD targeted github branch or manually in your cli.
sls deploy --aws-profile <REPLACE_AWS_PROFILE> --stage <REPLACE_STAGE>
NOTE: you will need your AWS_PROFILE that you setup in the CI/CD Pipeline instructions.
At times during development you may wish to deploy changes to just one lambda. To do this run the following:
sls deploy function --aws-profile <REPLACE_AWS_PROFILE> --stage <REPLACE_STAGE> -f <REPLACE_FUNCTION_NAME>